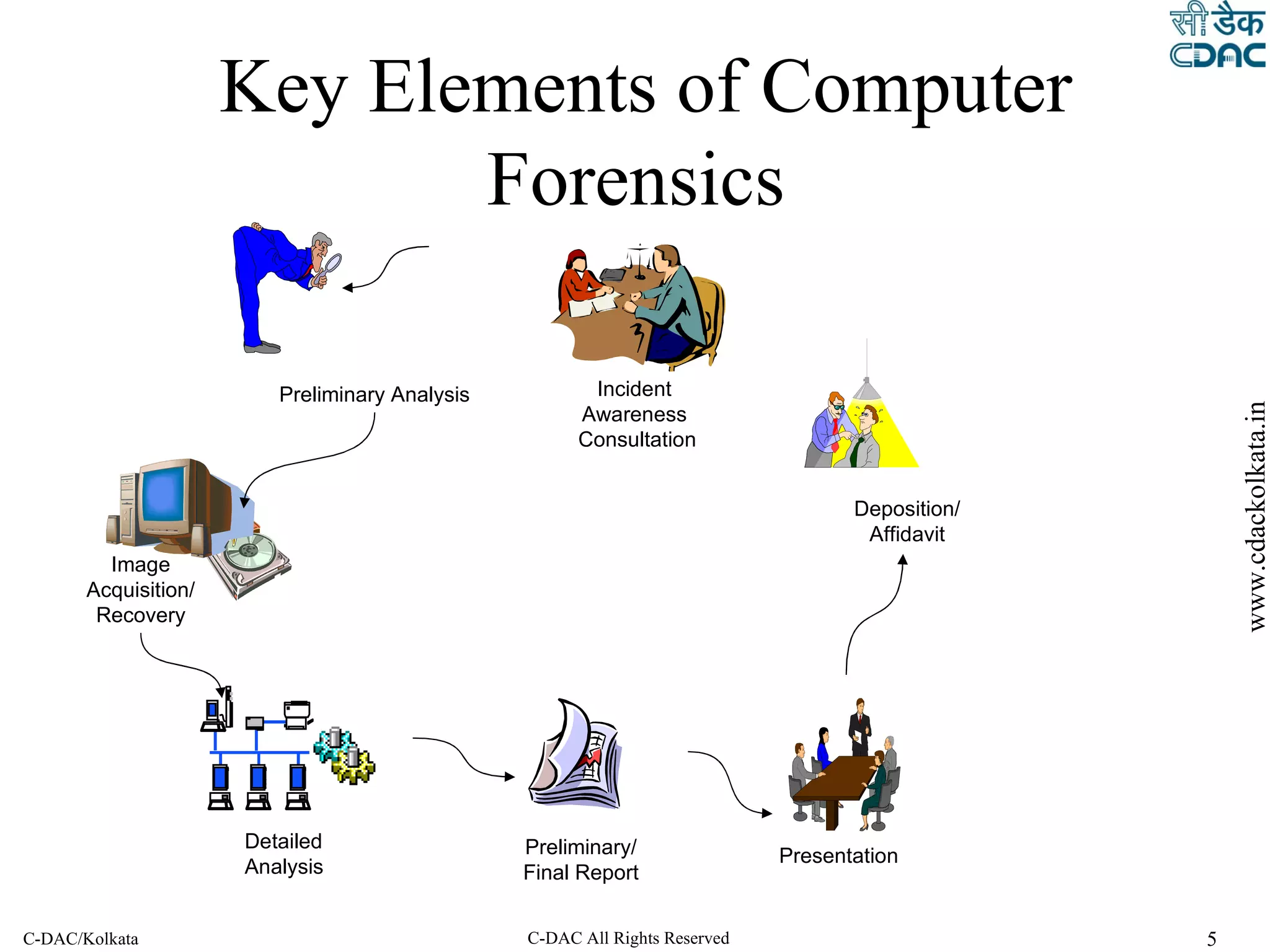
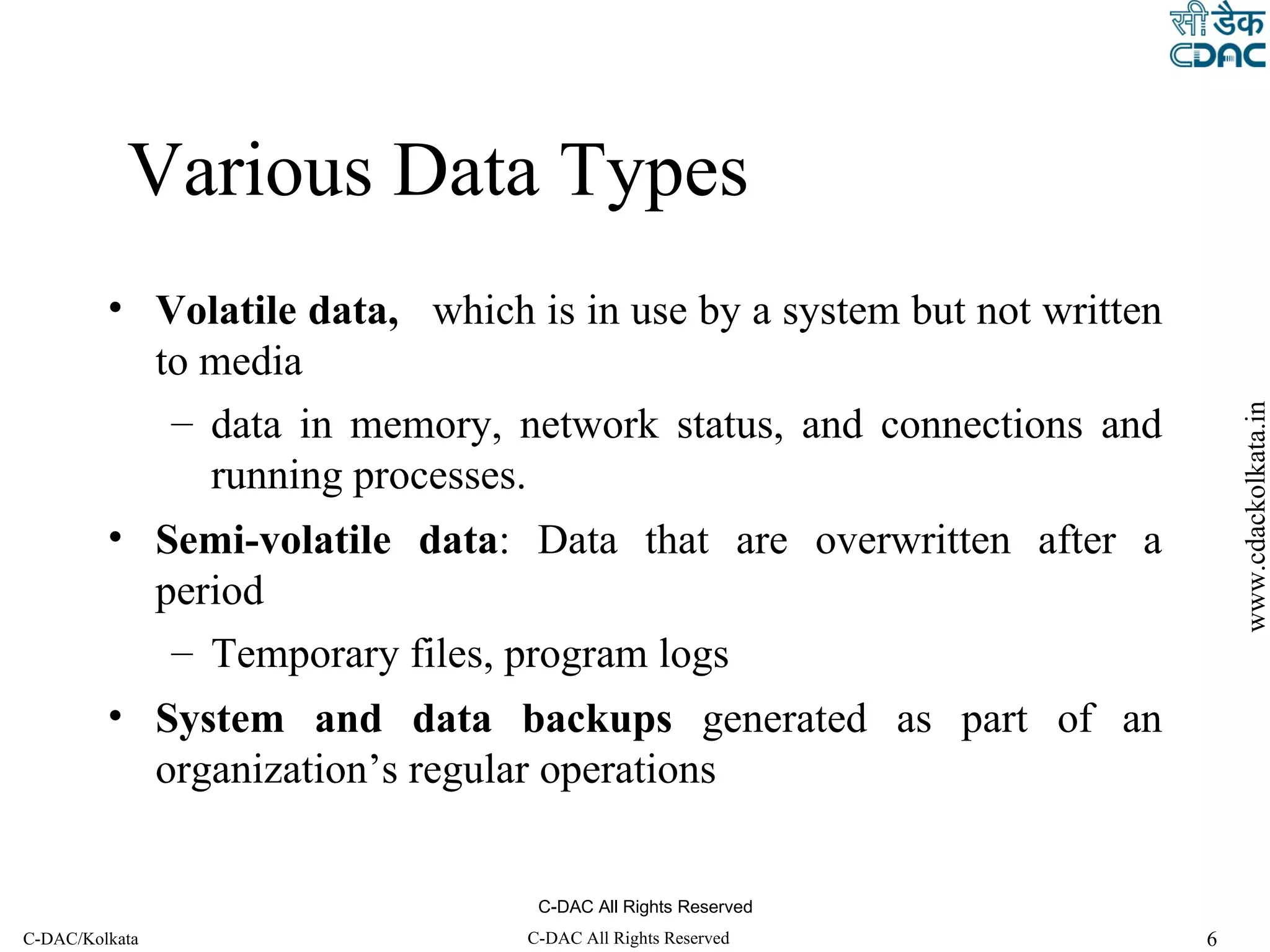
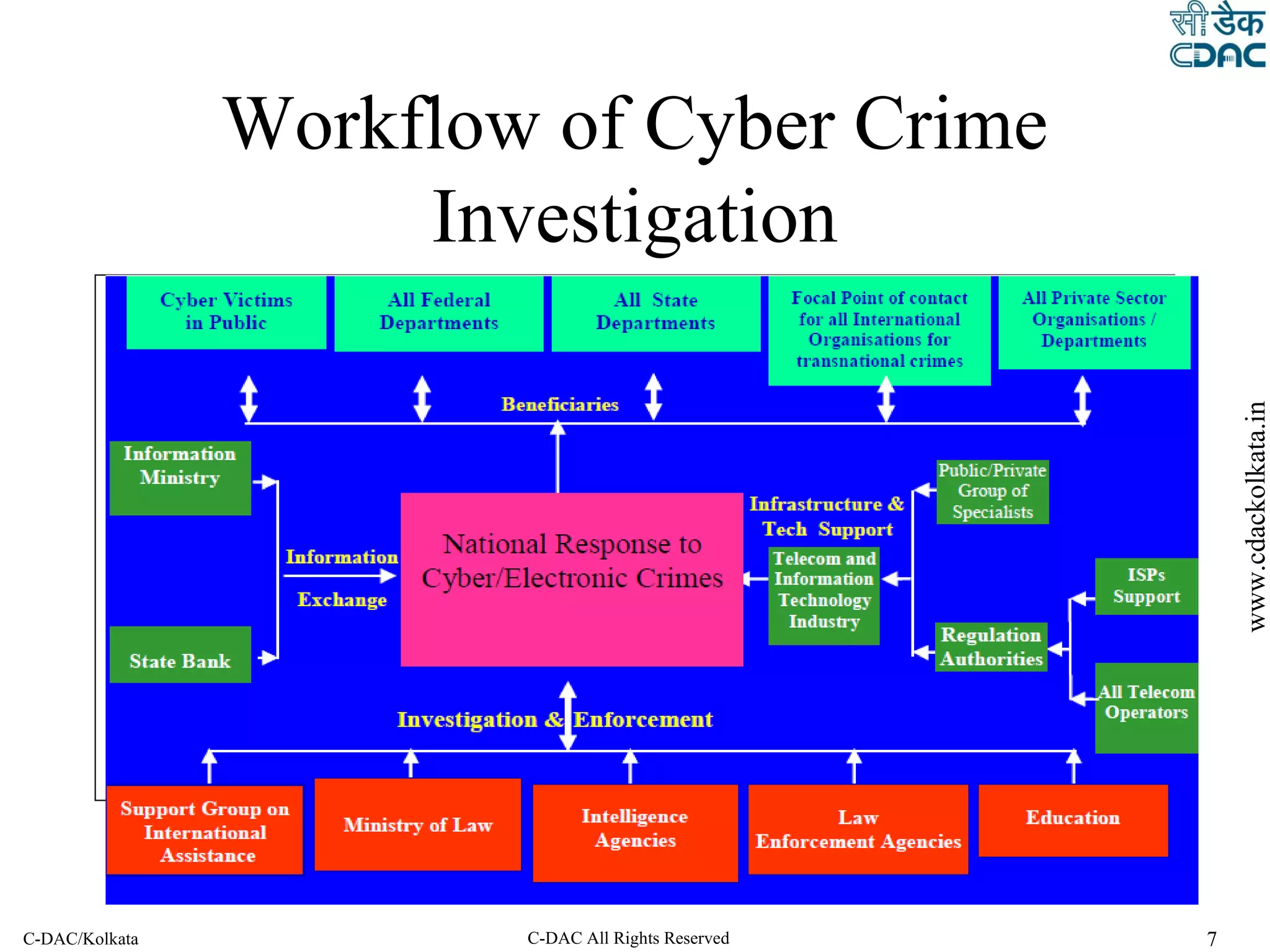
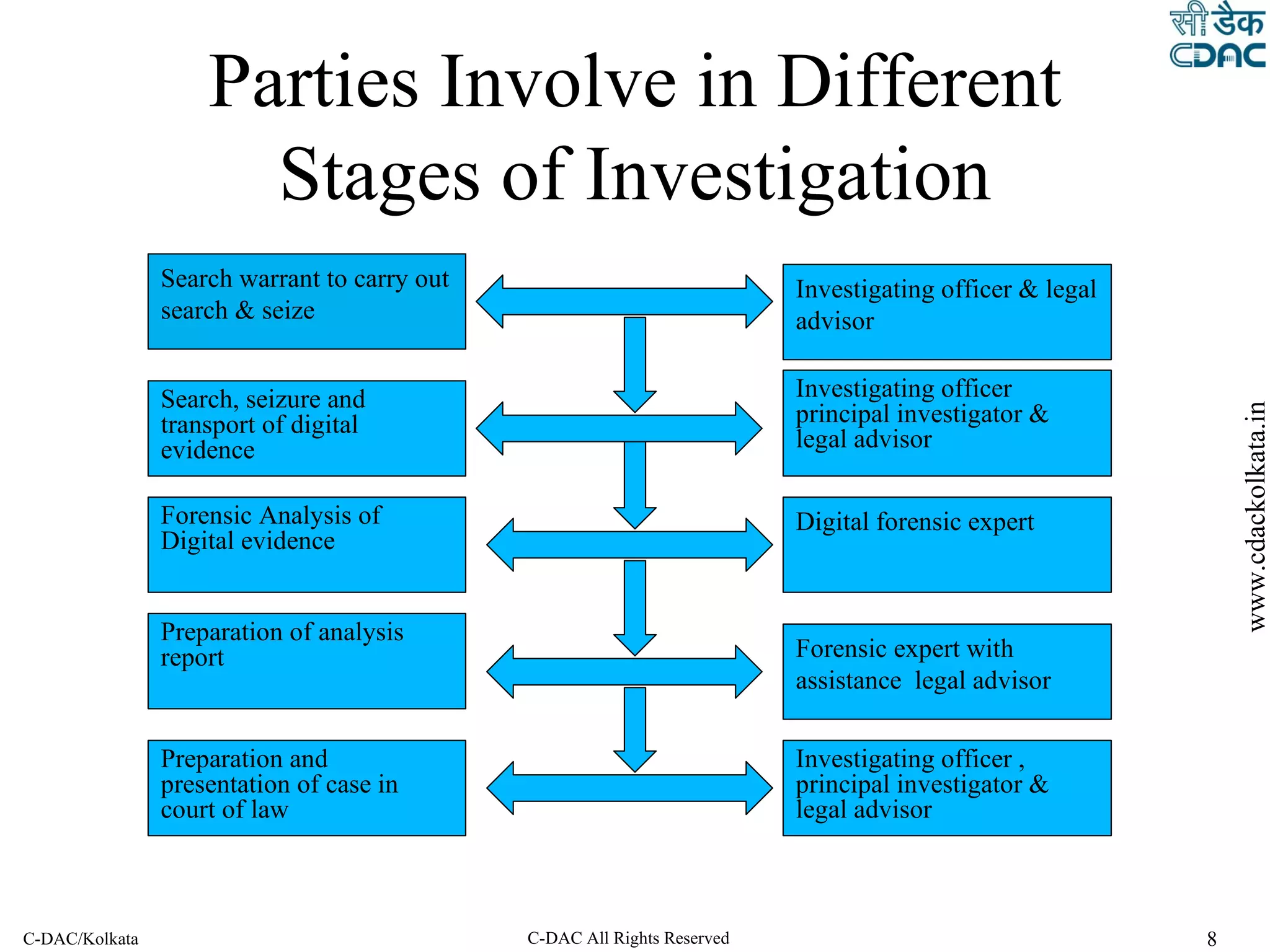
The document outlines the steps of a cyber forensic investigation process:
1. Verification and identification of systems involved to collect relevant data.
2. Preservation, collection and acquisition of evidence from systems in a manner that minimizes data loss and maintains a legally defensible chain of custody.
3. Processing, review and analysis of collected data through techniques like timeline analysis, keyword searching and data recovery to find relevant evidence.