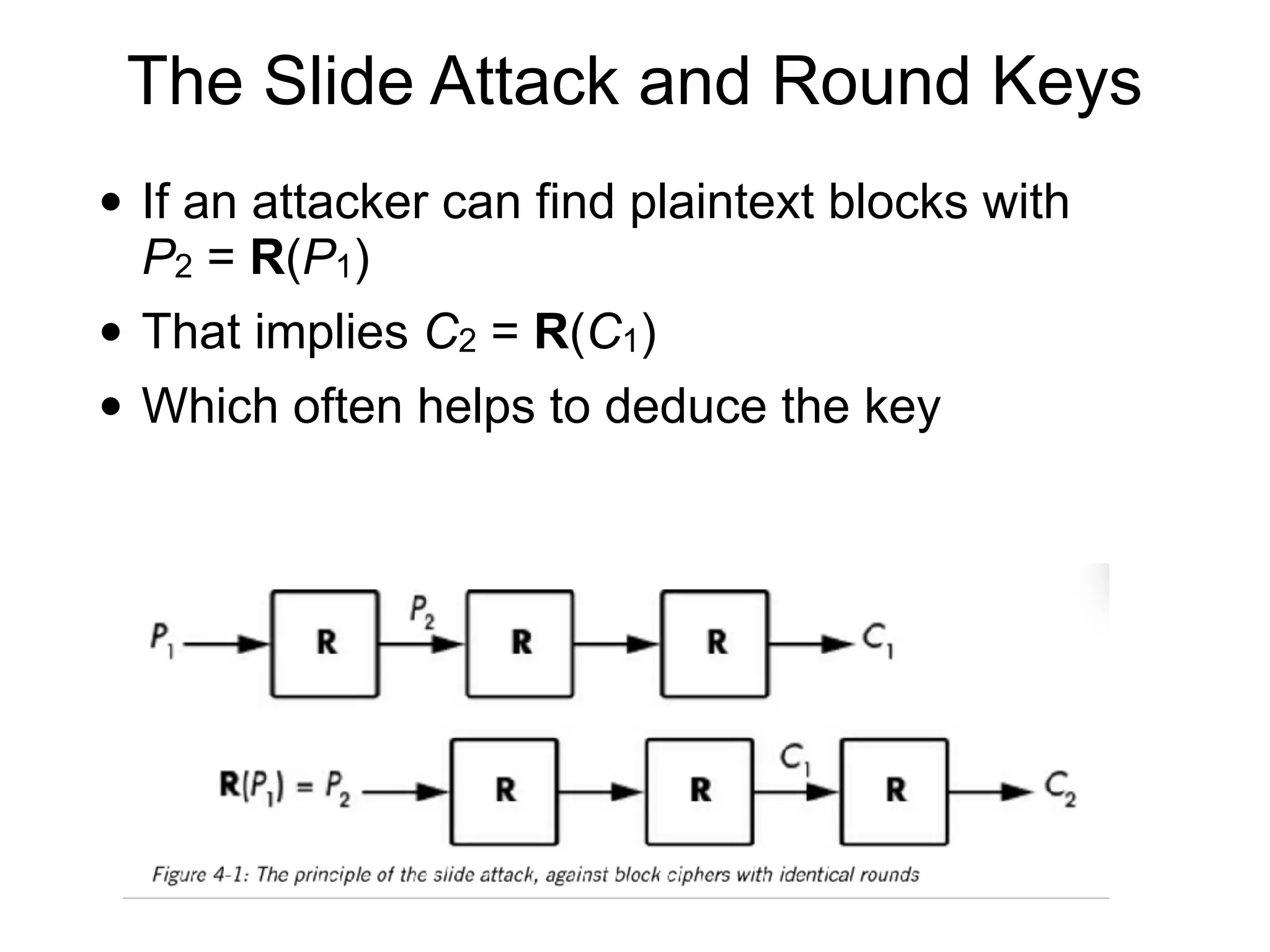
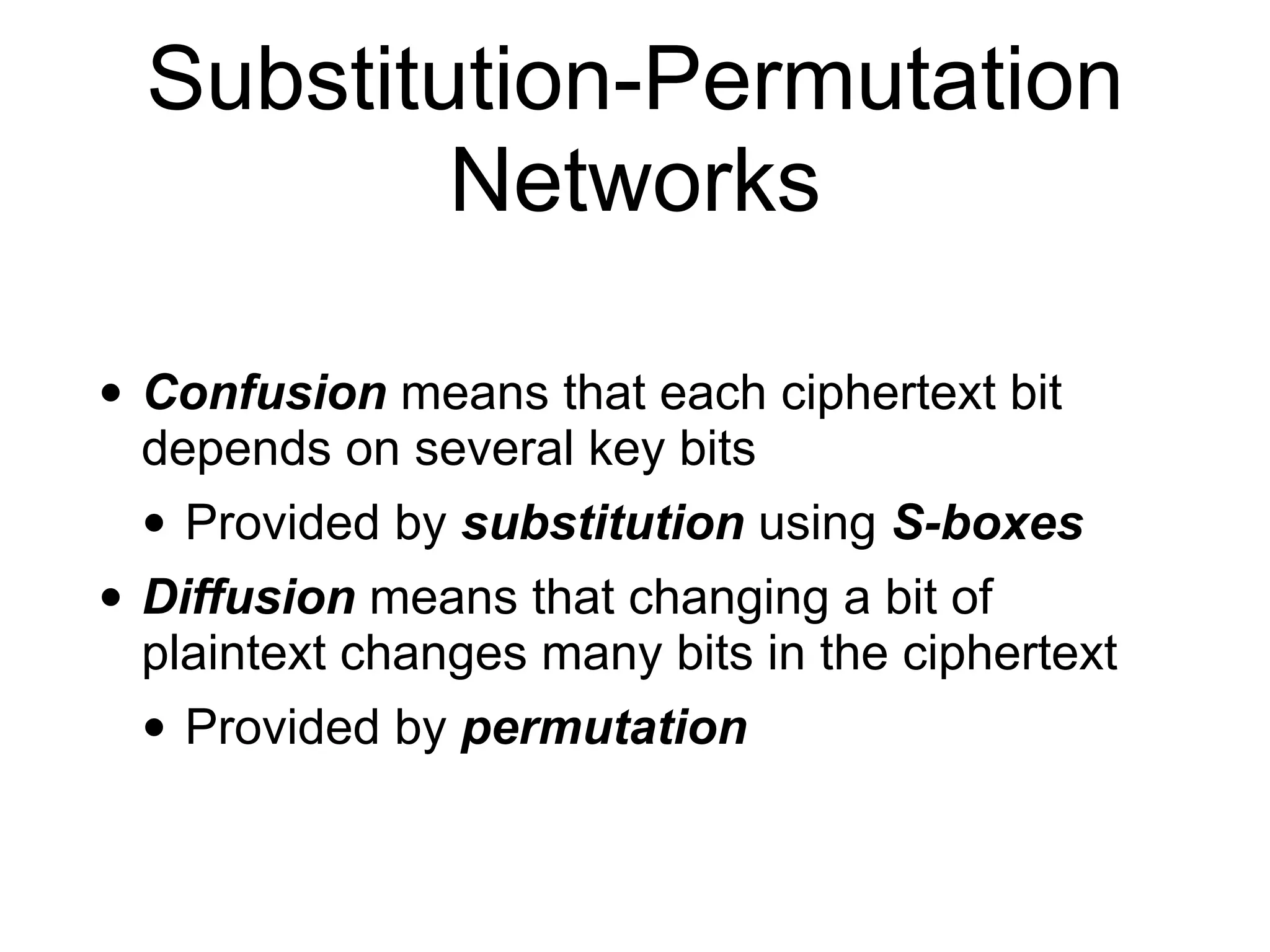
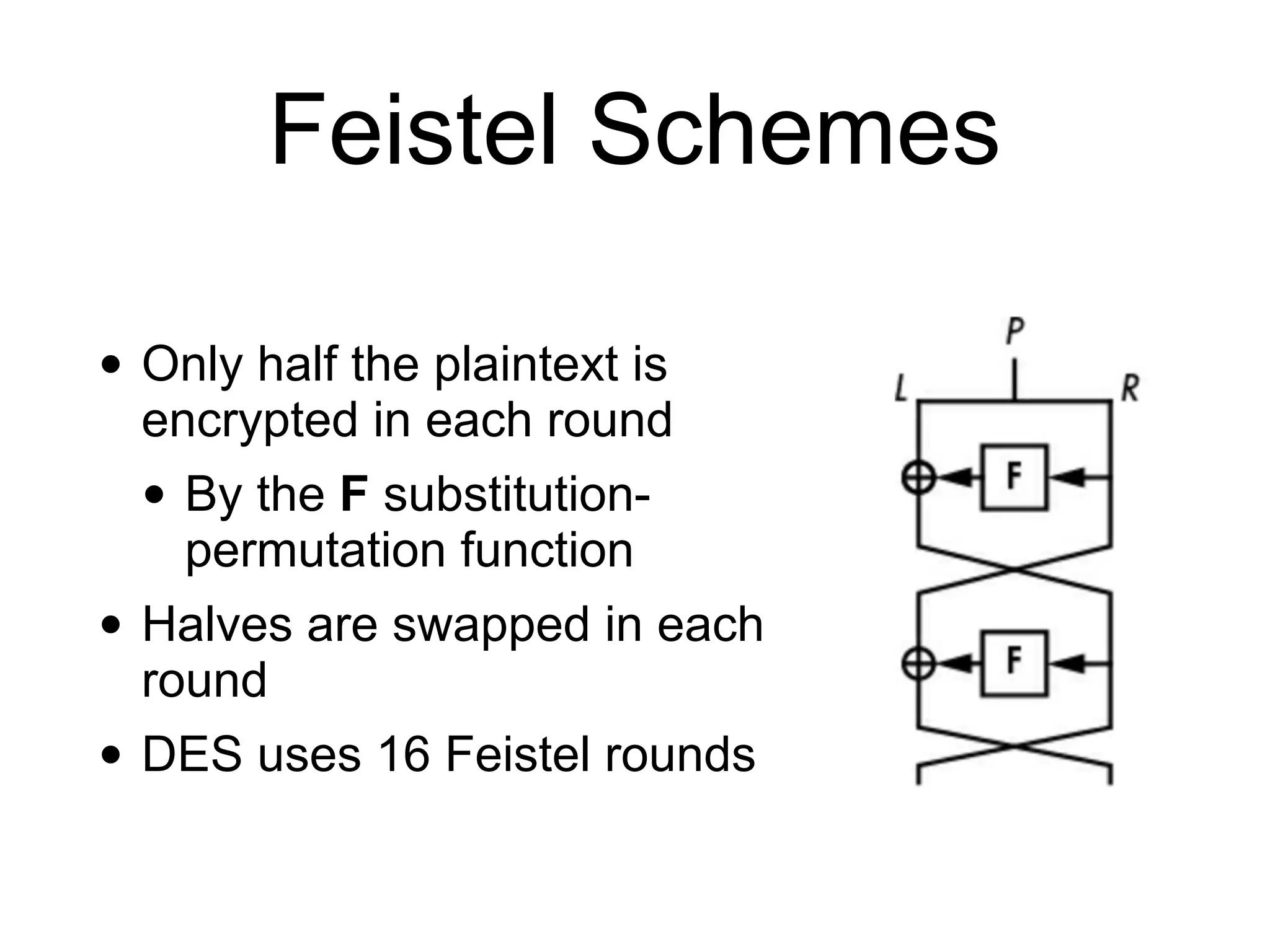
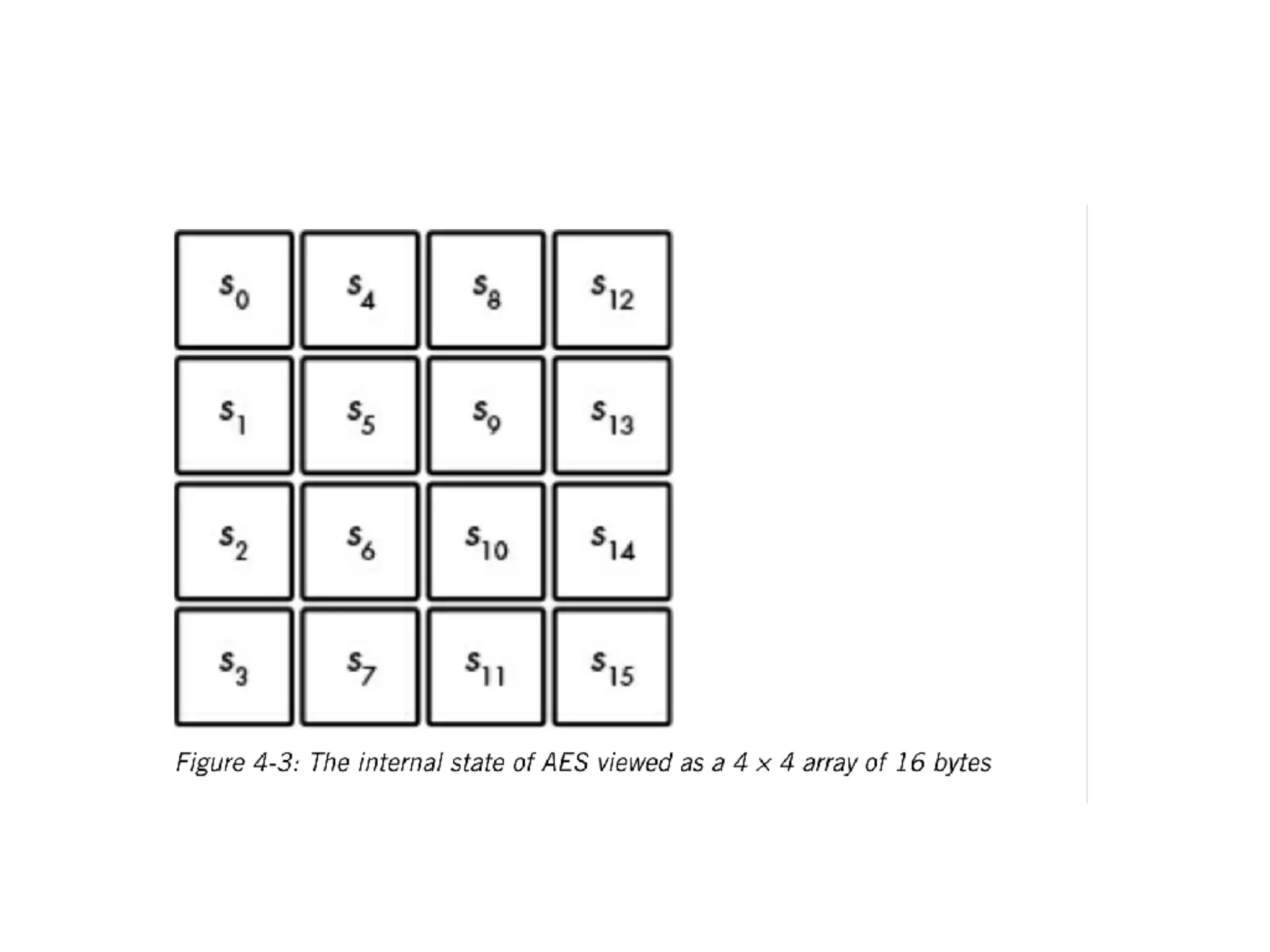
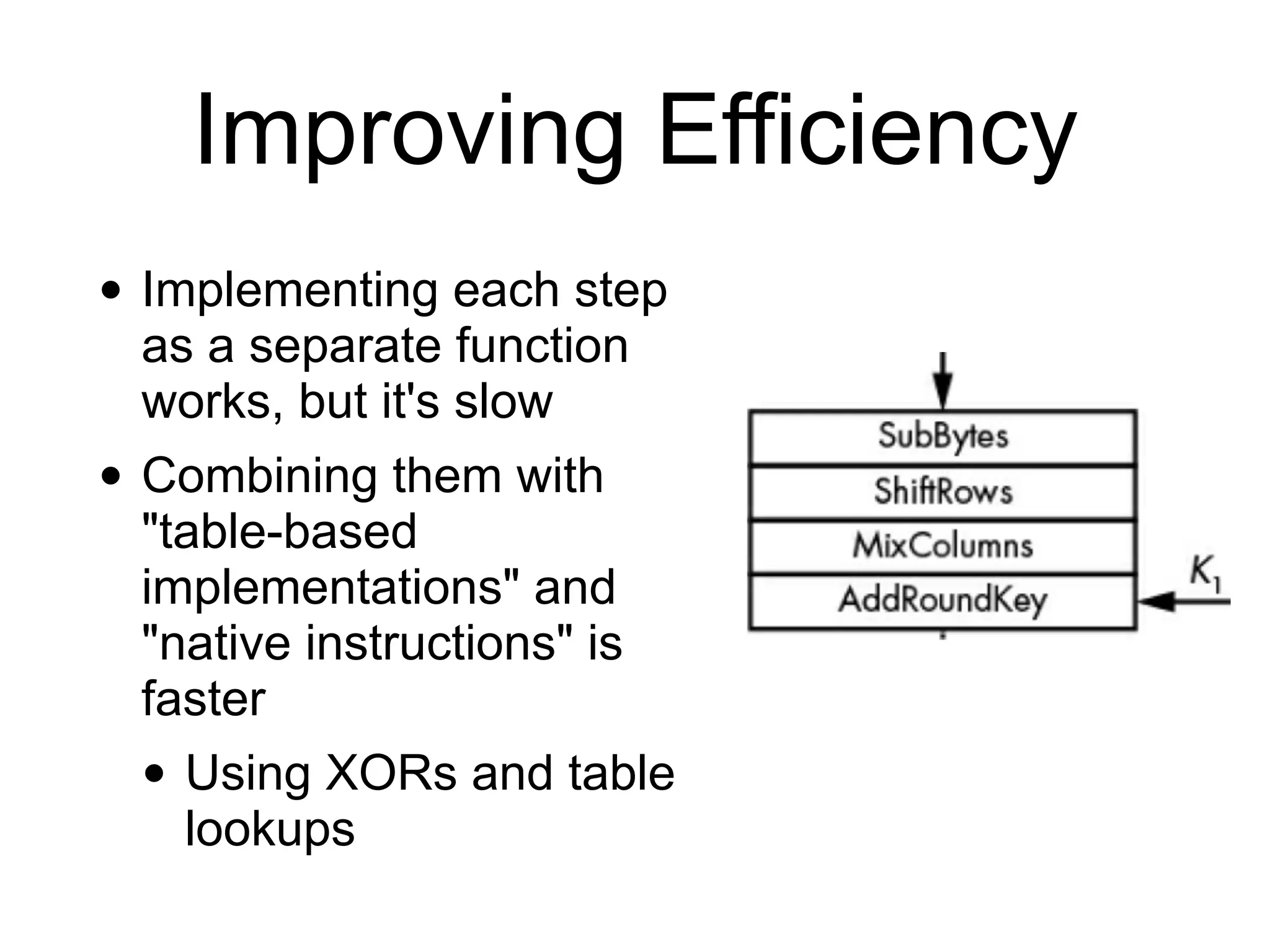
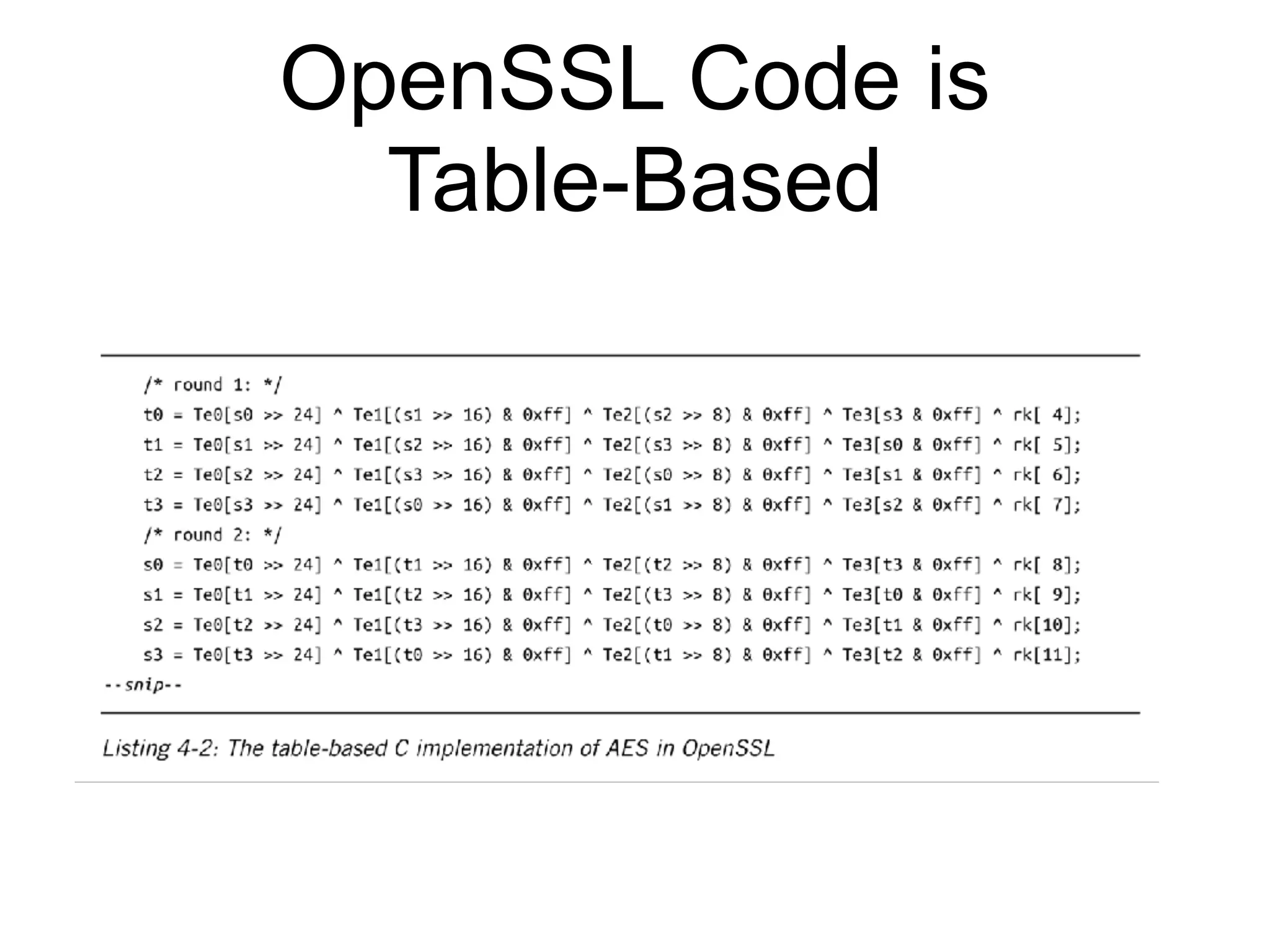
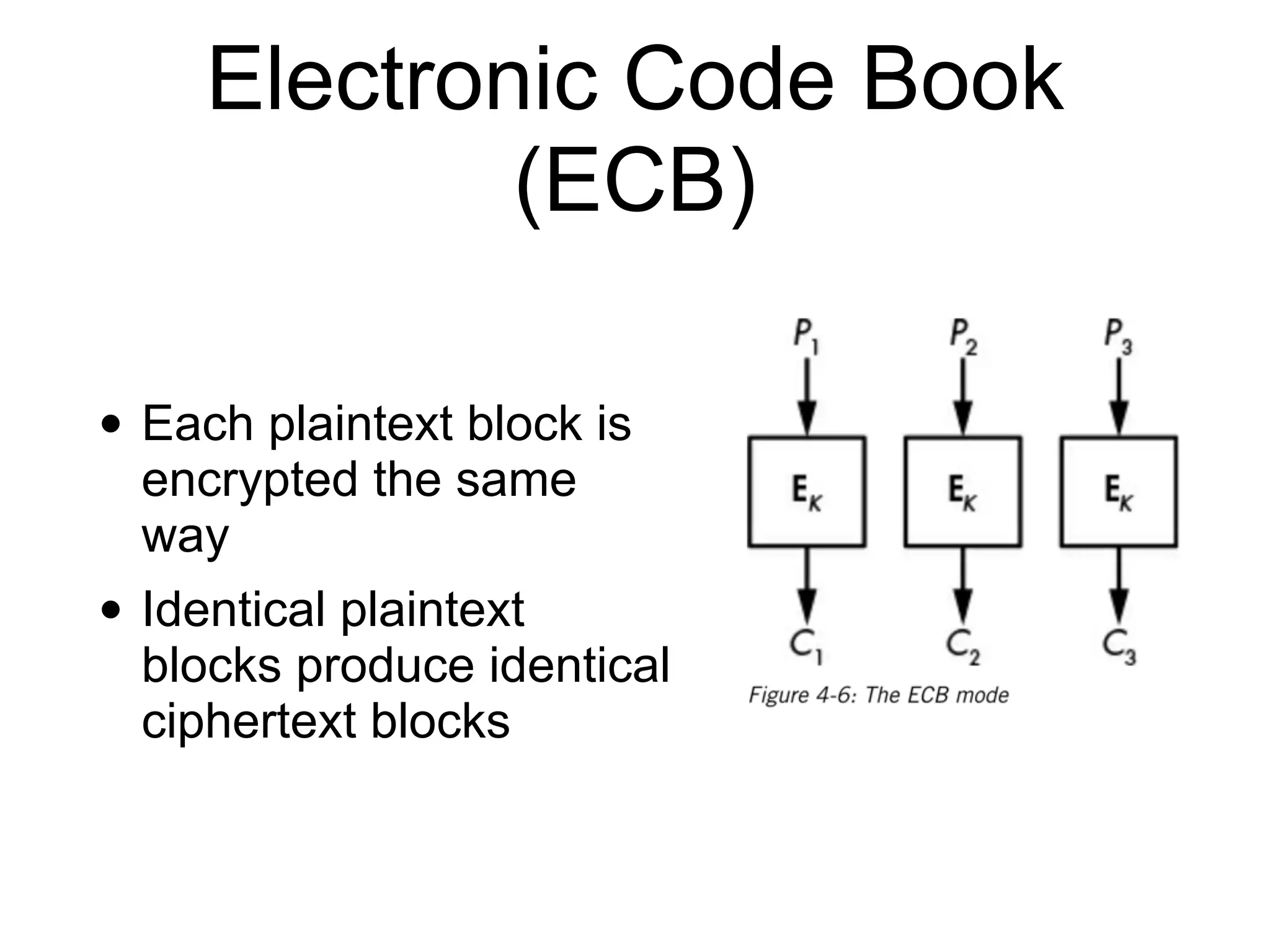
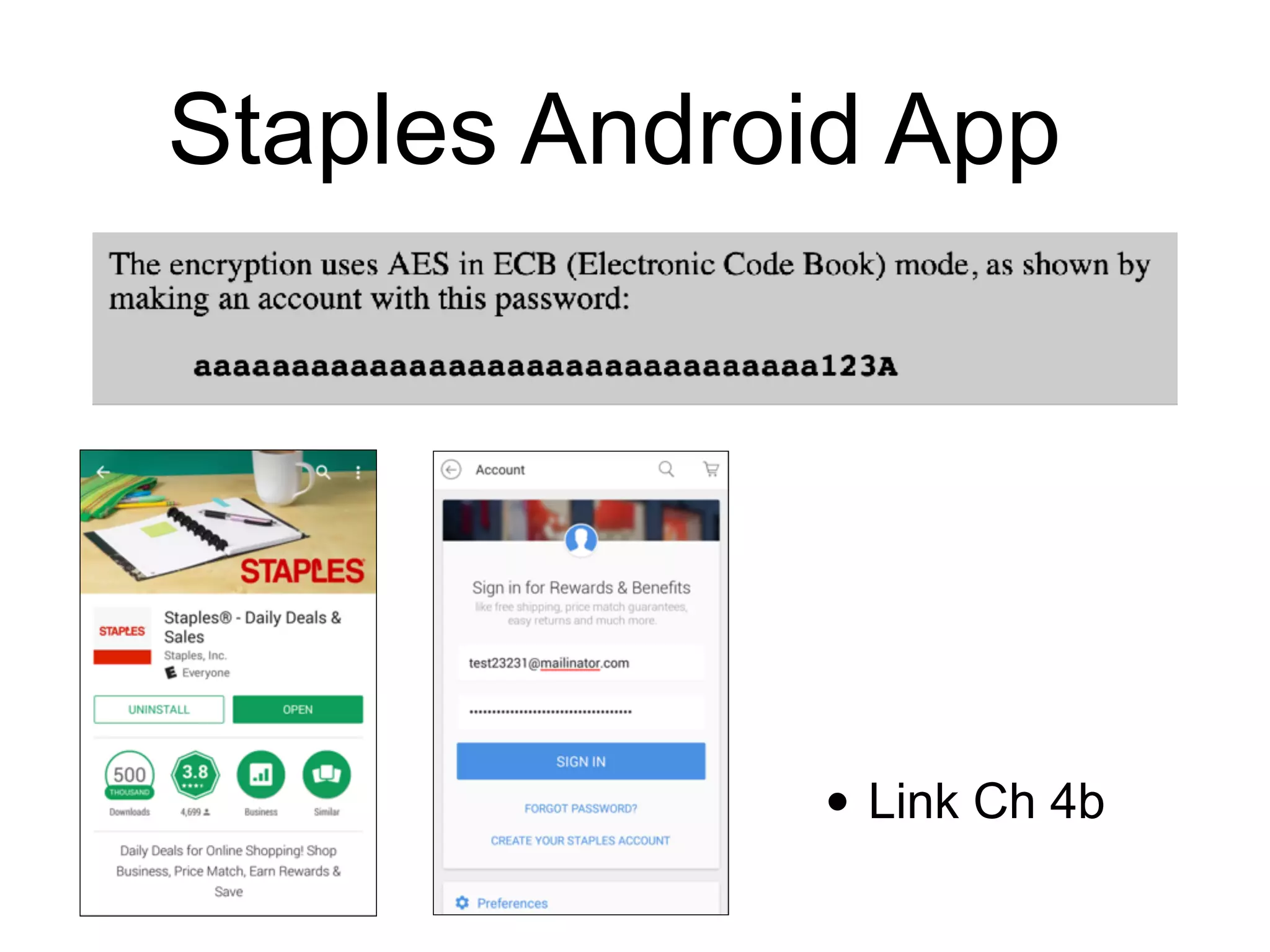
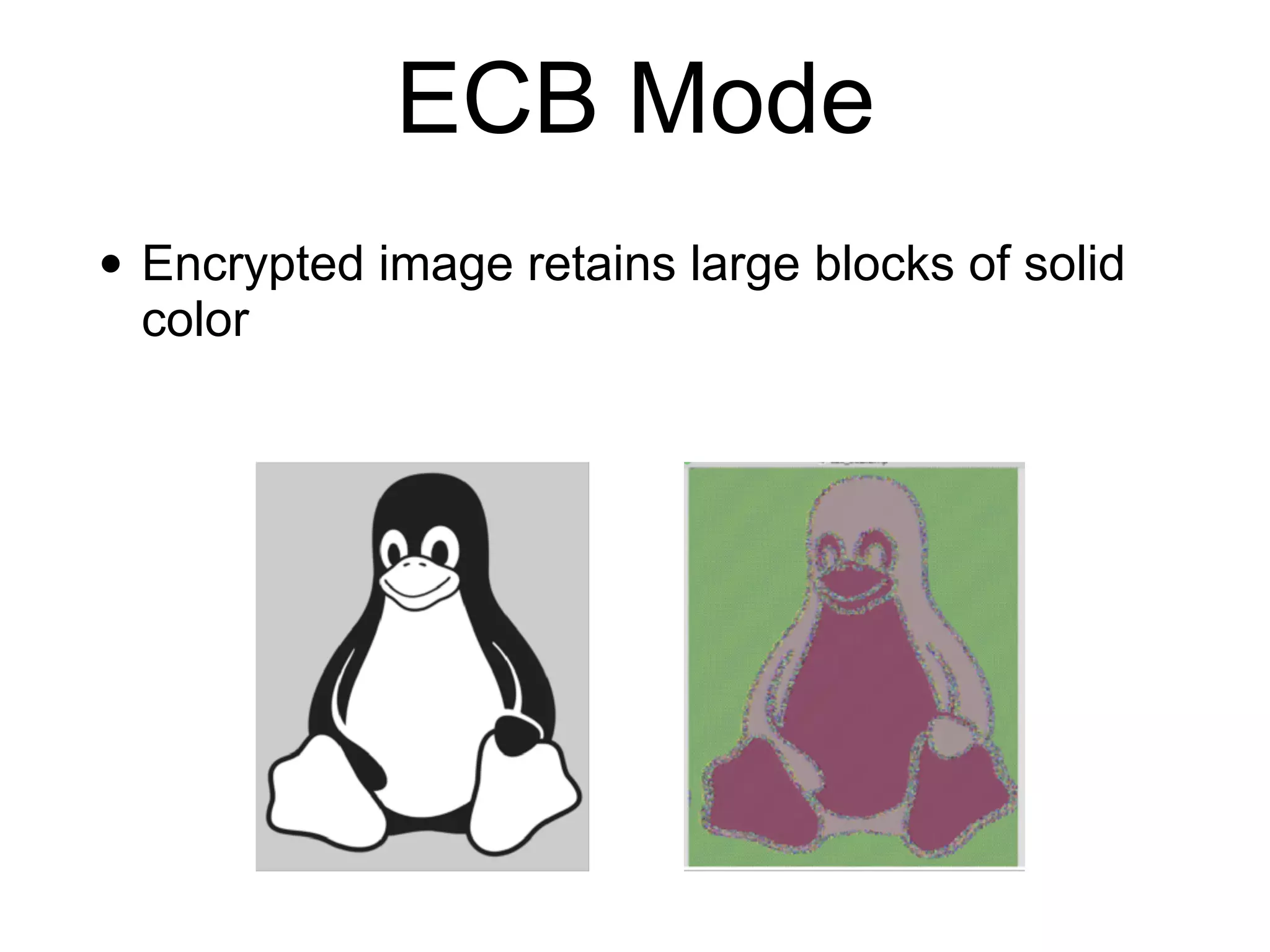
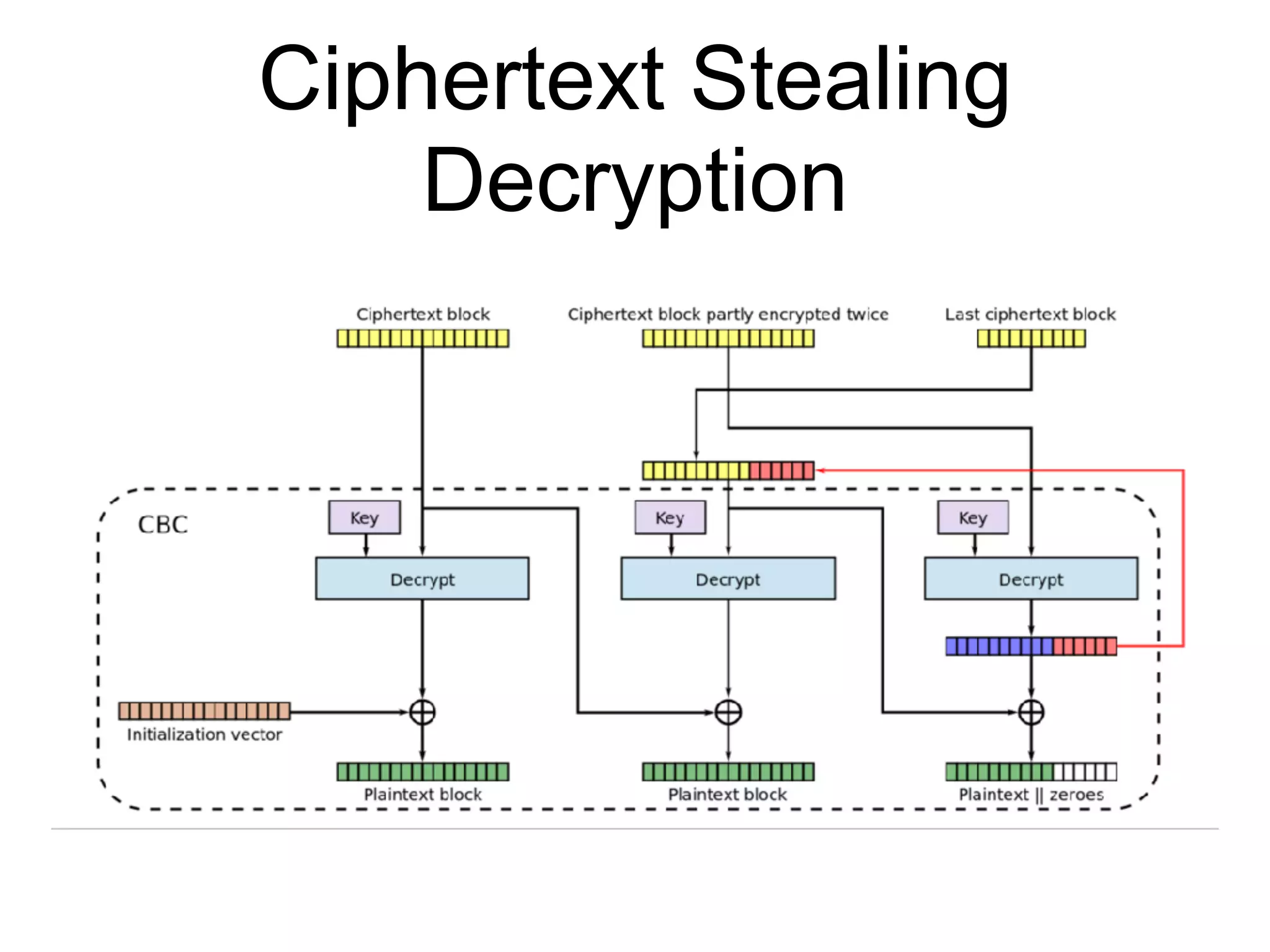
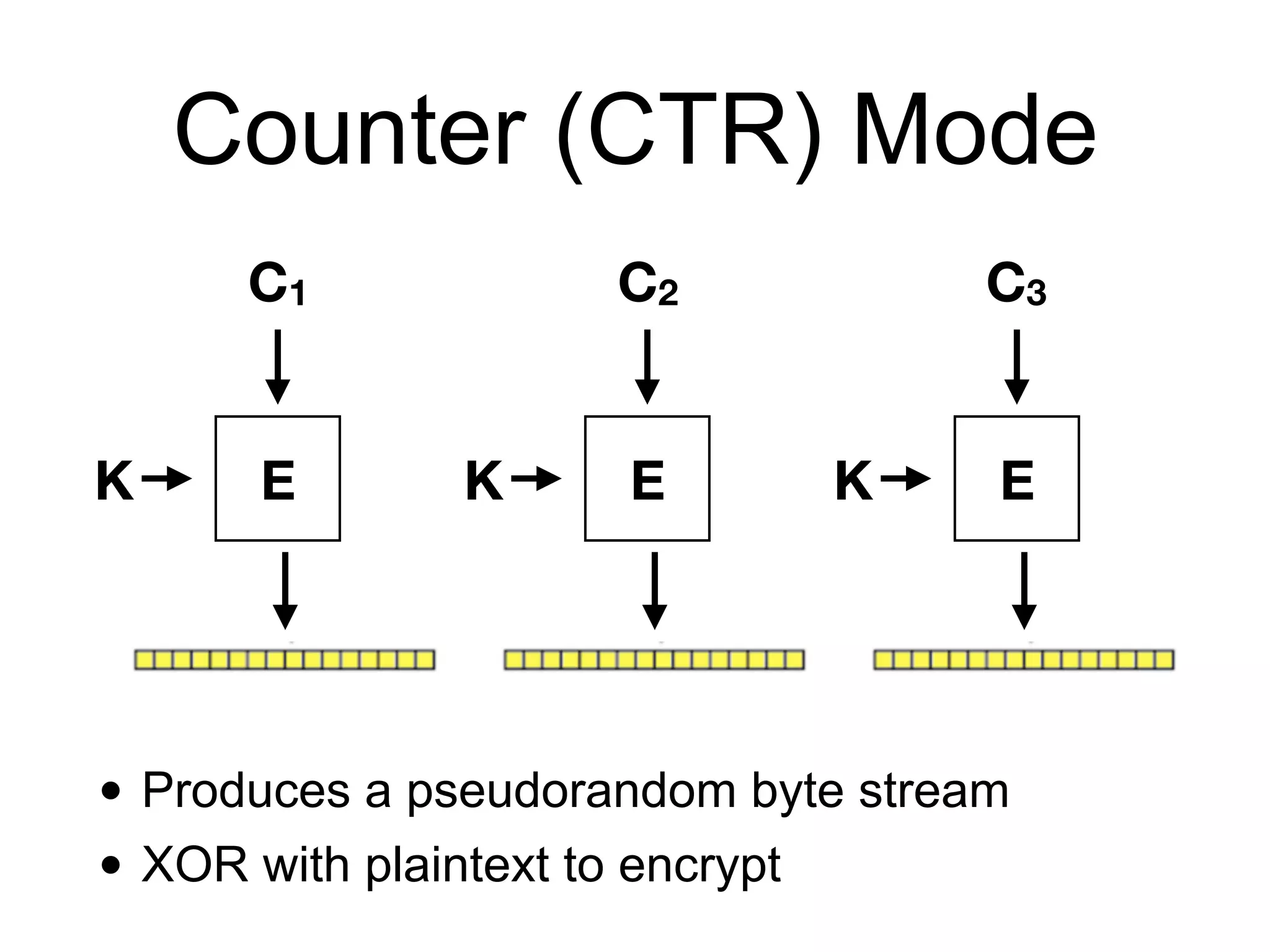
This document discusses block ciphers and their implementation. It begins with an overview of block cipher history and components like block size and round keys. It then examines the AES block cipher standard and how to efficiently implement it using table lookups and processor instructions. Finally, it covers modes of operation like CBC, CTR, and their security, as well as potential attacks like padding oracles and meet-in-the-middle.