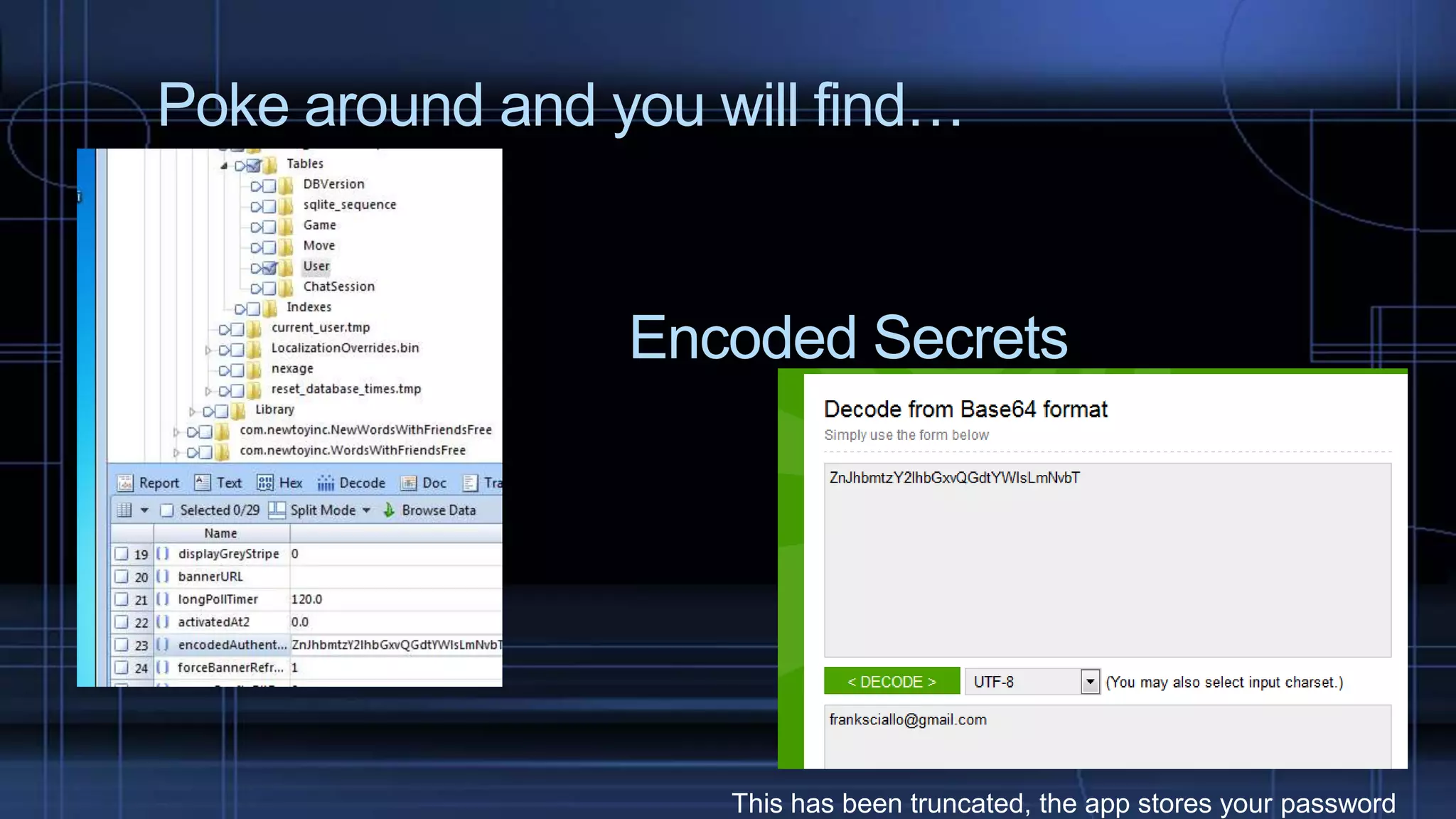
This document discusses mobile device forensics. It explains that mobile devices store a variety of personal information, including calls, texts, emails, photos and more. It also outlines the challenges of investigating mobile devices and describes the components of mobile devices like the IMEI, SIM card, and memory. The document provides details on acquiring data from mobile devices, including identifying the device, isolating it to prevent remote wiping, and extracting data from internal memory, SIM cards and external storage.