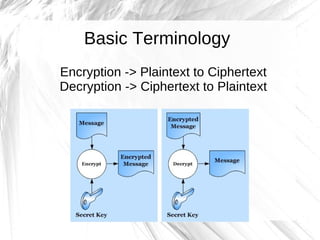
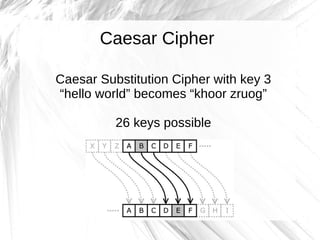
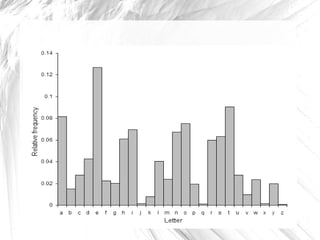
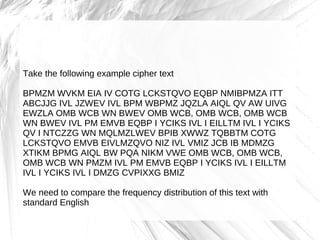
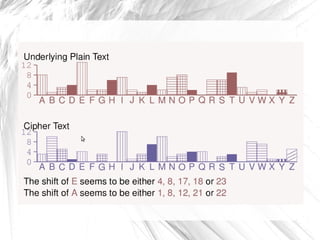
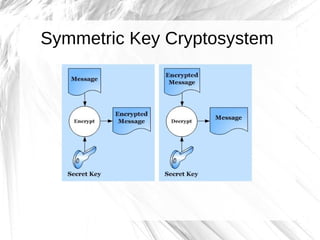
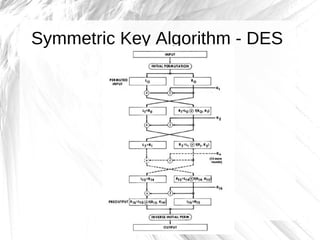
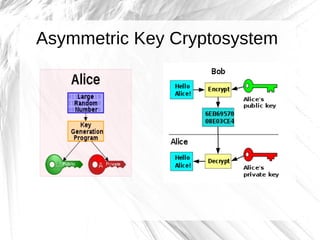
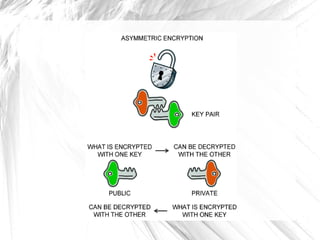
The document discusses cryptography, highlighting its definitions, goals, and applications while tracing its historical evolution from ancient Greek techniques to modern encryption methods. It covers key concepts like encryption, decryption, and ciphers, as well as challenges and advancements in the field, particularly in relation to computer science and mathematics. The work also emphasizes the practical importance of cryptography in ensuring data security across various platforms.