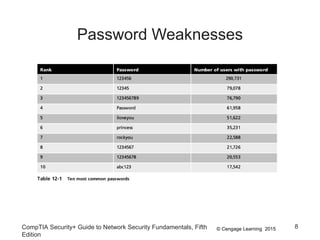
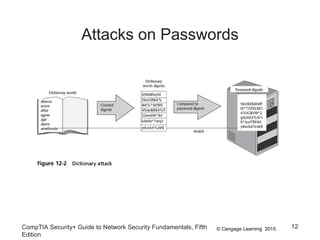
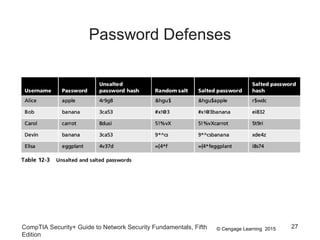
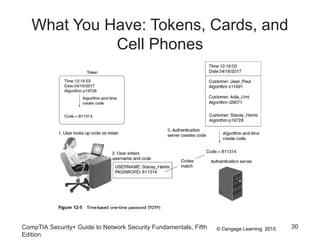
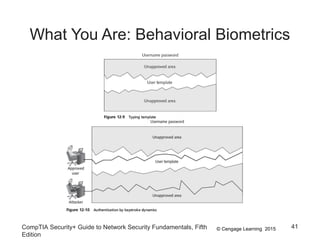
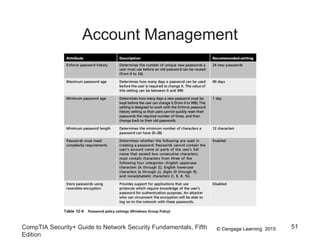
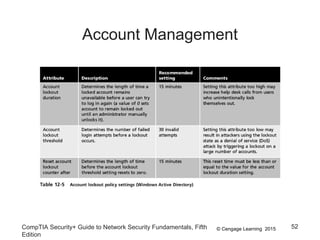
This document summarizes authentication methods and password security based on a chapter from the CompTIA Security+ Guide to Network Security Fundamentals. It describes different types of authentication credentials including what users know (passwords), have (tokens, cards, phones), are (biometrics), and do (behavioral patterns). It outlines vulnerabilities in passwords, common attacks, and defenses including complexity, hashing, and salts. Multi-factor authentication using multiple credential types provides stronger security than single-factor passwords alone.