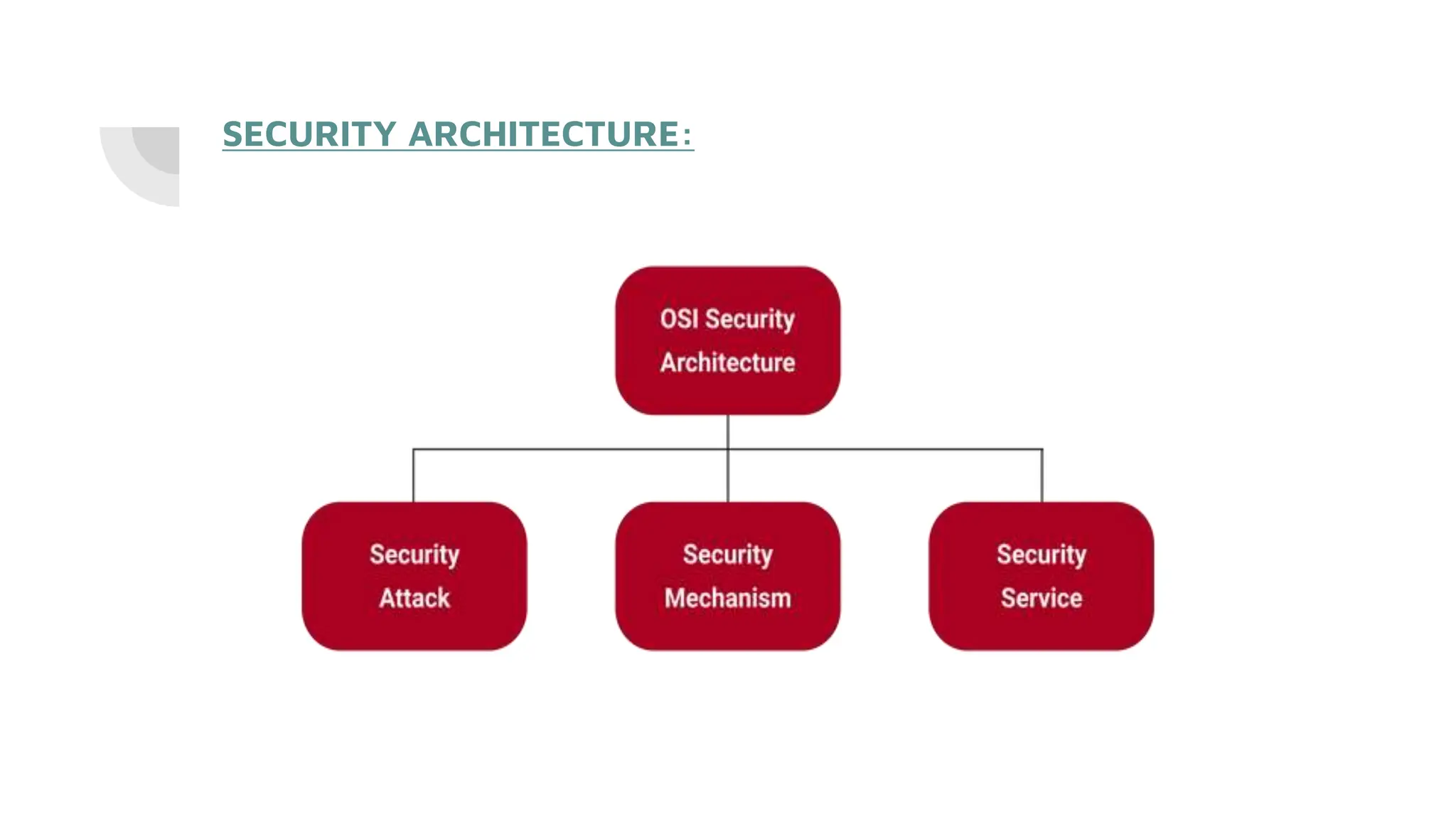
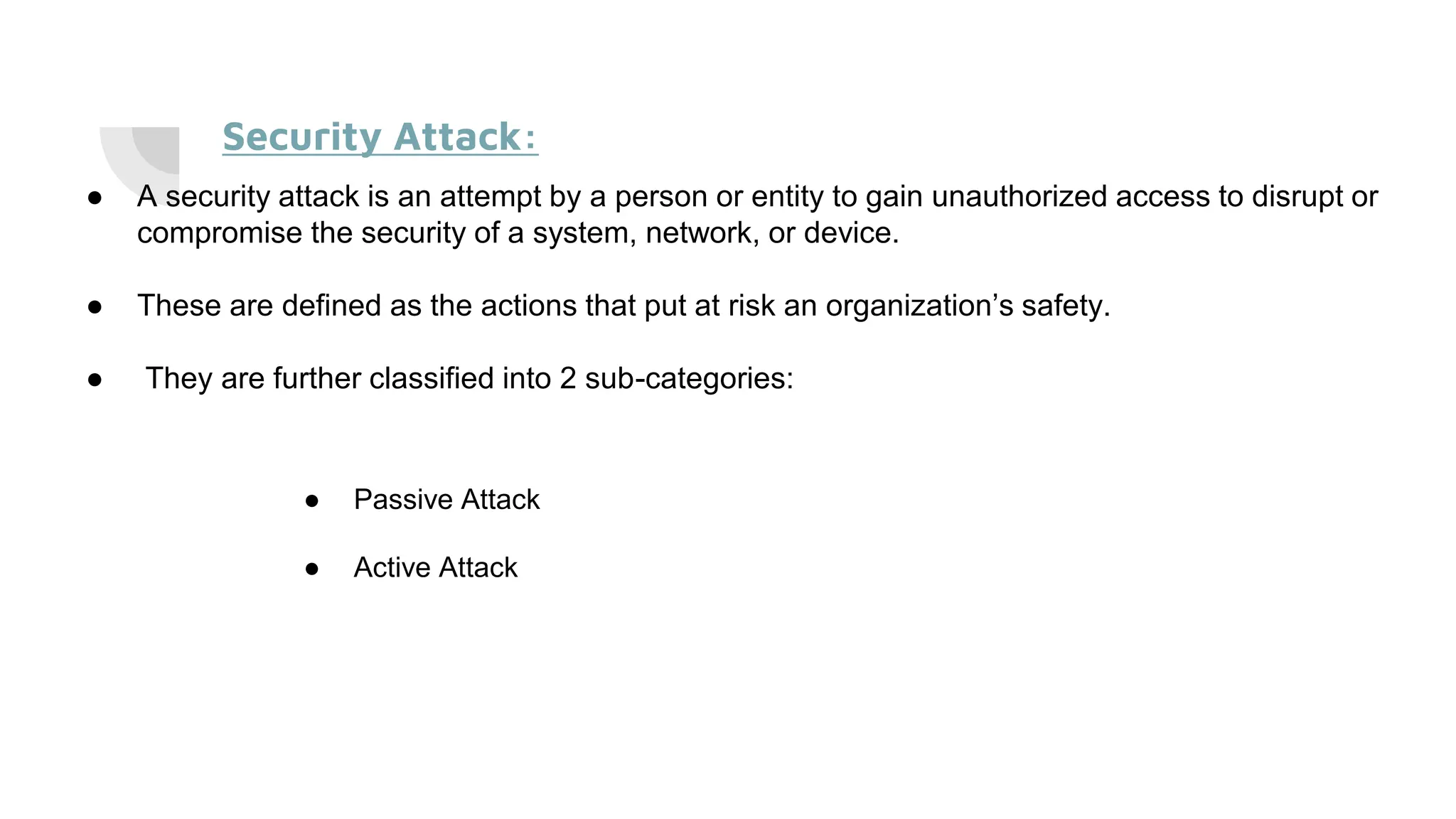
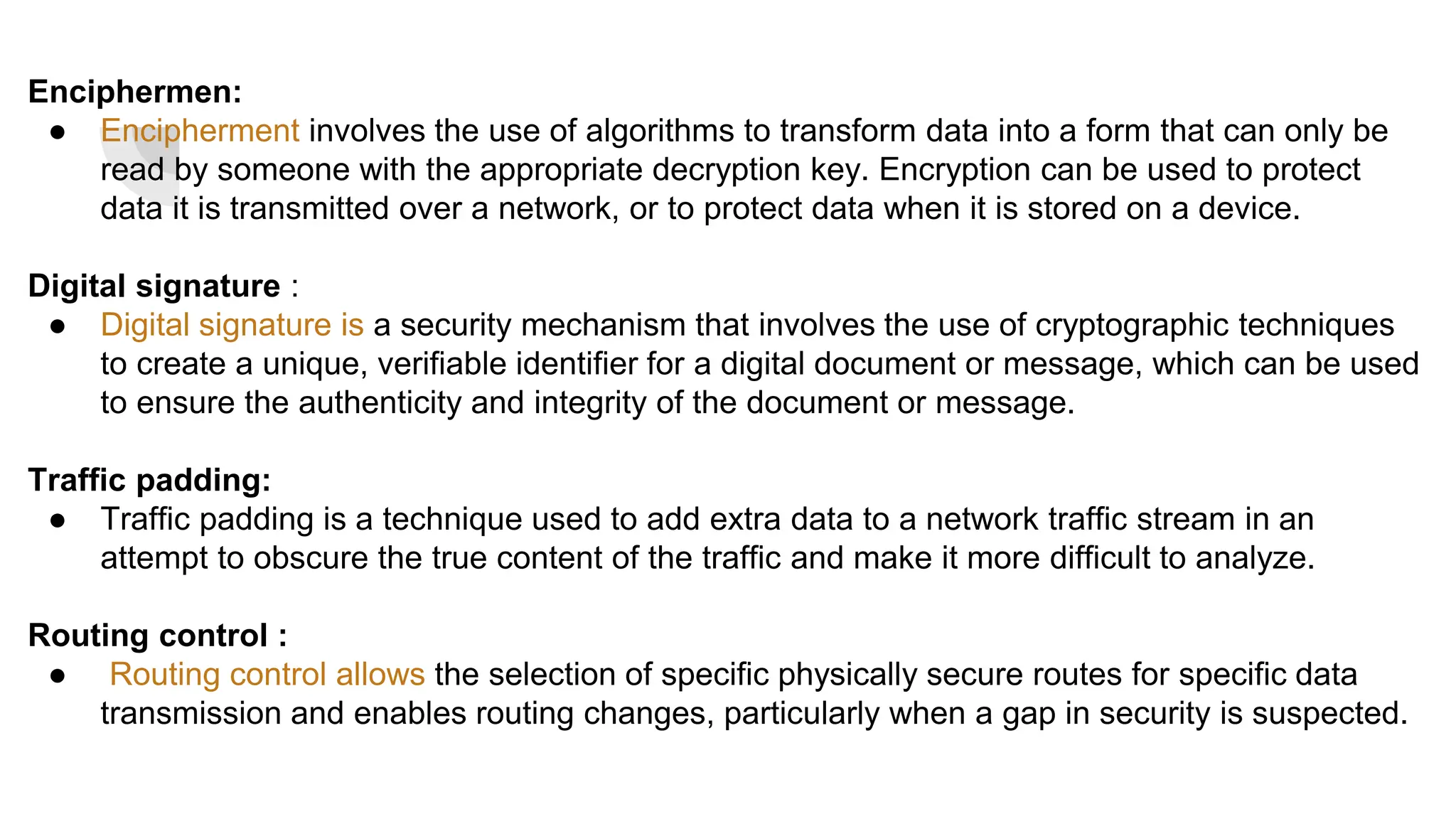
The document discusses the OSI (Open Systems Interconnection) security architecture. It defines the OSI security architecture as providing a systematic approach to security across the seven layers of the OSI model. It ensures confidentiality, integrity, and availability of data through security services and mechanisms at each layer. Security services include authentication, access control, data integrity, and others. Security mechanisms implement these services and protect against attacks, such as encryption for confidentiality. The OSI security architecture provides organized security and meets international standards.