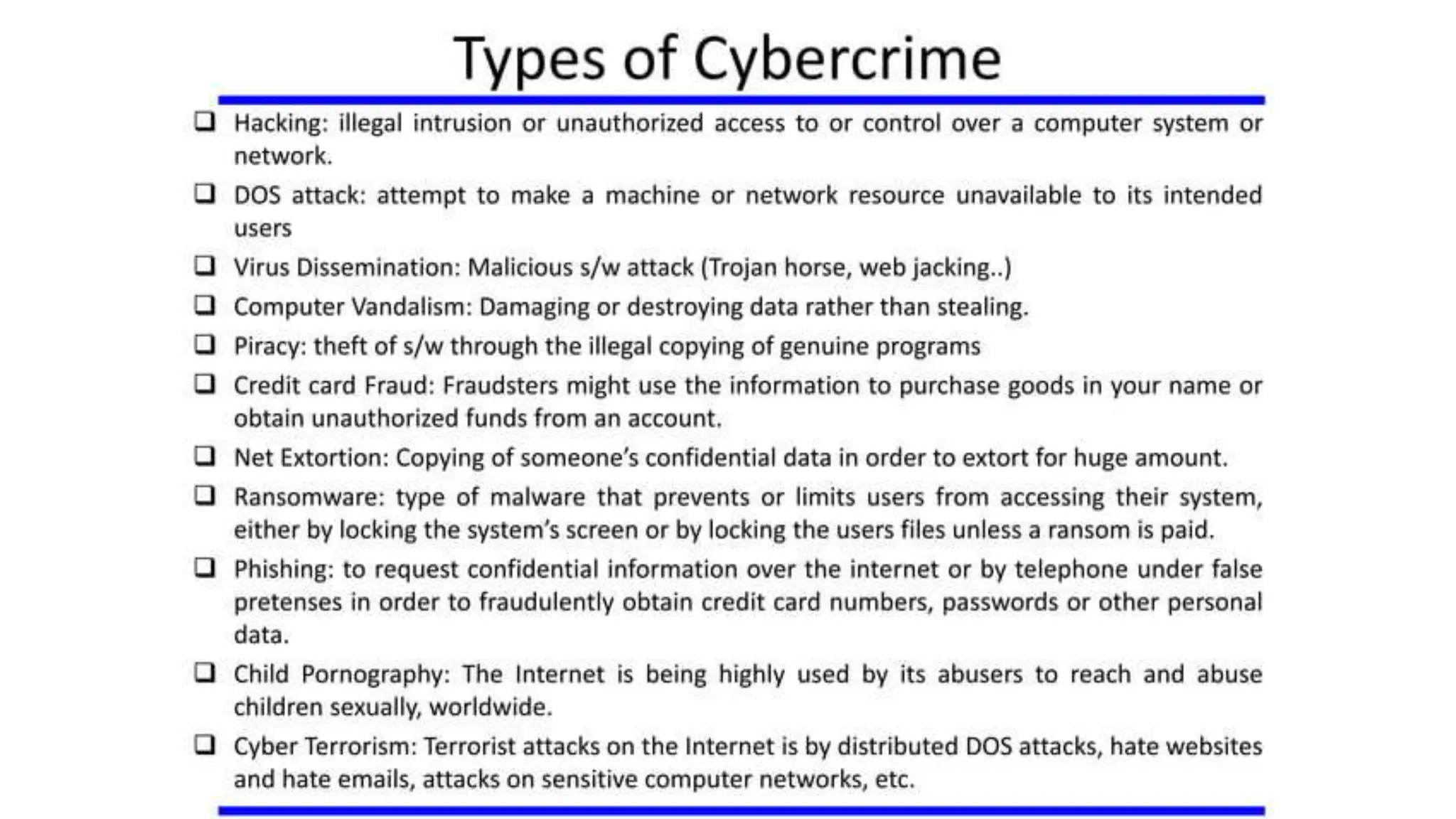
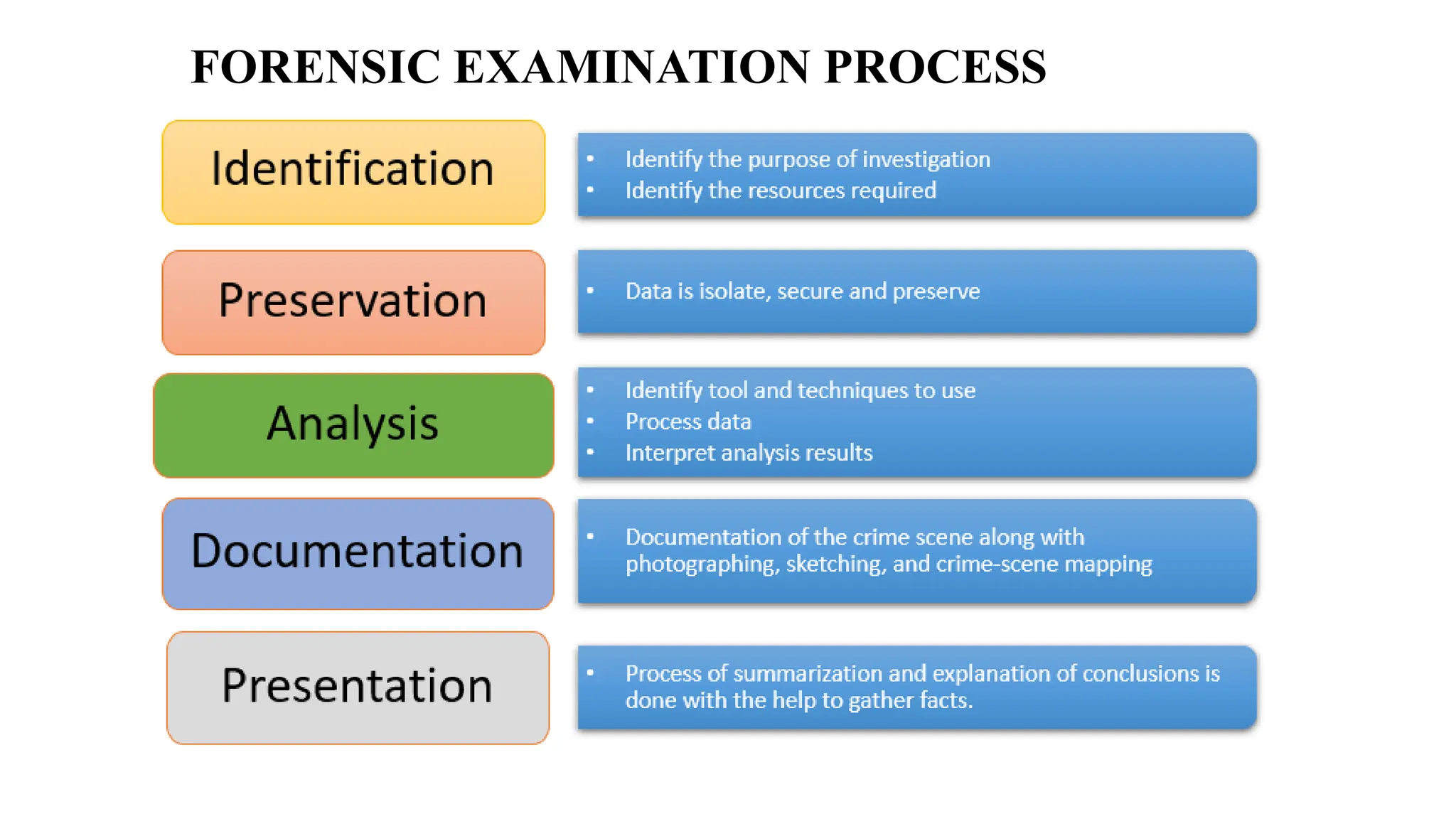
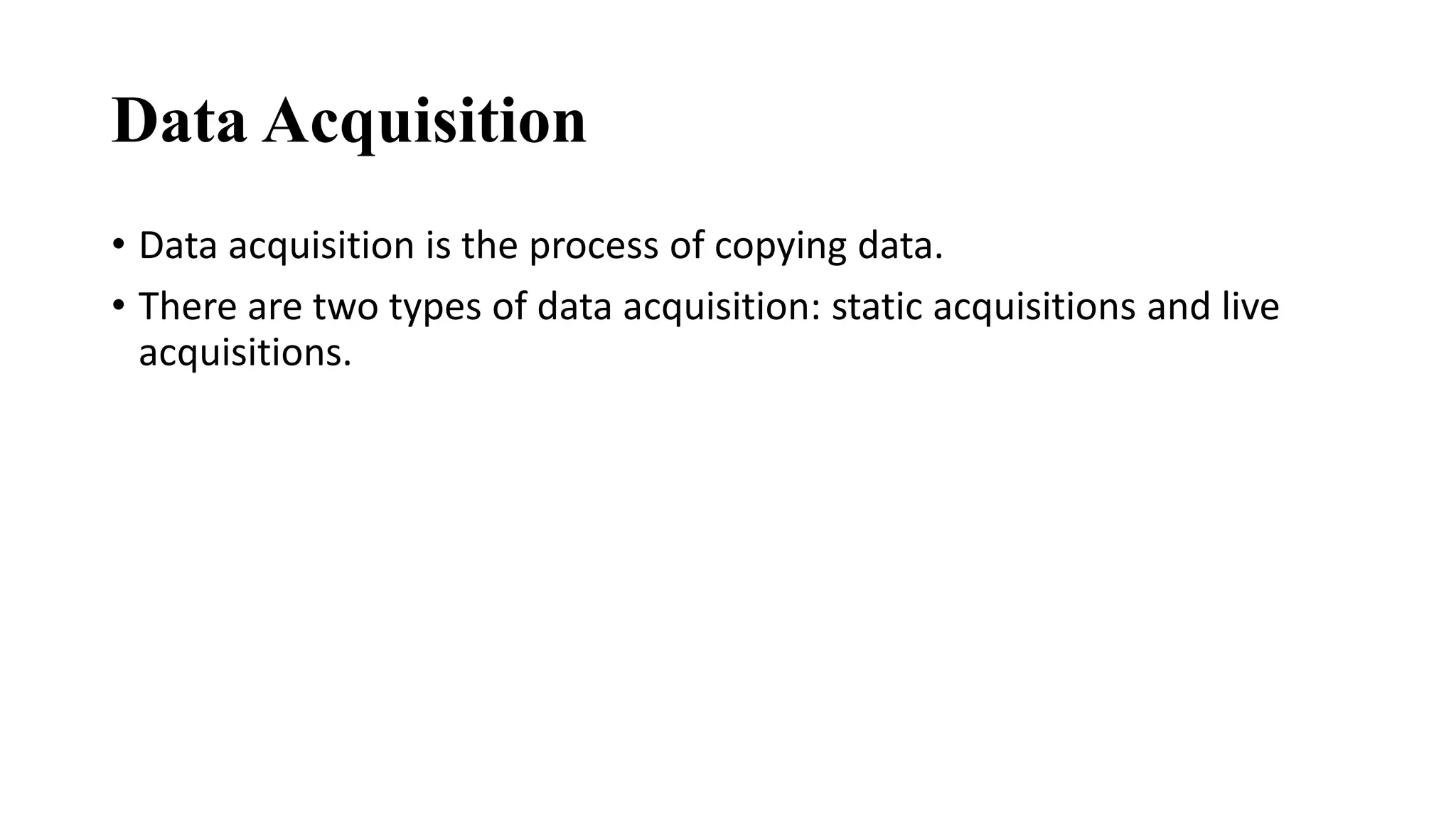
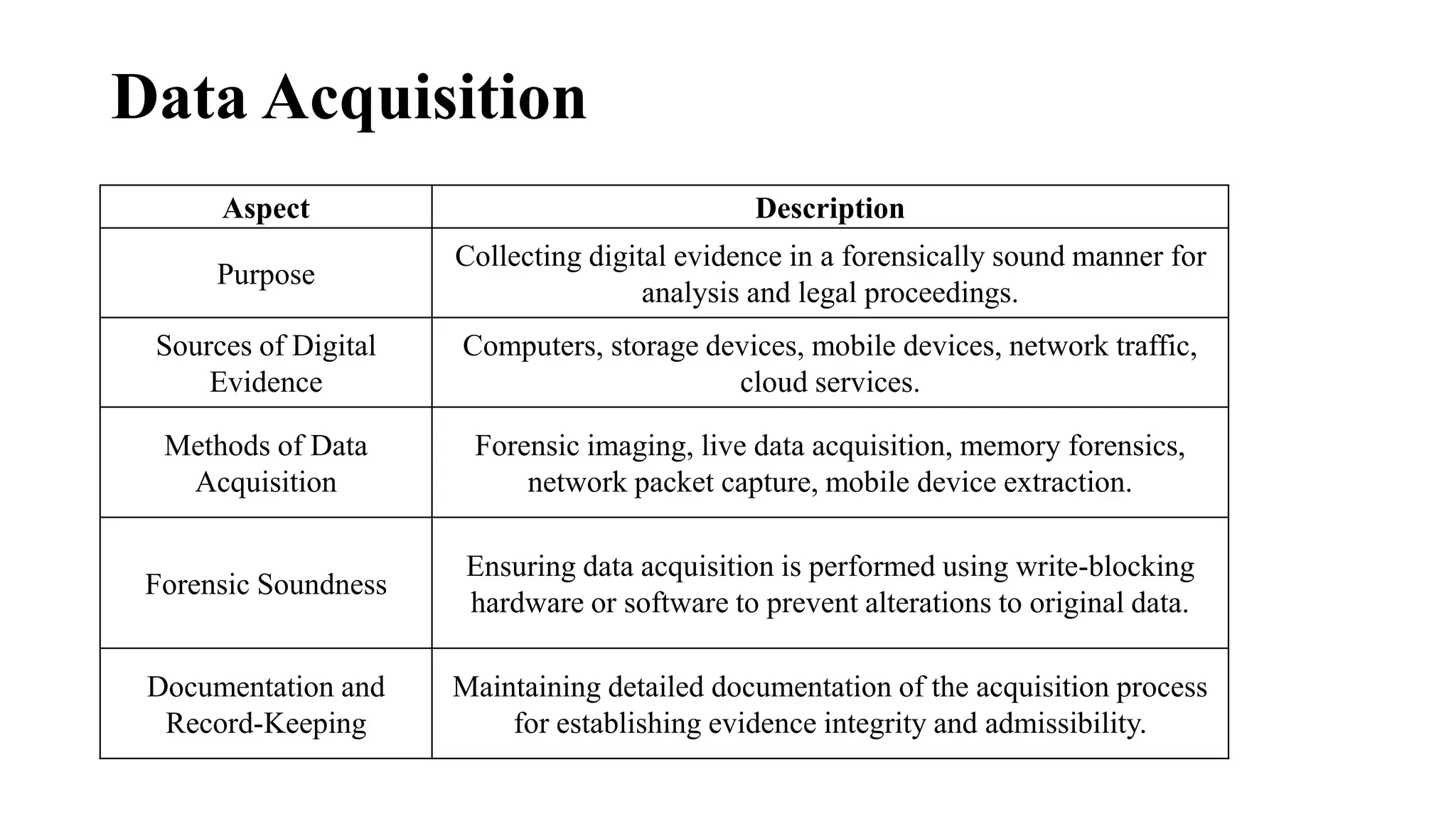
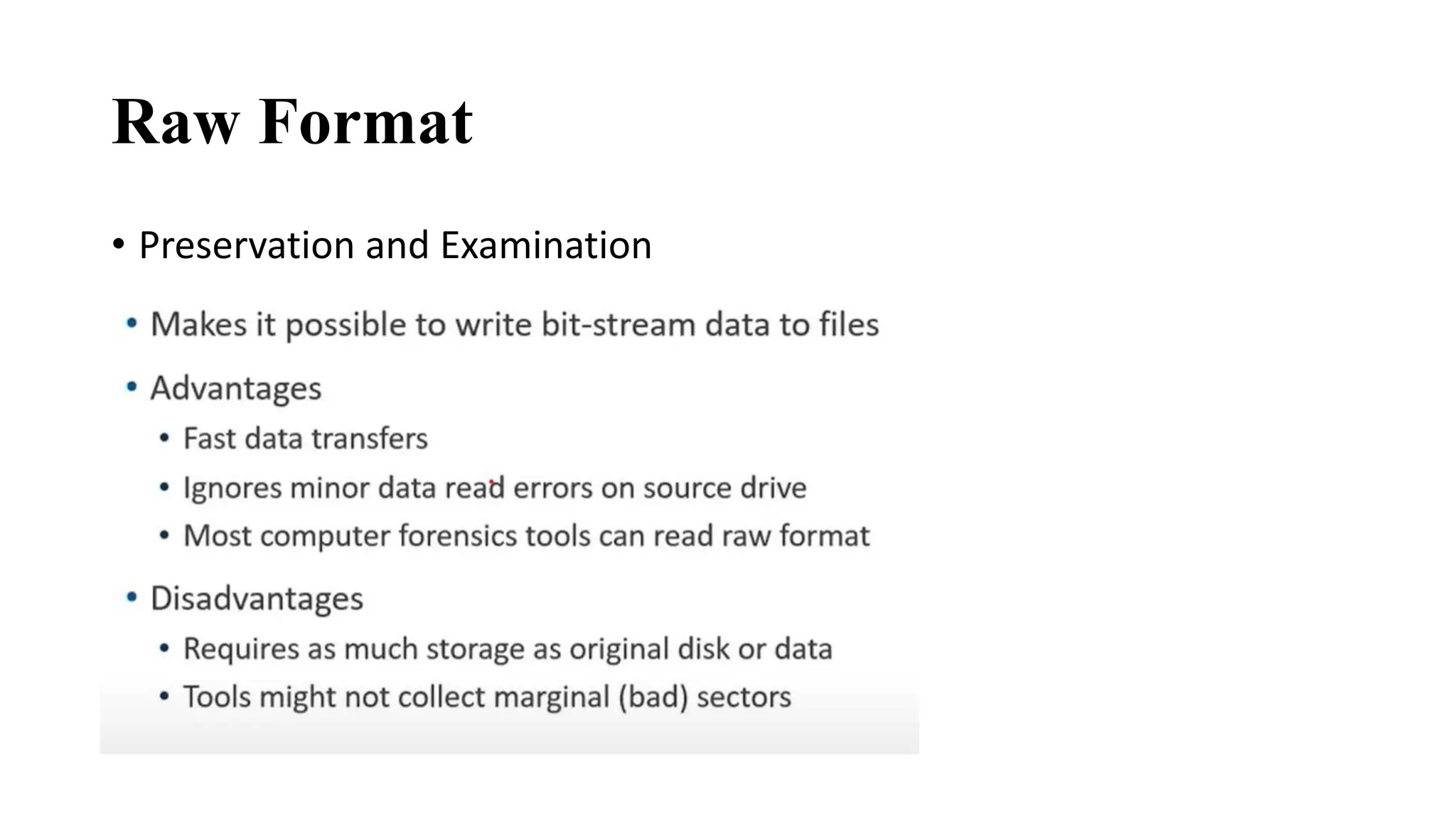
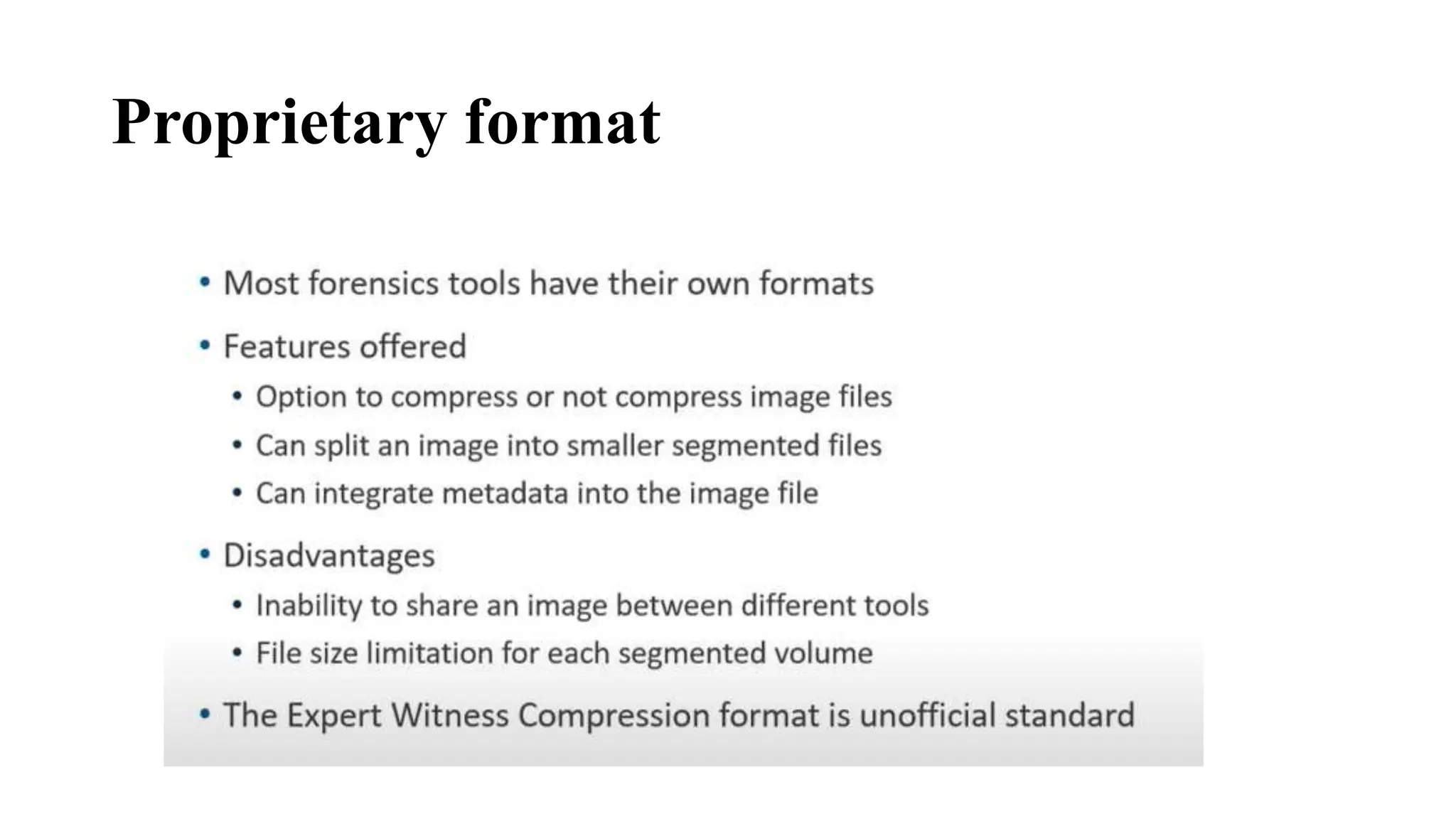
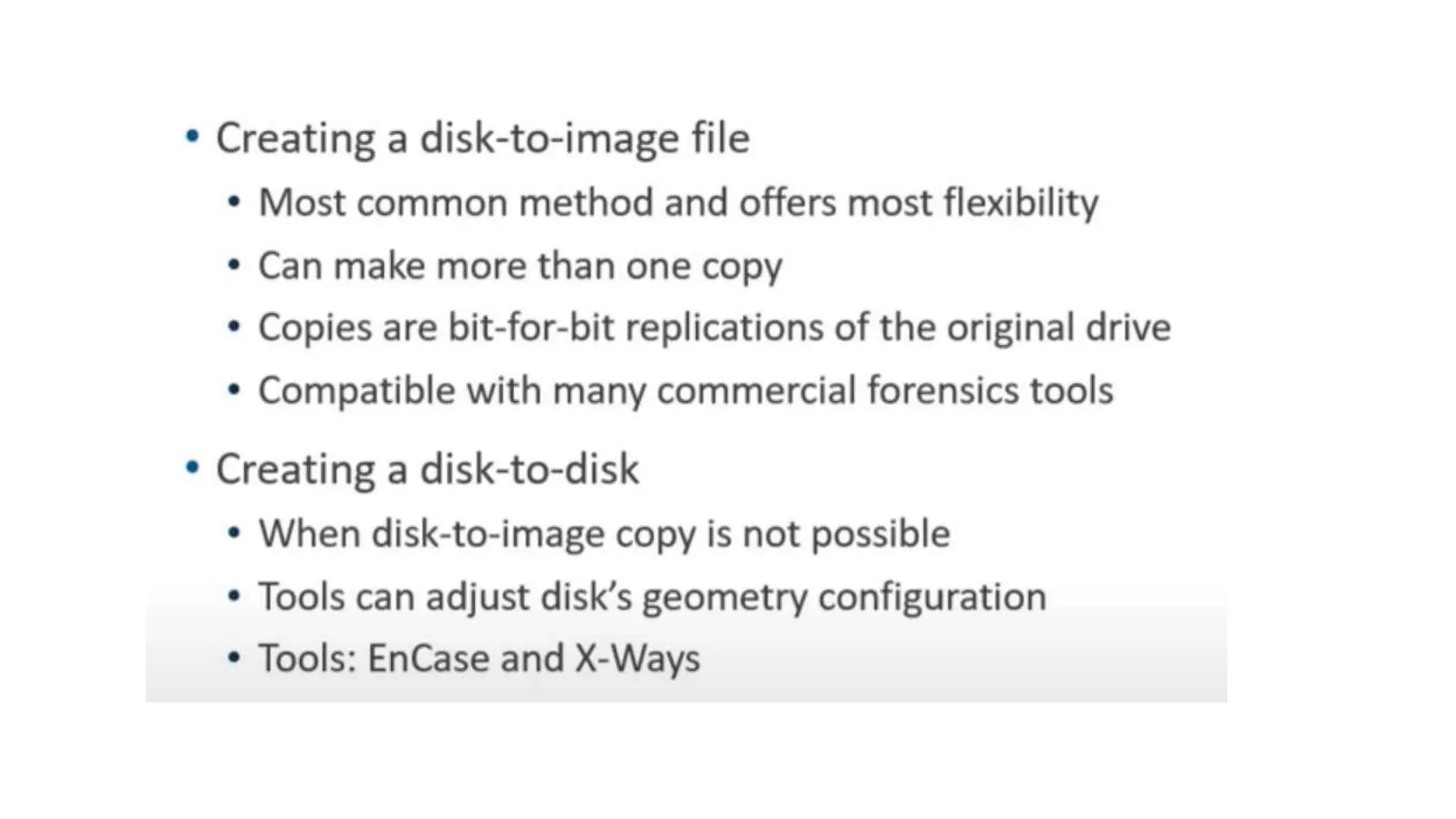
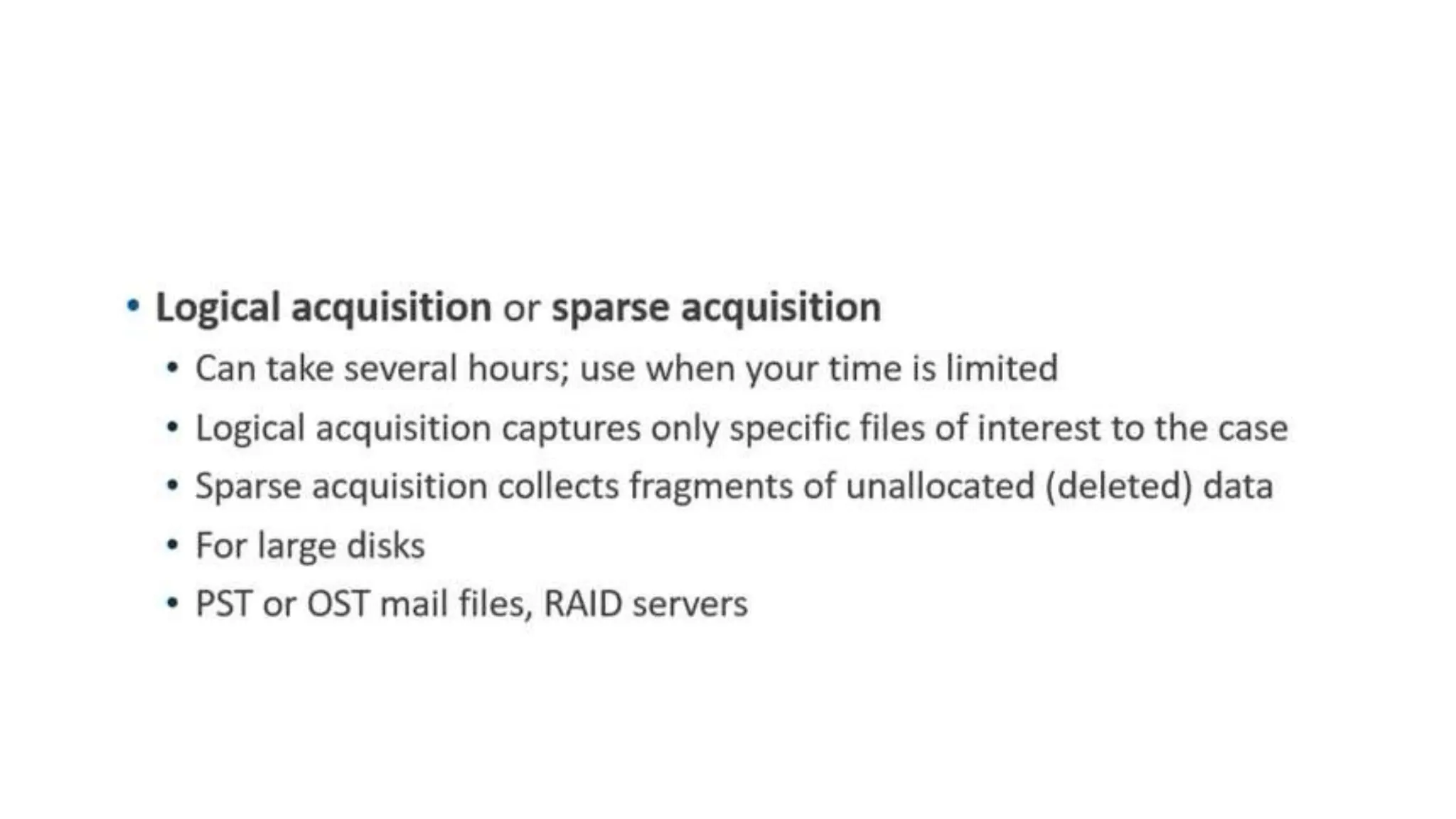
The document provides a comprehensive overview of cyber forensics, detailing its purpose, processes, and various types, such as network and mobile forensics. It also discusses the relationship between cybersecurity and cybercrime, classification of cyber crime, traditional computer crime challenges, and the steps involved in forensic investigations. Key concepts include data recovery methods, digital evidence handling, and the importance of maintaining evidence integrity for legal proceedings.