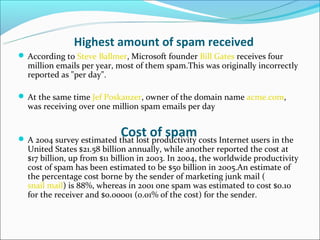
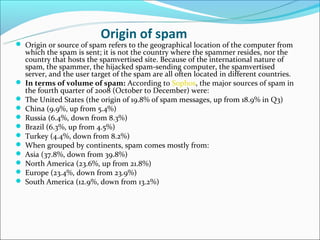
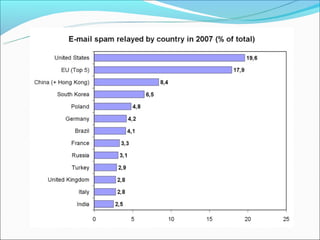
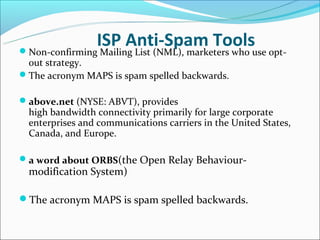
Email spam, also known as junk email or unsolicited bulk email, is a subset of electronic spam that involves sending nearly identical unsolicited messages to numerous recipients. Spam has grown significantly since the early 1990s, with about 80% of spam now sent using botnets. Spammers collect email addresses from various sources and sites to send spam messages advertising products like pharmaceuticals. Fighting spam involves techniques like using email providers that utilize blacklists to block spam, protecting email addresses, and effectively reporting spam messages.





![Statistics and estimates
The total volume of email spam has been consistently growing, but in 2011 the
trend seems to have reversed.
The first known spam email, advertising a DEC product presentation, was sent in
1978 by Gary Thuerk to 600 addresses, which was all the users of ARPANET at
the time, though software limitations meant only slightly more than half of the
intended recipients actually received it.
As of August 2010, the amount of spam was estimated to be around 200 billion
spam messages sent per day. More than 97% of all emails sent over the net are
unwanted, according to a Microsoft security report.
A 2010 survey of US and European email users showed that 46% of the
respondents had opened spam messages, although only 11% had clicked on a
link.[45]](https://image.slidesharecdn.com/spam2-120905143615-phpapp01/85/What-is-SPAM-9-320.jpg)