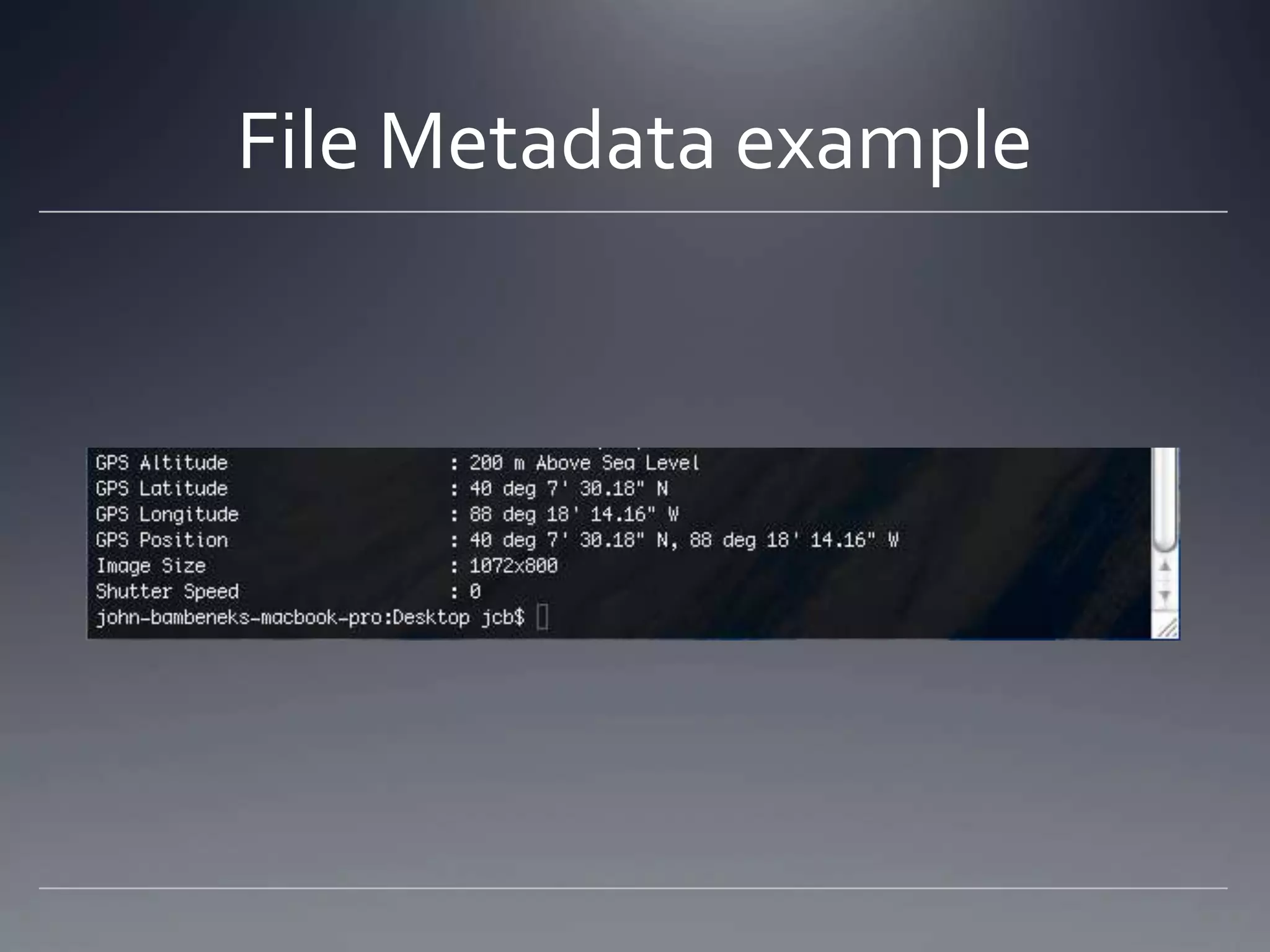
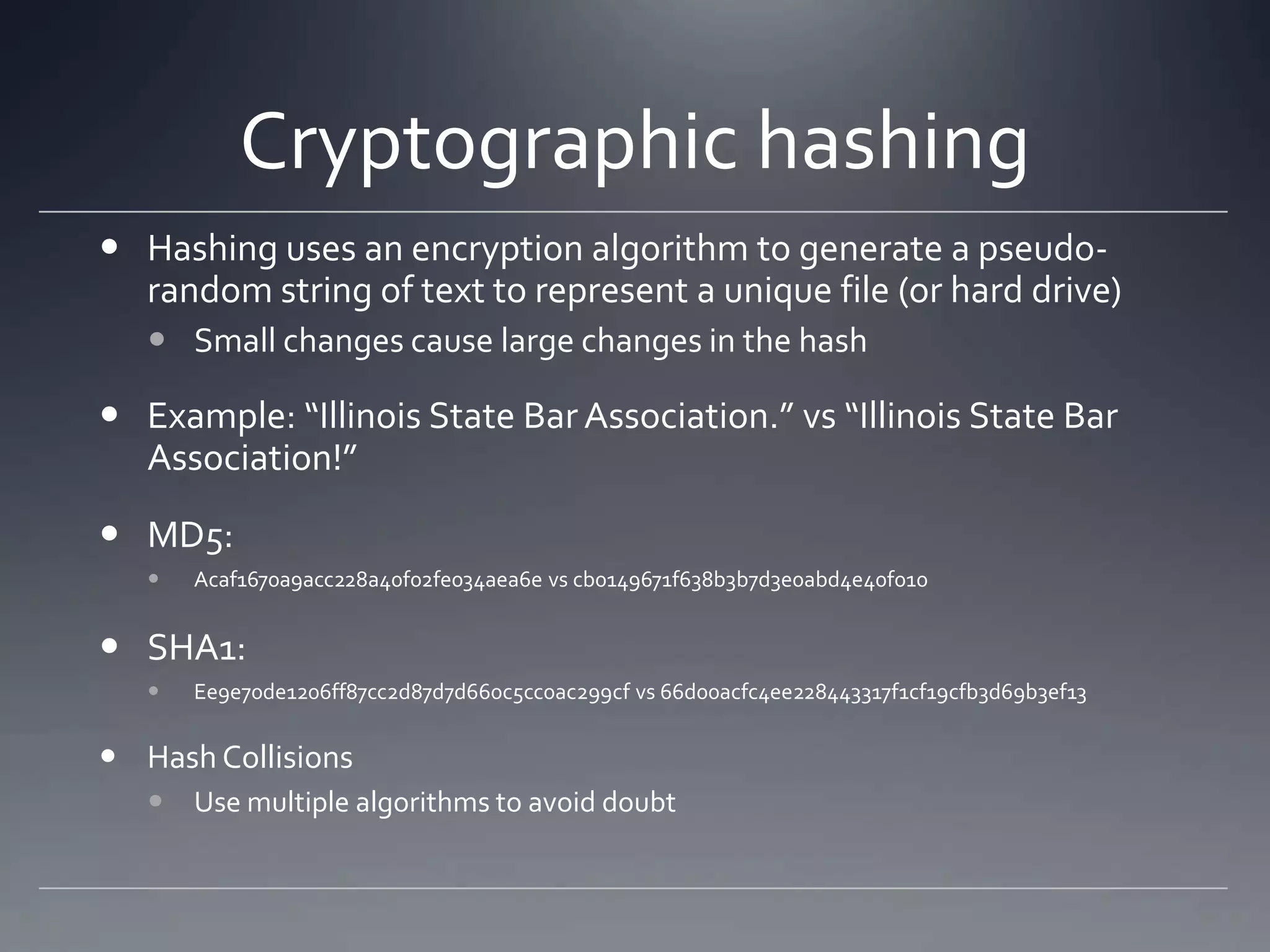
The document outlines topics related to computer forensics including types of computer crimes, incident response versus computer forensics, laws related to the field, challenges with prosecution, key aspects of digital evidence like chain of custody and integrity, methods of data acquisition from networks, memory, hard drives and logs, and considerations for courtroom presentation.

















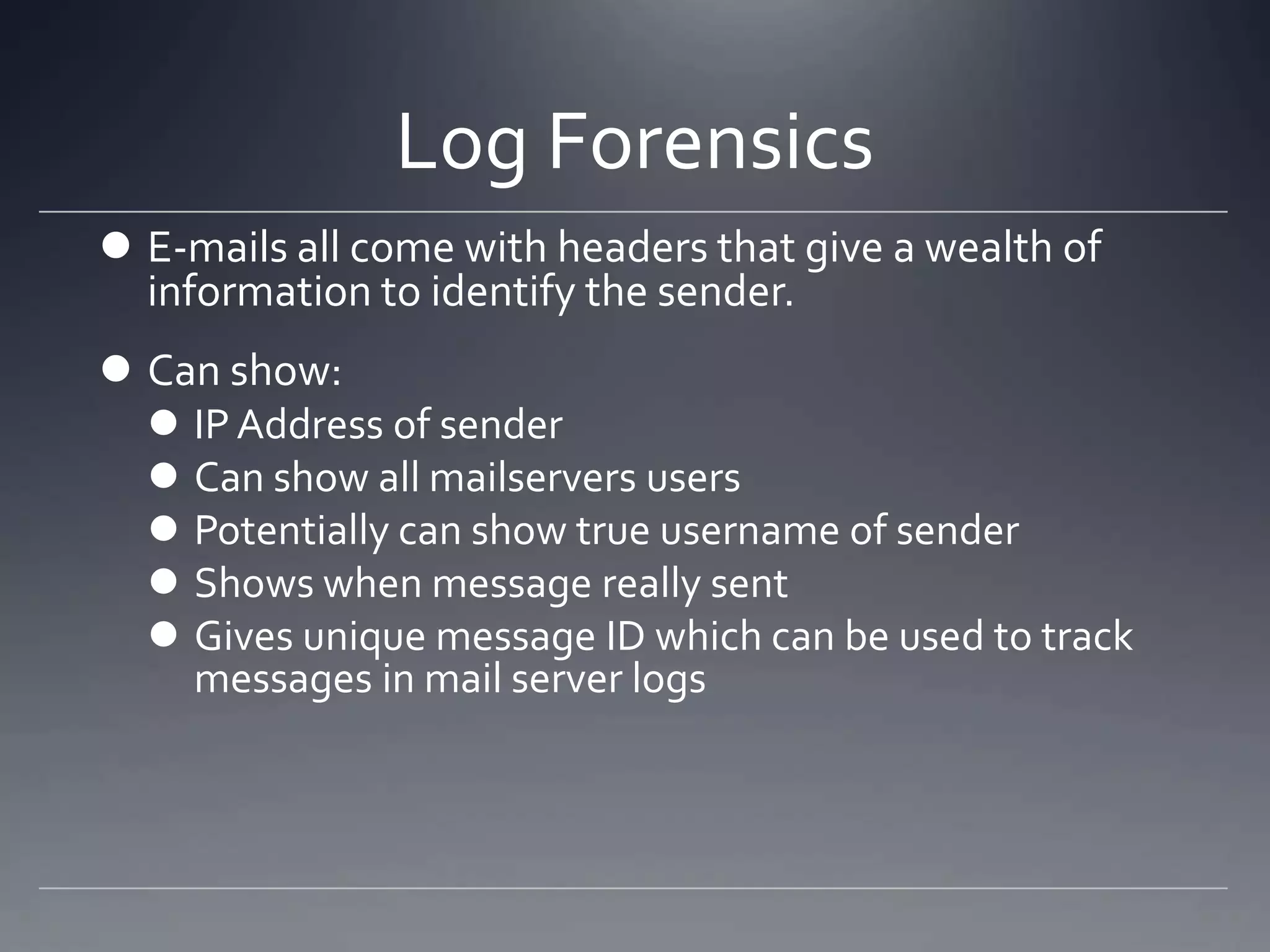
![E-mail Headers Example
Return-path:dbernardi@frontier.com
Envelope-to: jcb@bambenekconsulting.com
Delivery-date: Wed, 03 Aug 2011 12:06:16 -0500
Received: from out01.dlls.pa.frontiernet.net ([199.224.80.228]) by chicago.bambenekconsulting.com with esmtp (Exim 4.69)
(envelope-from <dbernardi@frontier.com>) id 1Qoetc-0001aE-01 for jcb@bambenekconsulting.com; Wed, 03 Aug 2011
12:06:16 -0500
X-IronPort-Anti-Spam-Filtered: true
X-IronPort-Anti-Spam-Result:
Av8EAB1/OU4yLK7Y/2dsb2JhbAA/Aw6CP5cljW6COAEFCCACAz4ODQMCDQoBNwIXPgEBBAEdyQ2DPoMEBIdam05V
X-IronPort-AV: E=Sophos;i="4.67,311,1309737600"; d="xml'?rels'?docx'72,48?scan'72,48,208,217,72,48";a="146462351"
Received: from relay01.dlls.pa.frontiernet.net ([199.224.80.244]) by out01.dlls.pa.frontiernet.net with ESMTP; 03 Aug 2011
17:06:14 +0000 X-Previous-IP: 50.44.174.216
Received: from BernardiHome (unknown[50.44.174.216]) by relay01.dlls.pa.frontiernet.net (Postfix) with ESMTPA id
B4A0930C095; Wed, 3 Aug 2011 17:06:12 +0000 (UTC)
From: "don bernardi" <dbernardi@frontier.com>
To: "'Stephanie Beine'" <sbeine@genetictechnologies.com>, "'Rich Kaplan'"
<kapla111@umn.edu>, <experts@forensicDJS.com>, <jharman@genetictechnologies.com>, <jcb@bambenekconsulting.com
>
Cc: "'Jeremy Karlin'" <jkarlin@alcornkarlin.com>, "'Stephen M Komie'" <stephen_m_komie@komie-and-
associates.com>, "'John J. Rekowski'" <jjrekowski@co.madison.il.us>, <rja@dupageco.org>, "'Tiffany Bordenkircher'"
<tbordenkircher@isba.org>, <jheaton@isba.org>
References: <4F46AA8D5DFD674586F982B62079DD43059204B612@34093-MBX-C01.mex07a.mlsrvr.com>
In-Reply-To:<4F46AA8D5DFD674586F982B62079DD43059204B612@34093-MBX-C01.mex07a.mlsrvr.com>
Subject: nov 18,2011 ISBA seminar
Date: Wed, 3 Aug 2011 12:06:07 -0500
Message-ID: <005c01cc51ff$a43b93e0$ecb2bba0$@com>
MIME-Version:1.0 Content-Type: multipart/mixed; boundary="----=_NextPart_000_005D_01CC51D5.BB658BE0"
X-Mailer: Microsoft Office Outlook 12.0 Thread-Index: AcwOY1oNT74/g+iGTFi9Z6maxNsonhDmfBEw
Content-Language: en-us](https://image.slidesharecdn.com/isba-130816143950-phpapp01/75/Cybercrime-Computer-Forensics-ISBA-Master-Series-CLE-Nov-18-2011-23-2048.jpg)