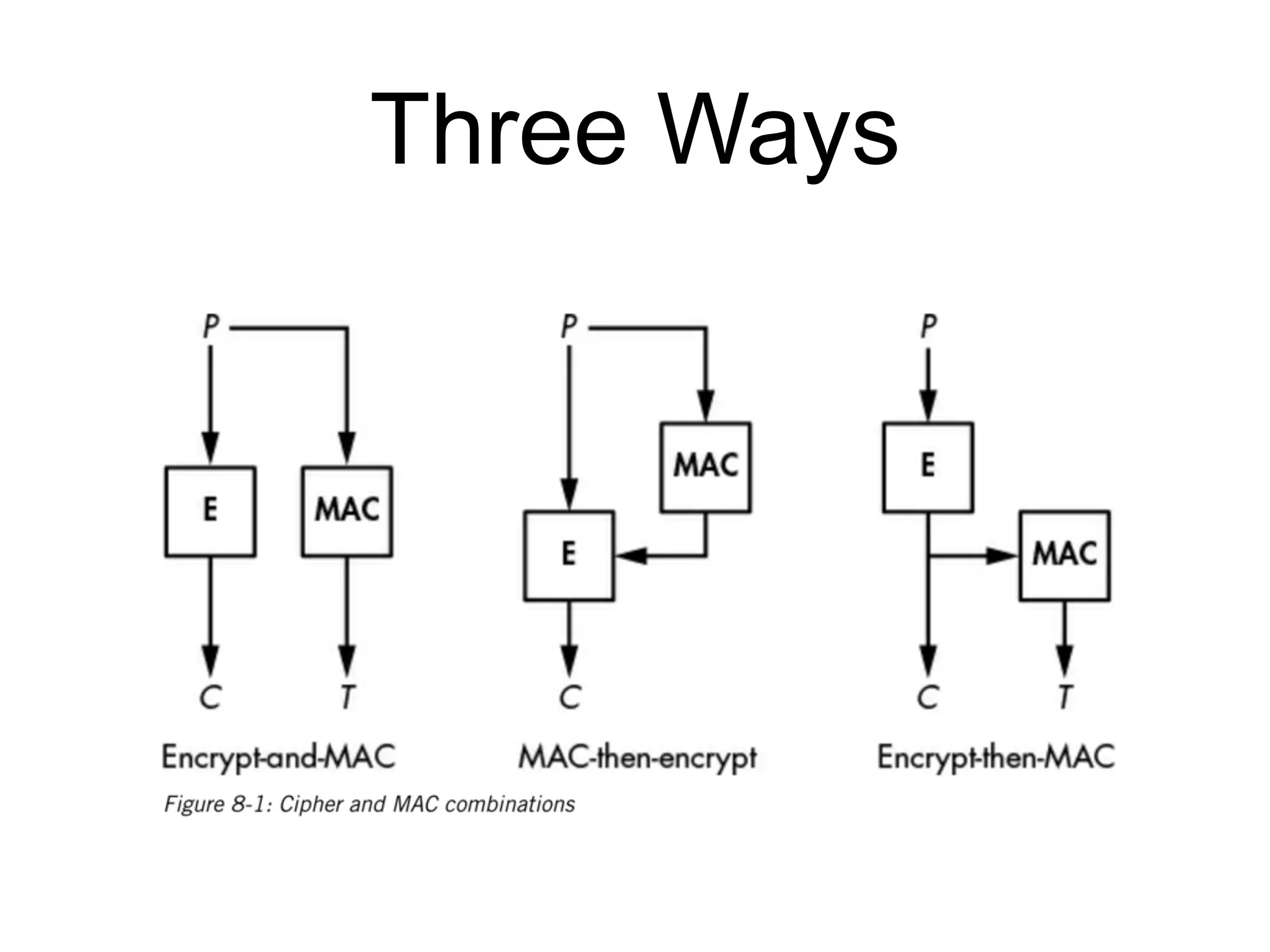
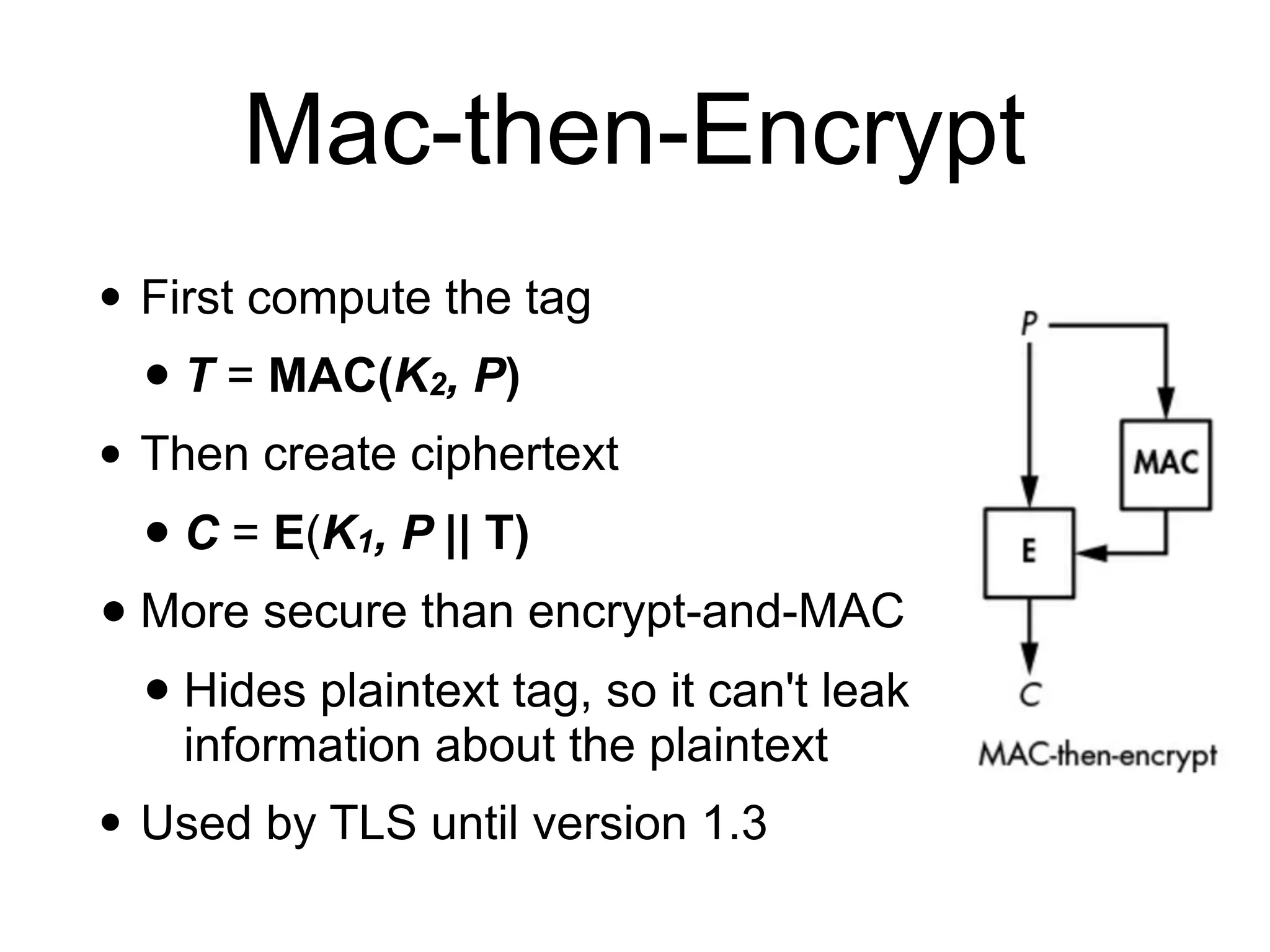
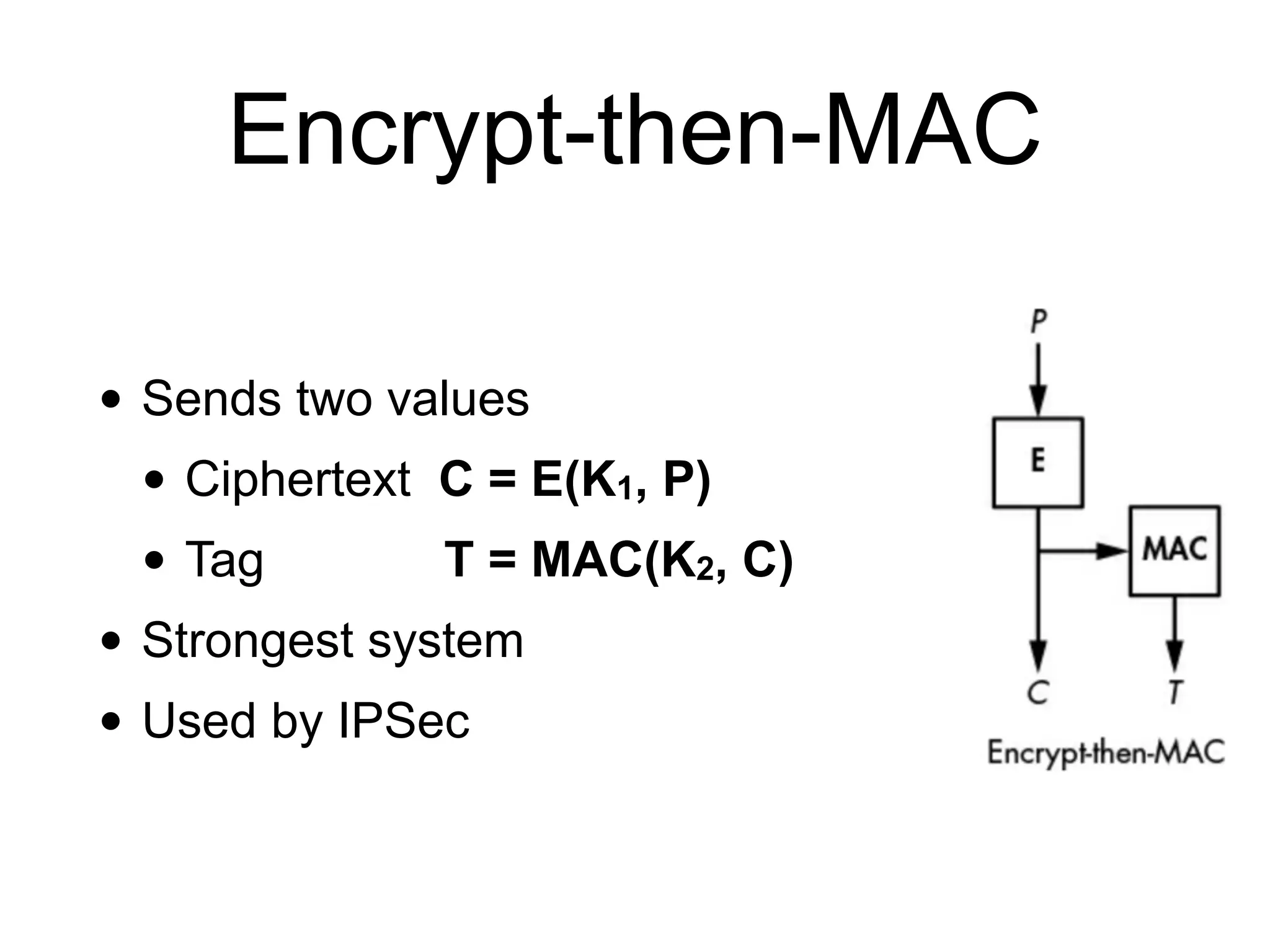
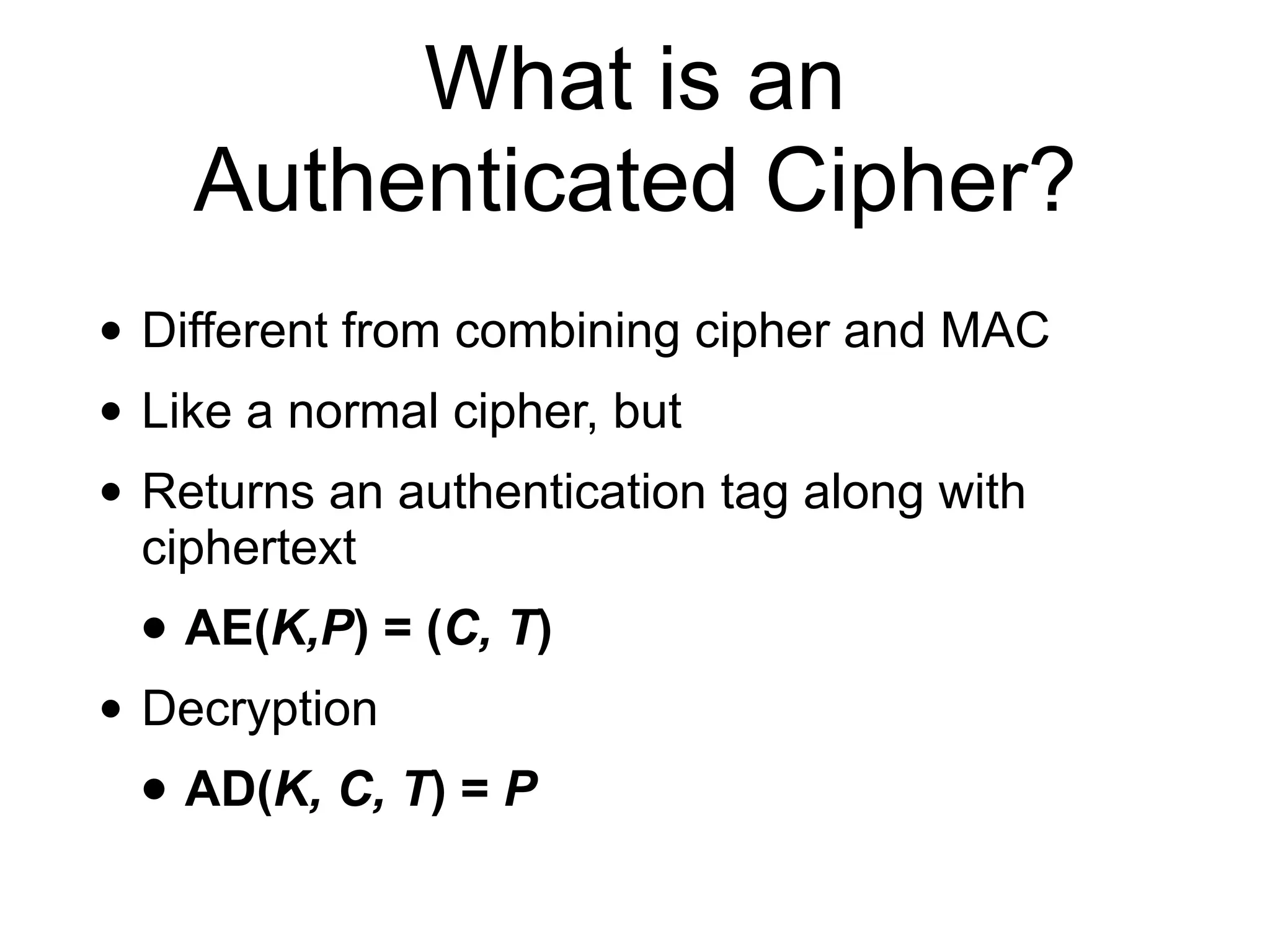
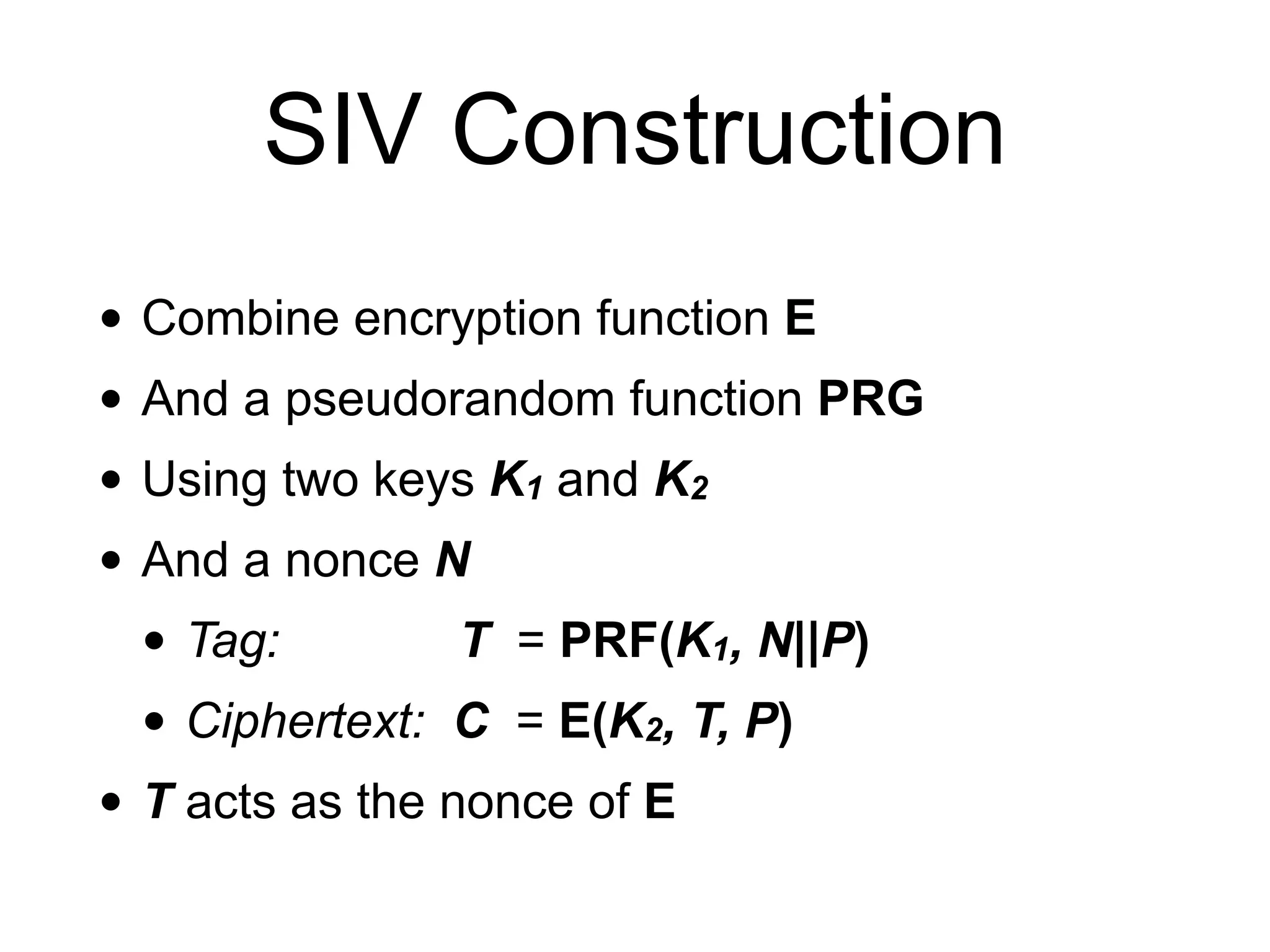
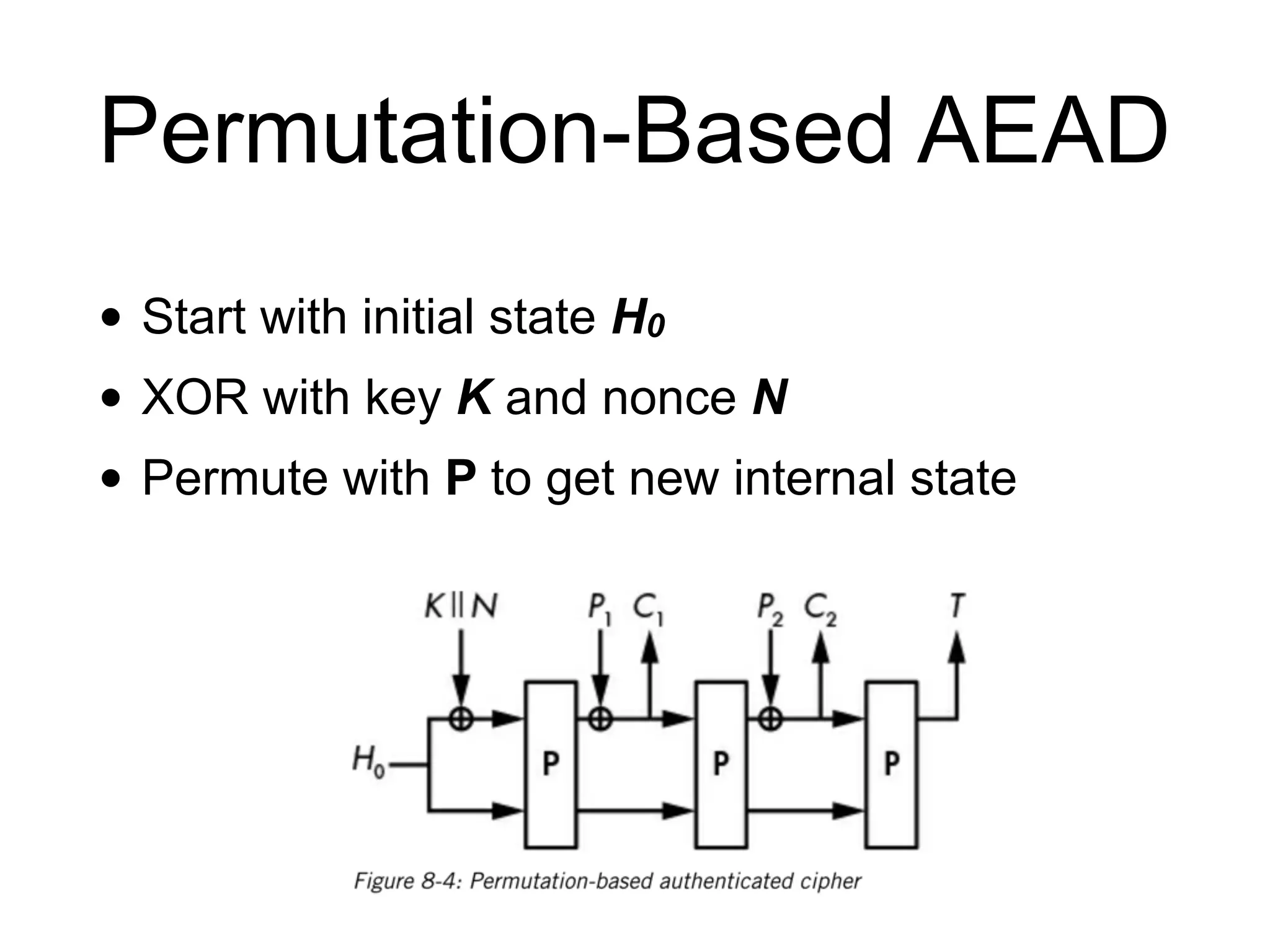
The document discusses authenticated encryption (AE), detailing methods like MACs (Message Authentication Codes) and different authenticated ciphers such as AES-GCM, OCB, and SIV, describing their functionalities, security requirements, and performance criteria. It addresses issues related to nonce reuse, the attack surface, and vulnerabilities of certain encryption methods. The document provides insights into the technical implementation of authenticated encryption and the trade-offs between security, efficiency, and complexity.