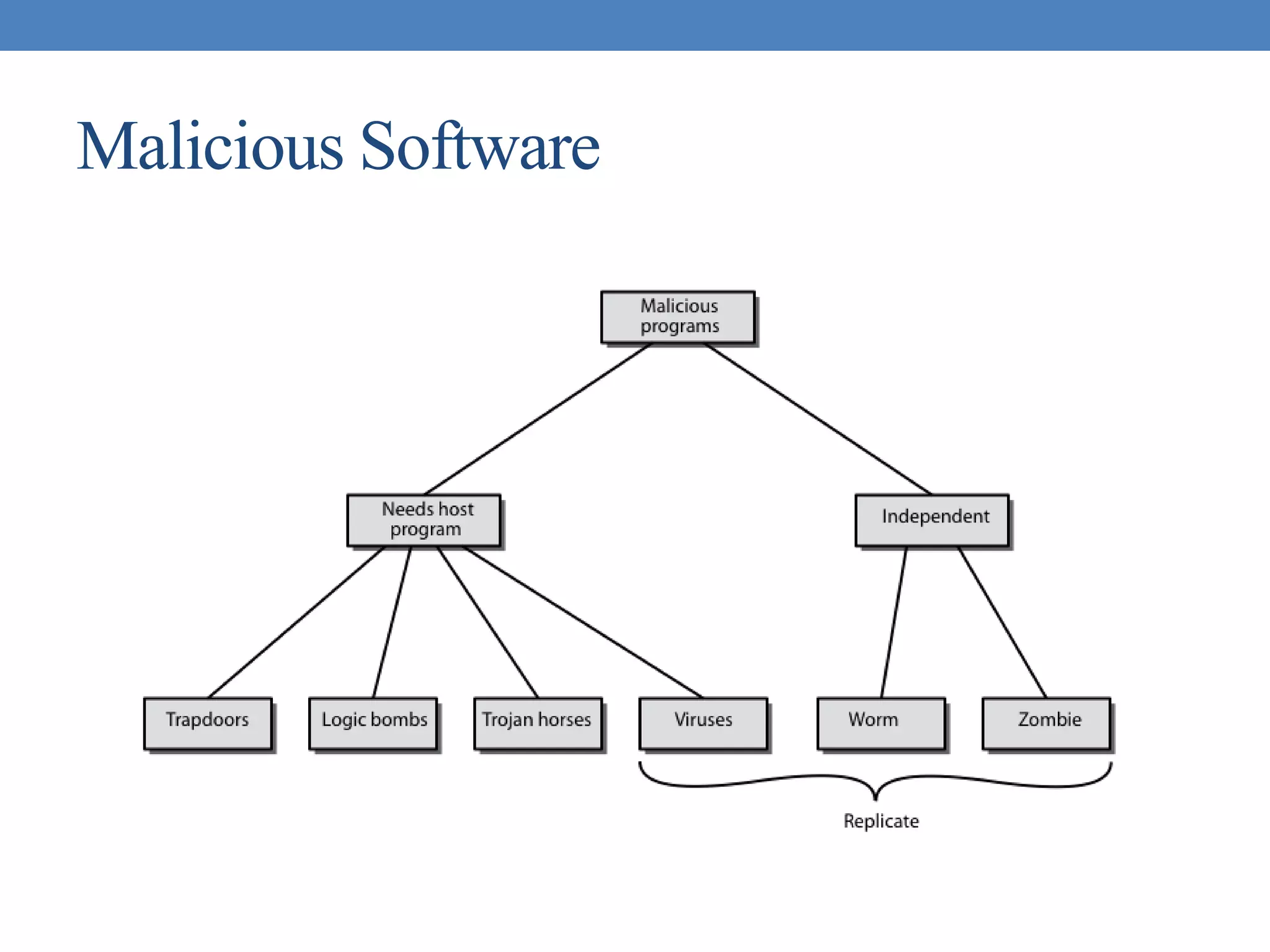
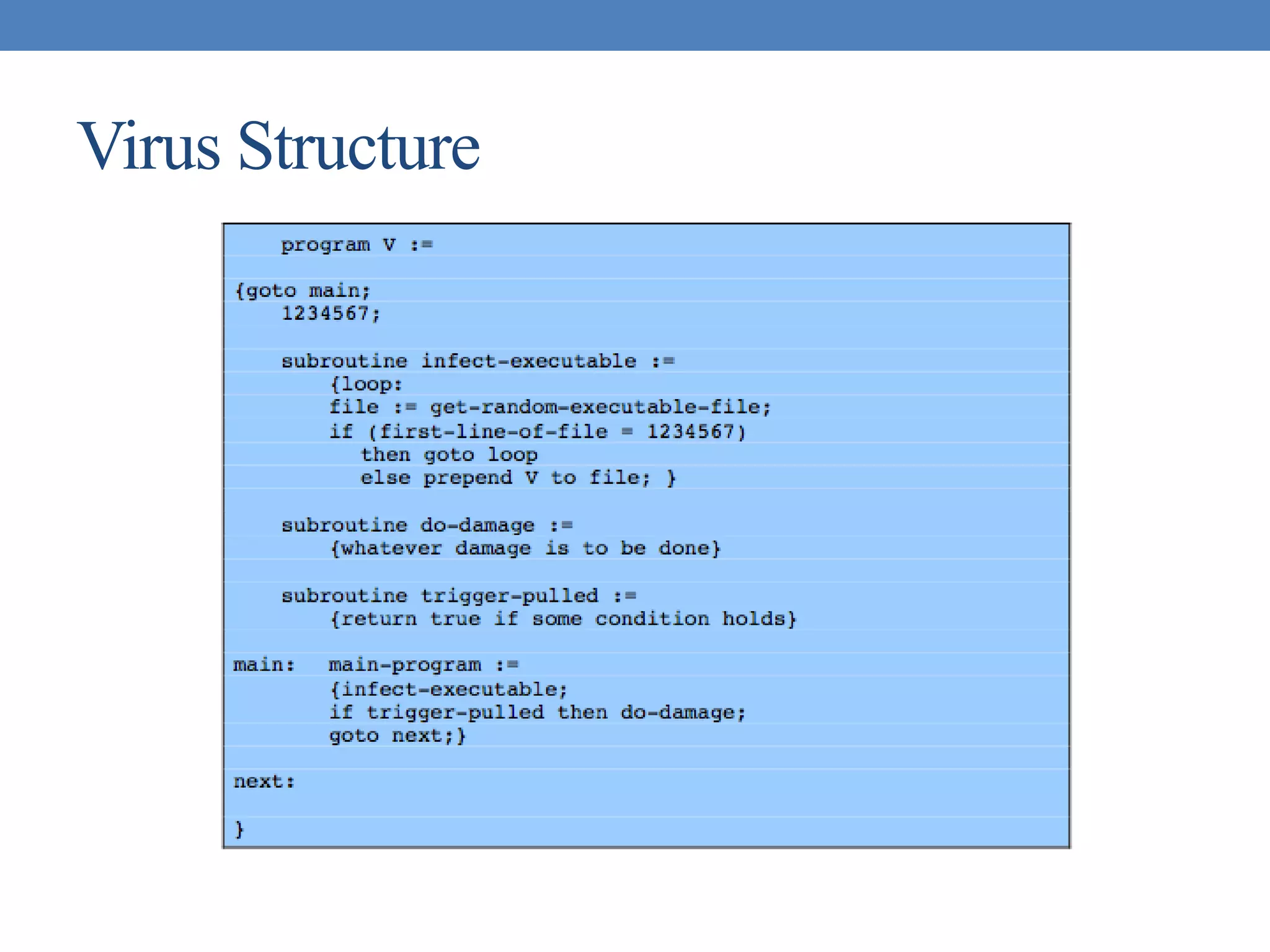
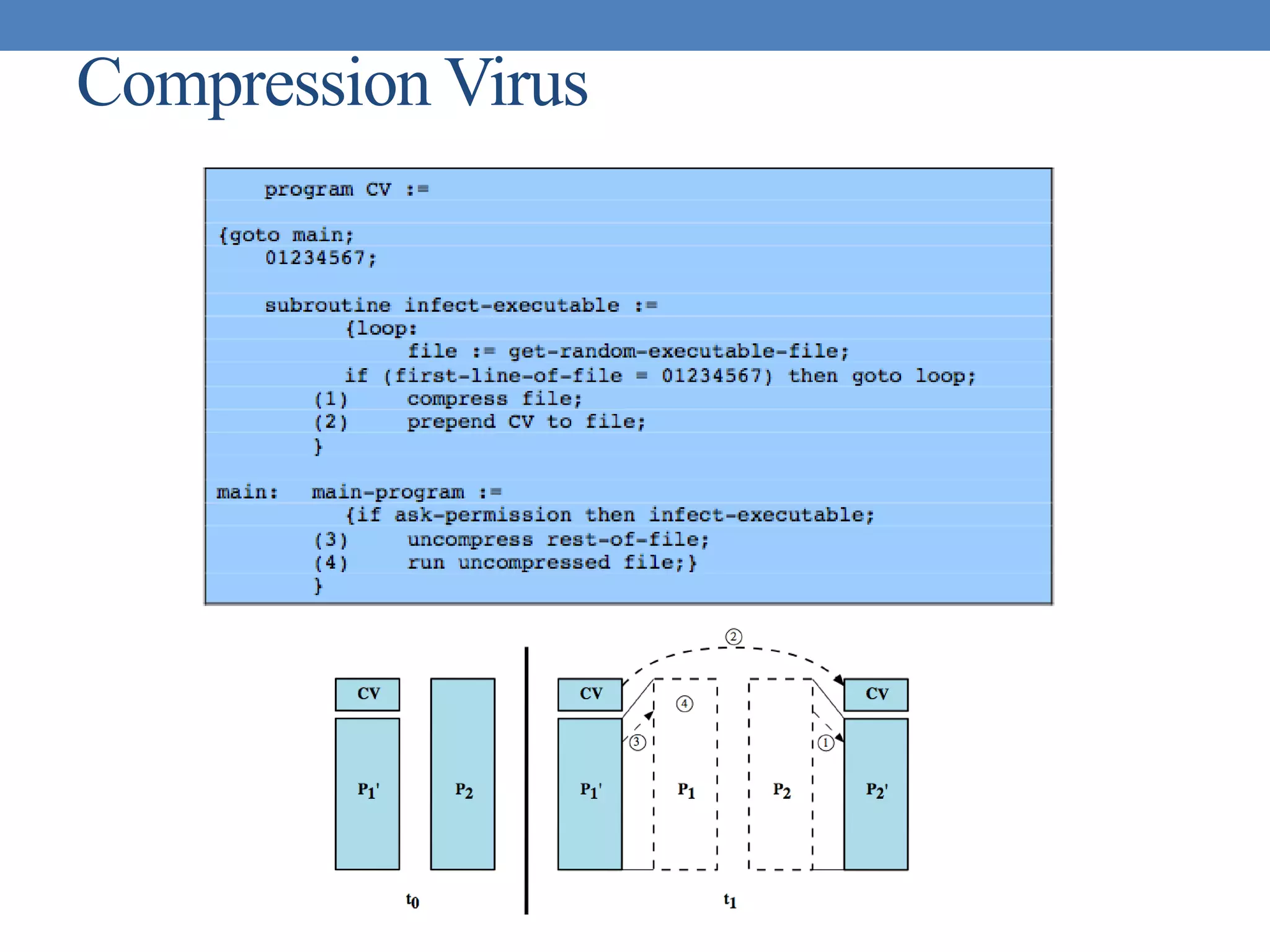
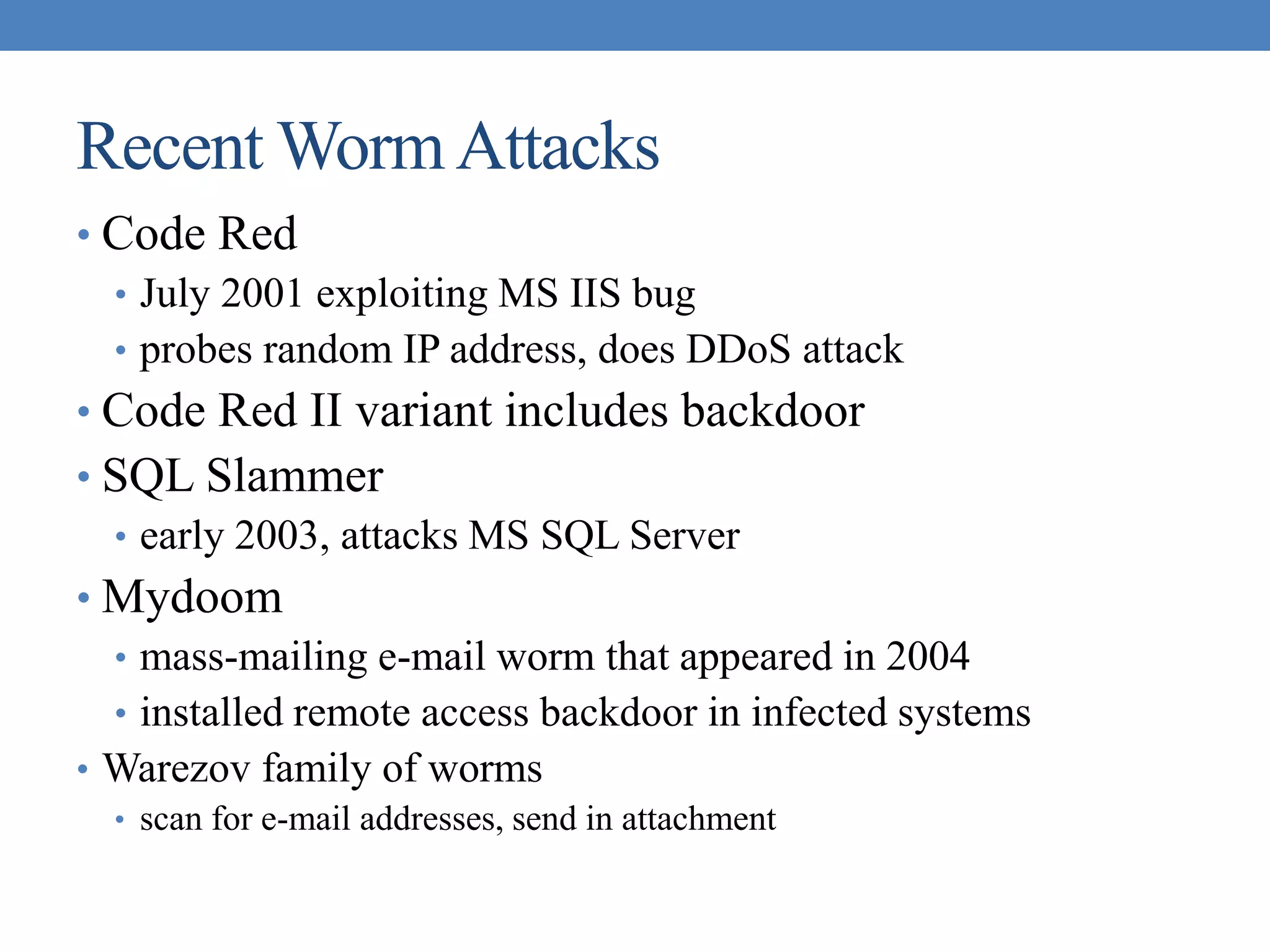
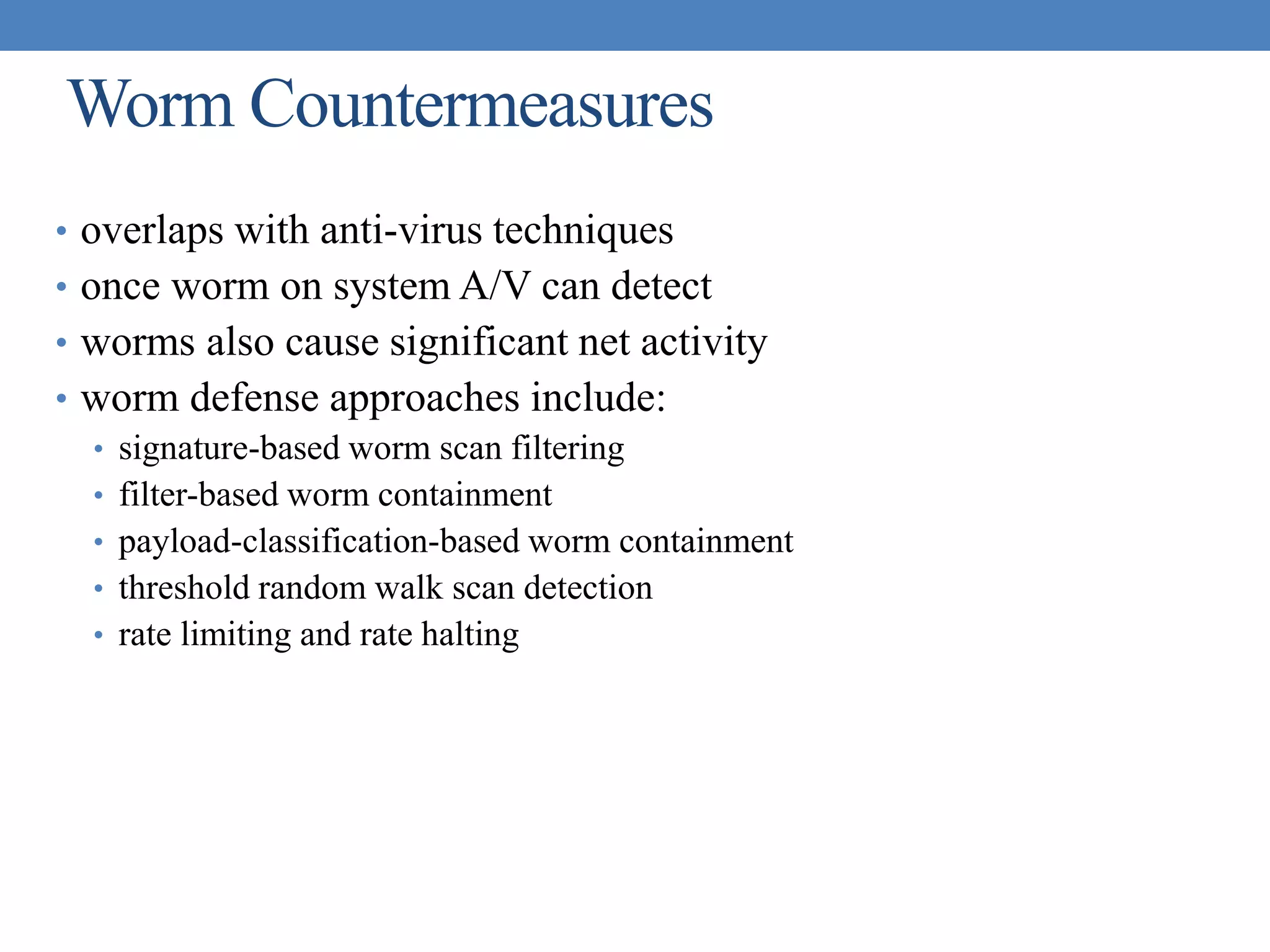
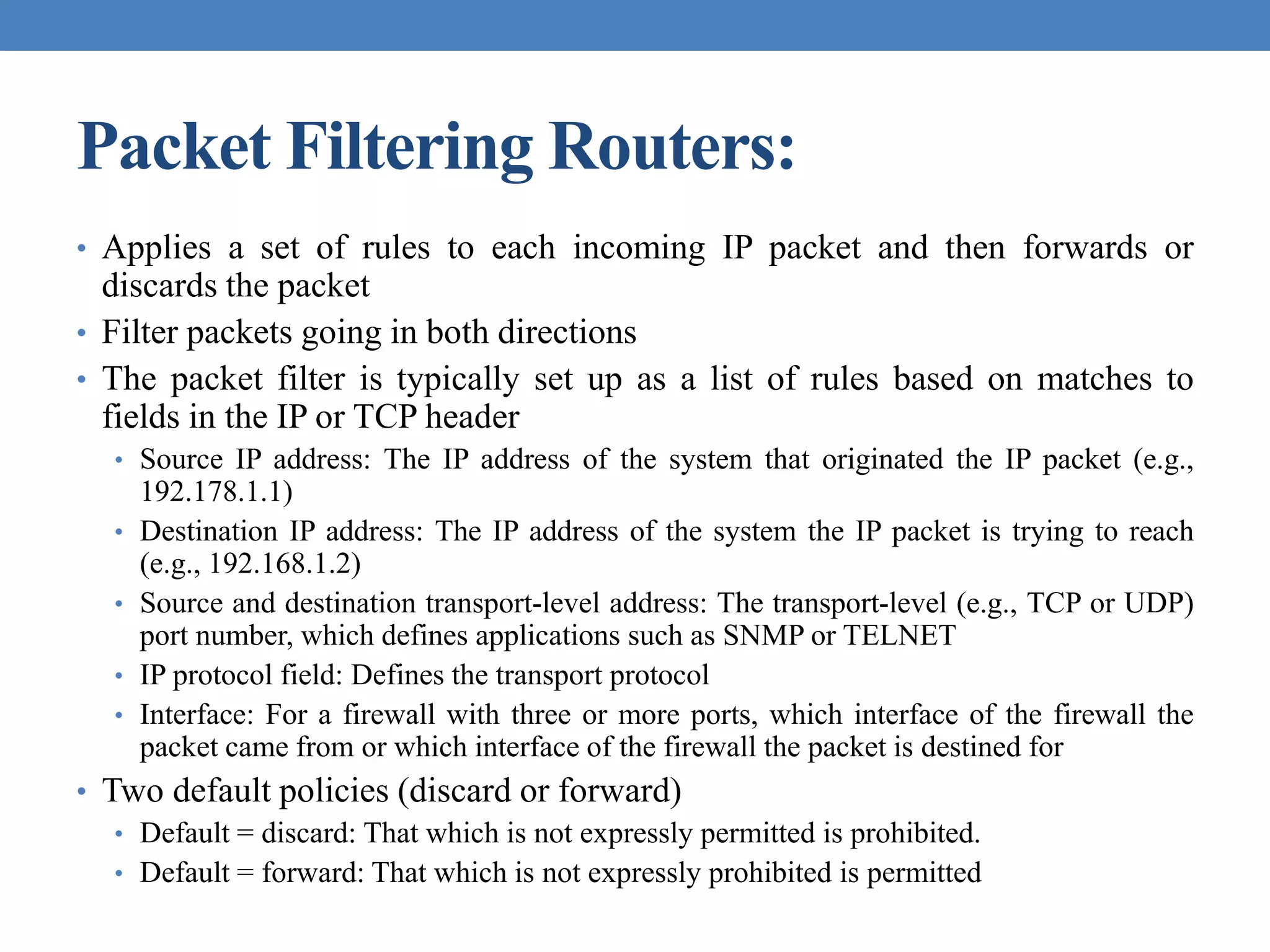
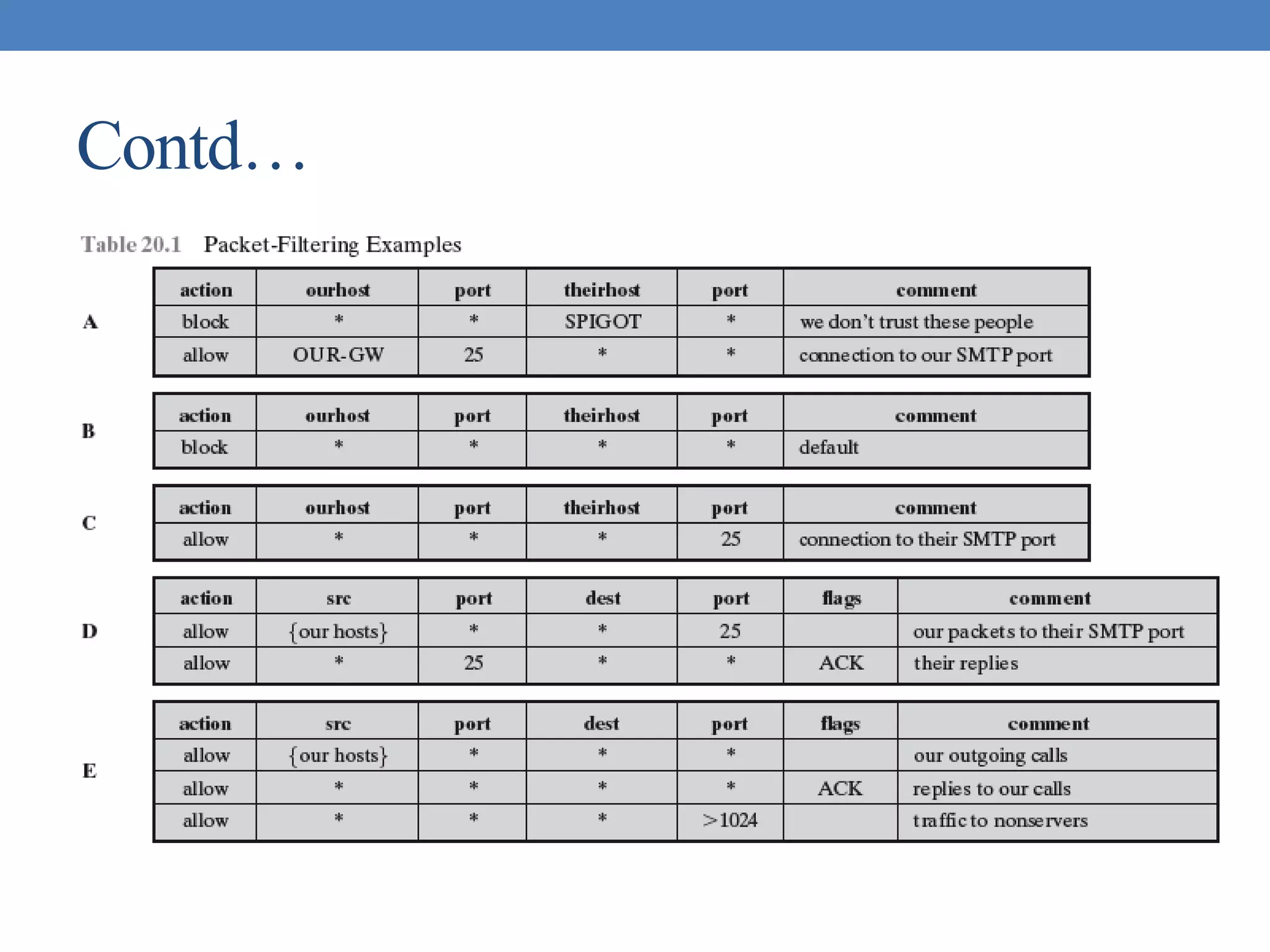
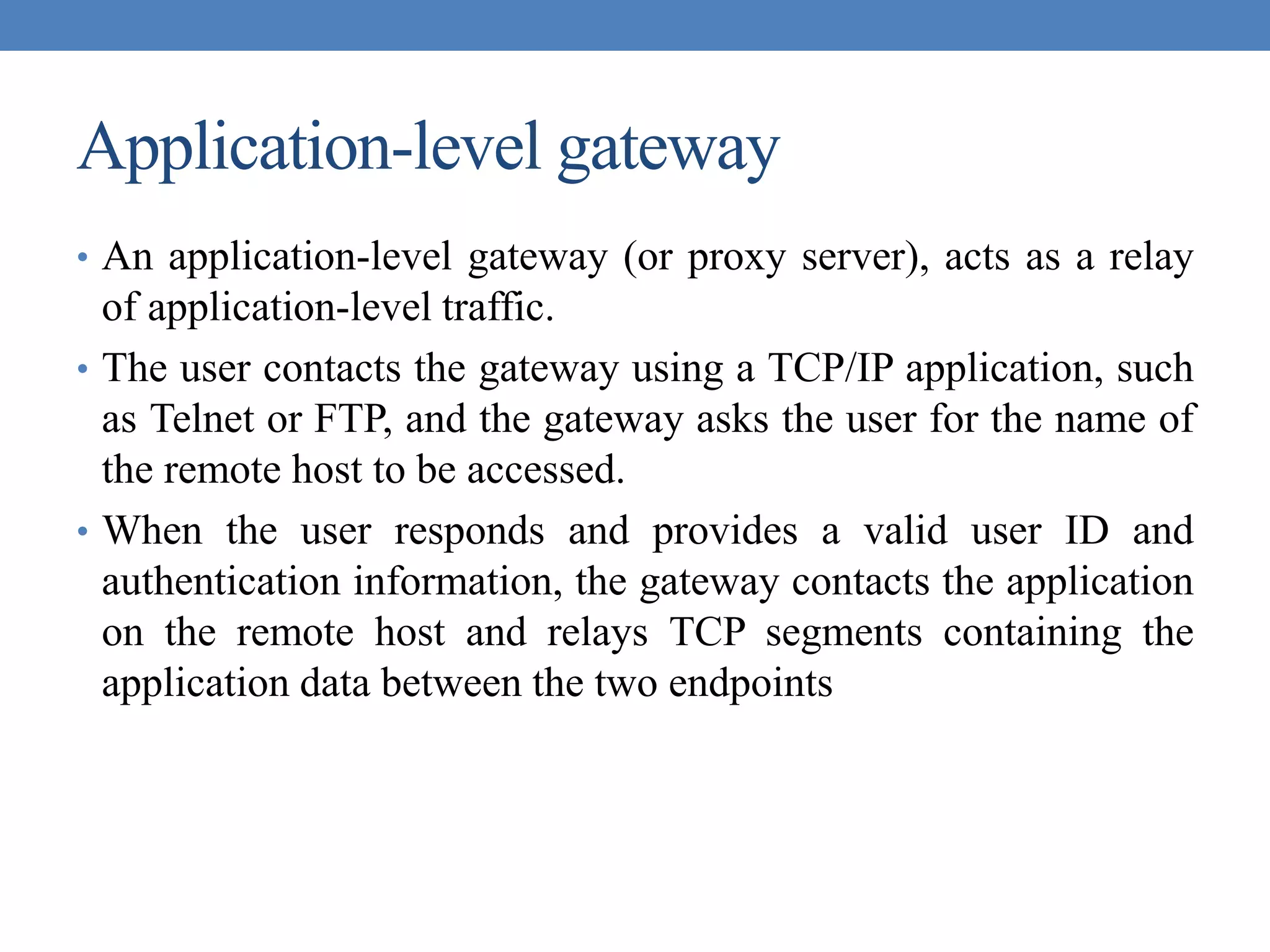
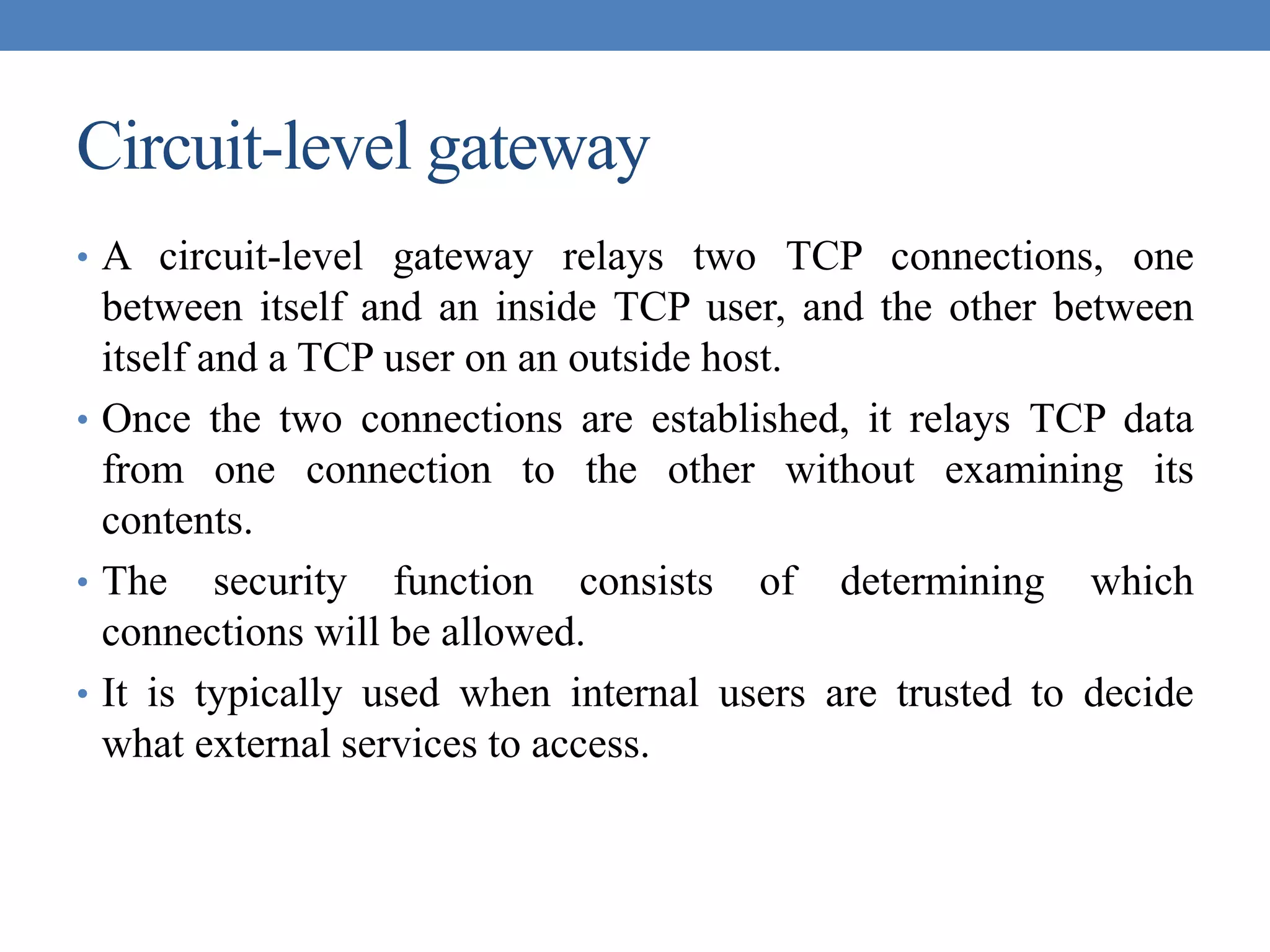
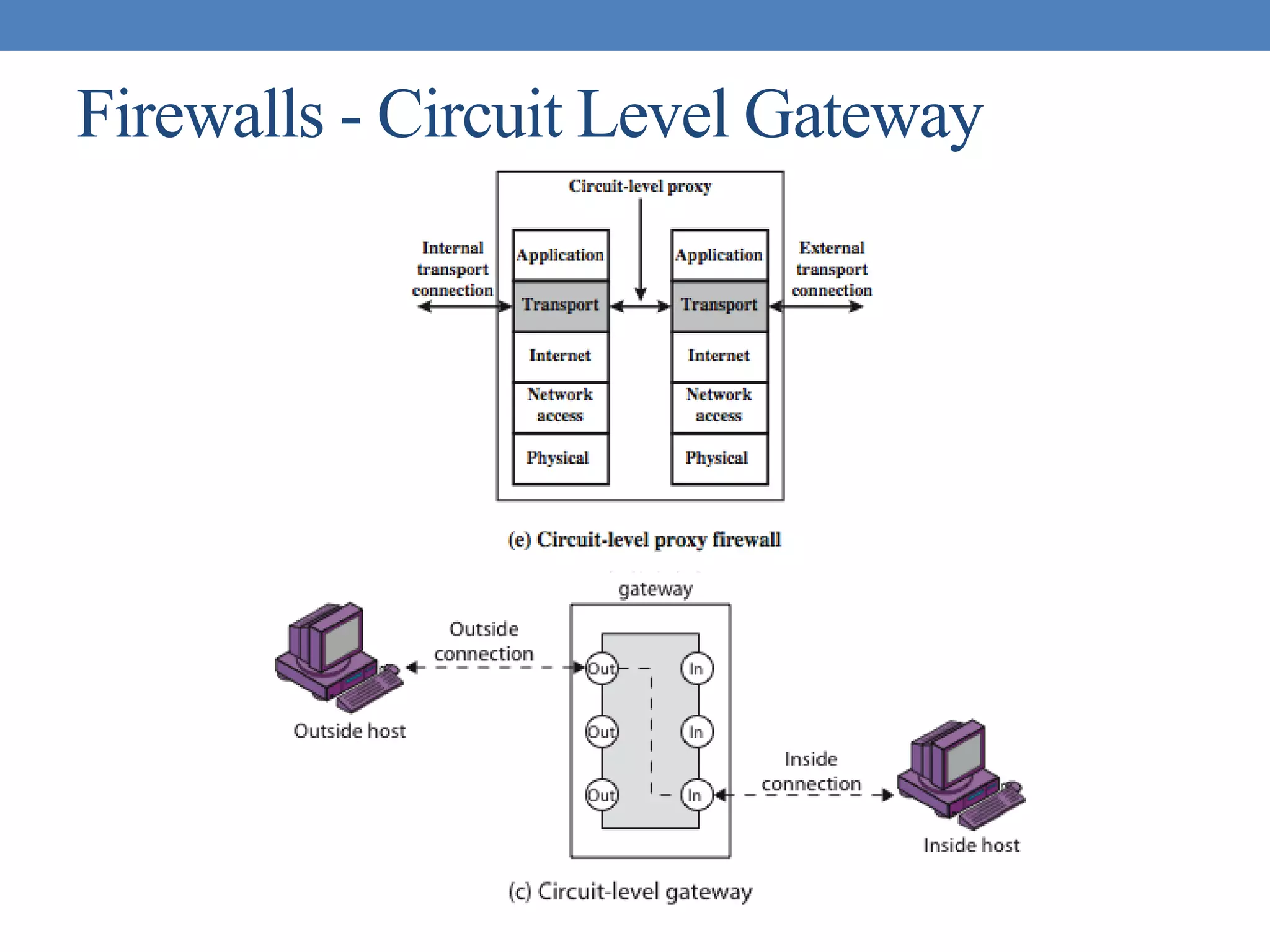
The document discusses intrusion detection and various types of intruders and intrusion techniques. It covers password capture methods like watching someone enter their password or using a Trojan horse. It also discusses different types of intrusion detection approaches like statistical anomaly detection, rule-based detection, and honeypots. The document then covers password management, viruses, worms, and distributed denial of service attacks. It concludes by discussing firewall design principles and characteristics like packet filtering routers.