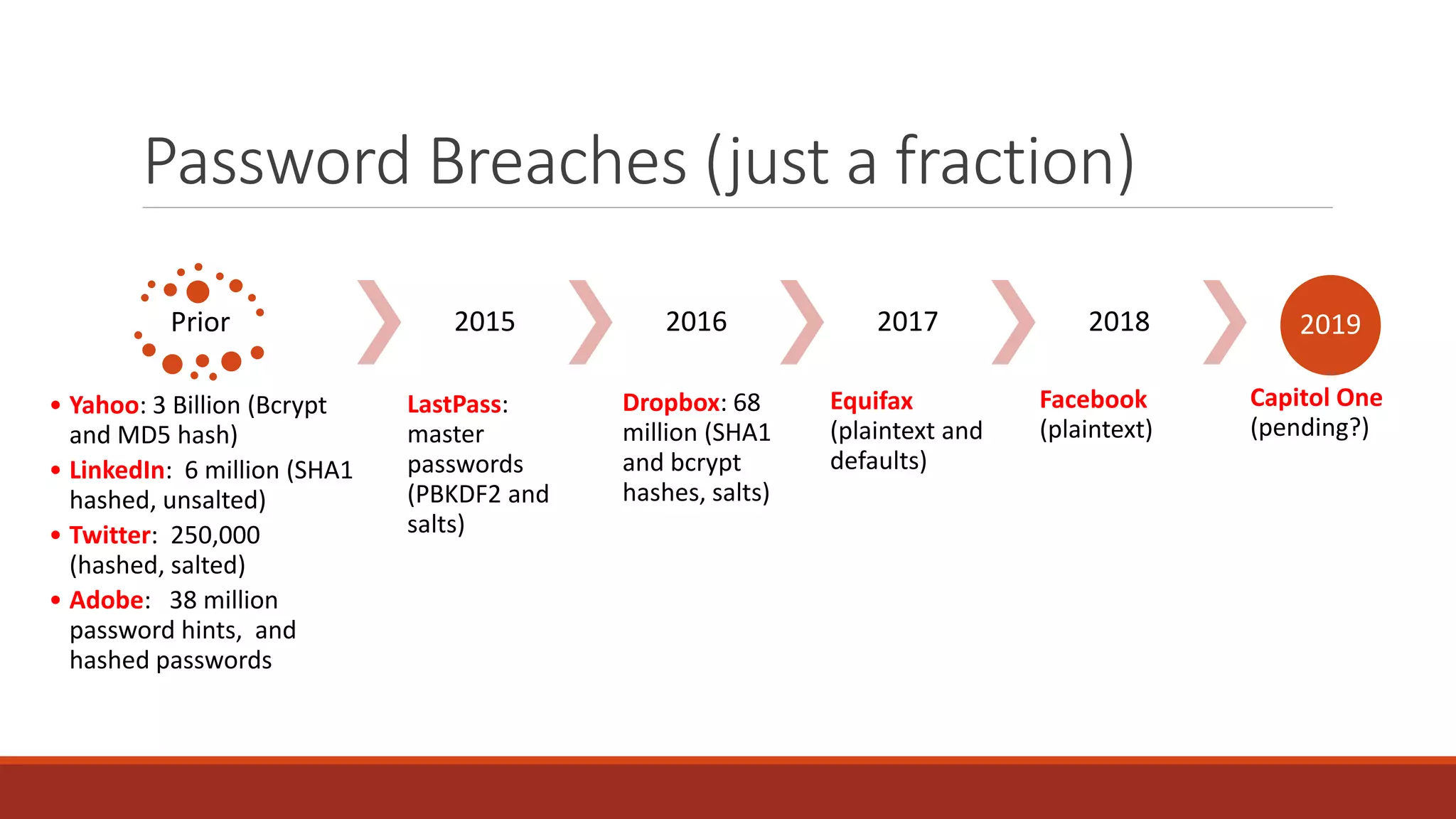
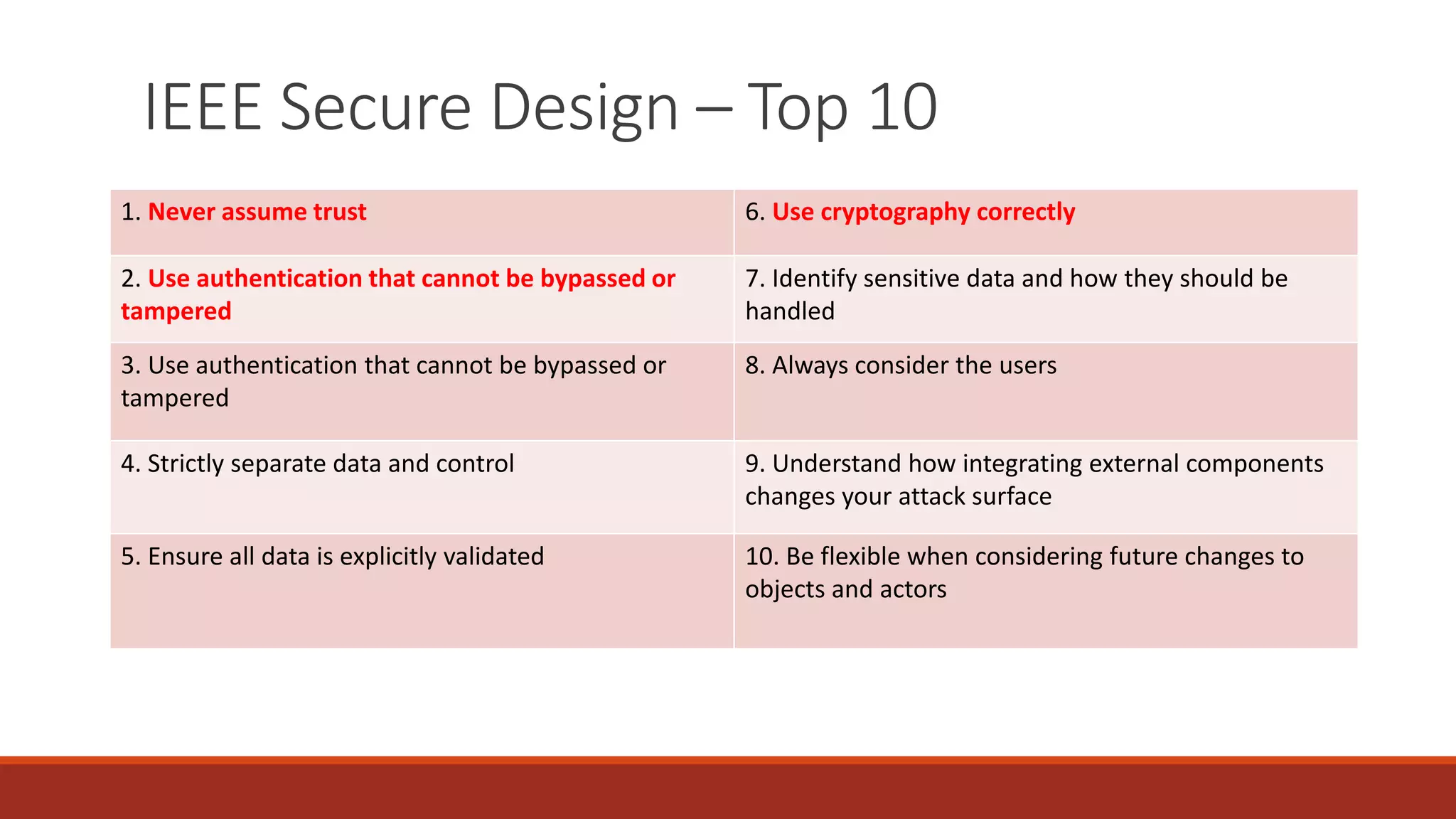
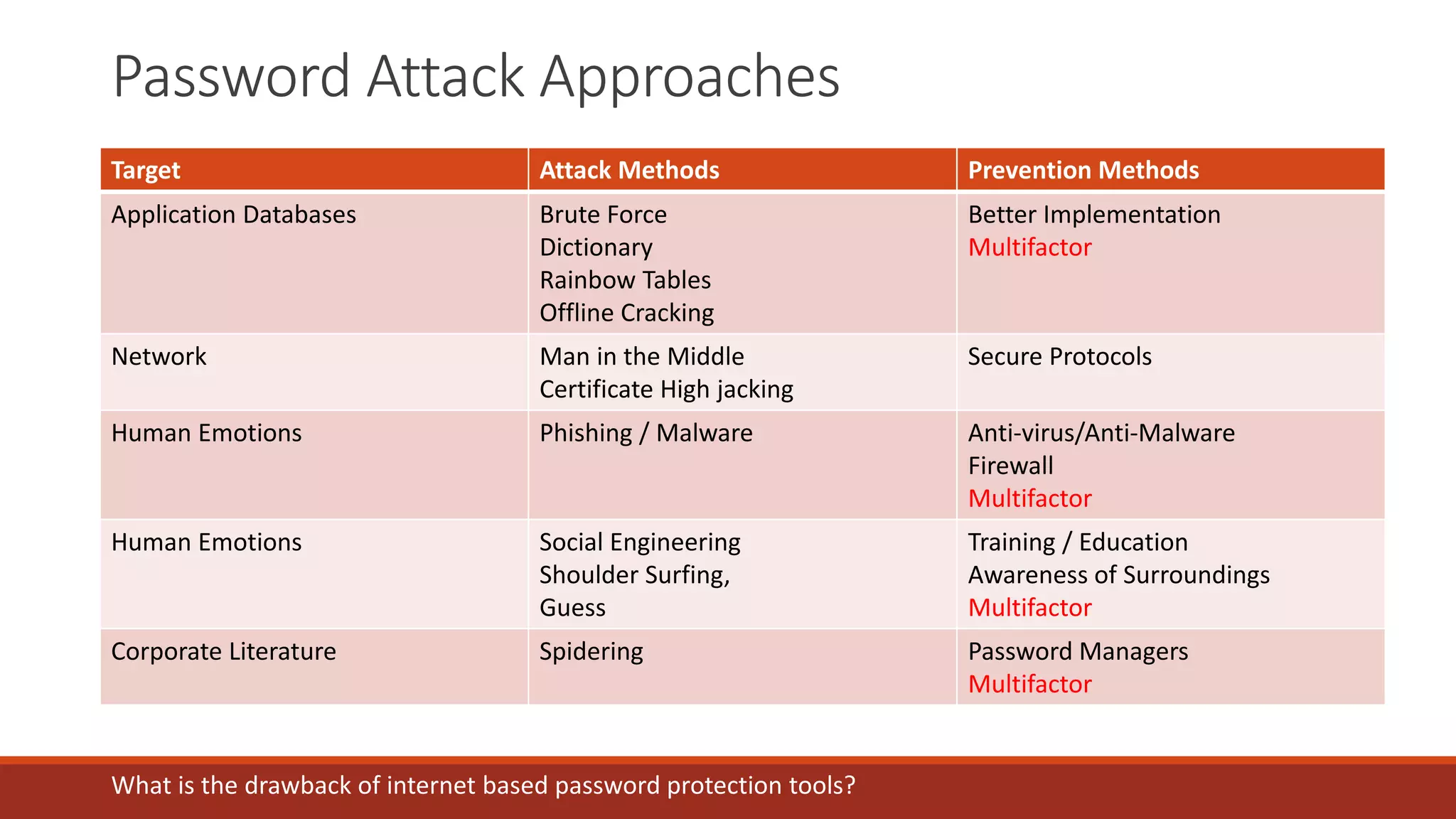
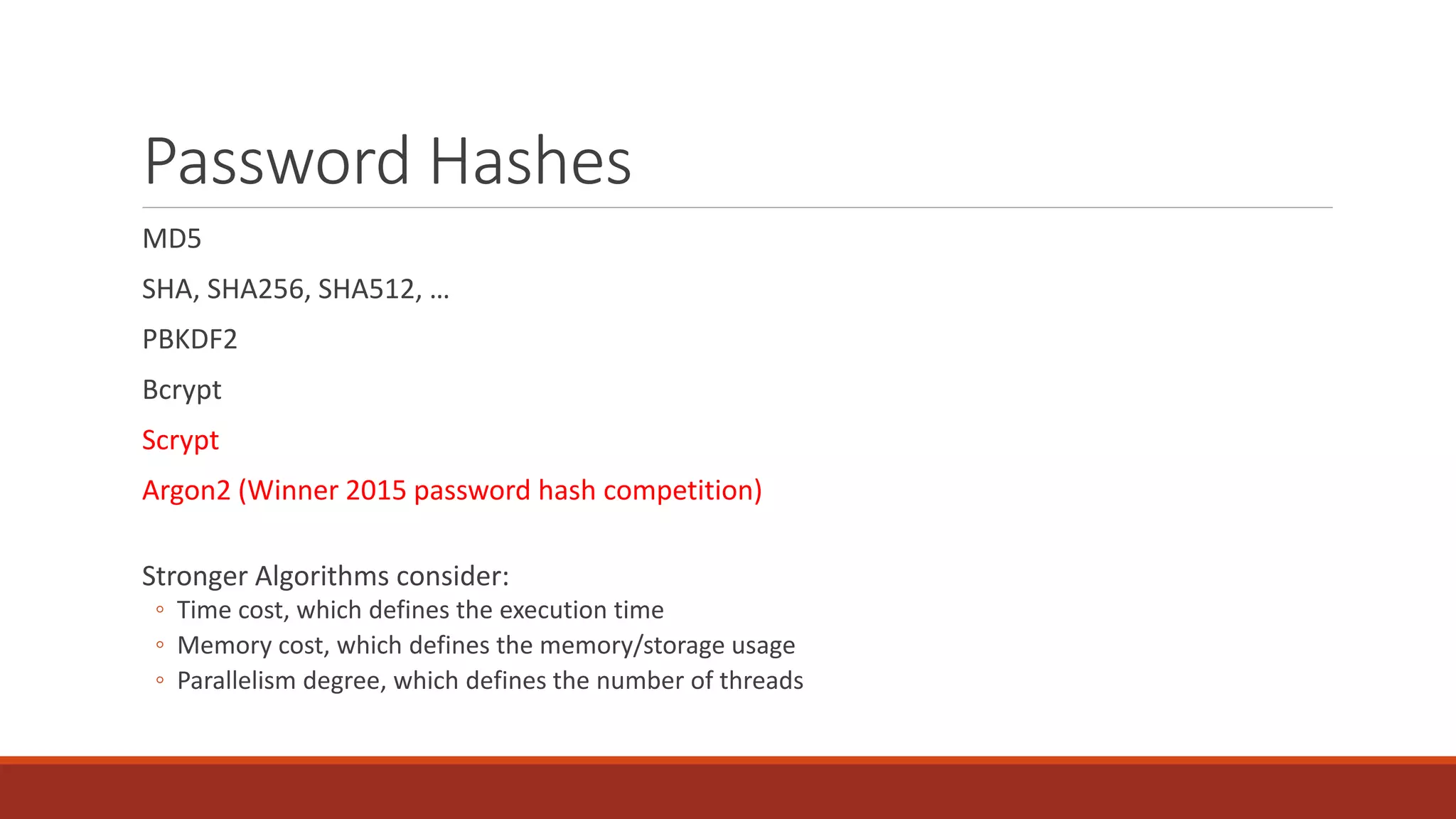
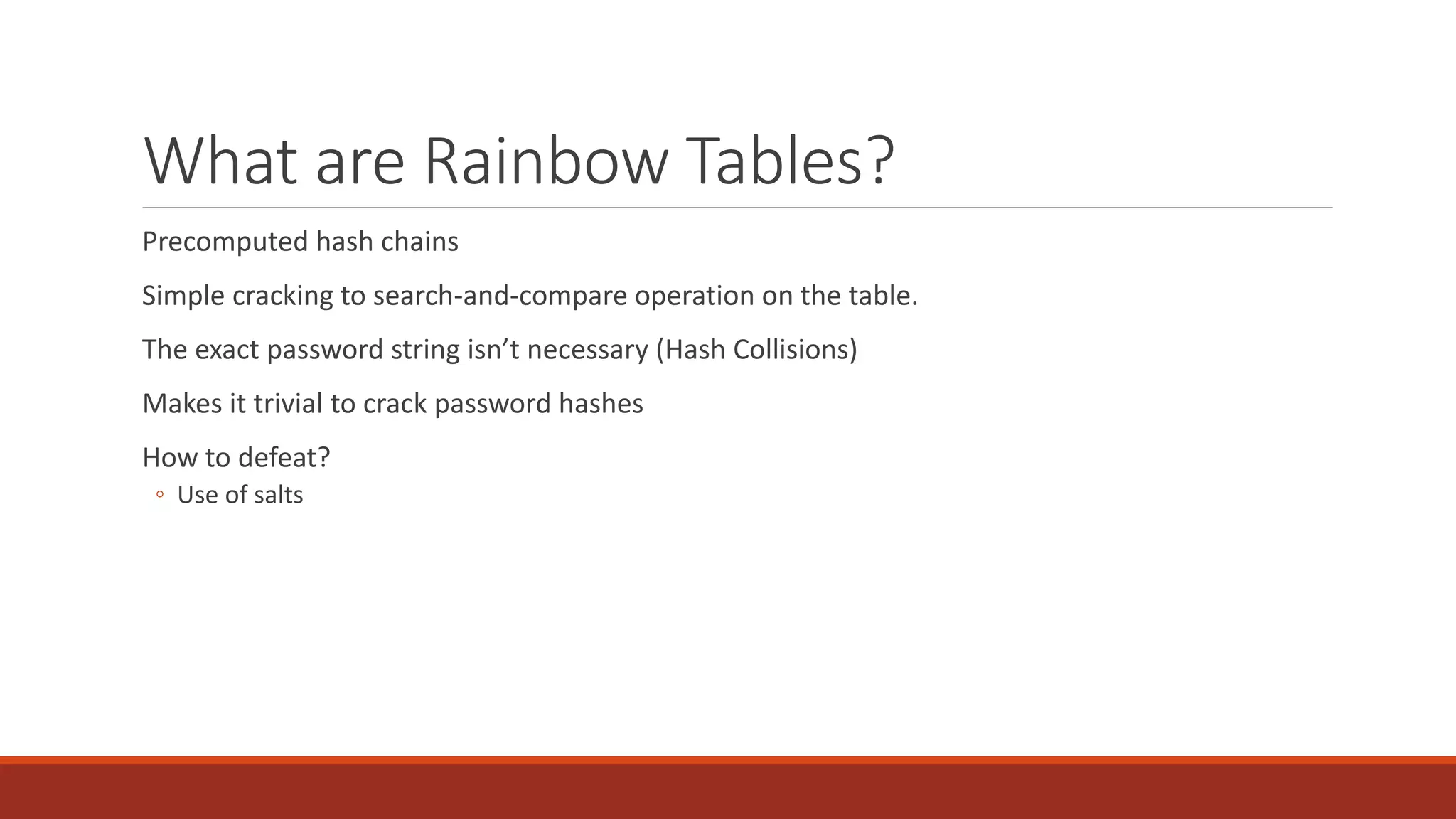
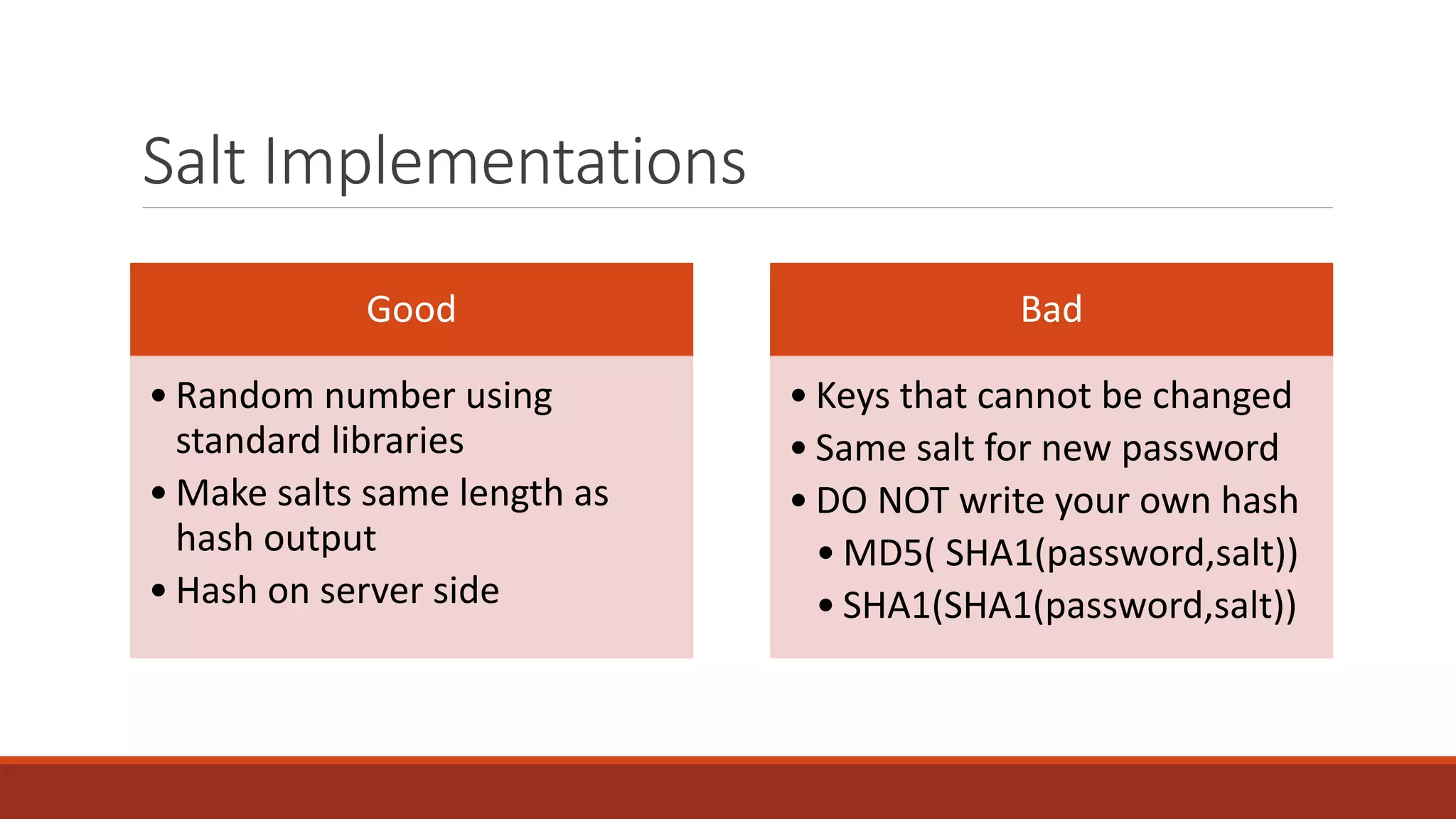
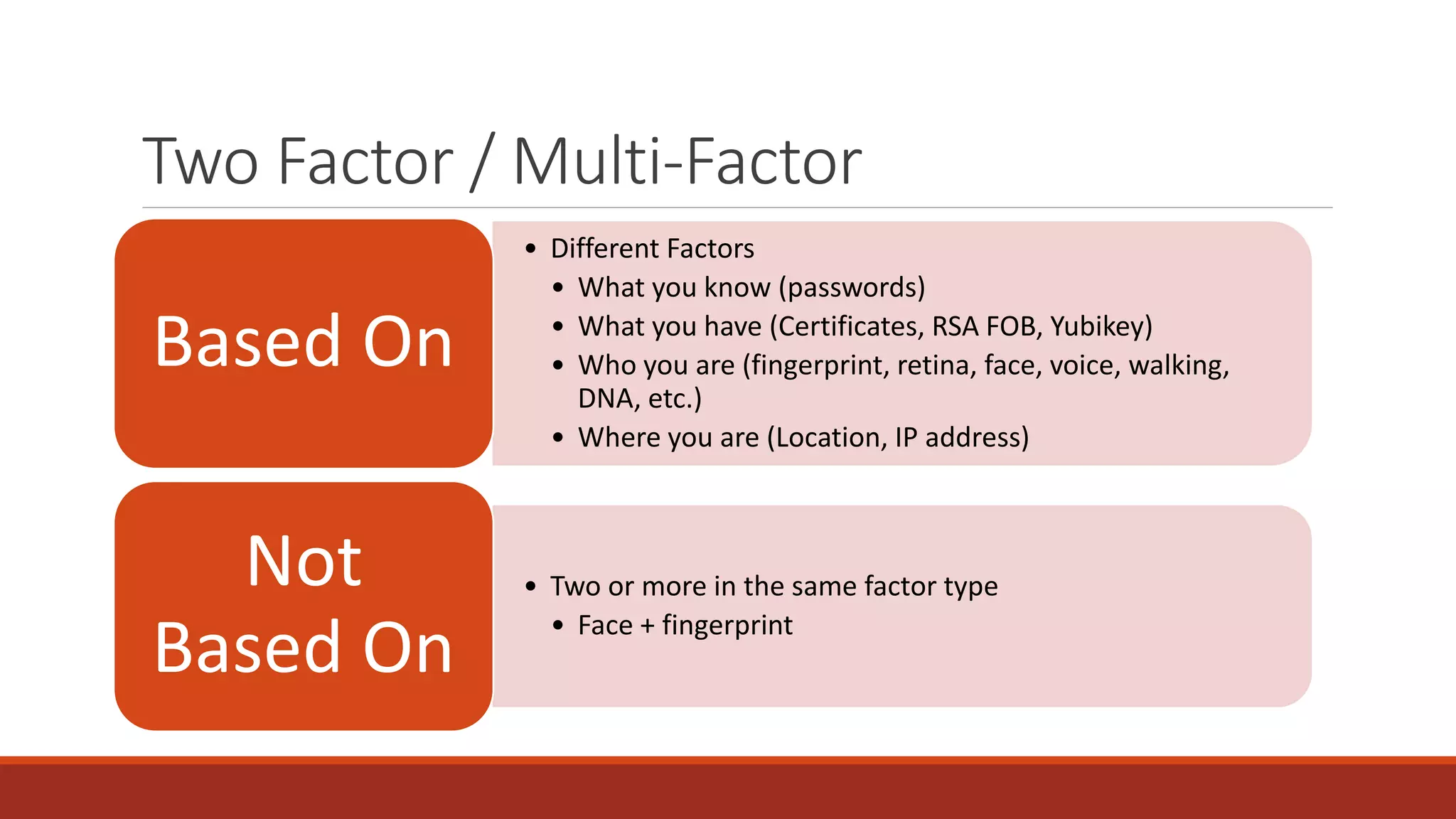
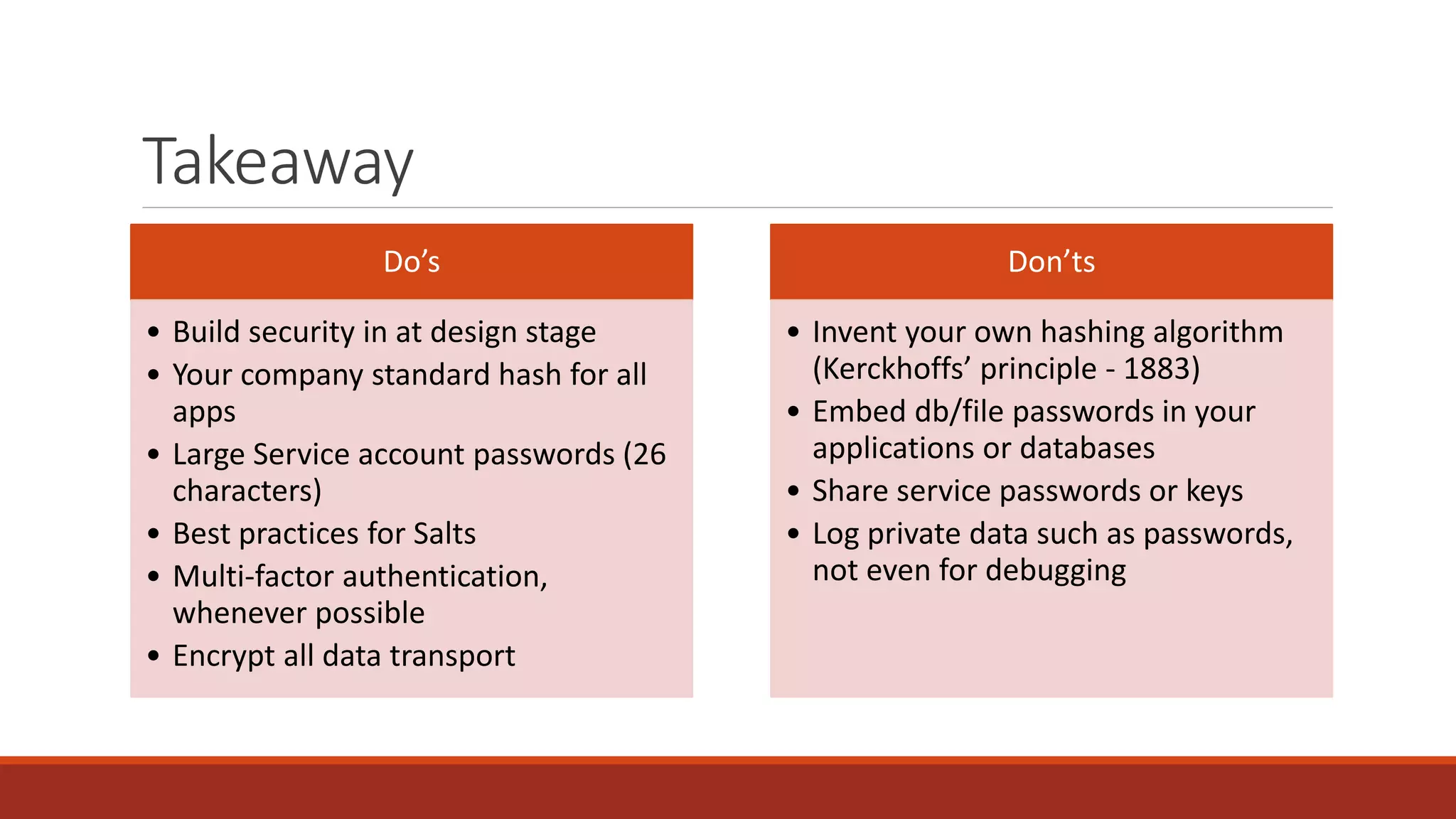
The document discusses best practices for password security and the importance of implementing robust authentication methods to prevent breaches, citing various high-profile password leaks. It emphasizes the need for strong hashing algorithms, the correct use of salts, and multi-factor authentication to enhance security. The document also outlines common password attack methods and the corresponding prevention techniques to safeguard sensitive information.