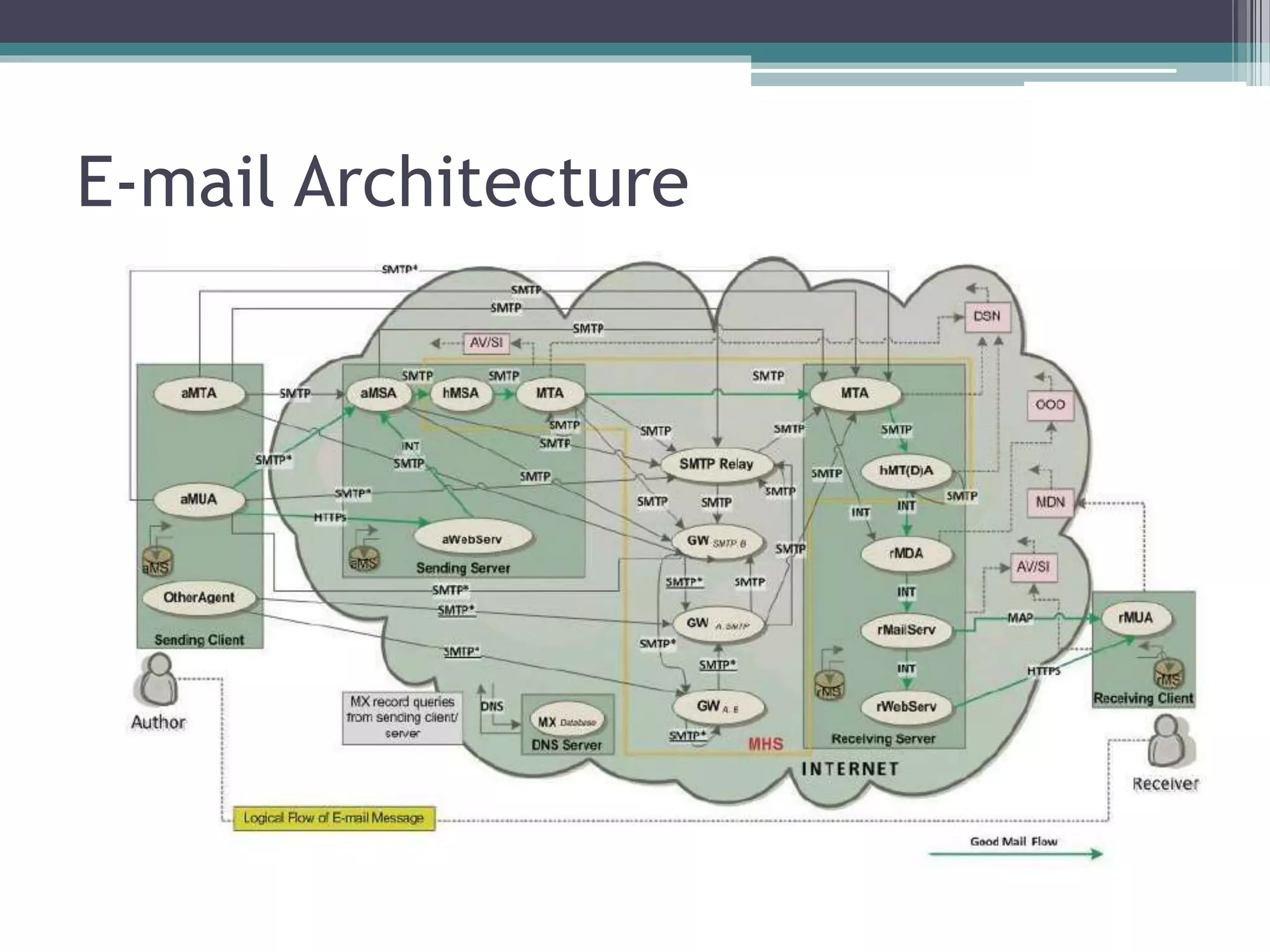
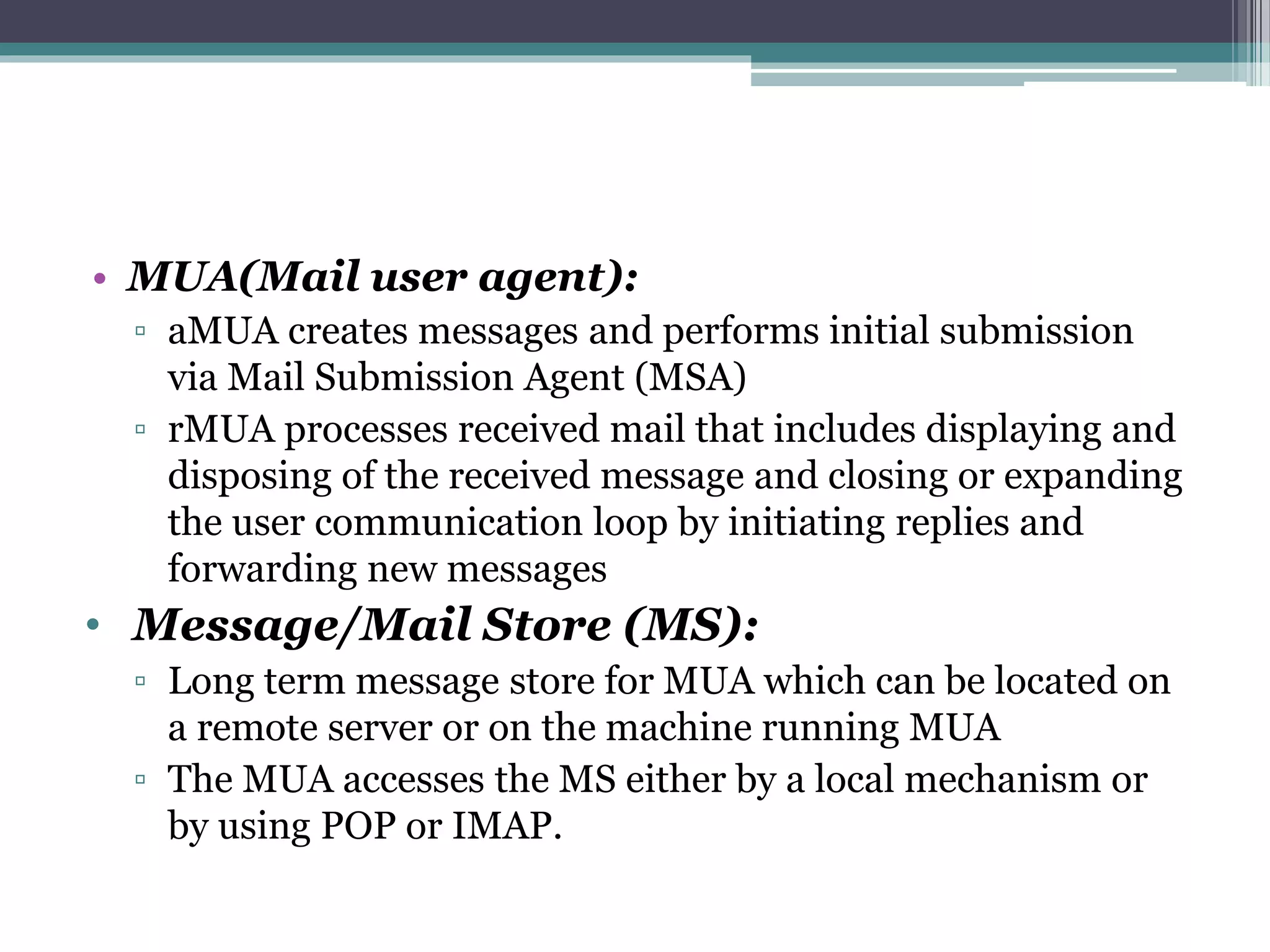
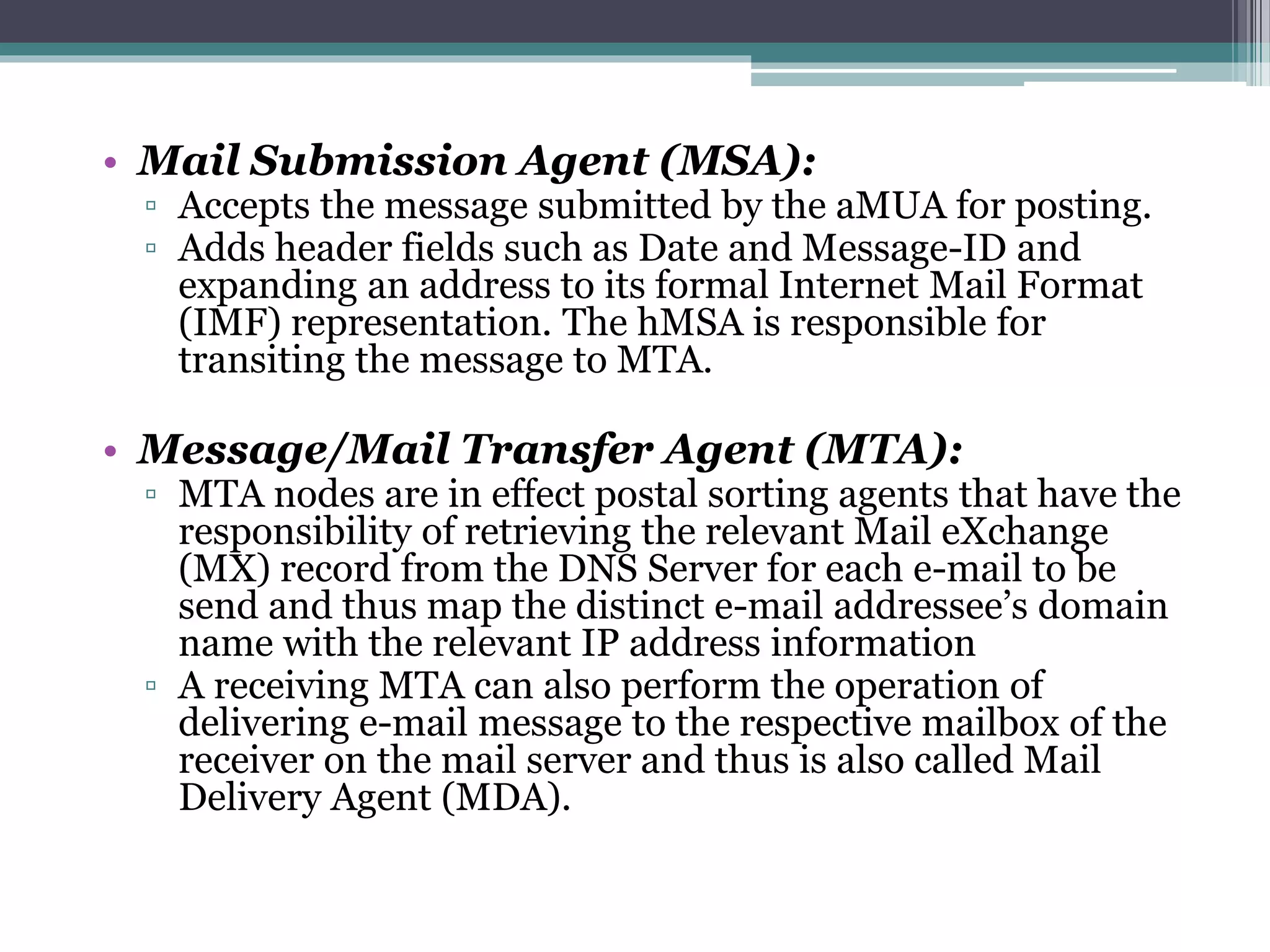
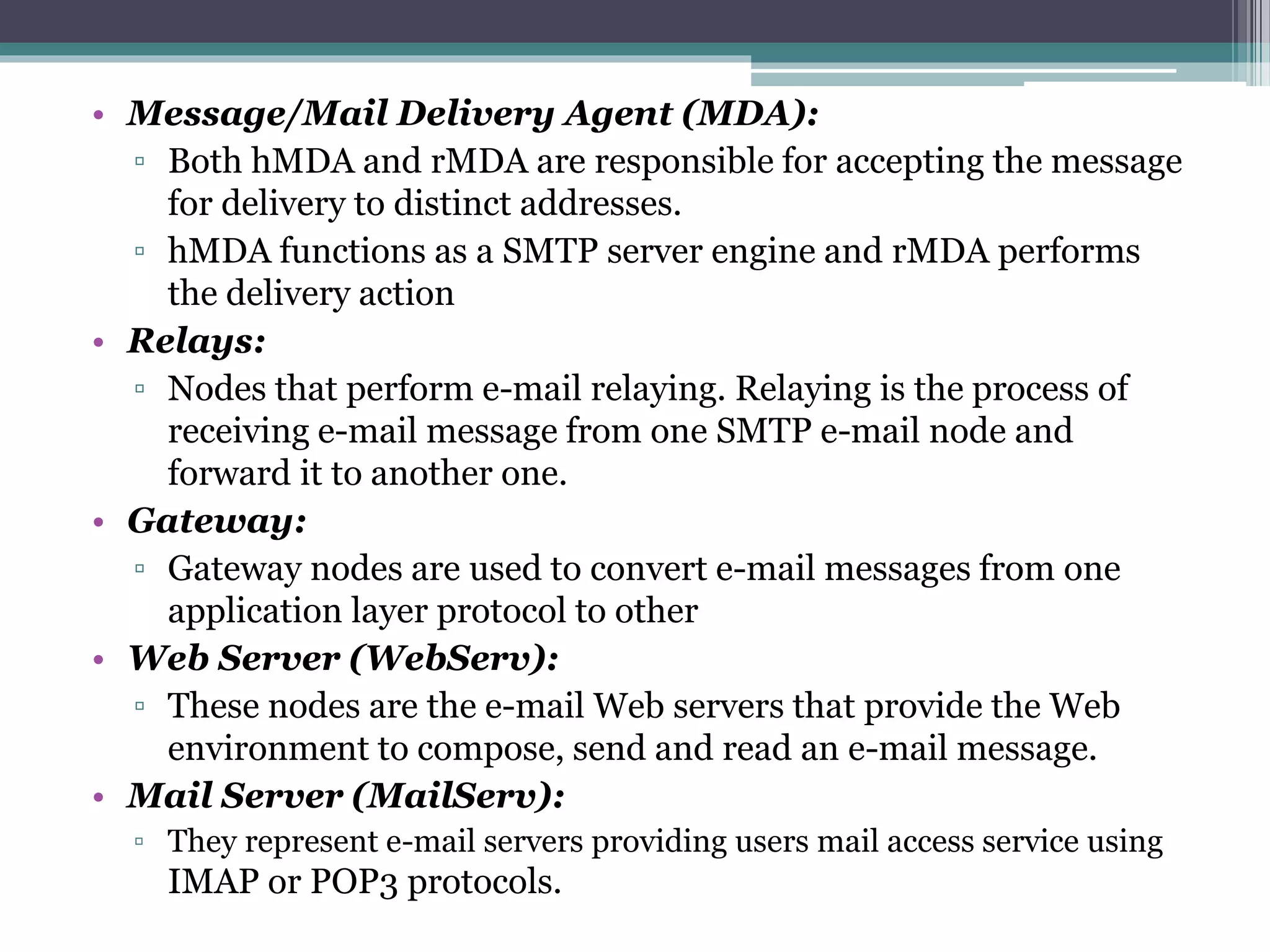
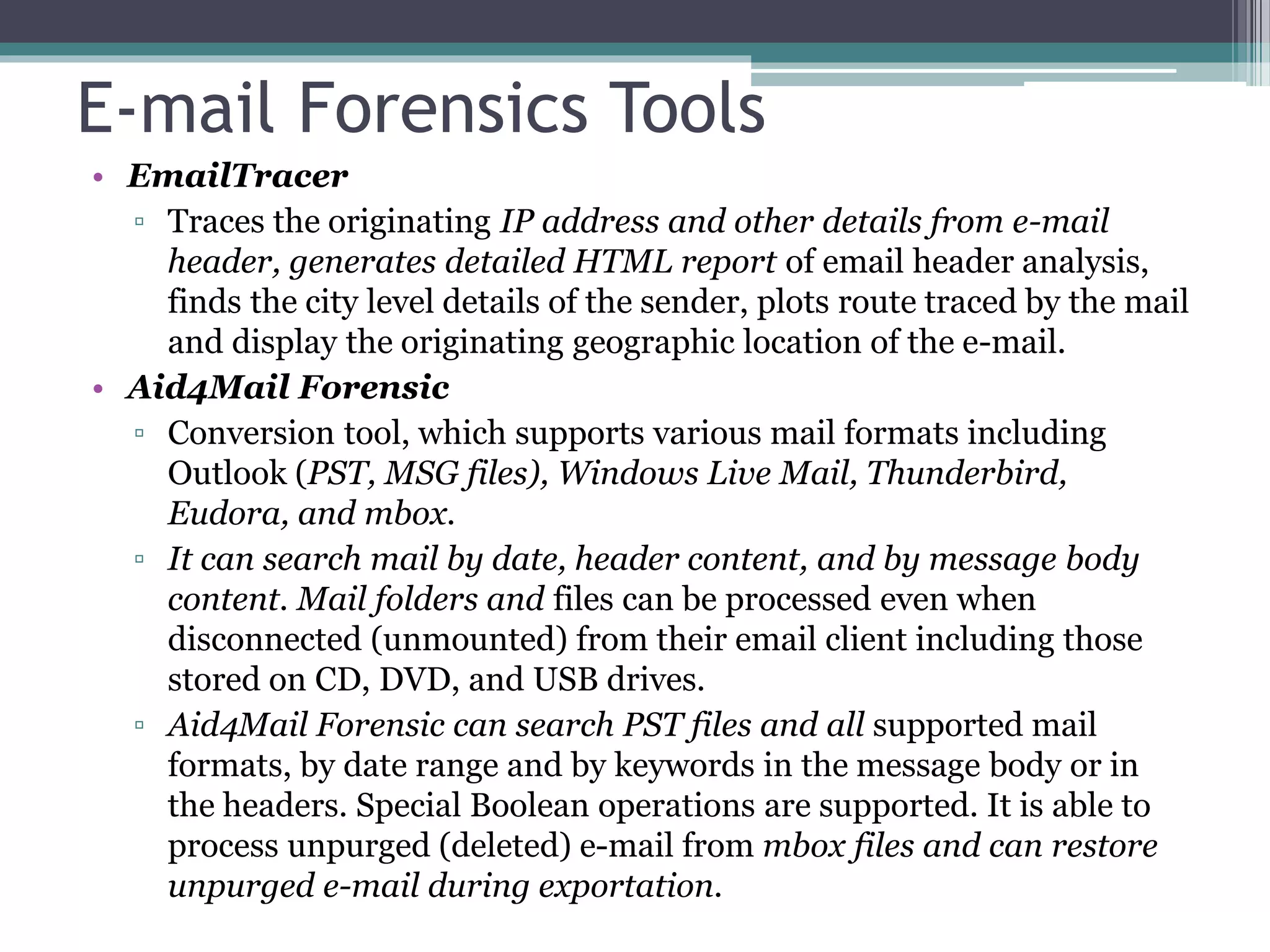
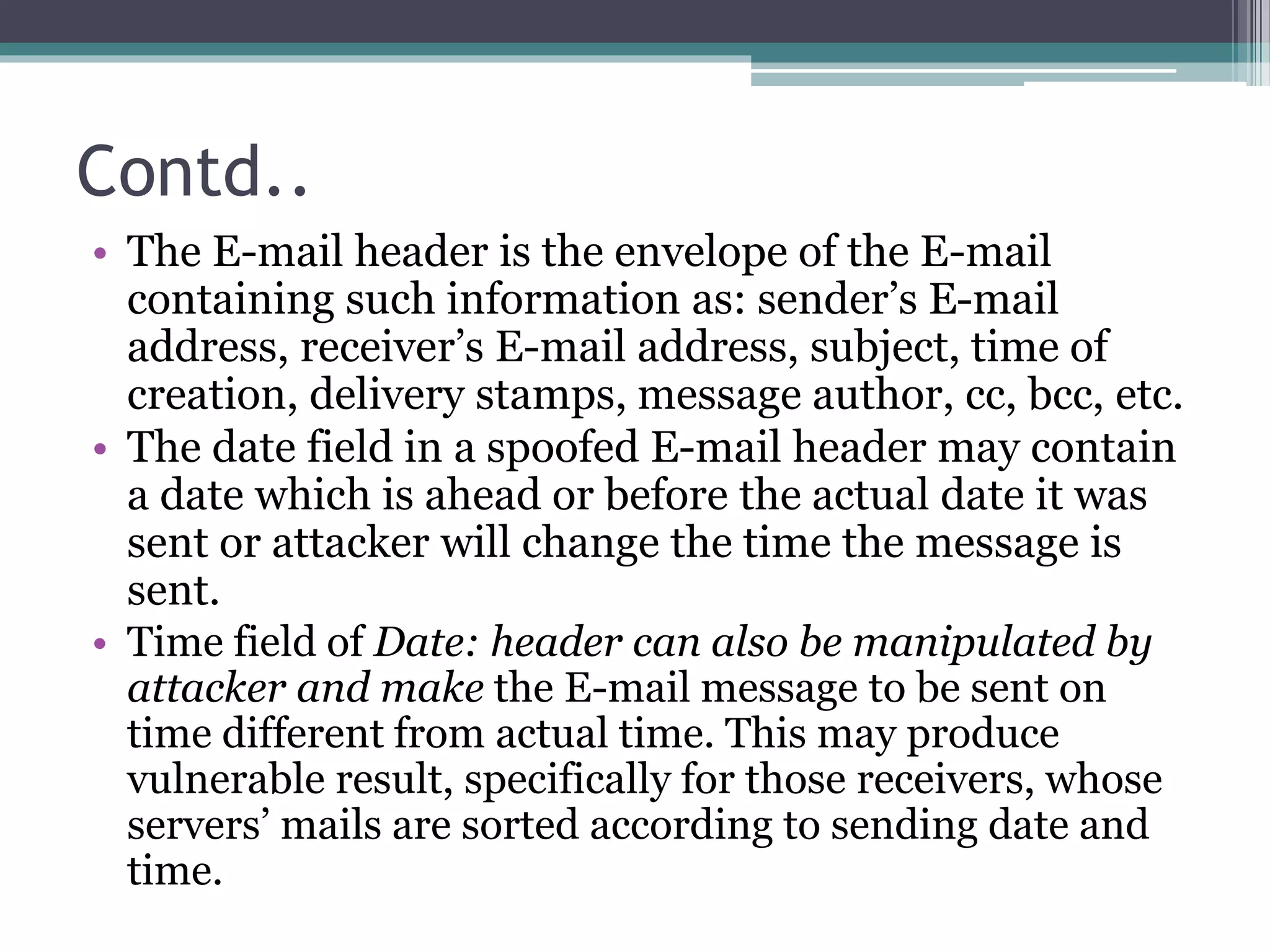
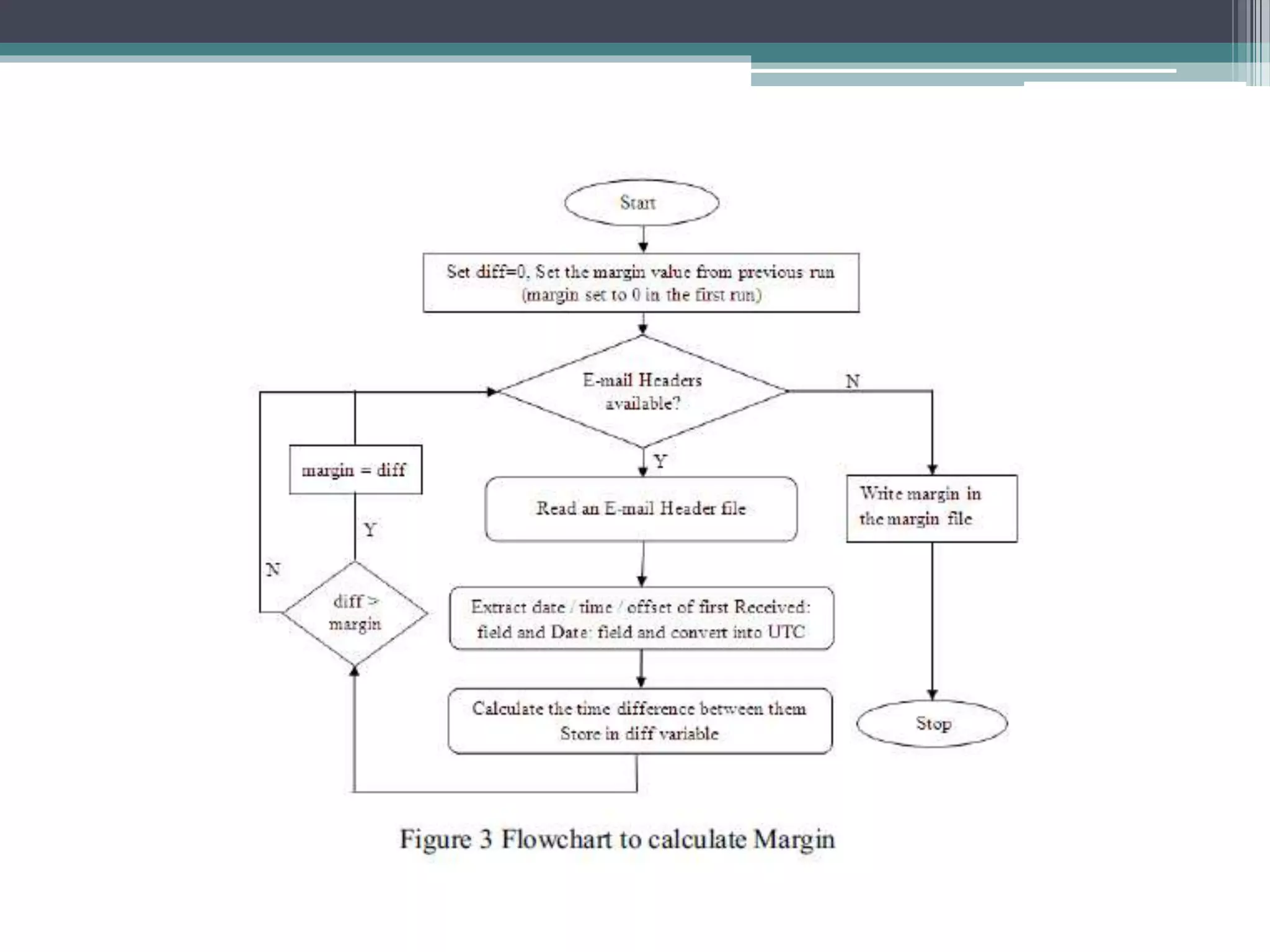
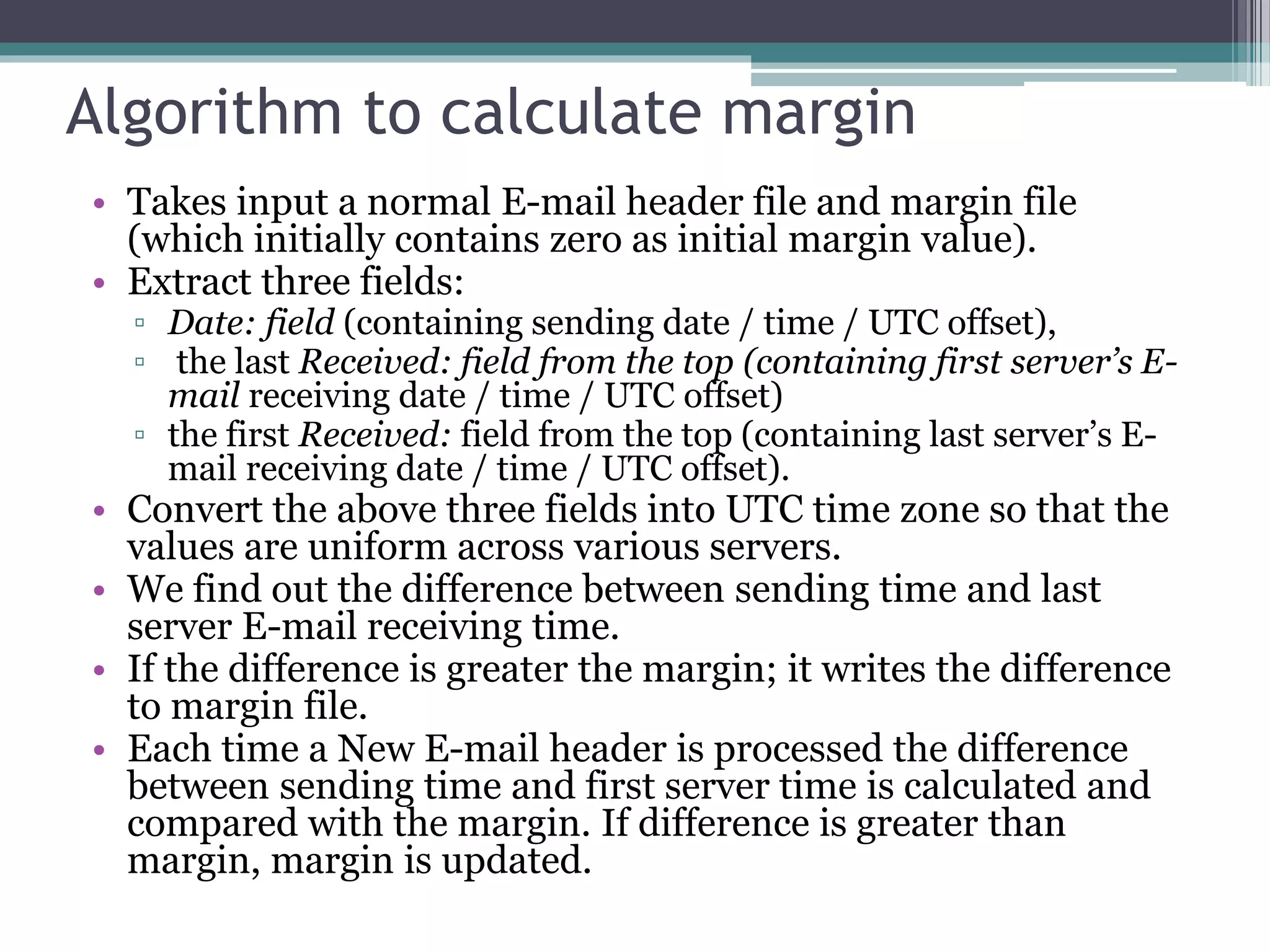
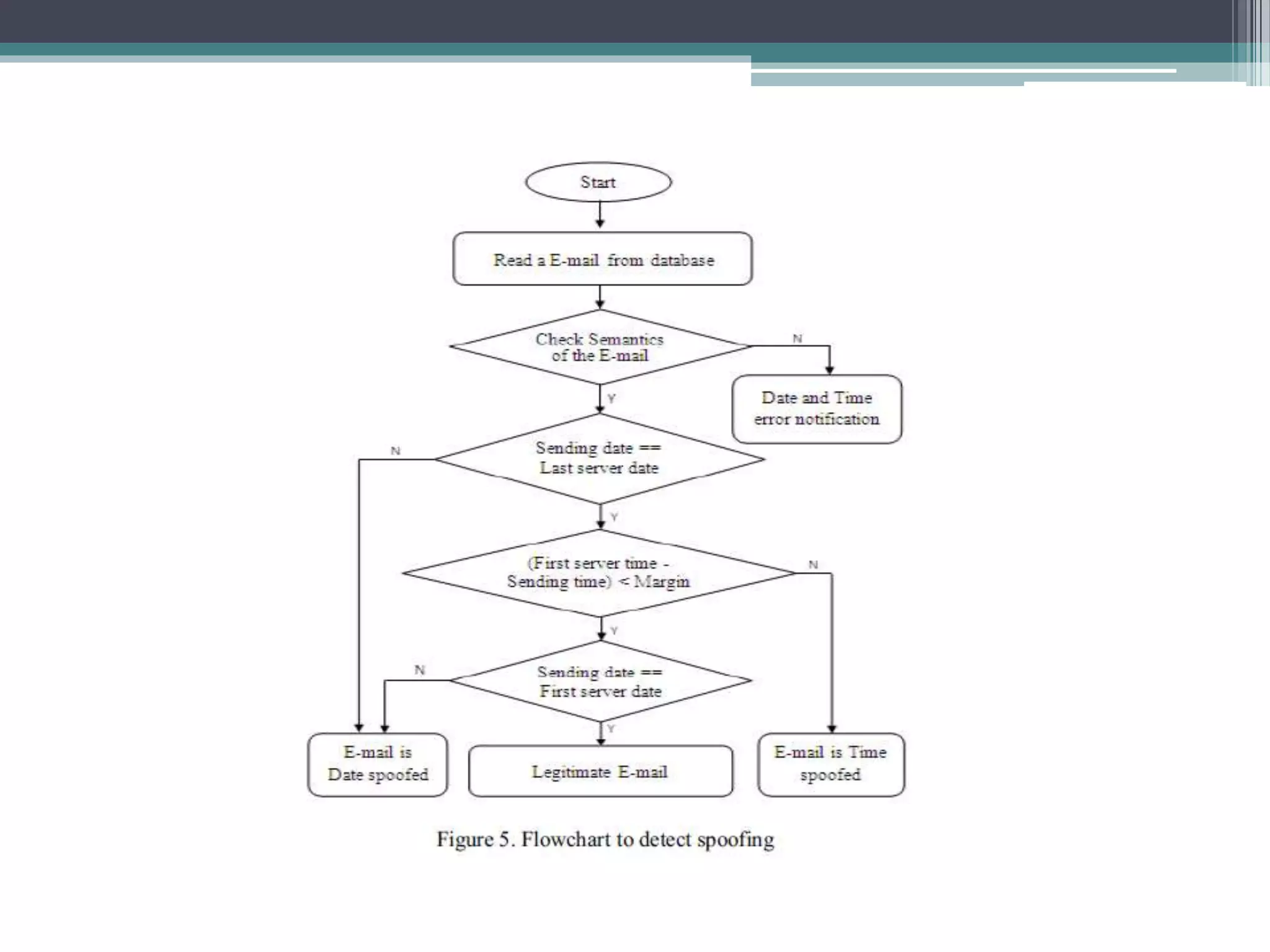
The document discusses e-mail forensics. It begins by describing the architecture of e-mail systems, including mail user agents, message stores, mail submission and transfer agents, and mail delivery agents. It then discusses common e-mail client attacks like malware distribution, phishing, spam, and denial-of-service attacks. The document outlines techniques for e-mail forensic investigation such as header analysis and server investigation. It also presents tools that can be used for e-mail forensics and summarizes a research paper on detecting e-mail date and time spoofing through analysis of header fields.










![References
[1] Preeti Mishra, Emmanuel S. Pilli and R. C.
Joshi-”Forensic Analysis of E-mail Date and
Time Spoofing”-2012 Third International
Conference on Computer and Communication
Technology
[2] M. Tariq Banday-”Techniques And Tools For
Forensic Investigation Of E-mail”-International
Journal of Network Security & Its Applications
(IJNSA), Vol.3, No.6, November 2011
[3] http://www.spamlaws.com/different-types-
email-exploits.html](https://image.slidesharecdn.com/e-mailforensics-161124053030/75/E-mail-forensics-21-2048.jpg)