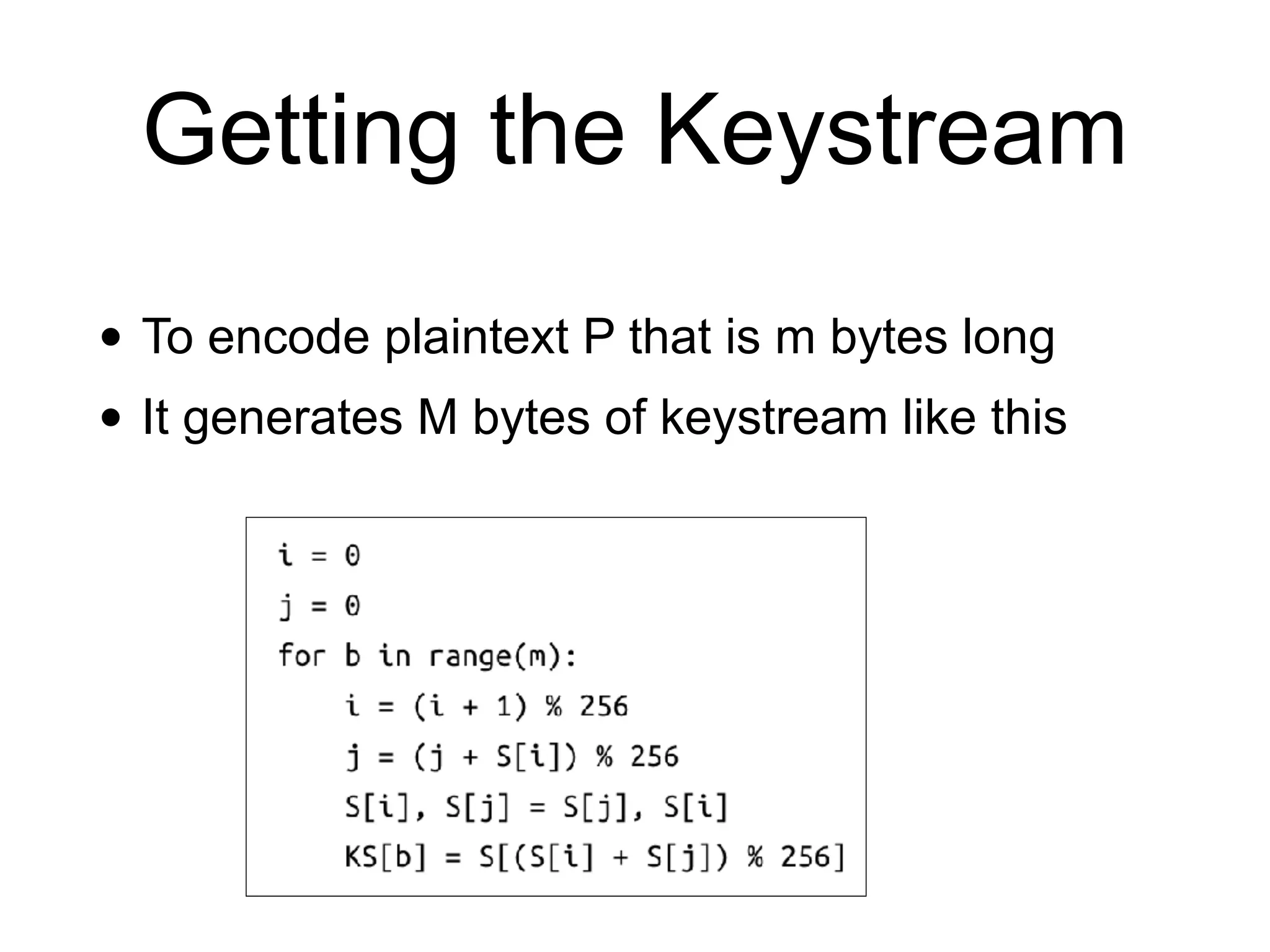
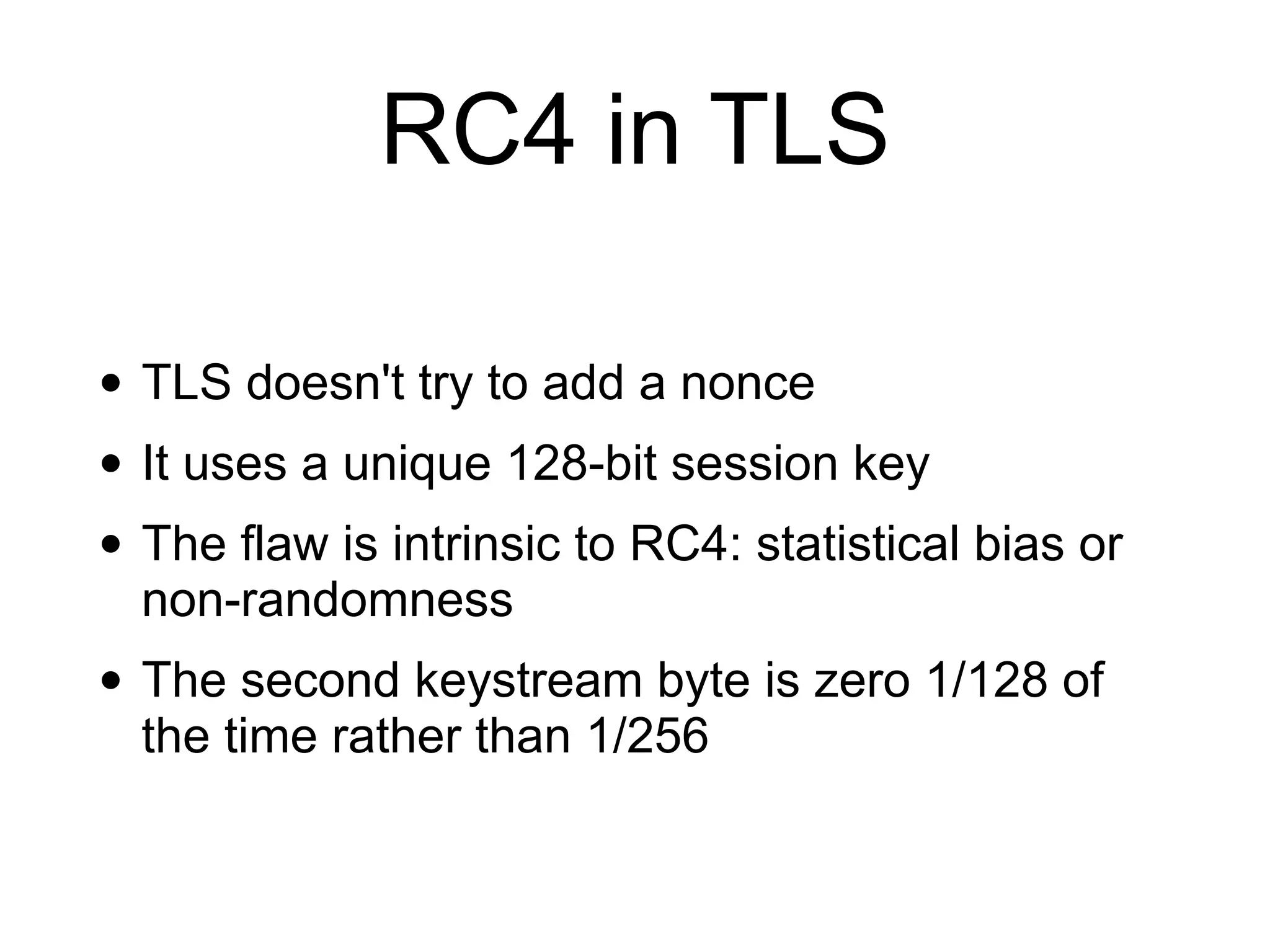
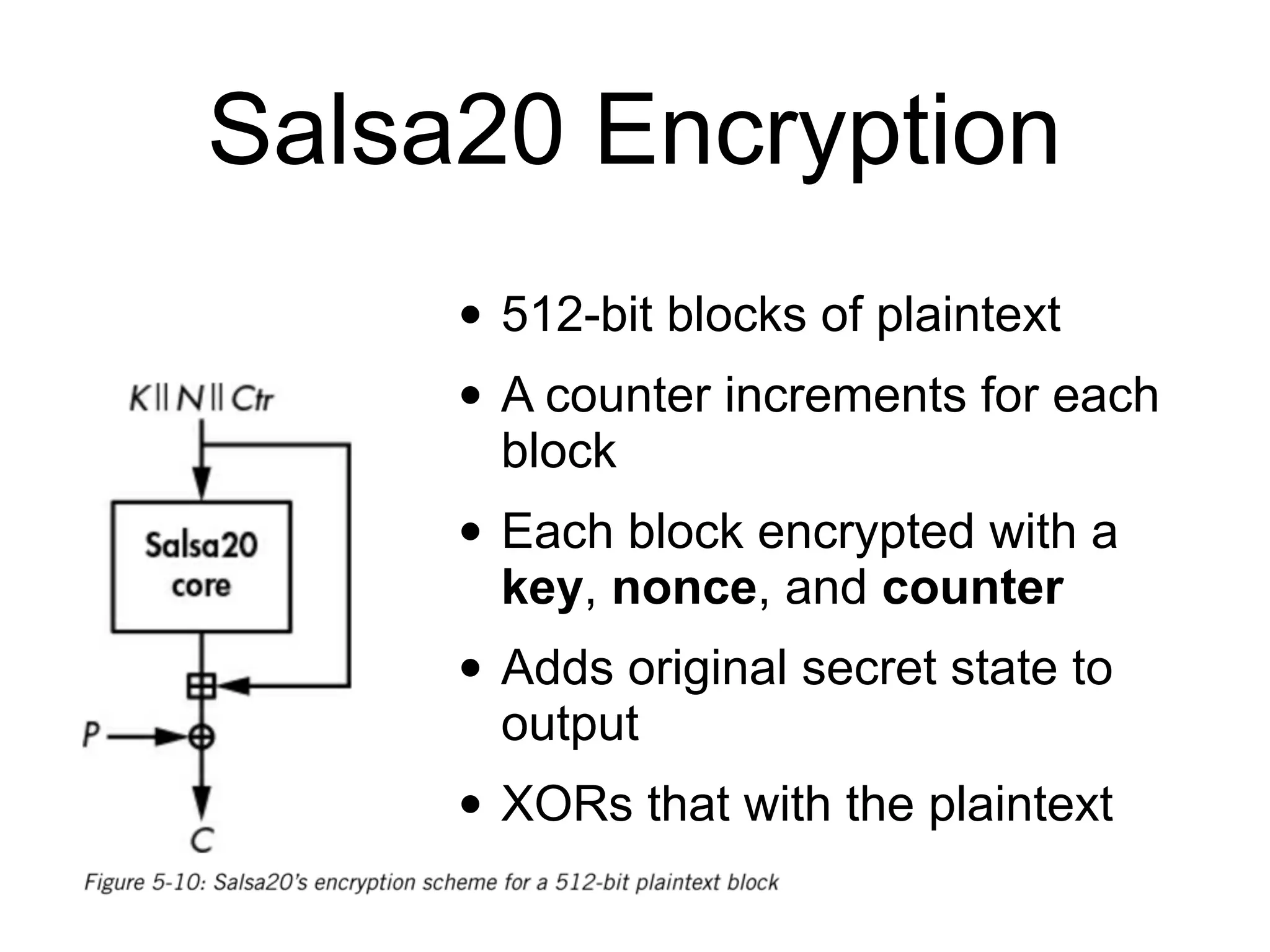
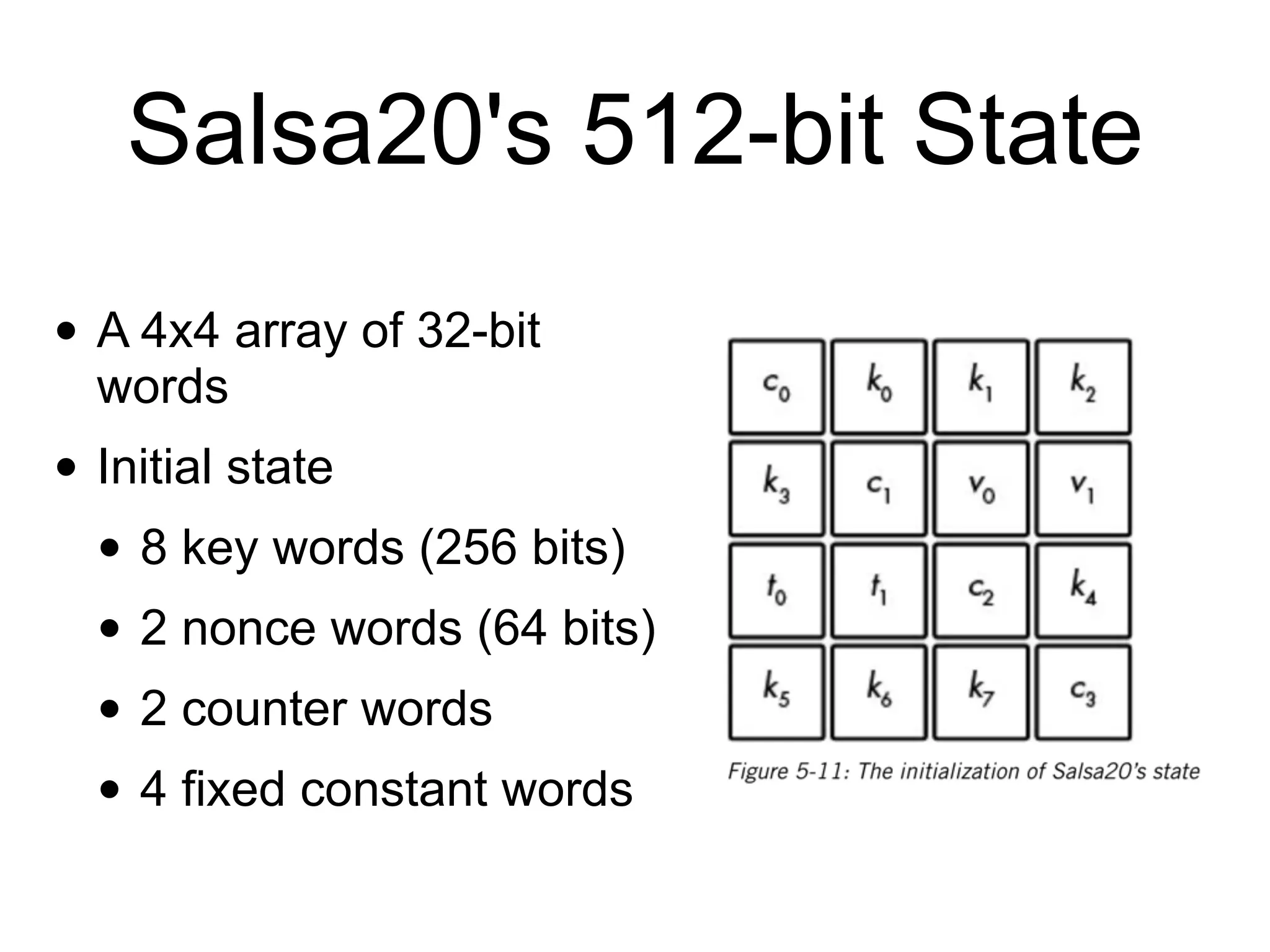
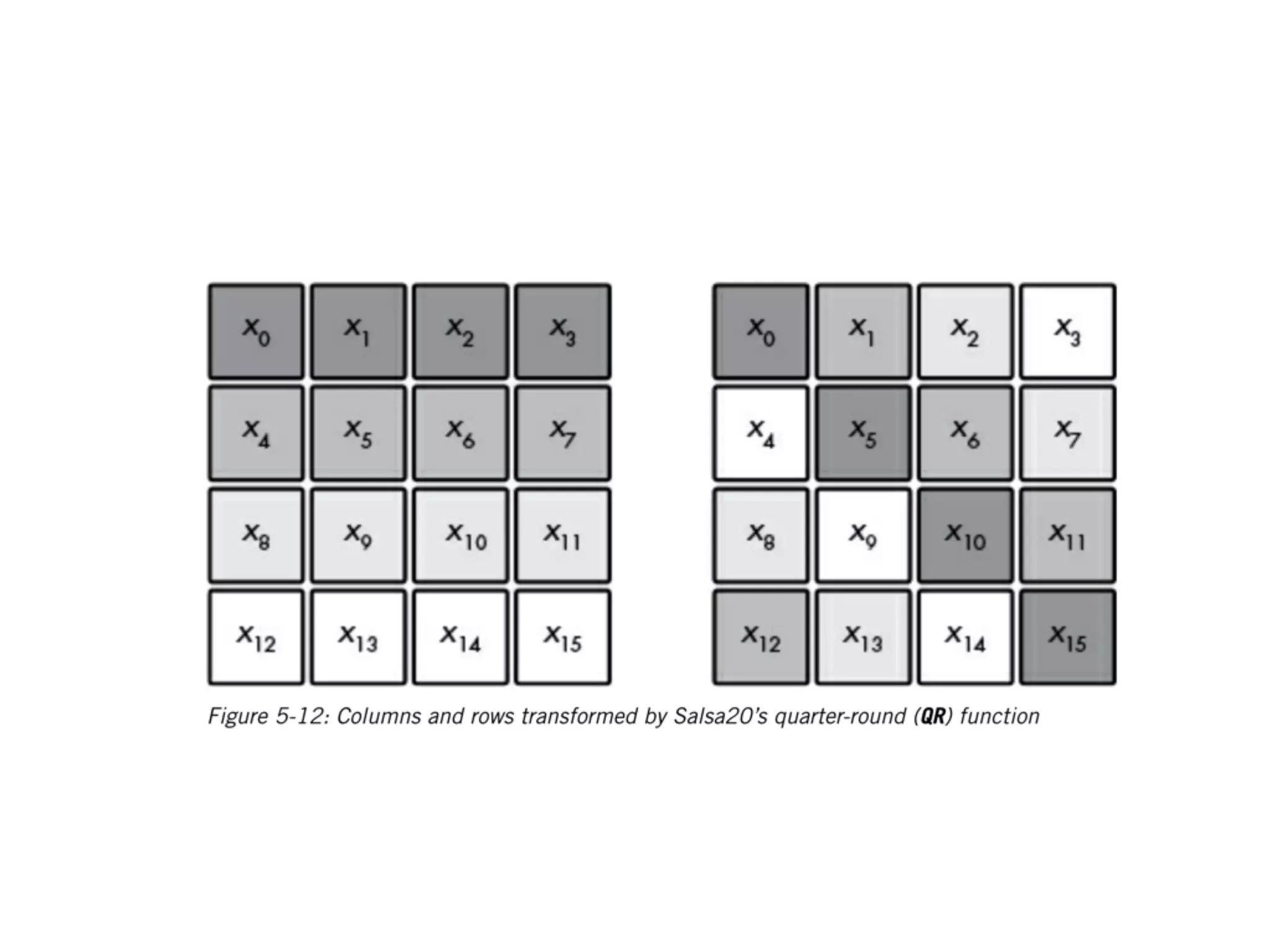
The document discusses stream ciphers in cryptography, detailing their operation, types (stateful and counter-based), and vulnerabilities like nonce reuse and attacks, using examples such as Grain-128a and A5/1. It contrasts hardware-oriented and software-oriented implementations, highlighting efficiency and security weaknesses in popular algorithms like RC4 and WEP. The document emphasizes the importance of unique keys and nonces to maintain security in encrypted communications.






















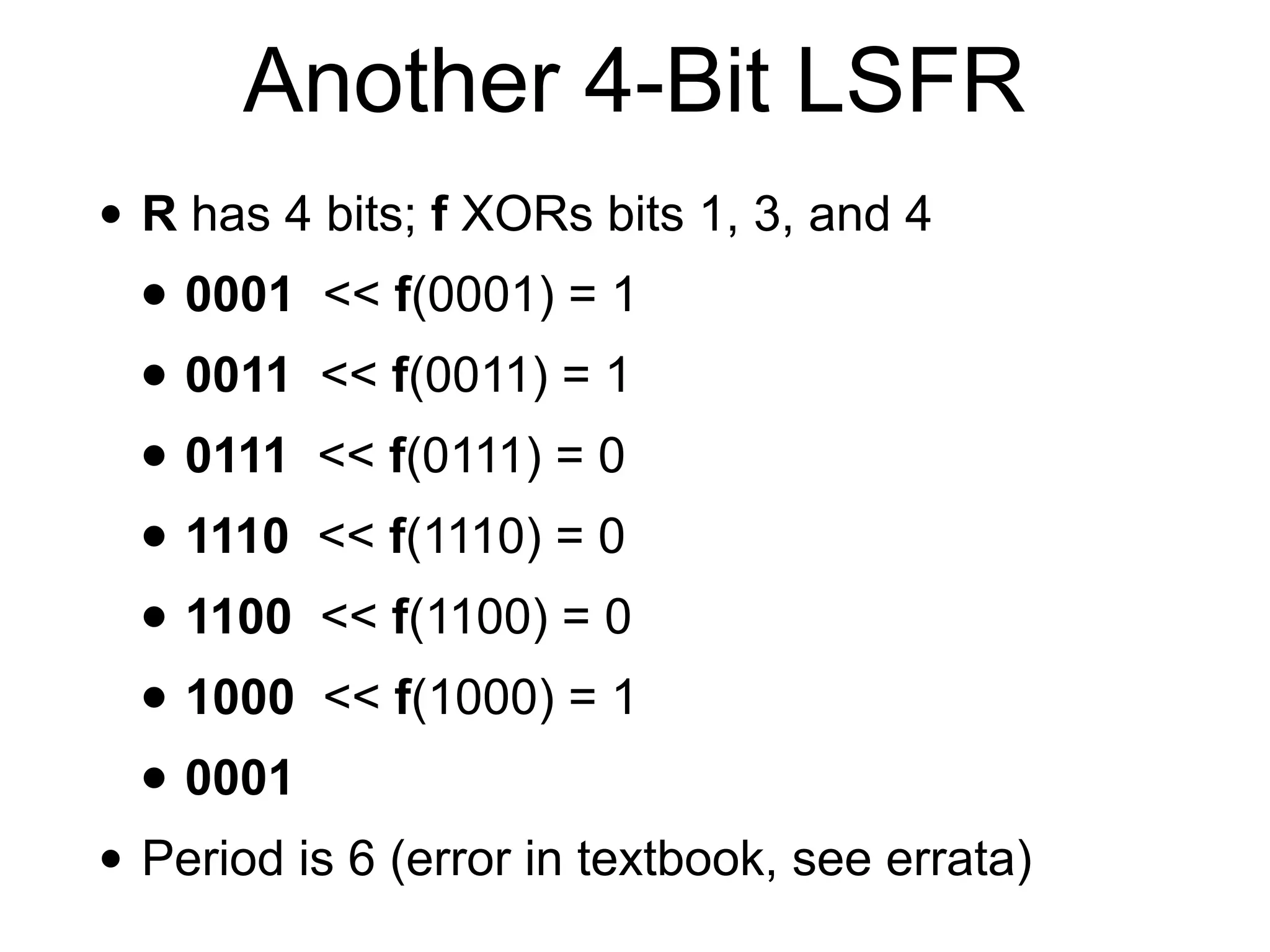























![How RC4 Works
• Internal state is 256 bytes, starting at
• S[0]=0; S[1]=1; S[2]=2, ... S[255]=255
• All it does is shuffle those values around like a
deck of cards
• No XOR or OR or AND](https://image.slidesharecdn.com/141-ch5-190225184701/75/CNIT-141-5-Stream-Ciphers-53-2048.jpg)