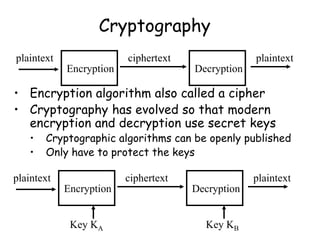
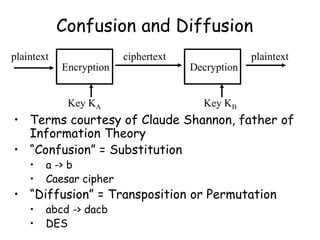
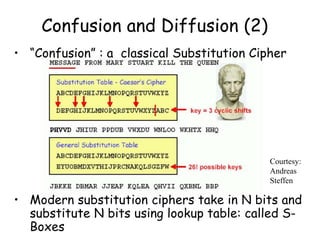
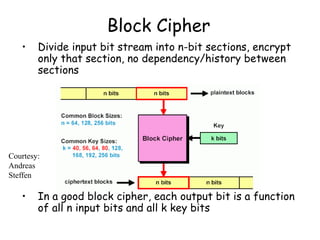
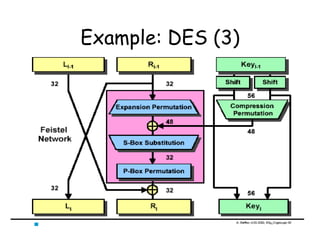
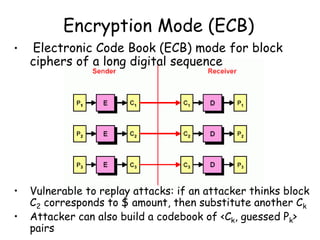
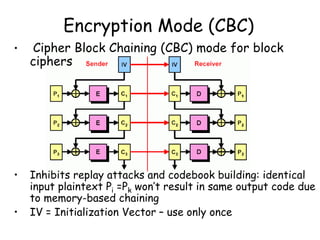
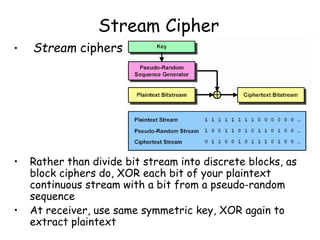
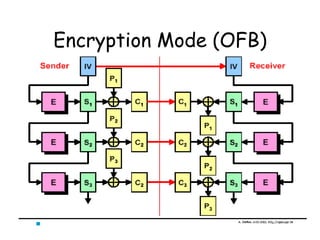
This document provides an introduction to symmetric block ciphers. It discusses how symmetric block ciphers use the same secret key for encryption and decryption. The key must be securely distributed and kept secret. Examples of symmetric block ciphers include the Data Encryption Standard (DES) and the Advanced Encryption Standard (AES). The document also covers cryptanalysis techniques, the principles of confusion and diffusion, block cipher structure, encryption modes like ECB and CBC, and compares block ciphers to stream ciphers.