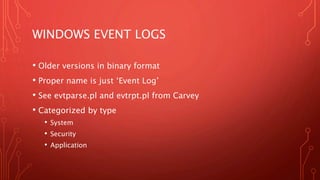
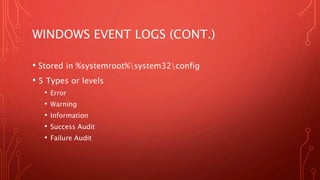
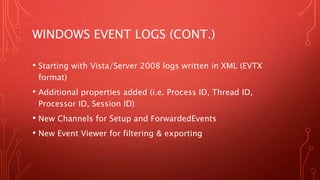
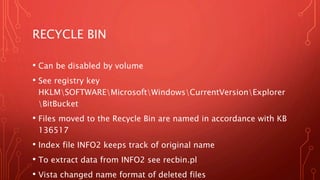
System event logs, application logs, and other log files chronicle system events and can help with timeline reconstruction. Windows event logs are stored in XML or binary format and contain details like event type, date/time, and process information. Other useful logs include Prefetch files, scheduled tasks, recycle bin contents, hibernation files, and application-specific logs. Thoroughly investigating log files is important for finding relevant details in an investigation.