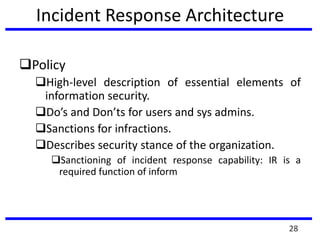
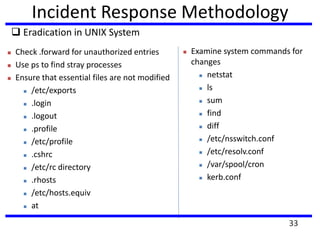
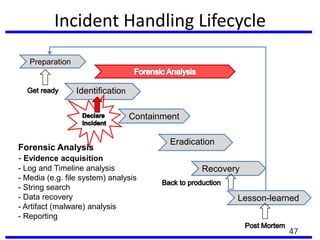
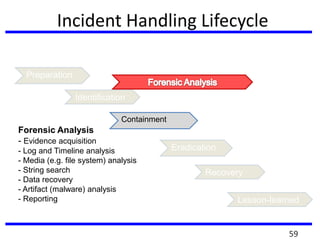
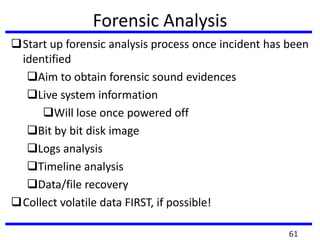
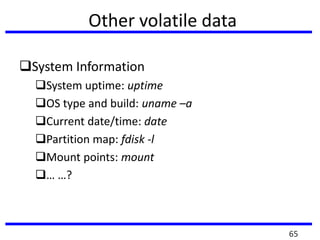
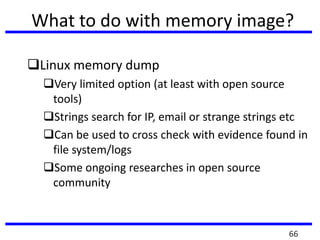
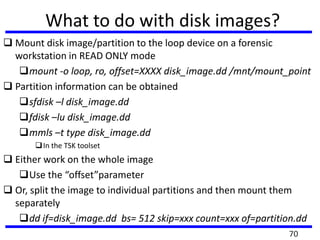
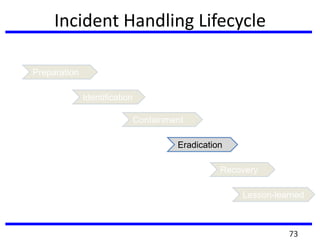
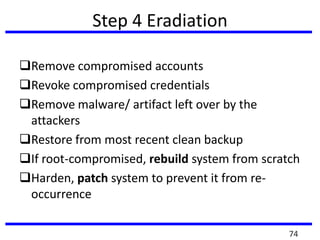
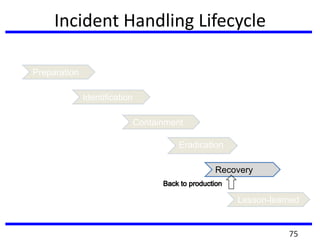
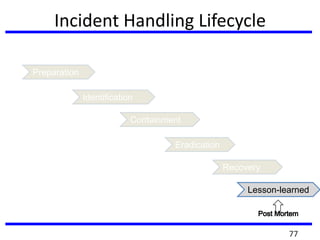
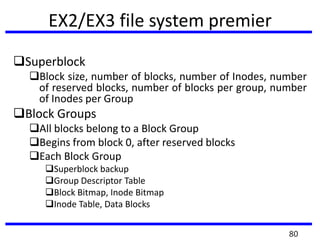
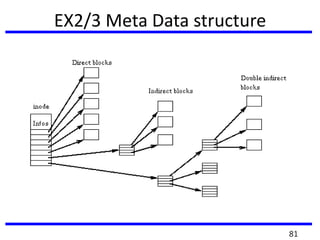
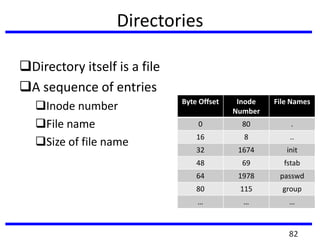
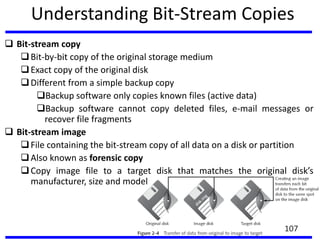
The document provides a comprehensive overview of computer forensics, outlining its goals, methodologies, and types of cyber crimes. It discusses the techniques used in investigations, the importance of digital evidence in legal cases, and the various stakeholders involved in computer forensics, including law enforcement and private corporations. Additionally, it covers identity theft, types of cyber forensics, and strategies for tackling cyber criminal activities.