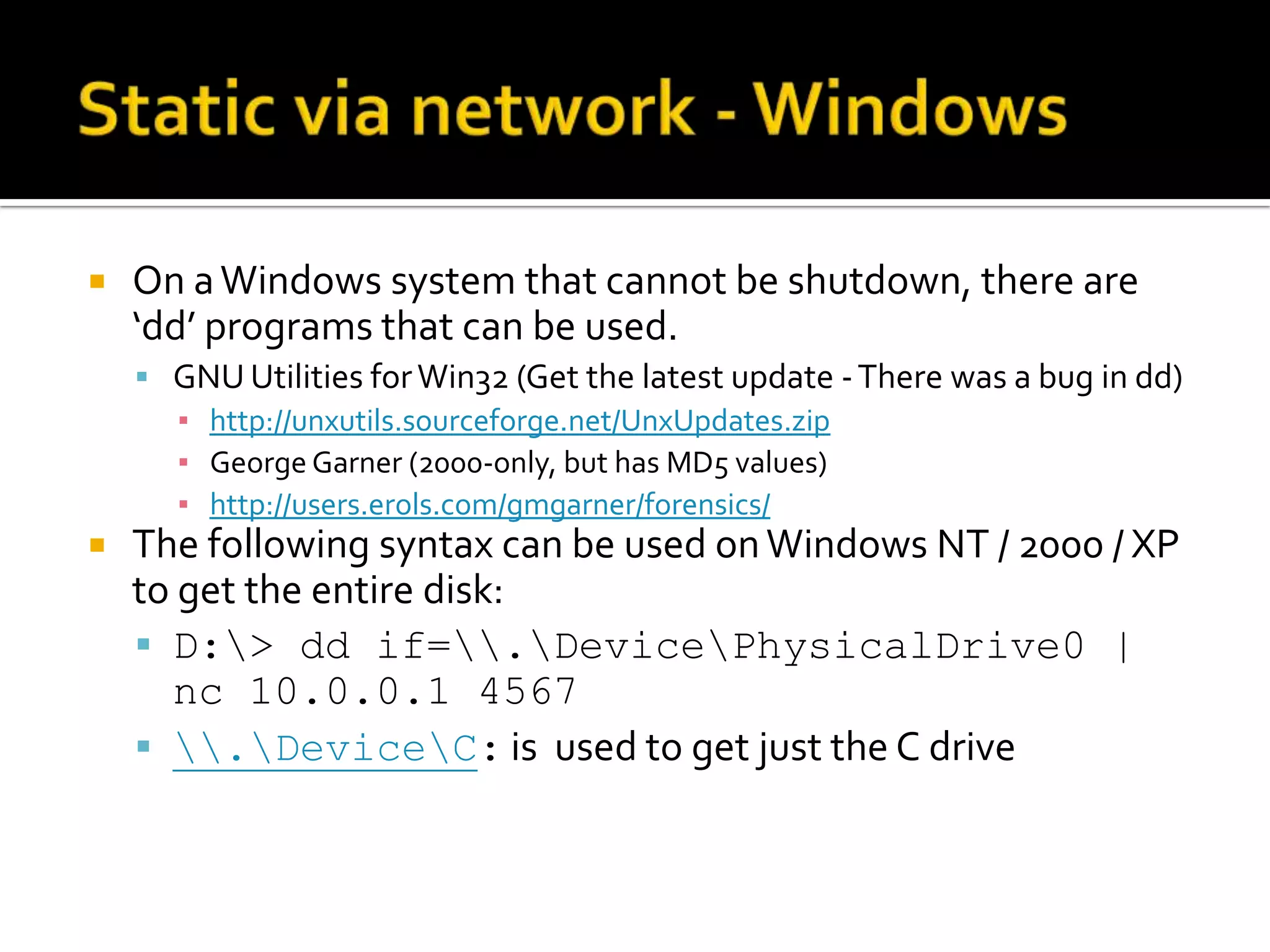
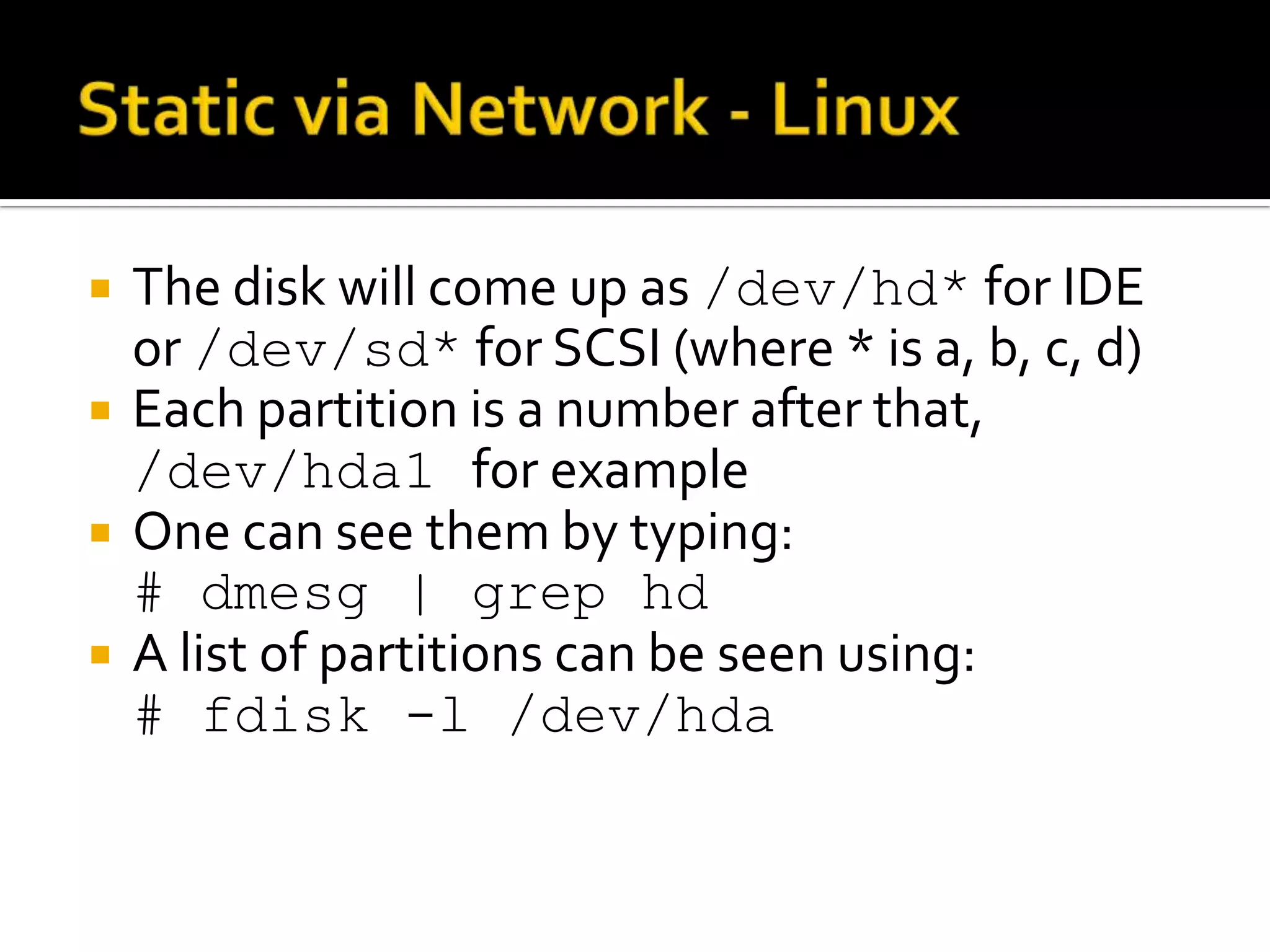
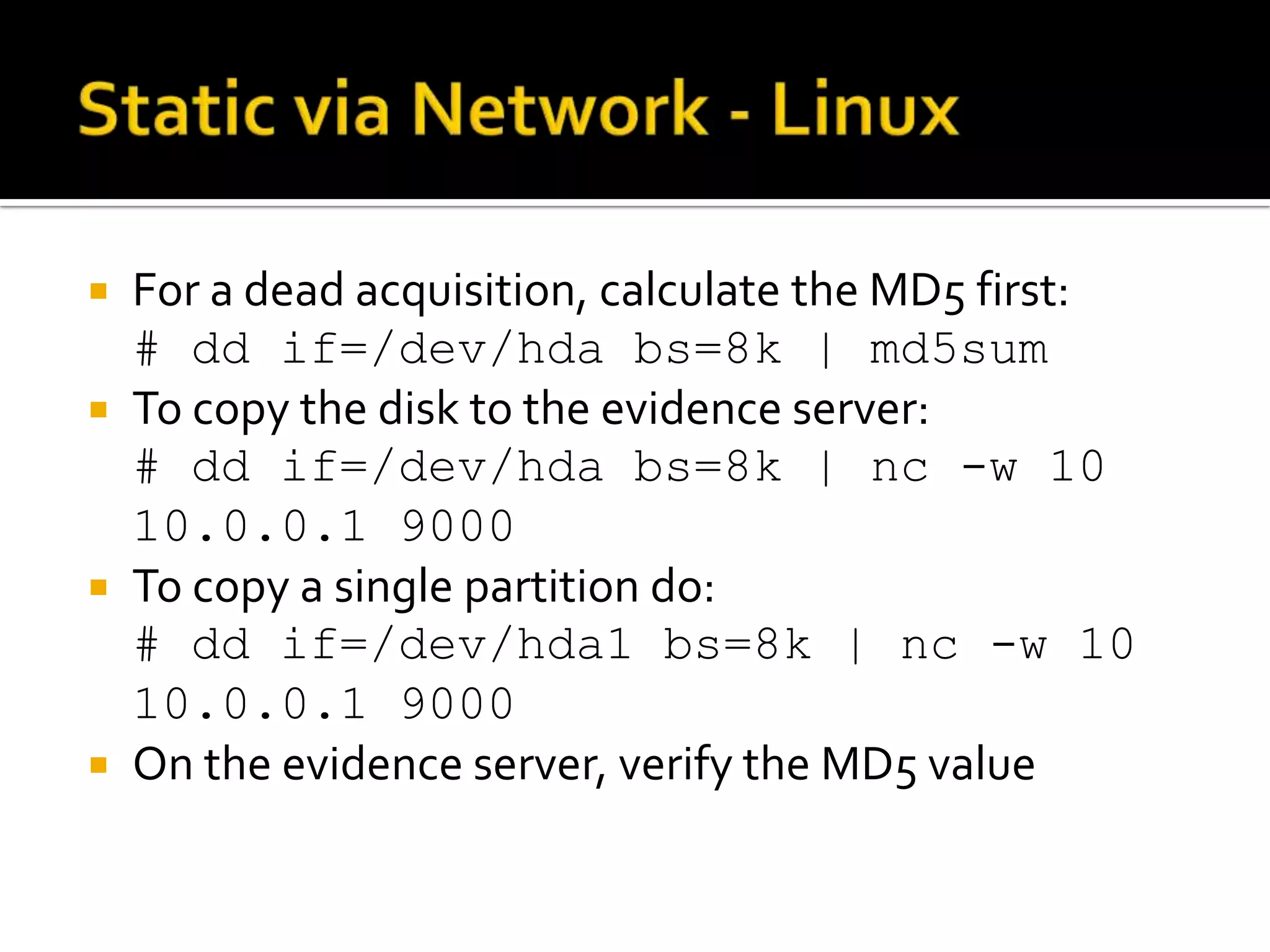
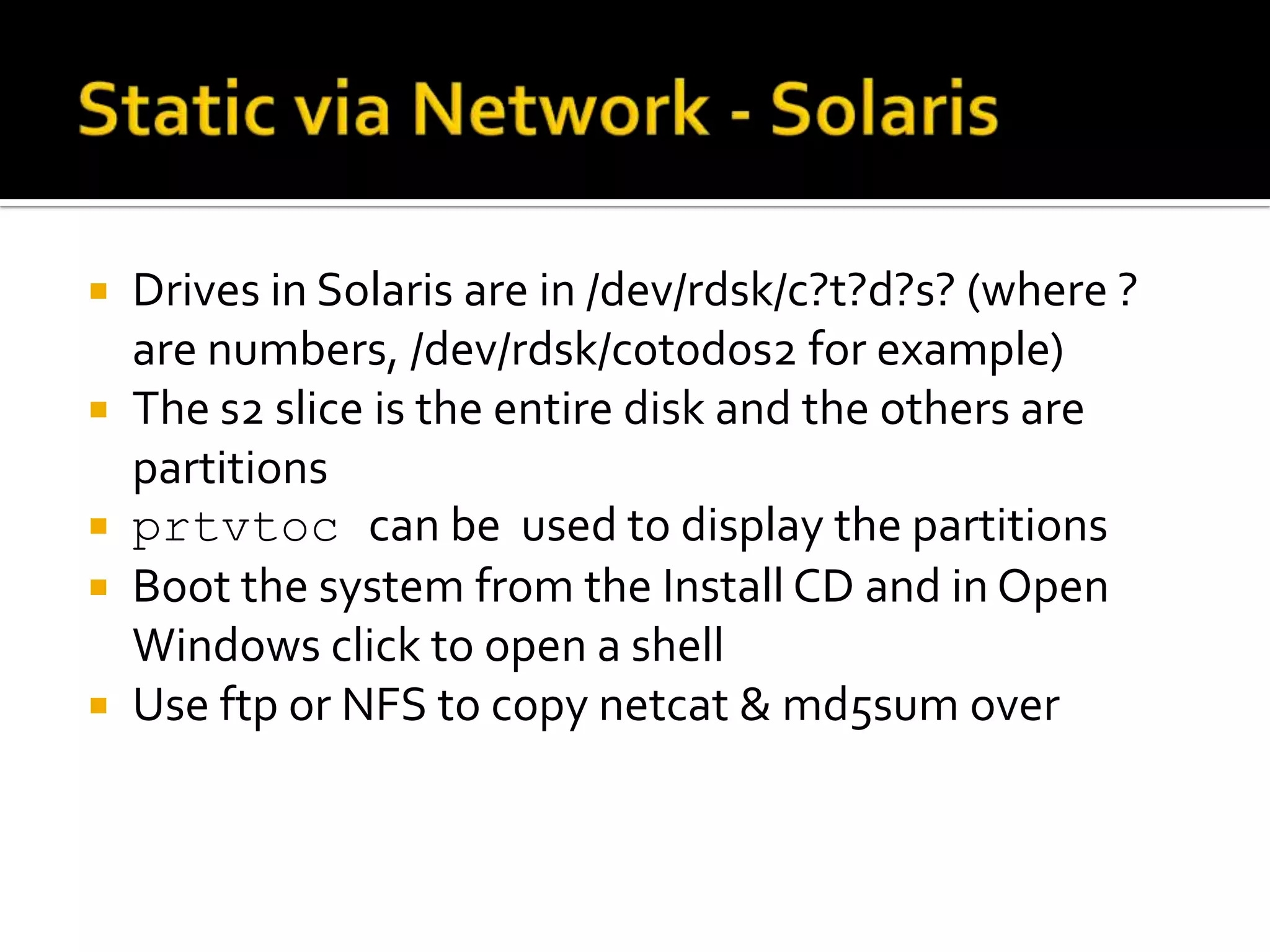
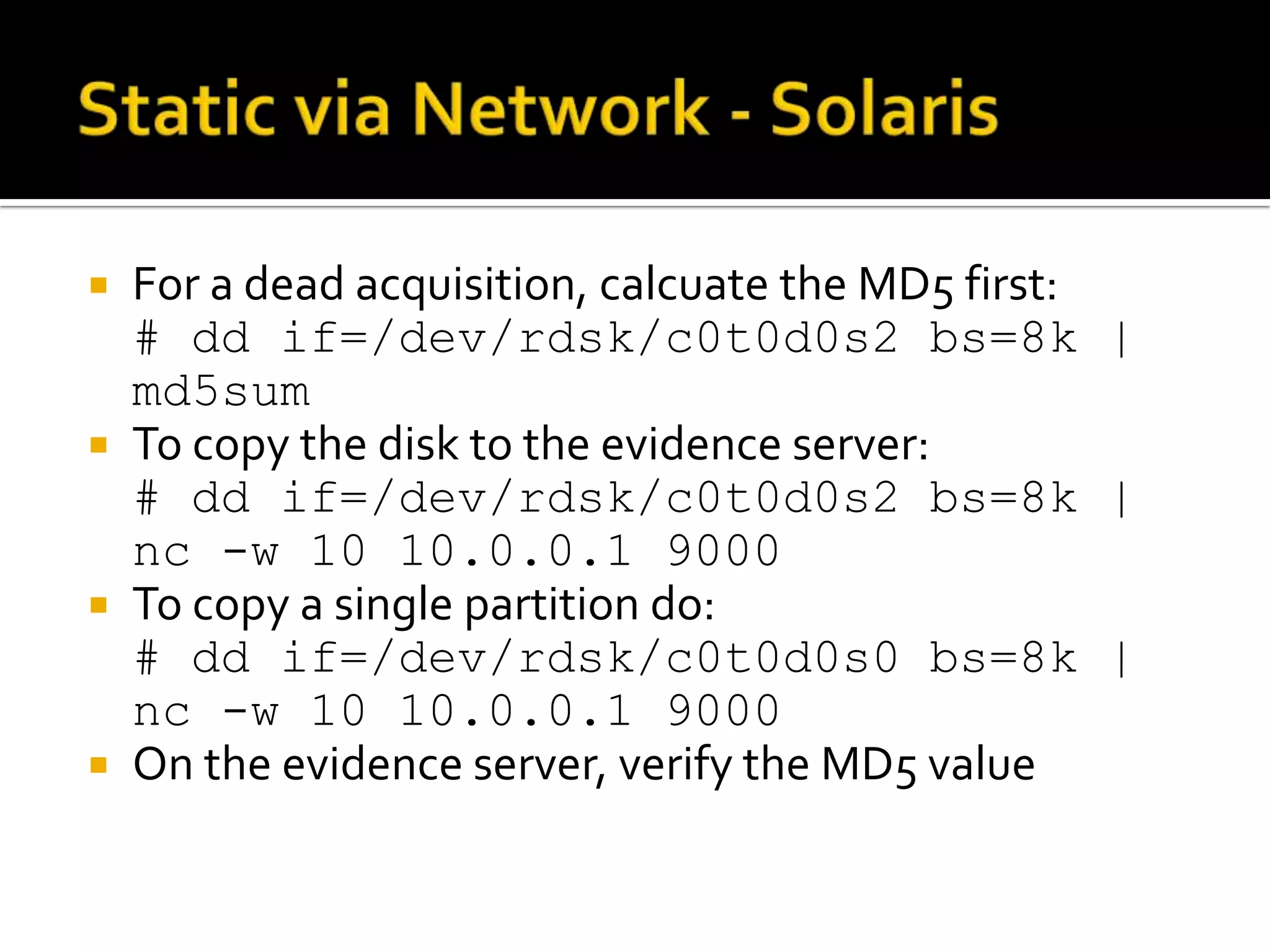
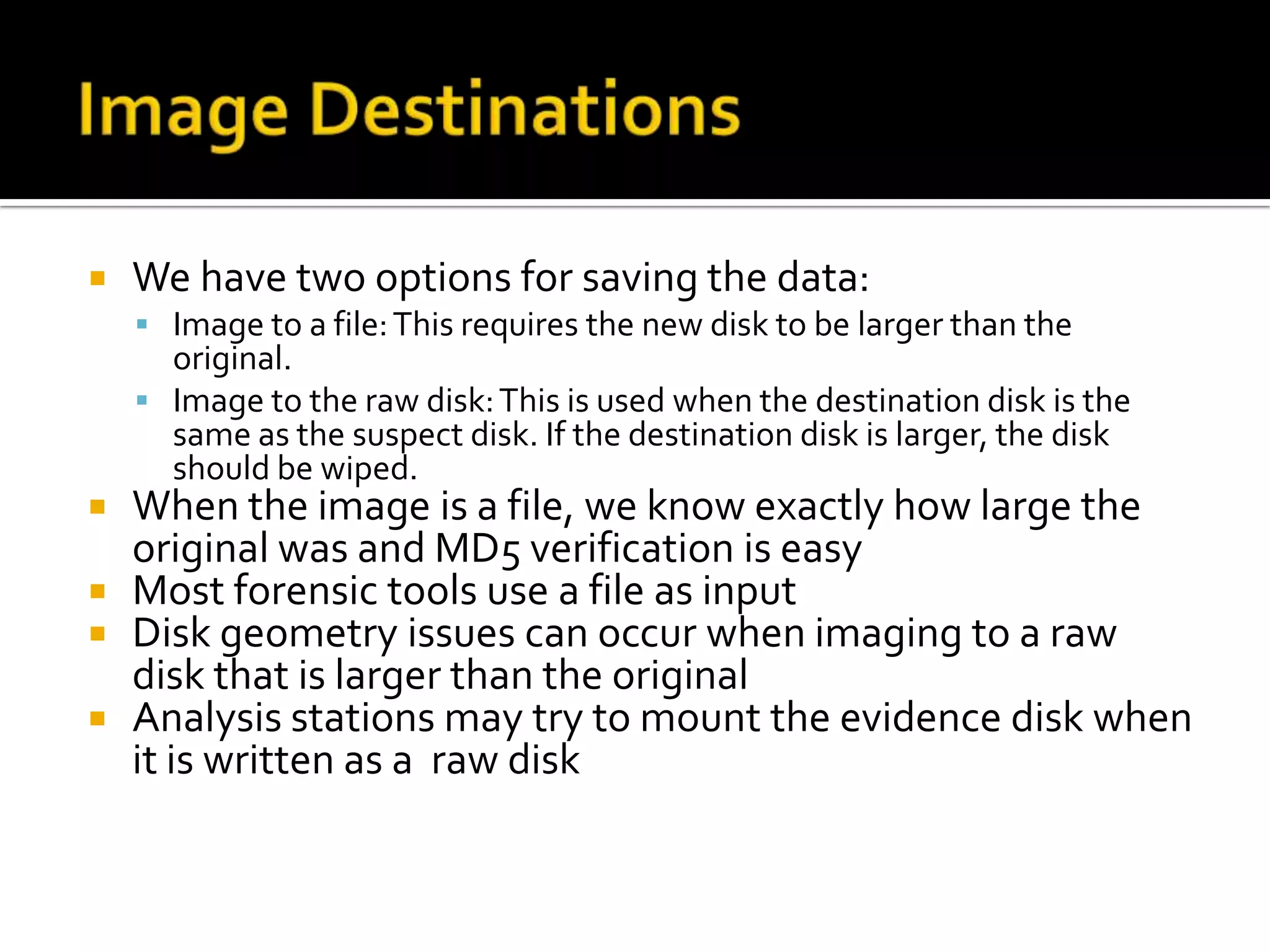
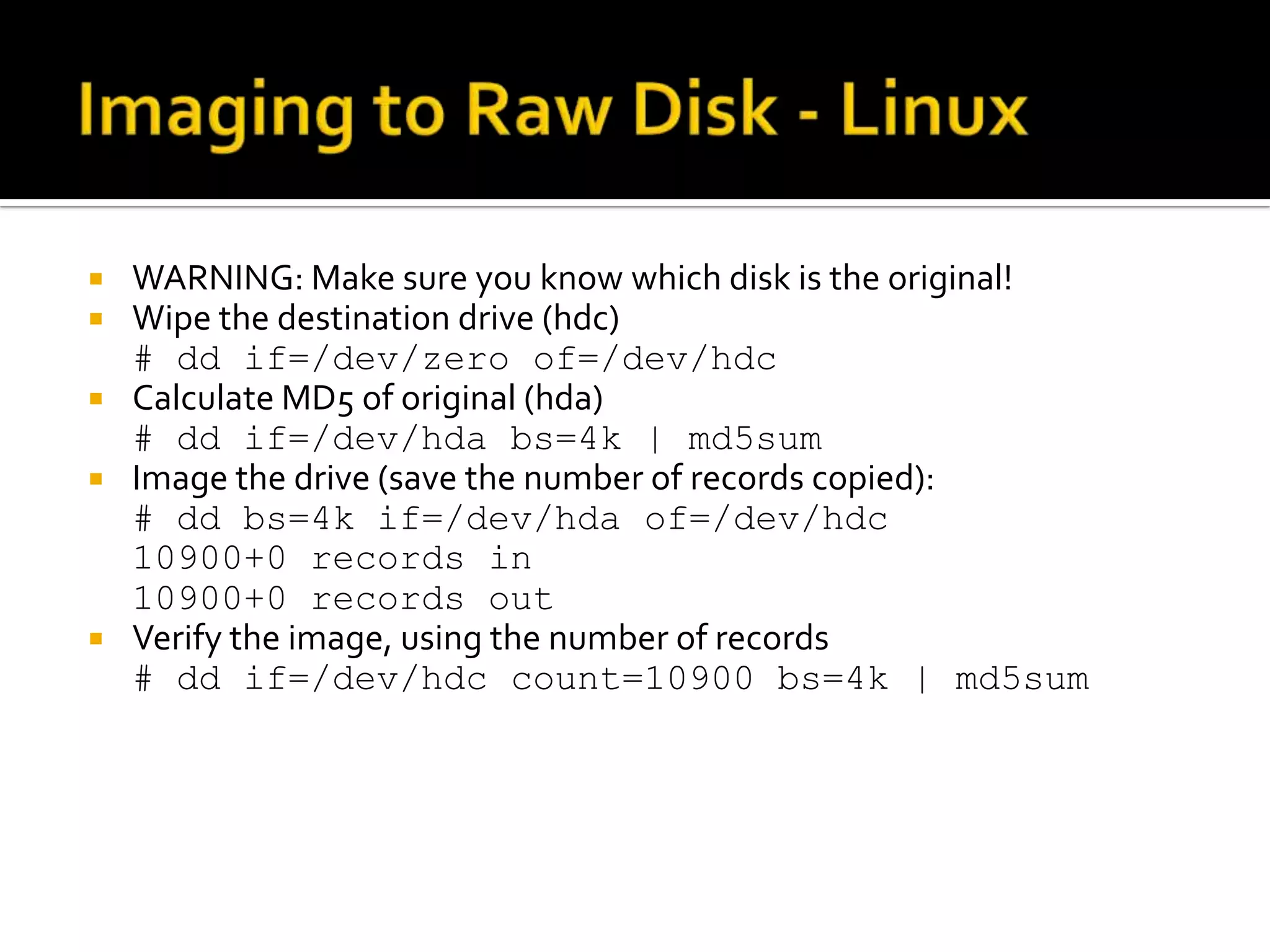
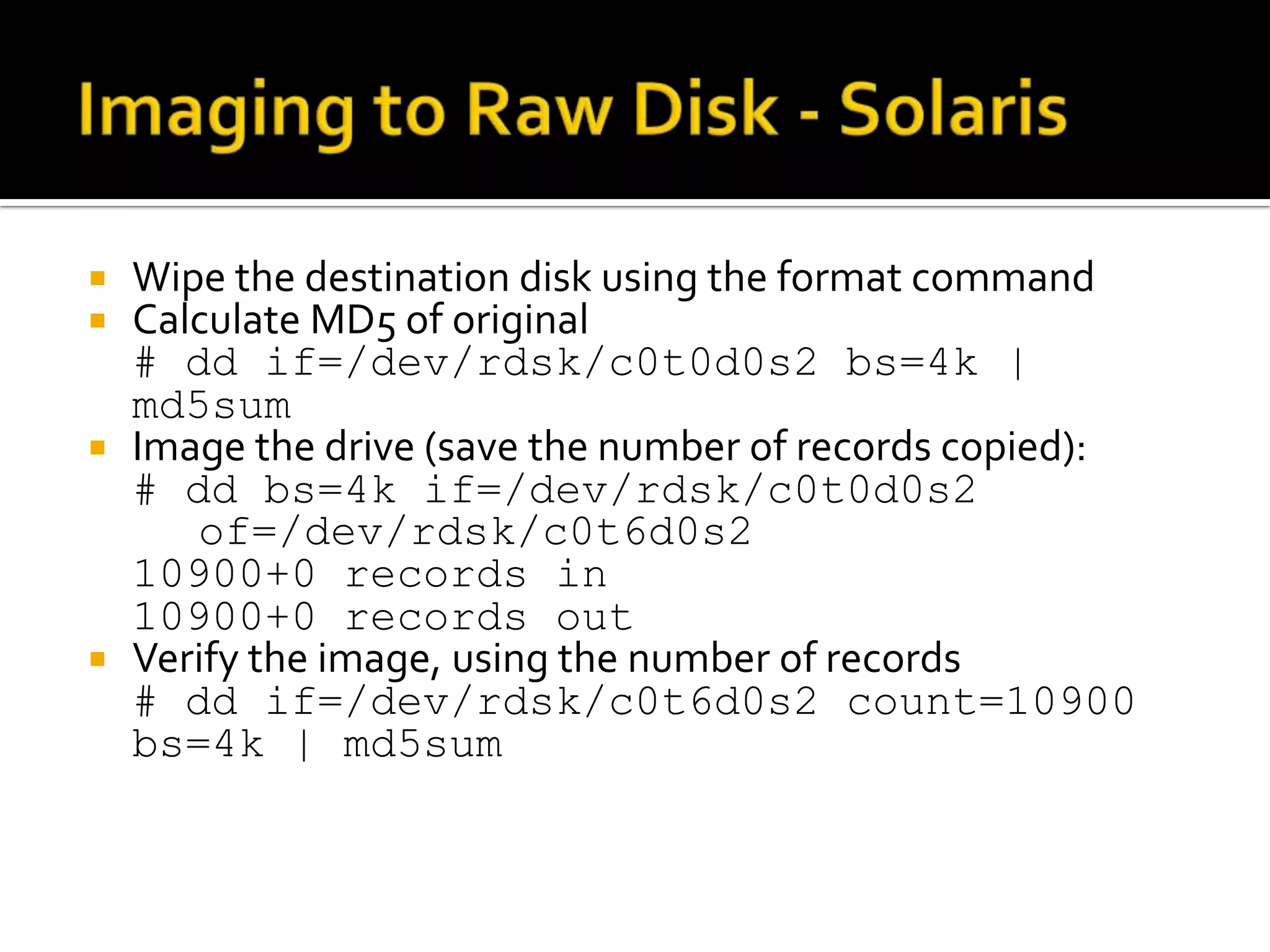
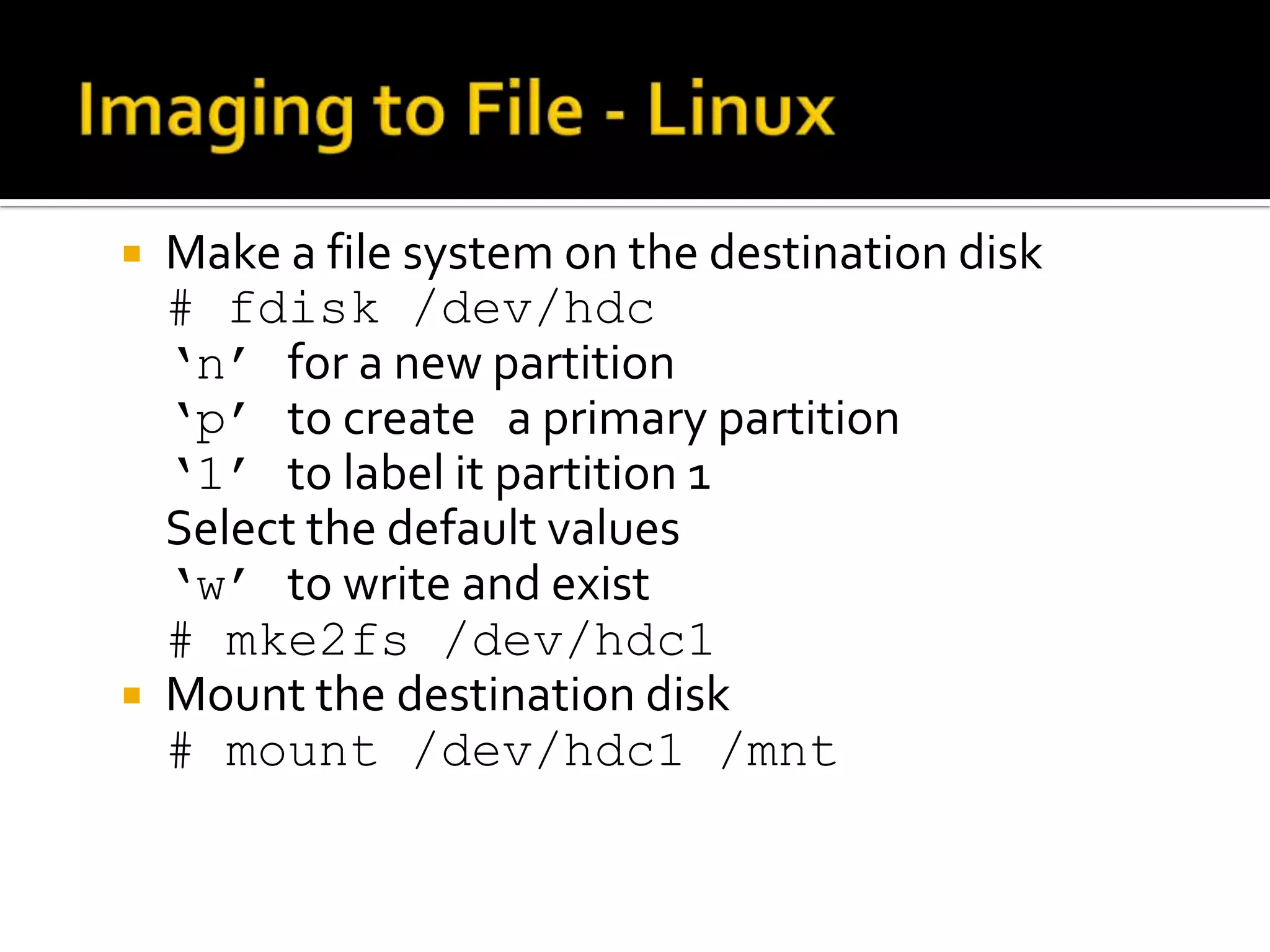
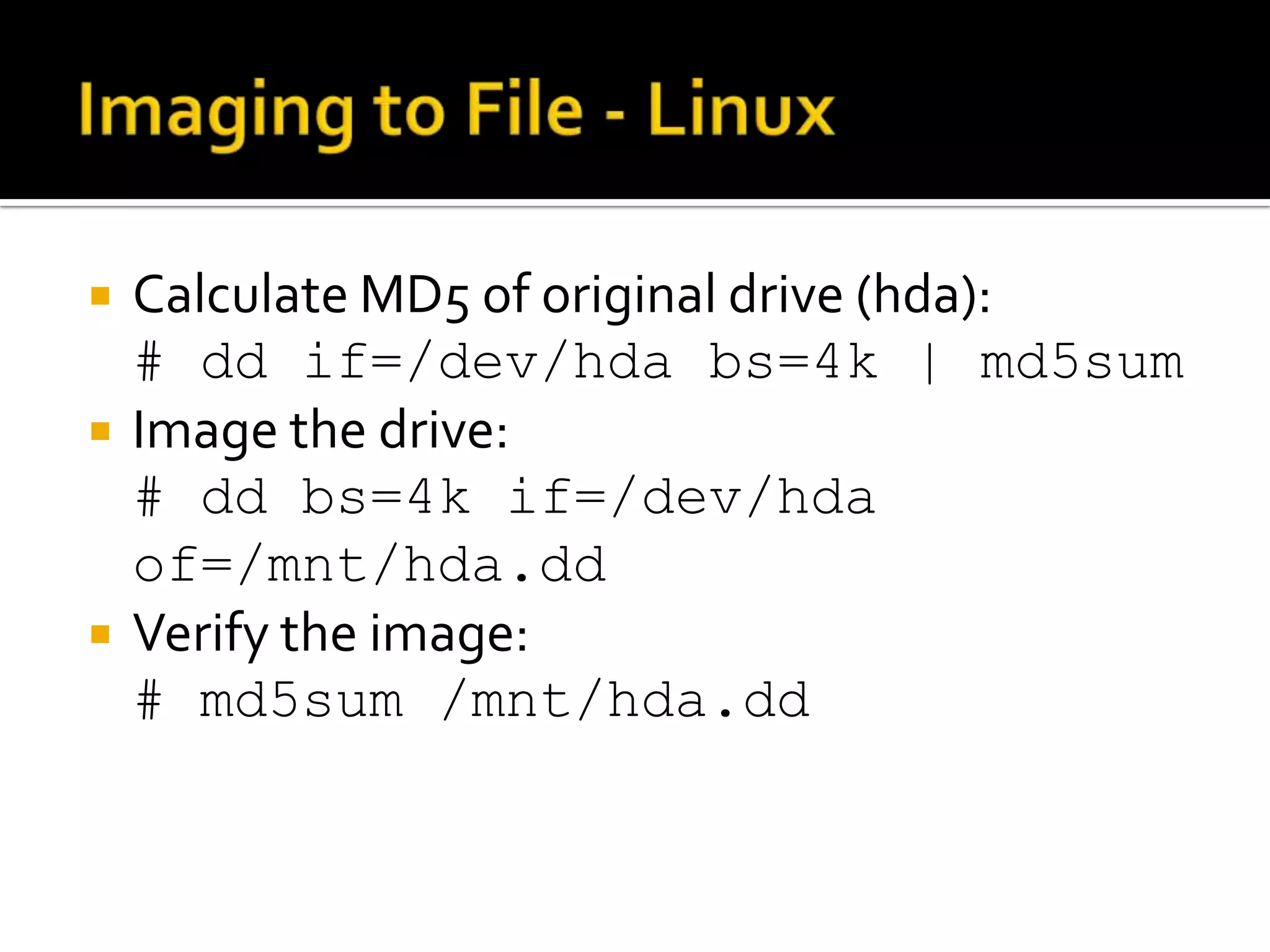
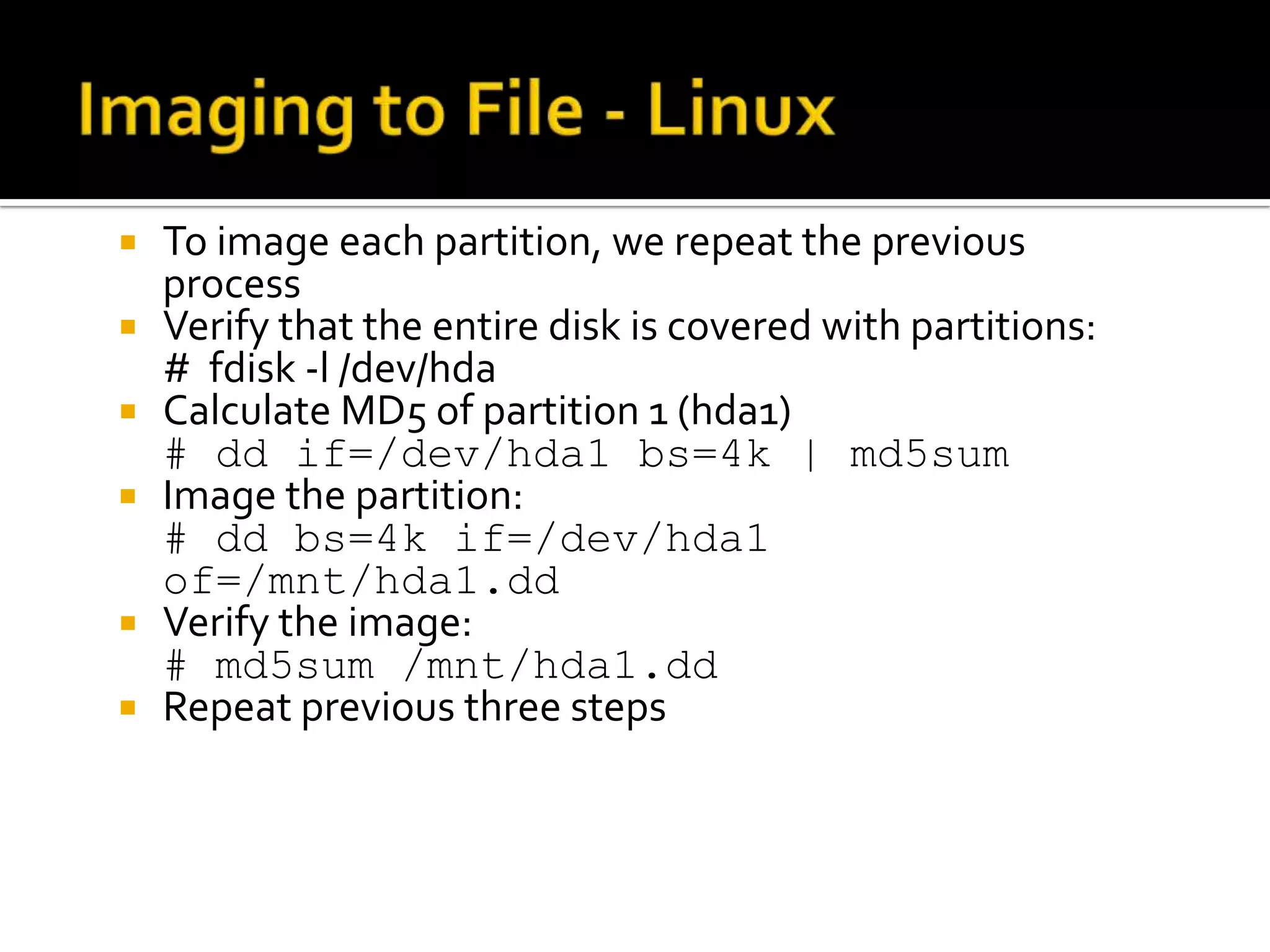
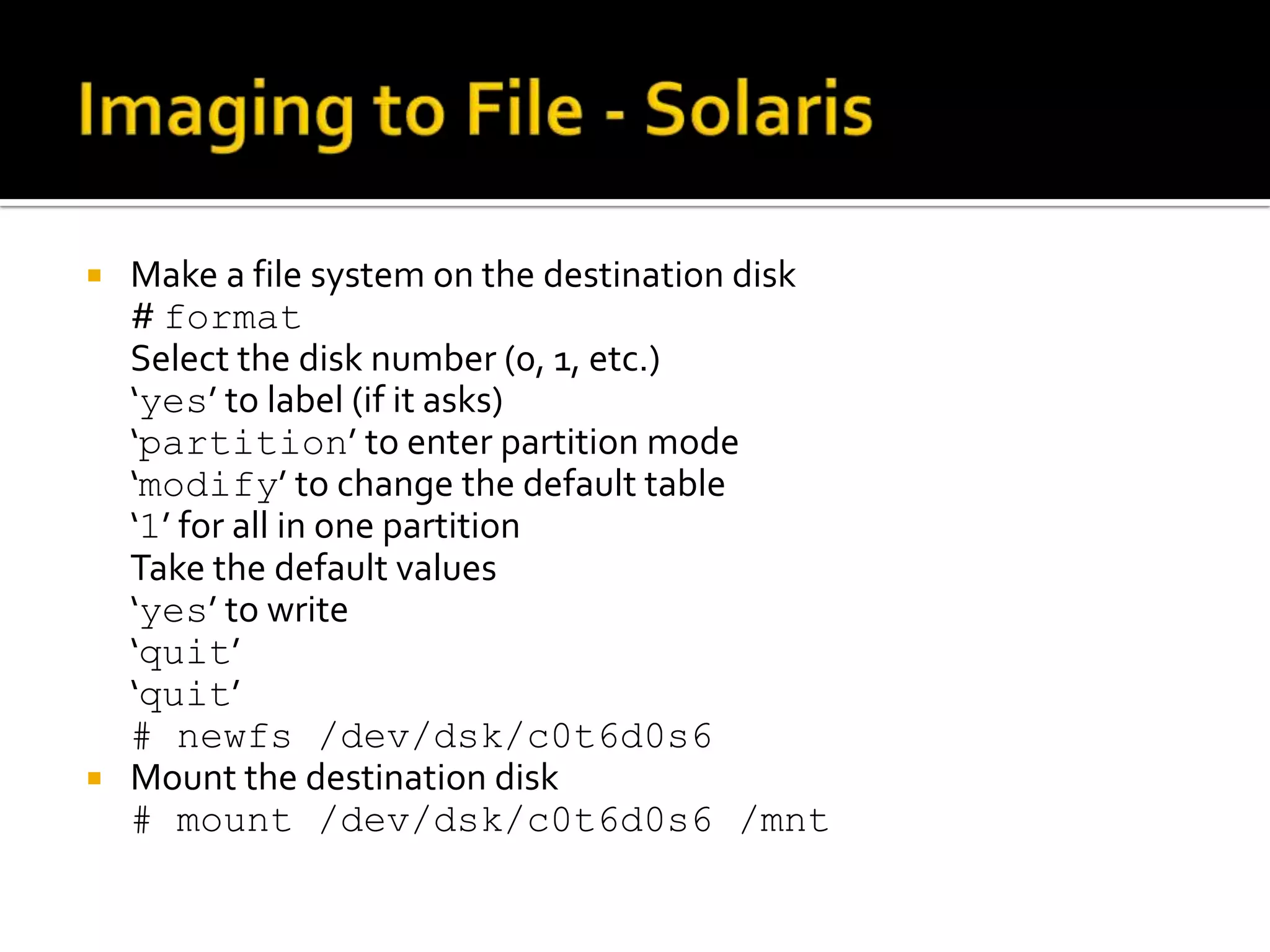
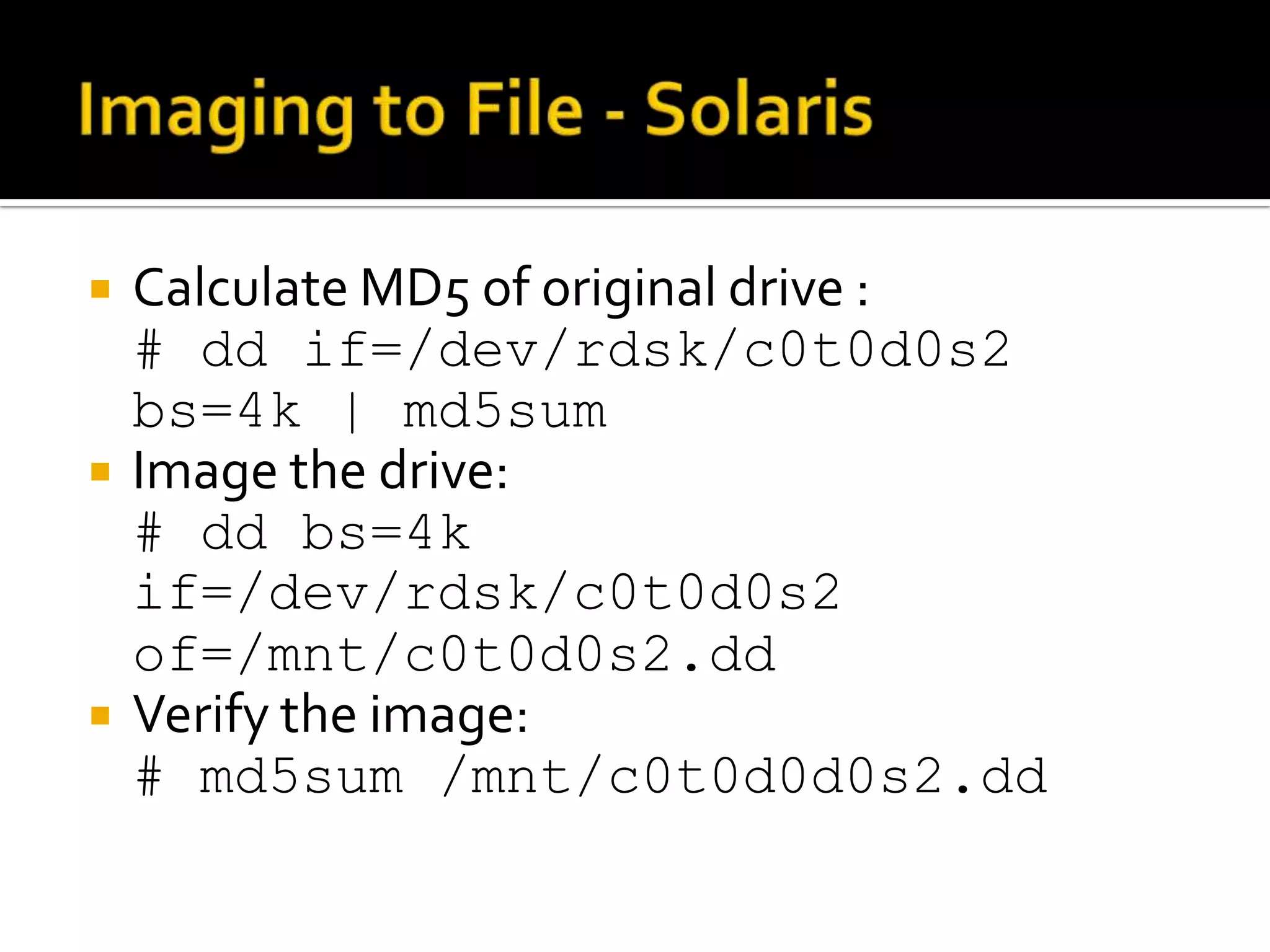
The document discusses static data acquisition techniques, focusing on hard drive data collection methods and the importance of preserving data integrity through proper imaging and copying procedures. It outlines various methods for acquiring hard drives, including live and dead acquisitions, and emphasizes considerations like system access, shutdown protocols, and the selection of tools. The document also highlights tools like 'dd', netcat, and specialized forensic software, while cautioning against potential issues during live acquisitions and the necessity of verifying data integrity using md5 checks.