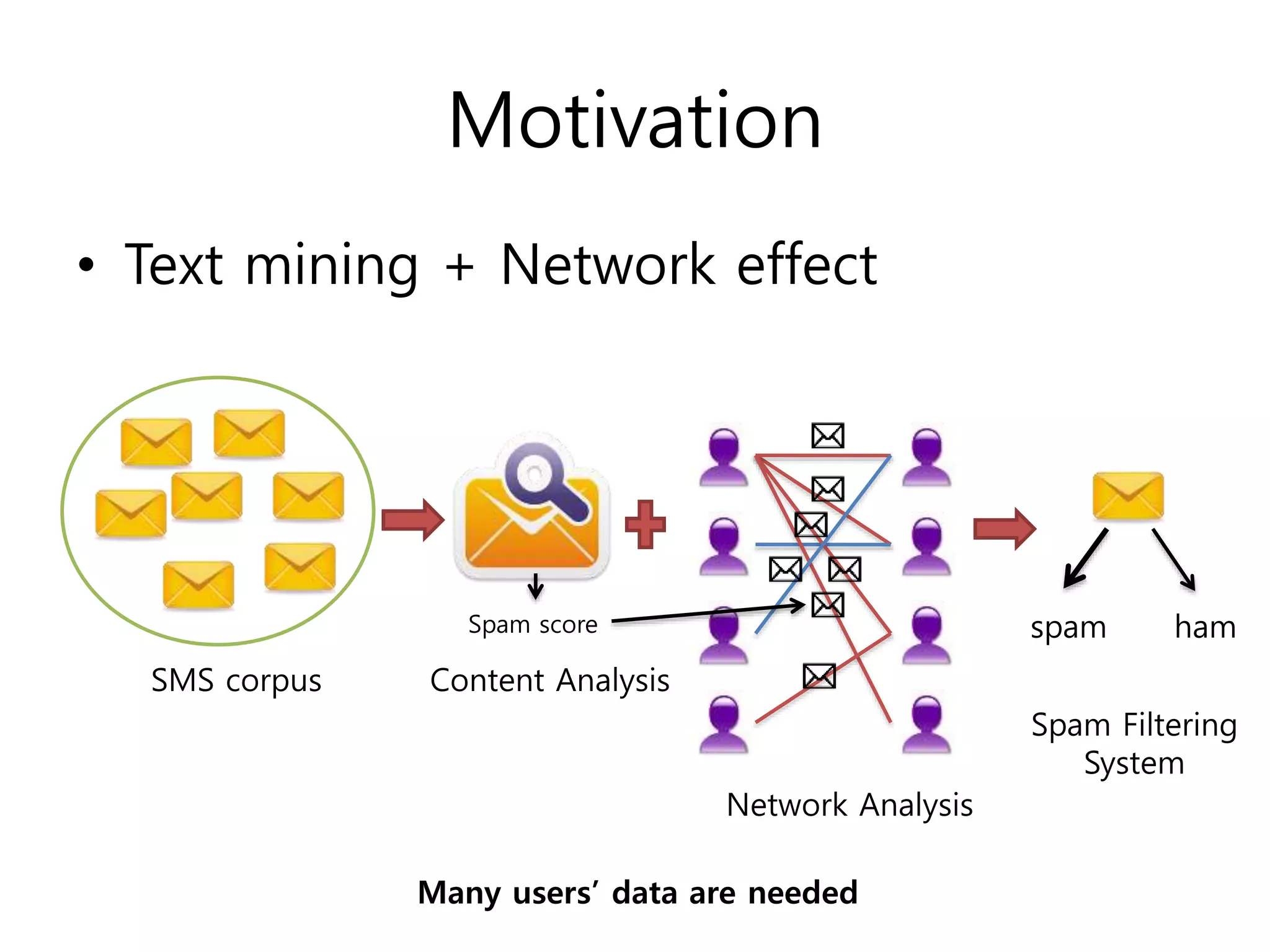
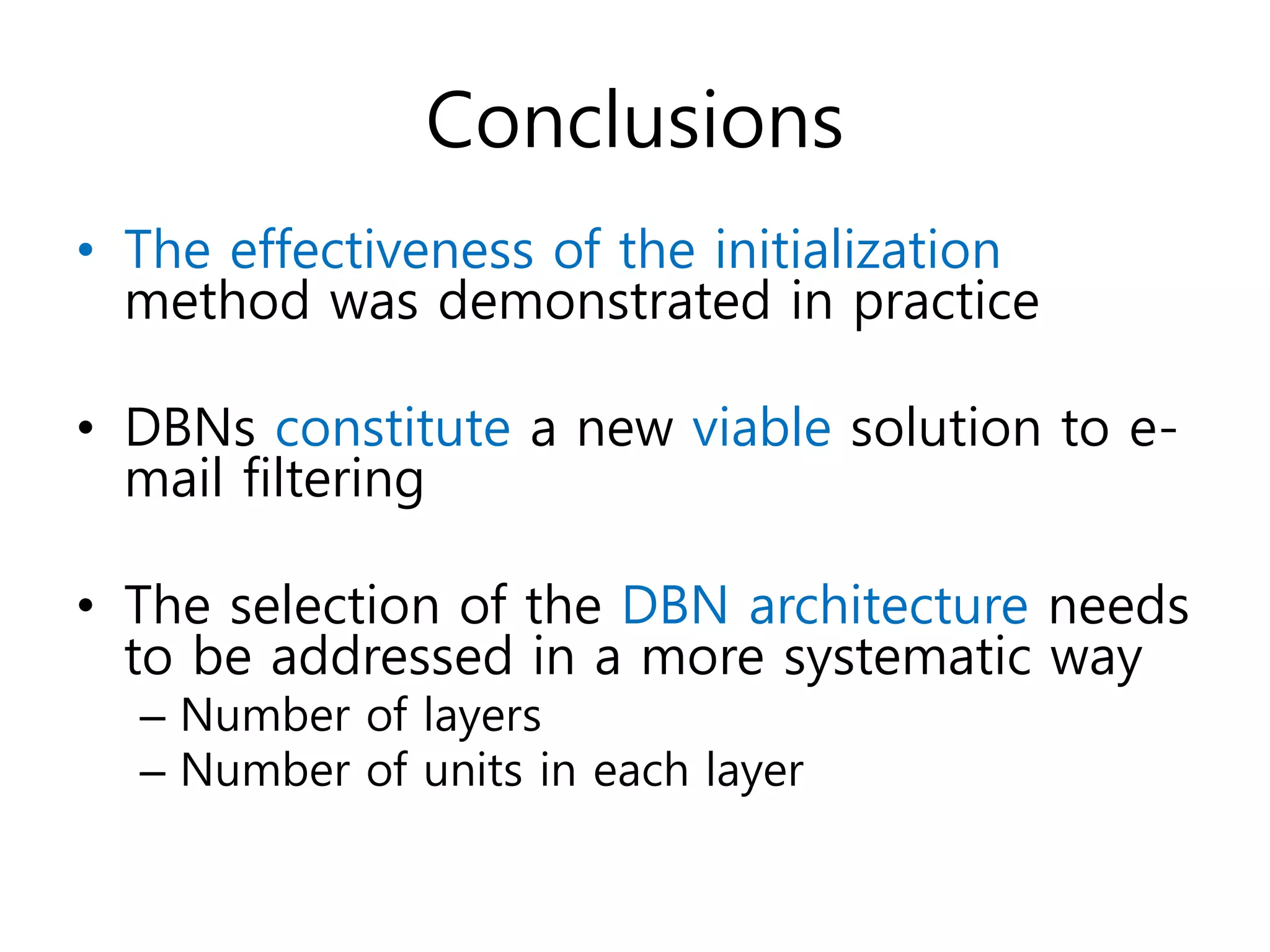
The document describes using deep belief networks (DBNs) for spam filtering of SMS and email messages. It discusses:
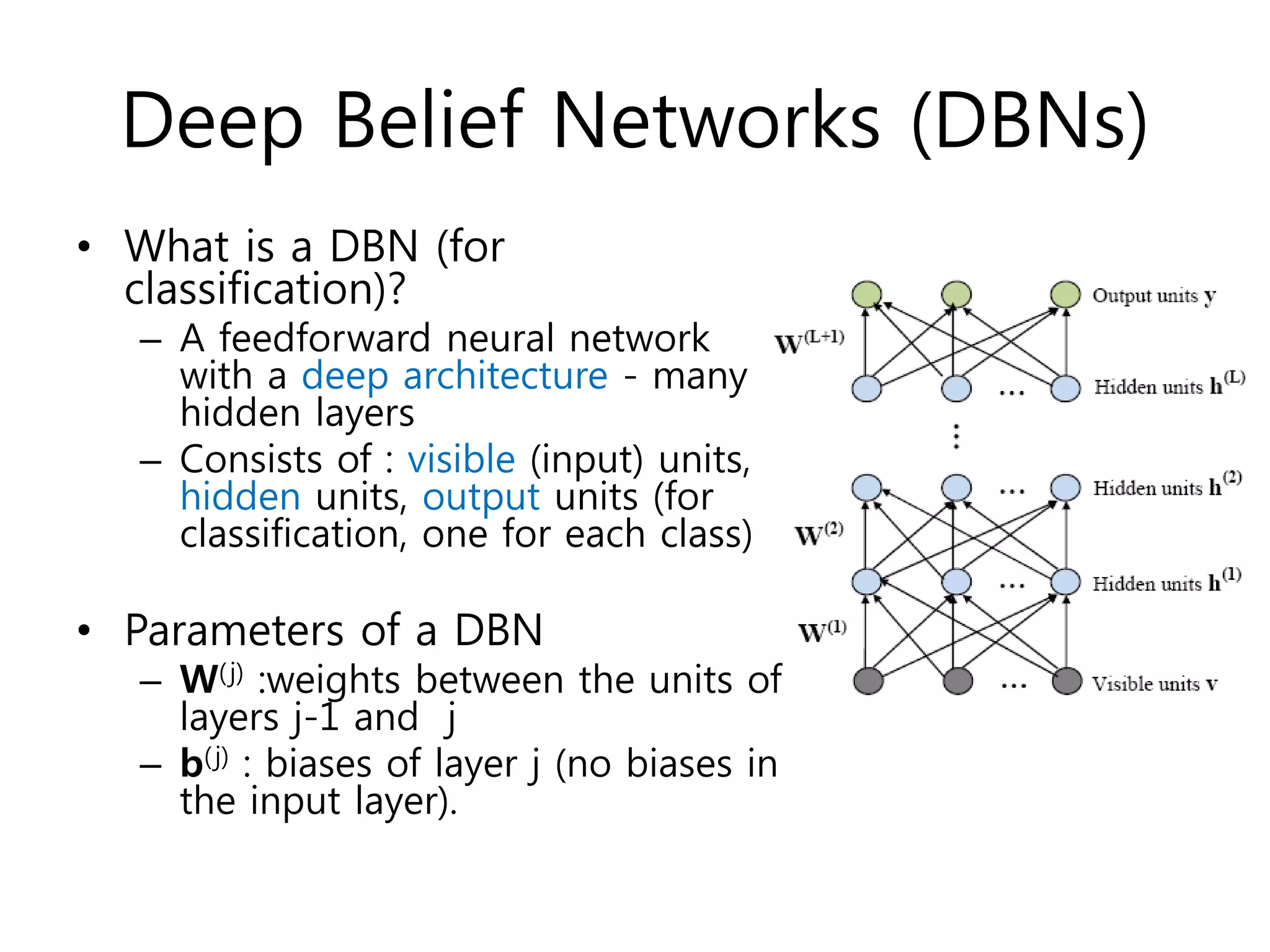
- DBNs consisting of multiple hidden layers for classification with visible, hidden, and output units.
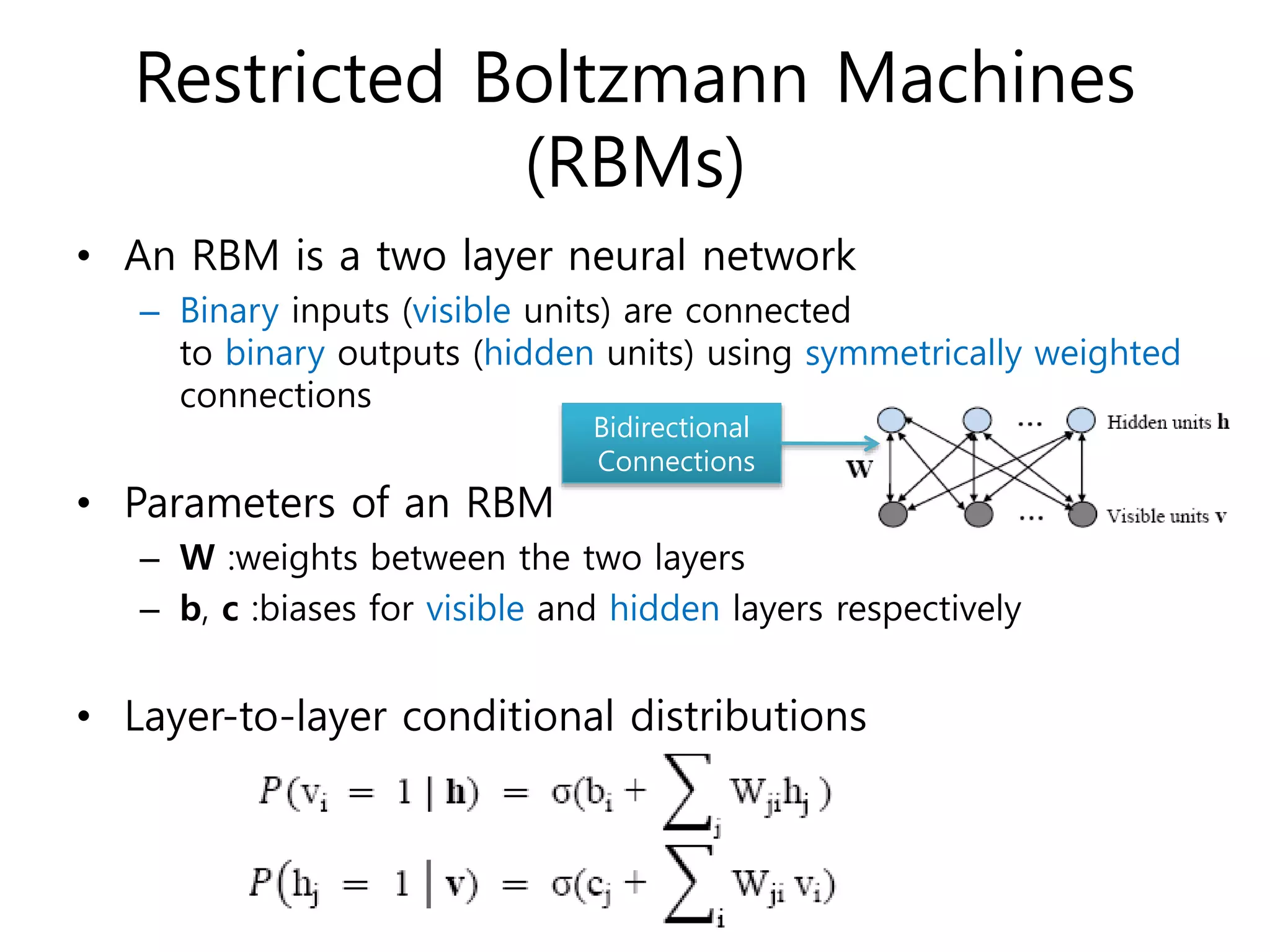
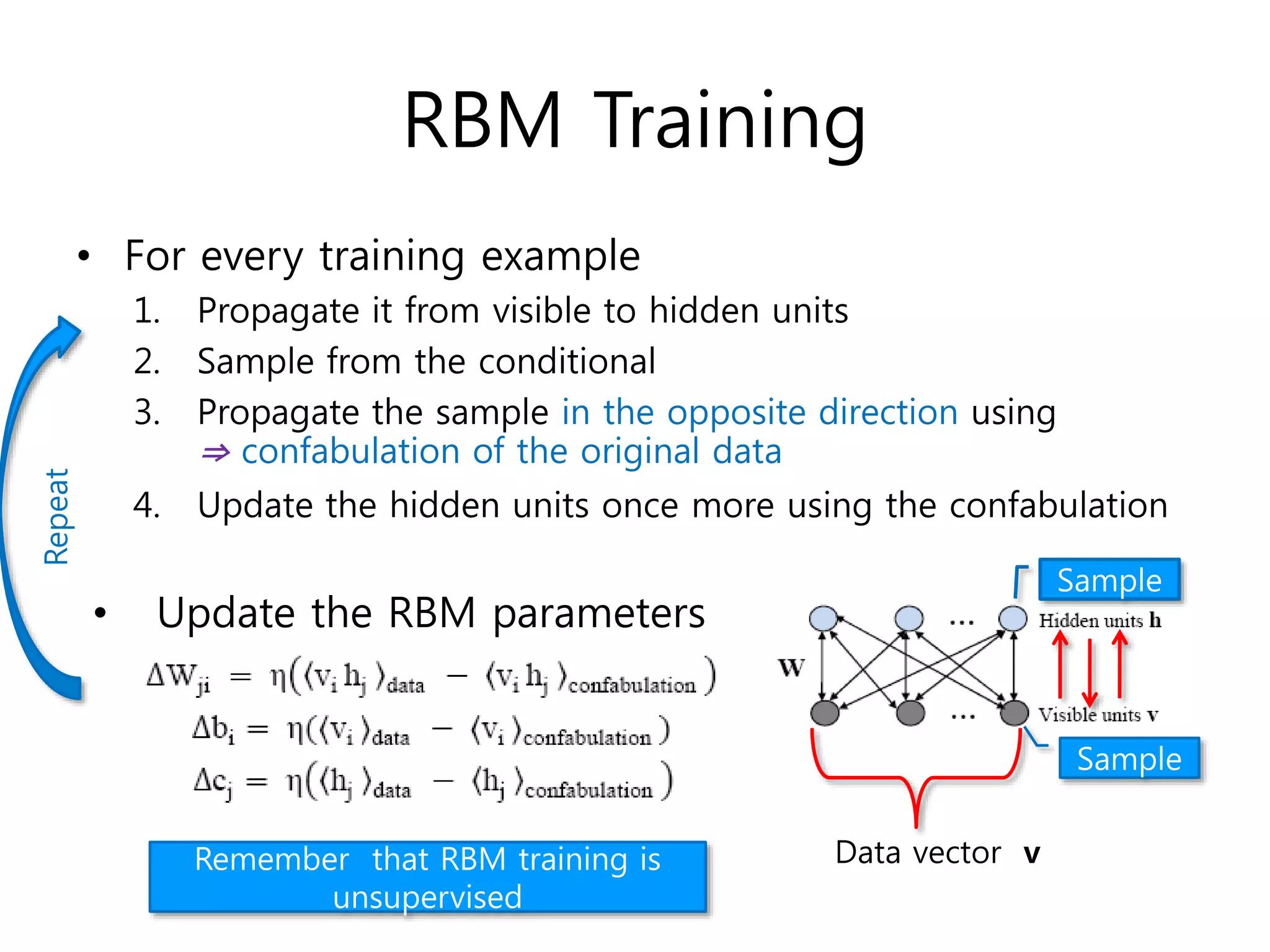
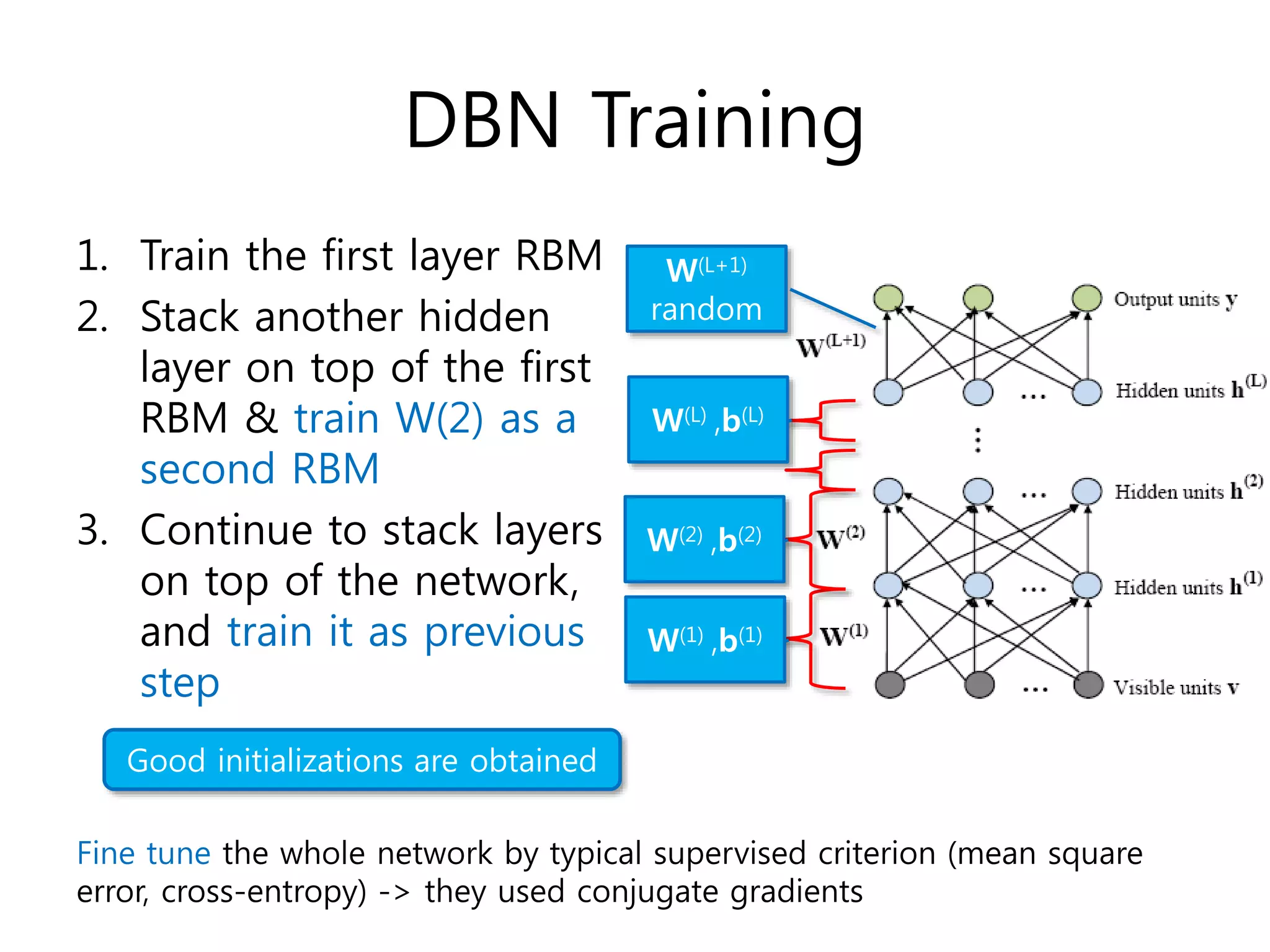
- Training DBNs using an unsupervised greedy layer-wise approach by initializing each layer as a restricted Boltzmann machine (RBM) and then fine-tuning the whole network through backpropagation.
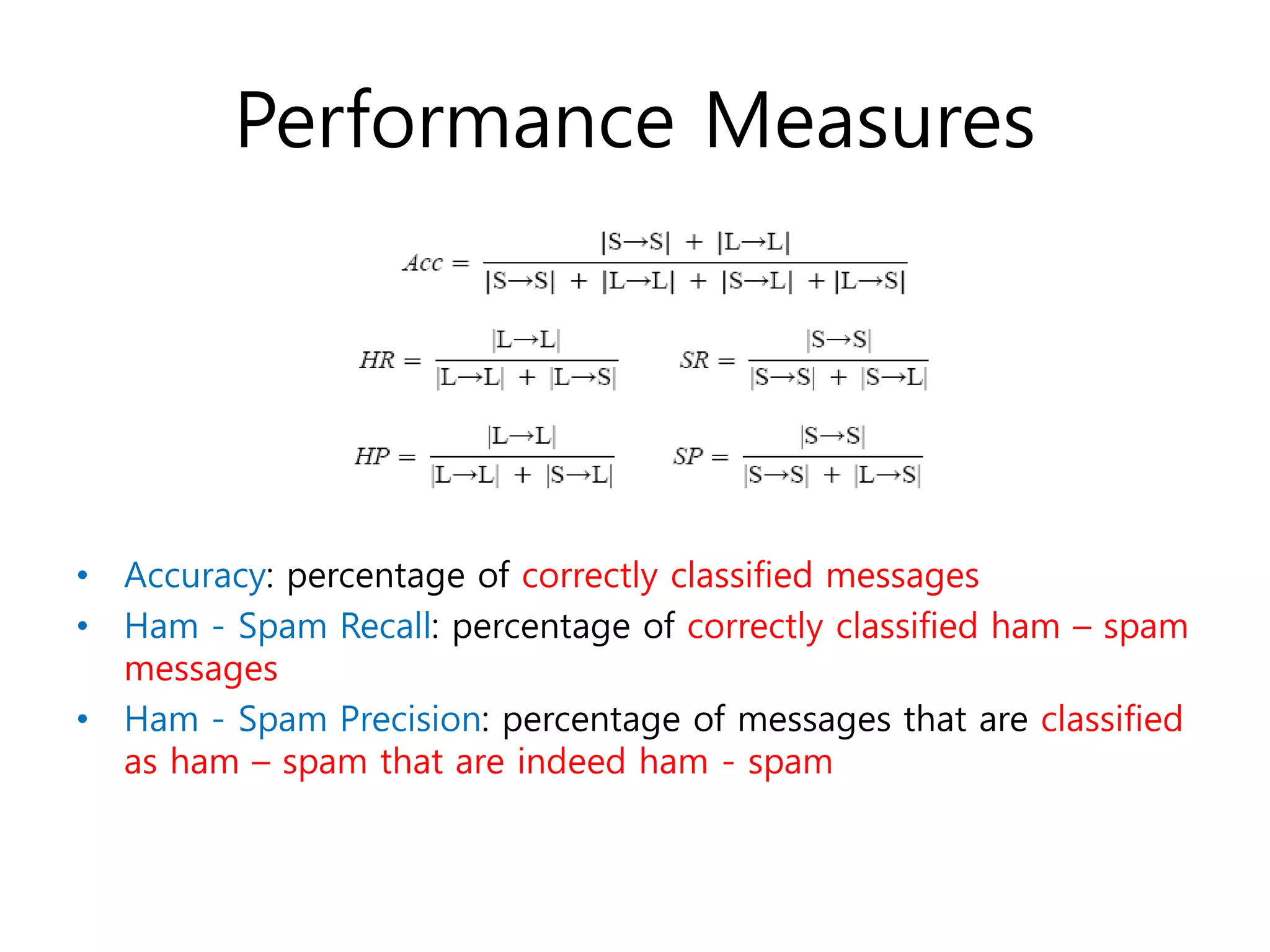
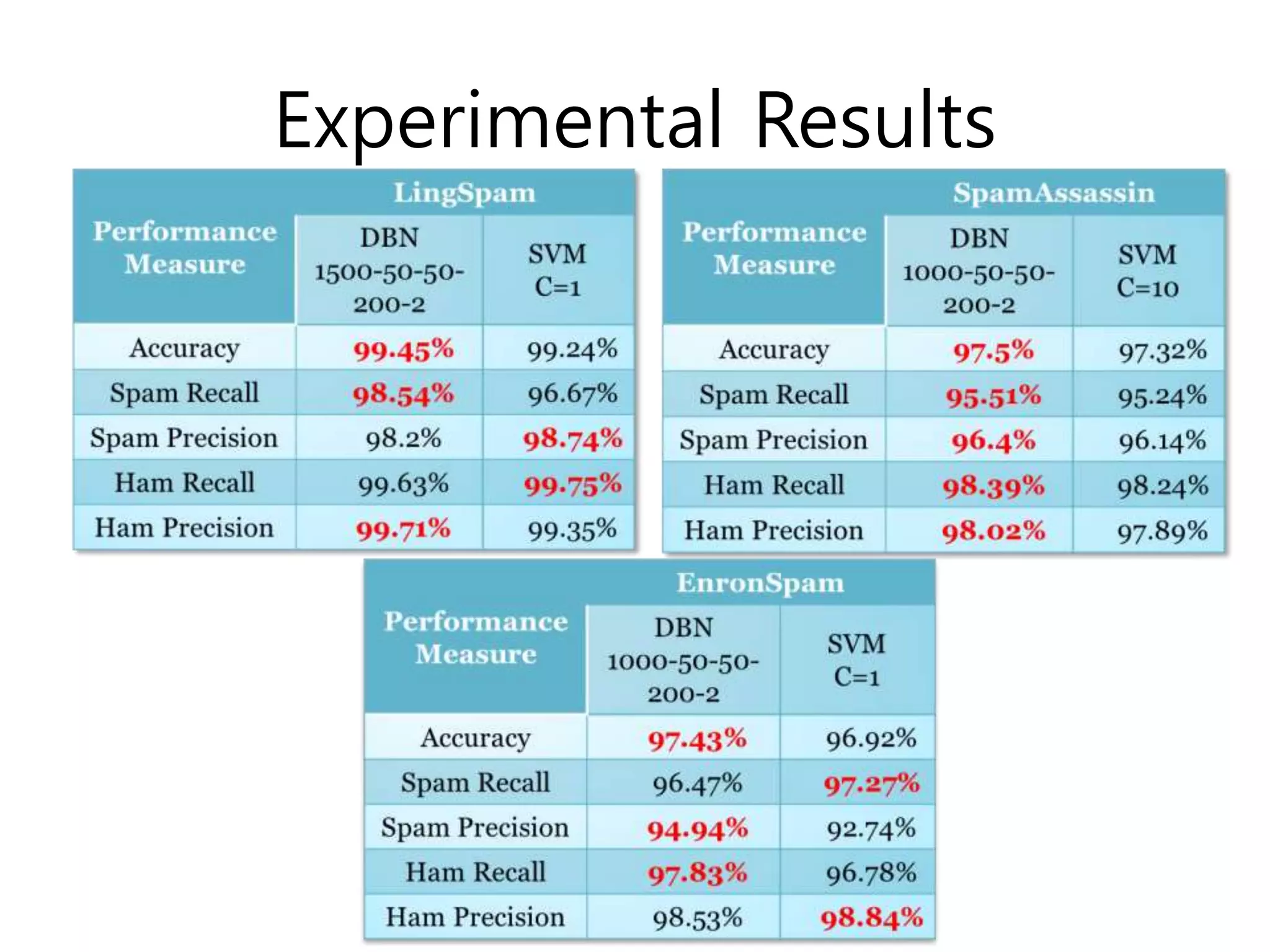
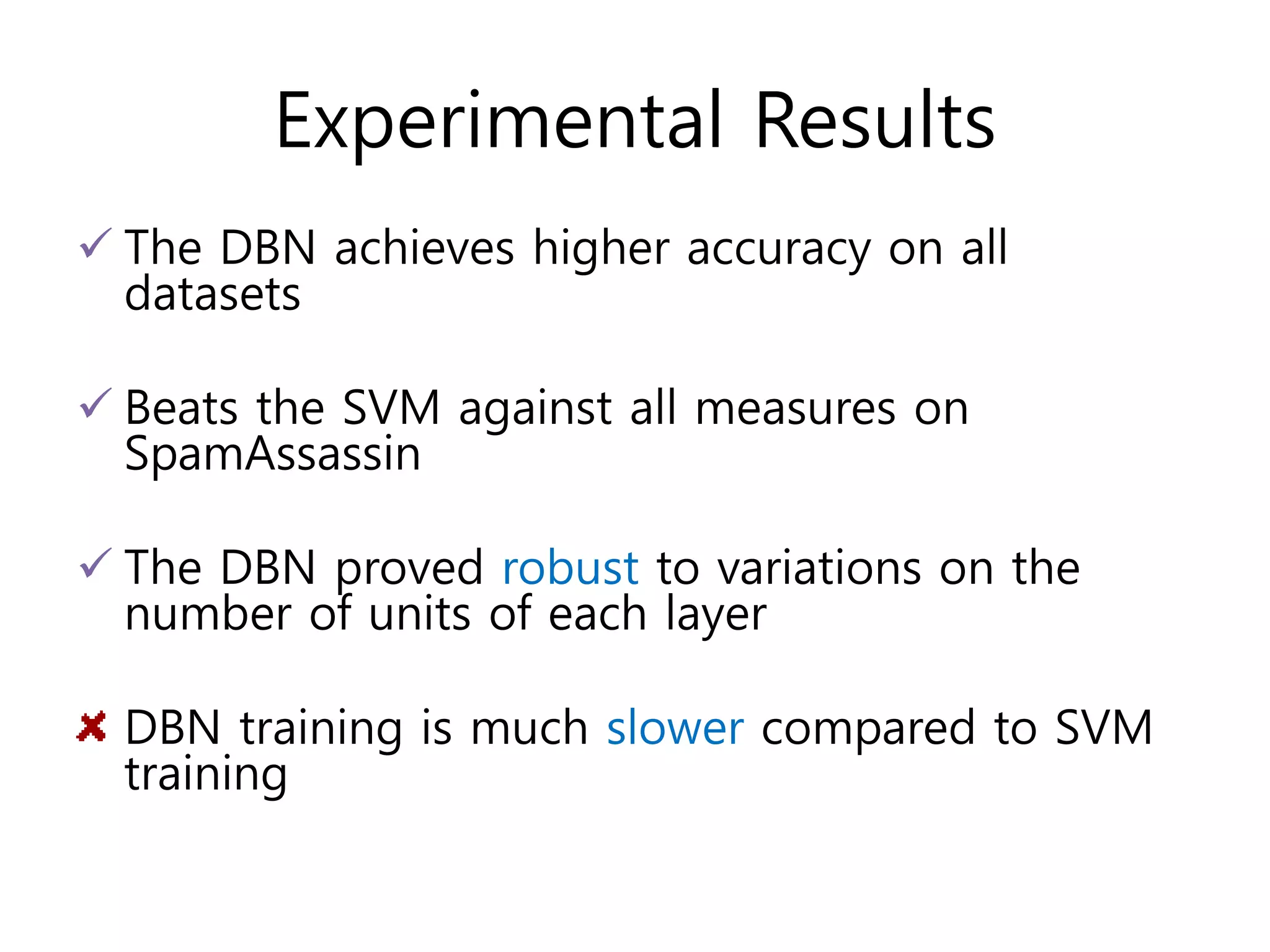
- Experimental results showing DBNs achieve higher accuracy than SVMs on email spam datasets and outperform SVMs on classification measures, though DBN training is slower.
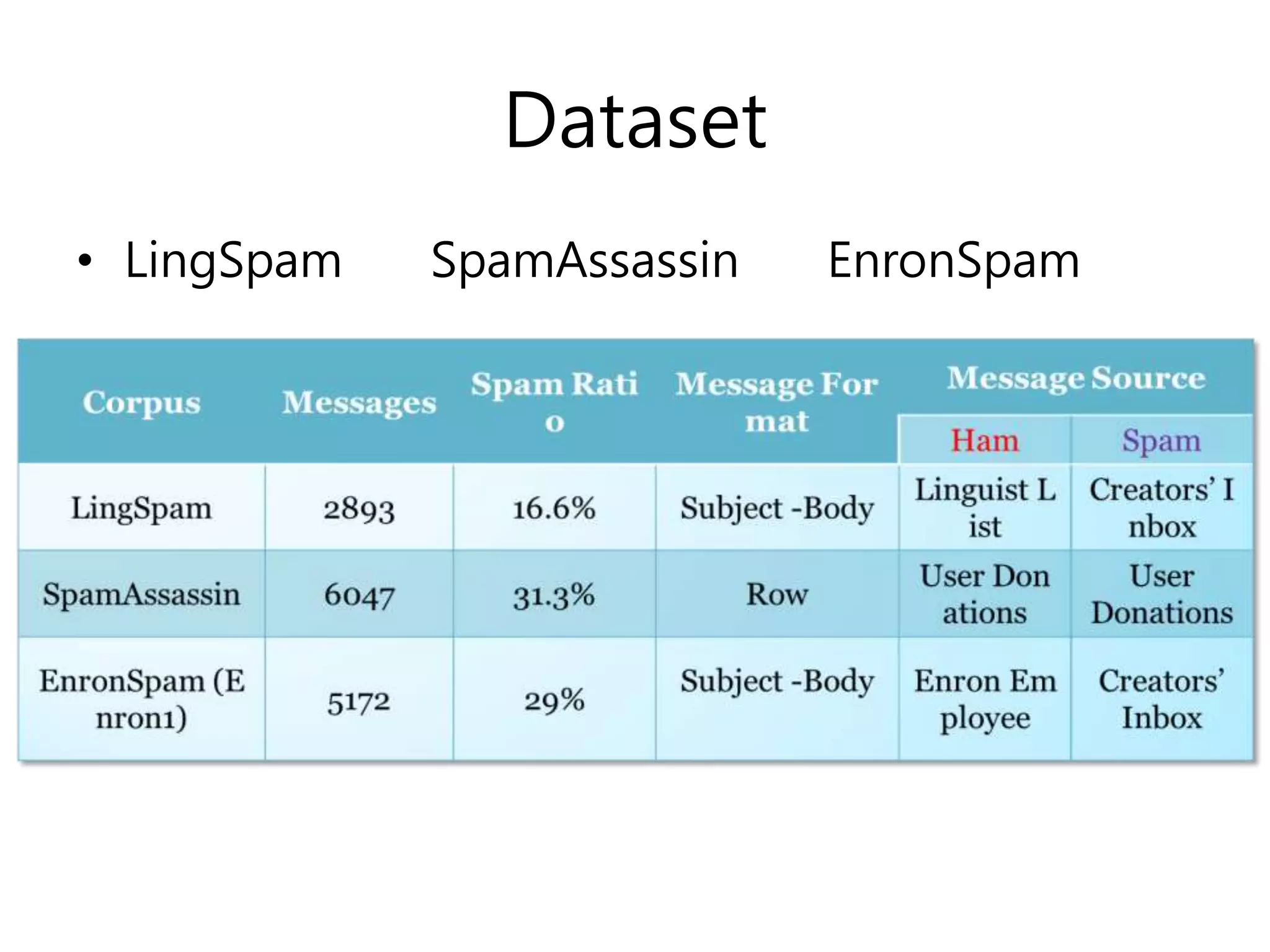
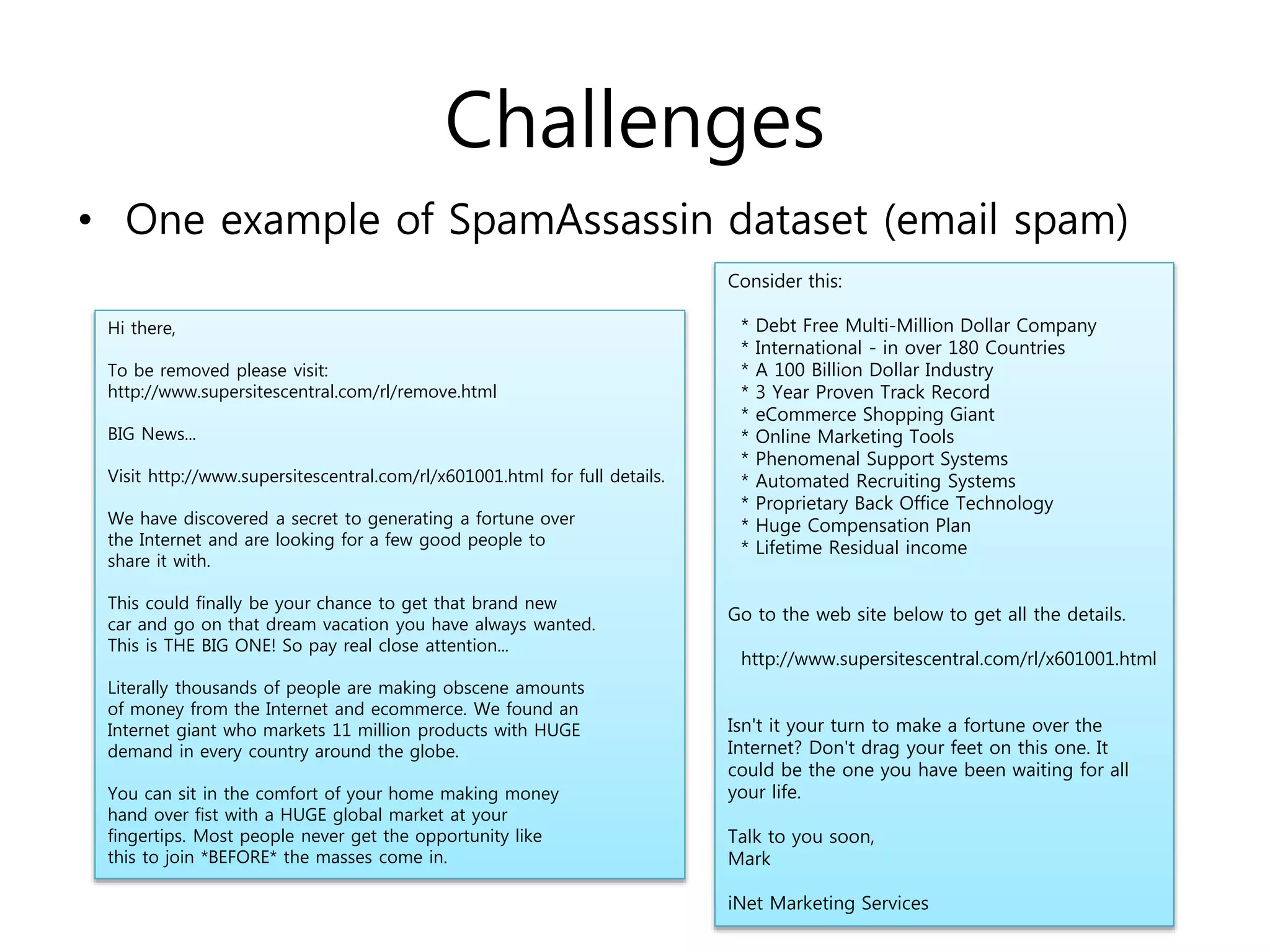
The document evaluates using DBNs for spam filtering and discusses challenges like handling non-English spam messages and multimedia spam.

![Training a DBN
• Conventional approach: Gradient based optimization
– Random initialization of weights and biases
– Adjustment by backpropagation
Optimization algorithms get stuck in poor solutions
due to random initialization
Solution
– Hinton et al [2006] proposed the use of a greedy layer-
wise unsupervised algorithm for initialization of DBNs
parameters
– Initialization phase: initialize each layer by treating it as a
Restricted Boltzmann Machine (RBM)](https://image.slidesharecdn.com/deepbeliefnetworksforspamfiltering-150305194705-conversion-gate01/75/Deep-belief-networks-for-spam-filtering-4-2048.jpg)
![Experimental Setup
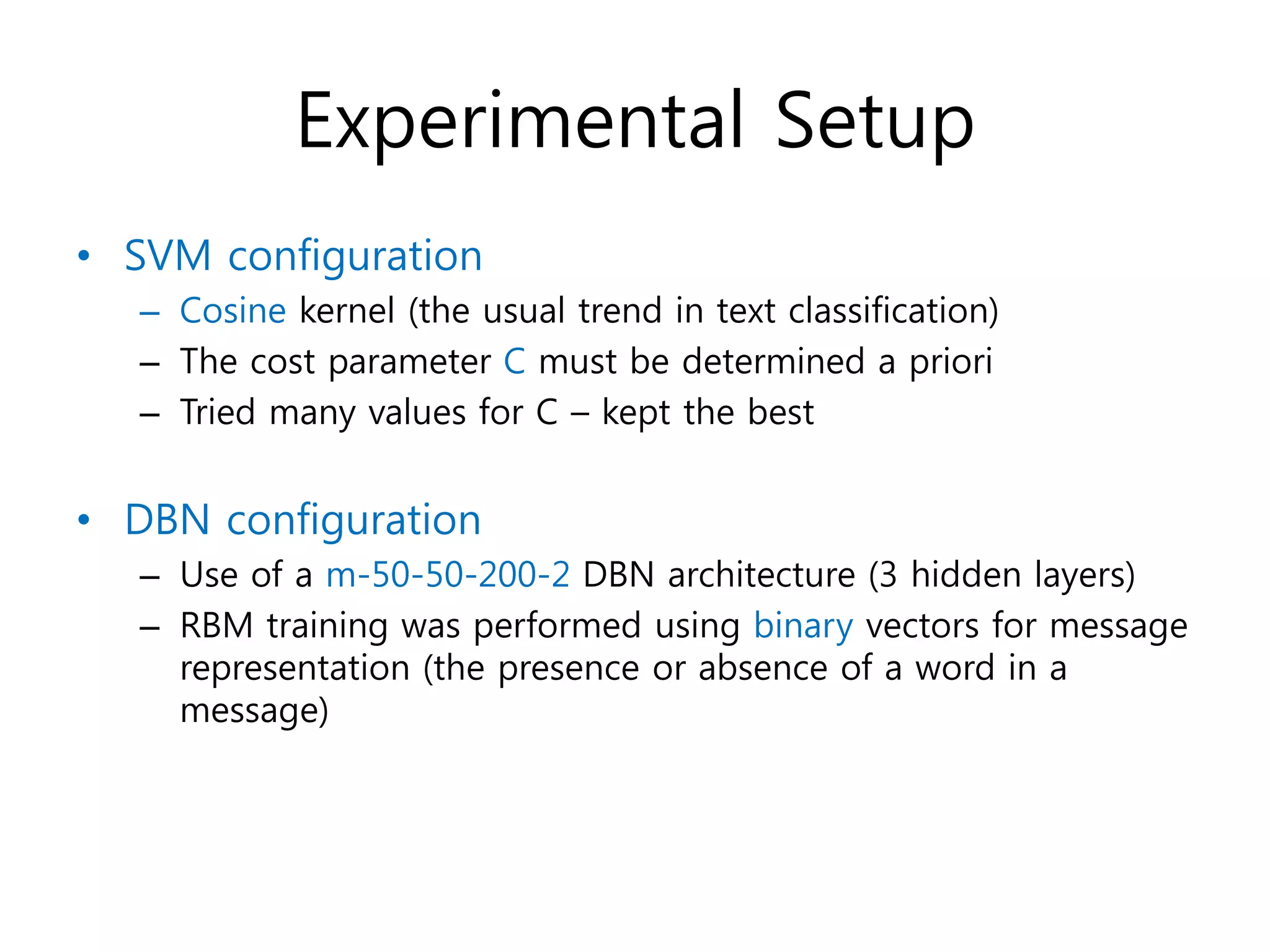
• Message representation: x=[x1, x2, …, xm]
– Each attribute(message) corresponds to a distinct word from
the corpus
– Use of frequency of the corresponding word
• Attribute selection
– Stop words and words appearing in <2 messages were
removed + Information gain score (m=1500 for LingSpam,
m=1000 for SpamAssassin and EnronSpam)
• All experiments were performed using 10-fold cross
validation](https://image.slidesharecdn.com/deepbeliefnetworksforspamfiltering-150305194705-conversion-gate01/75/Deep-belief-networks-for-spam-filtering-10-2048.jpg)
![Challenges
[Web발신]
- N H. 금 융 -
더쉽고, 더안전하게
~
7.8 % 로 7000
사.용.하.실.수
있습니다
[Web발신]
크♥사[ㅏ리1.95
로♡ㅂㅔ당+0.05
스♥ㅂL셀1.65
OK♡레알1.49
추쳐닌ck77
time-pr콤
[Web발신]
사-용-중-인
체_크_카_드
빌-려-주-면
월-4-5-0
당-일-진-행
바_로_결_제
[Web발신]
KB국민카드 김소
연님08/18KB국민
카드결제금액
3,500원.잔여포인
트리230(08/06기
준)
<공학인
증>2014-1학기
미상담 시 성적확
인 및 수강신청
제약!! 학기 중 상
담 필수~!!
• In case of Korean Spam SMS..?
1. See the distribution of words
and special characters in spam
and ham messages.
2. Input vector of DBN can be
‘number of special characters’
or ‘how correct the grammar
of message is’ … instead of
‘number of spam words’](https://image.slidesharecdn.com/deepbeliefnetworksforspamfiltering-150305194705-conversion-gate01/75/Deep-belief-networks-for-spam-filtering-16-2048.jpg)
