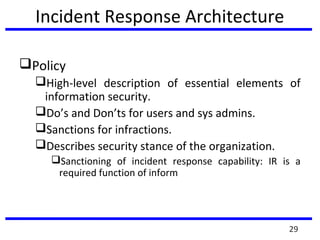
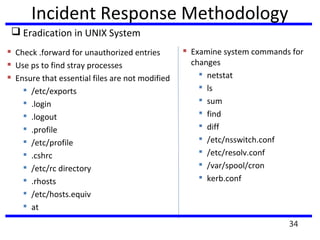
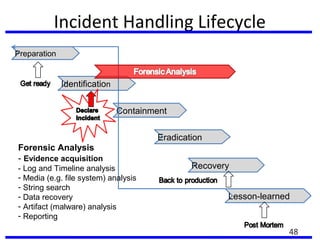
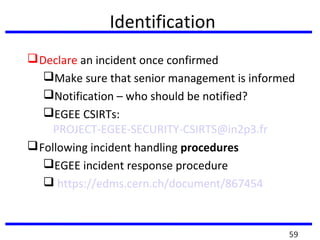
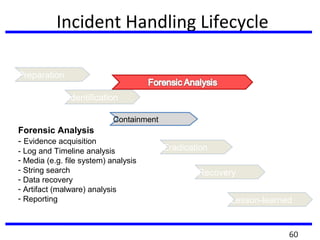
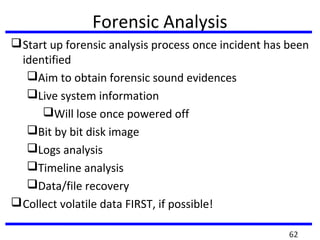
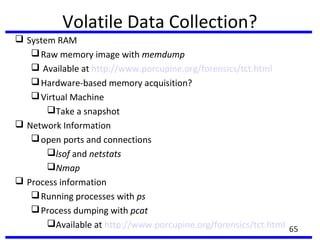
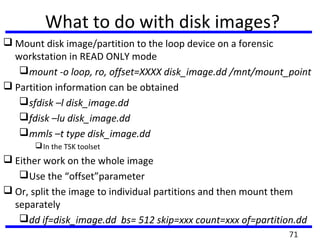
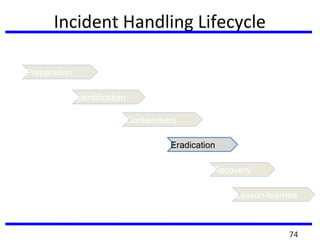
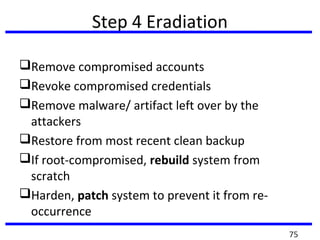
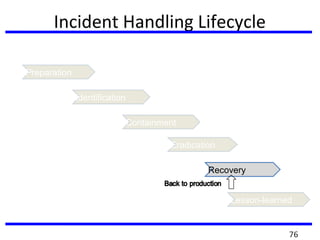
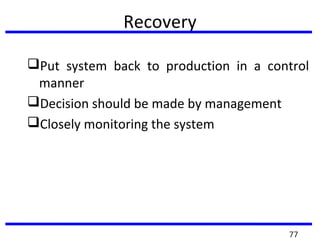
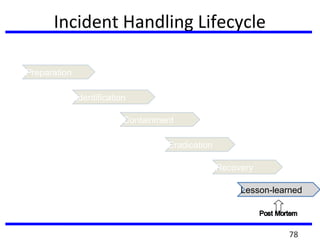
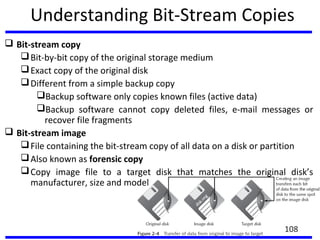
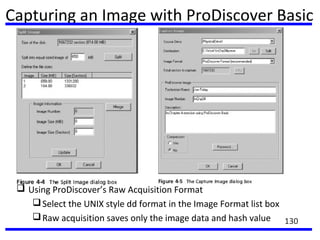
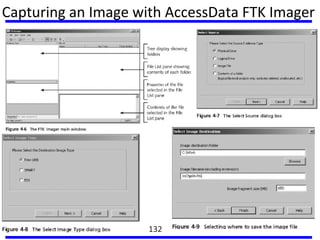
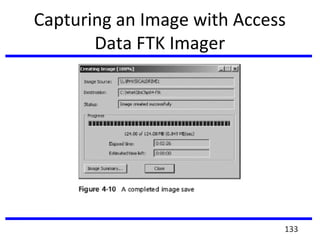
This document summarizes a training program on cyber security that took place from November 19th to December 2nd 2018. It covered topics such as computer forensics and its tools, traditional computer crimes, identity theft and fraud, computer forensics techniques, cyber crimes and how to reduce risks of identity theft. The training discussed investigating computer systems for evidence of crimes and recovering deleted files through data acquisition and forensic analysis.