The document discusses various data hiding techniques used to conceal information, including:
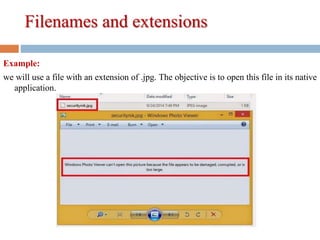
1) Manipulating file attributes like filenames, extensions, and hidden properties.
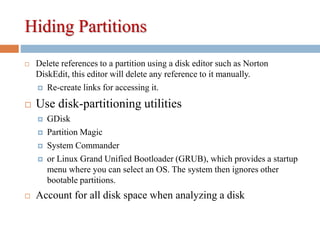
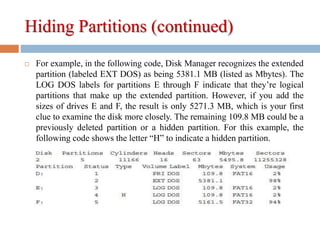
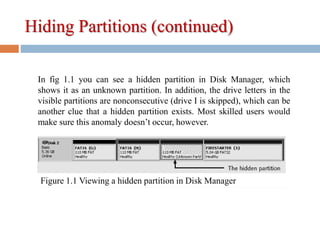
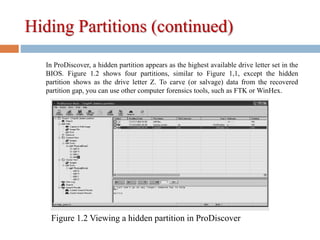
2) Hiding partitions by deleting references in disk editors or using partition tools.
3) Marking disk clusters as "bad" to hide data in free space.
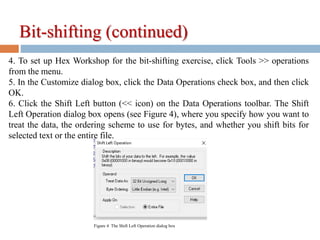
4) Bit-shifting to alter byte values and make files look like executable code.
5) Using steganography tools to hide data within image or text files by inserting digital watermarks.