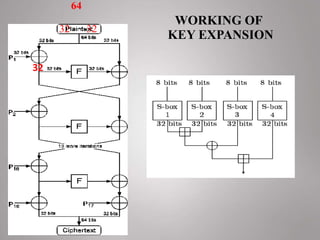
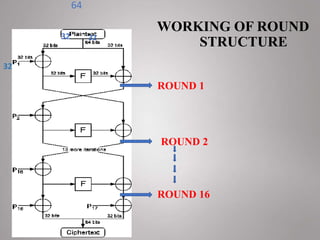
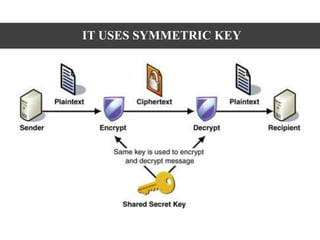
This document discusses the design and implementation of the Blowfish encryption algorithm using Verilog HDL. Blowfish is a symmetric block cipher that uses a variable-length key from 32 to 448 bits, making it suitable for securing data. The algorithm consists of two parts - key expansion and a round structure involving 16 rounds of operations. The authors implemented Blowfish using Verilog HDL on a Xilinx FPGA for applications requiring encryption like IoT devices. Their design achieved high-speed encryption of up to 4 bits per clock cycle and operated at a maximum frequency of 50MHz.