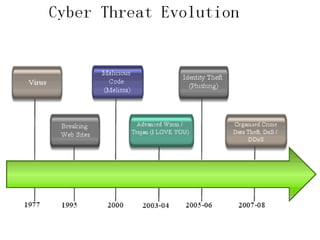
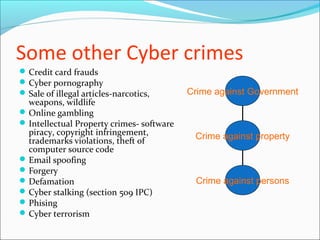
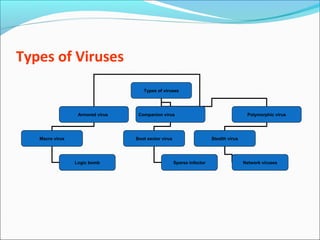
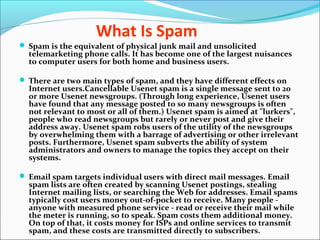
This document discusses various types of cybercrimes and the relevant laws in India. It defines cybercrimes as crimes that involve computers and the internet. The key points covered are:
- Types of cybercrimes include hacking, phishing, computer viruses, cyber pornography, denial of service attacks, and software piracy.
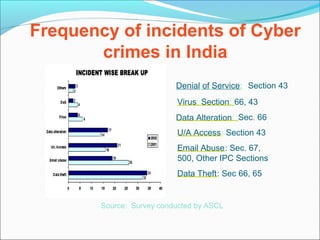
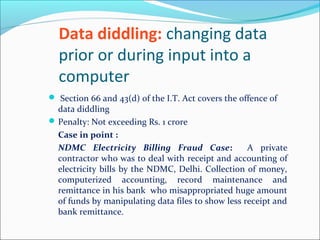
- The Indian IT Act 2000 is the main law governing cybercrimes and has sections dealing with hacking, data alteration, unauthorized access, and publishing obscene material.
- Other relevant laws include the IPC for offenses like fraud, forgery and criminal breach of trust.
- Investigating cybercrimes involves computer forensics to preserve digital evidence that can be accepted in