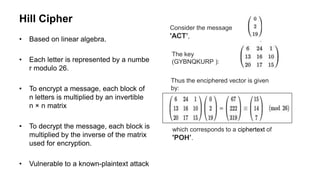
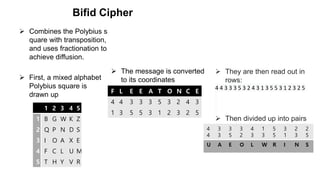
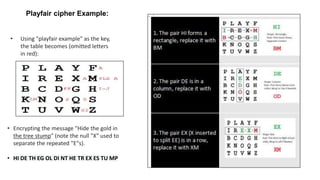
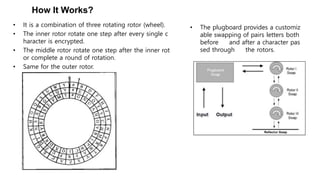
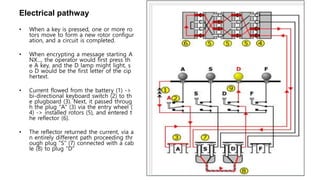
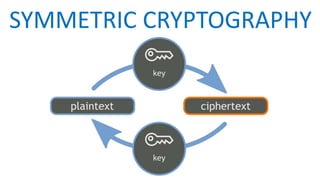
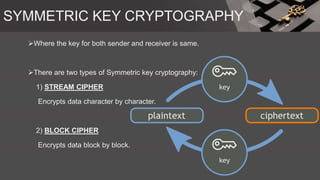
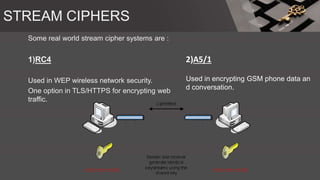
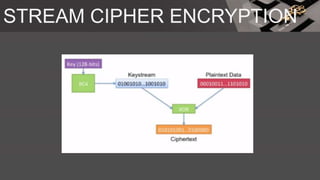
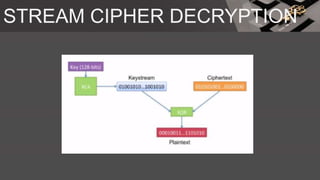
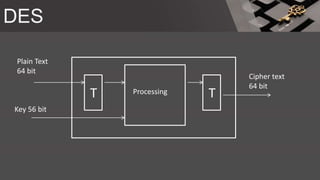
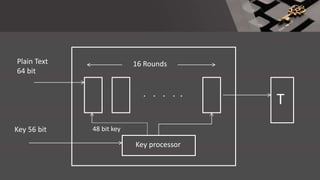
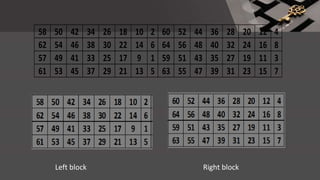
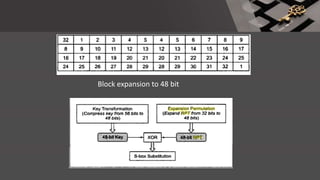
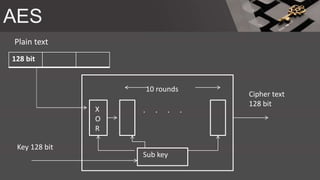
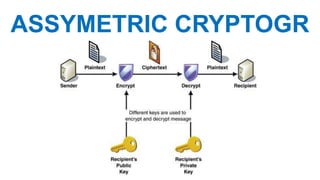
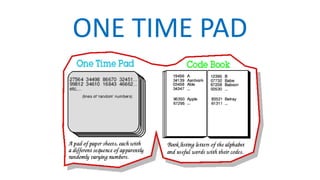
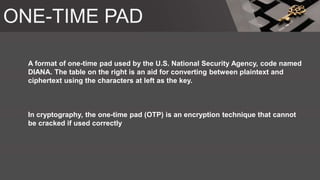
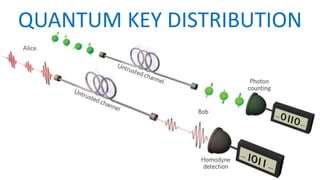
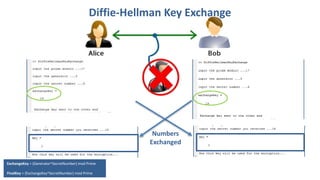
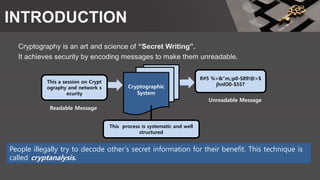
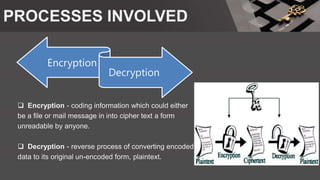
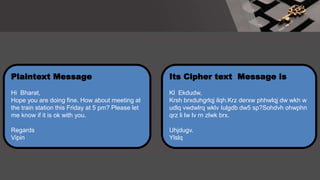
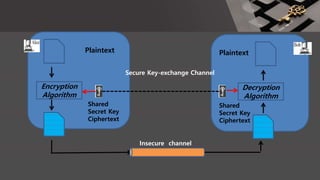
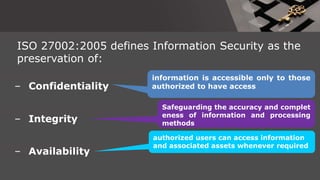
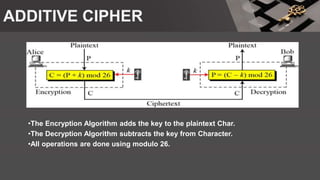
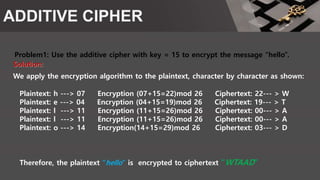
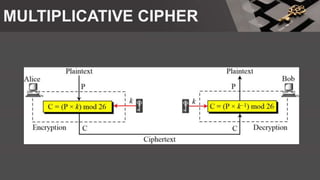
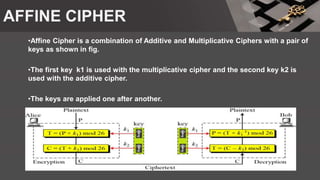
The document is a comprehensive presentation on cryptography, detailing its definition, processes involved like encryption and decryption, and various techniques such as additive and Vigenère ciphers. It also addresses the need for cryptography, the types of cryptography—symmetric and asymmetric—and their applications. Additionally, the document outlines traditional cryptography methods and highlights their vulnerabilities, leading to the development of more sophisticated techniques post-1950s.





![VIGENERE CIPHER
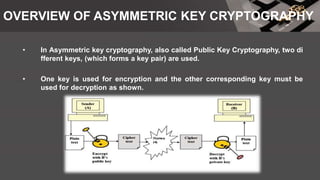
• Vigenere cipher was designed by Blaise de Vigenere, It uses a scheme to create
the key stream.
• The stream is repetition of an initial secret key stream of length, m, where
1≤ m ≥26
• The cipher can be described as below where (k1,k2,k3….km) is the initial secret
key agreed to by Alice and Bob.
P=P1P2P3……….. C=C1C2CK………….
PK=[(k1,k2………..,km)(k1k2…….km)….]
Encryption: Ci=(Pi+ki)mod26 Decryption: Pi=(Ci-ki)mod26](https://image.slidesharecdn.com/cryptography-170309030037/85/Cryptography-17-320.jpg)
![VIGENERE CIPHER
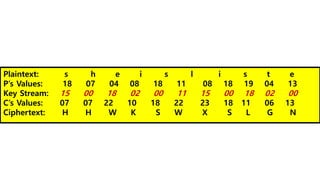
Problem: Encrypt the plaintext “ She is listening” using the 6 character keyword
“ PASCAL”( value = 15,00,18,02, 00,11).
Solution: The initial key is PASCAL(Value is 15,00,18,20,00,11). The key stream is the
repetition of the initial key stream (as many as can be needed). The Cipher text is fou
nd as shown:
P=P1P2P3……….. C=C1C2CK…………. PK=[(k1,k2………..,km)(k1k2…….km)….]
Encryption: Ci=(Pi+ki)mod26 Decryption: Pi=(Ci-ki)mod26
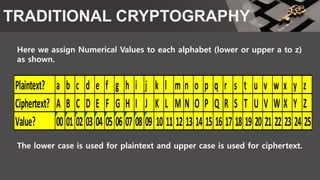
Plaintext? a b c d e f g h i j k l m n o p q r s t u v w x y z
Ciphertext? A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
Value? 00 01 02 03 04 05 06 07 08 09 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25](https://image.slidesharecdn.com/cryptography-170309030037/85/Cryptography-18-320.jpg)