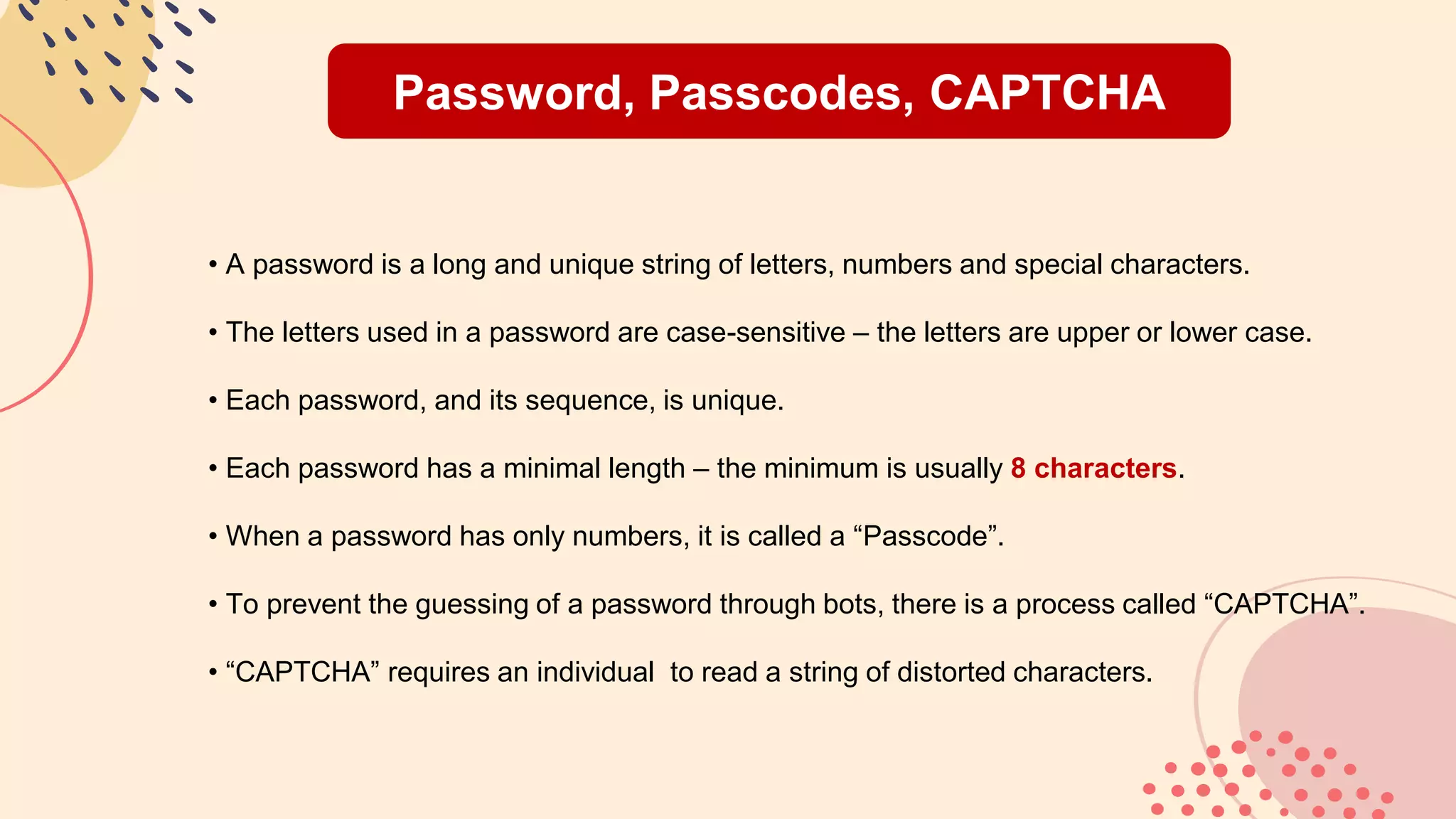
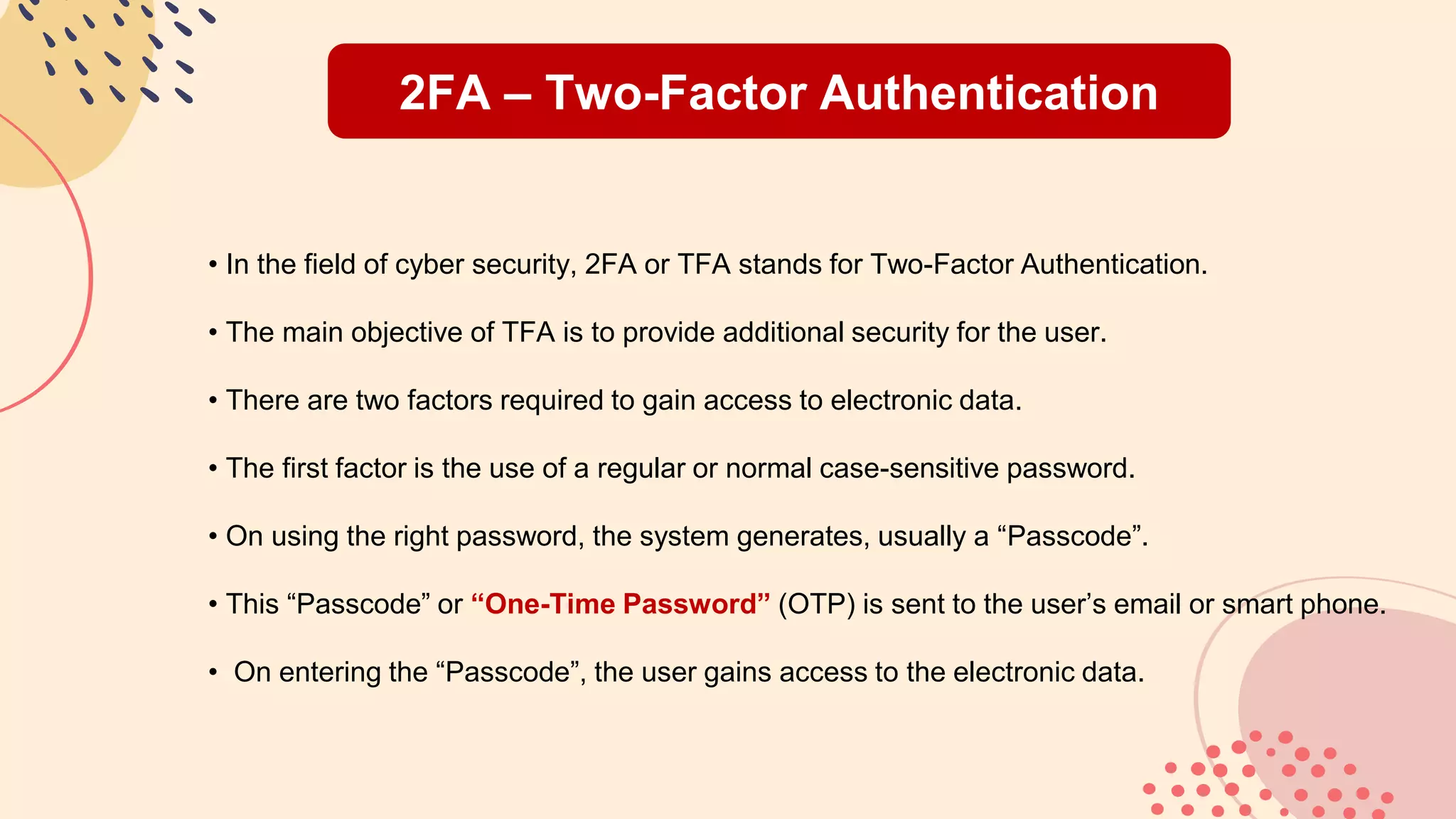
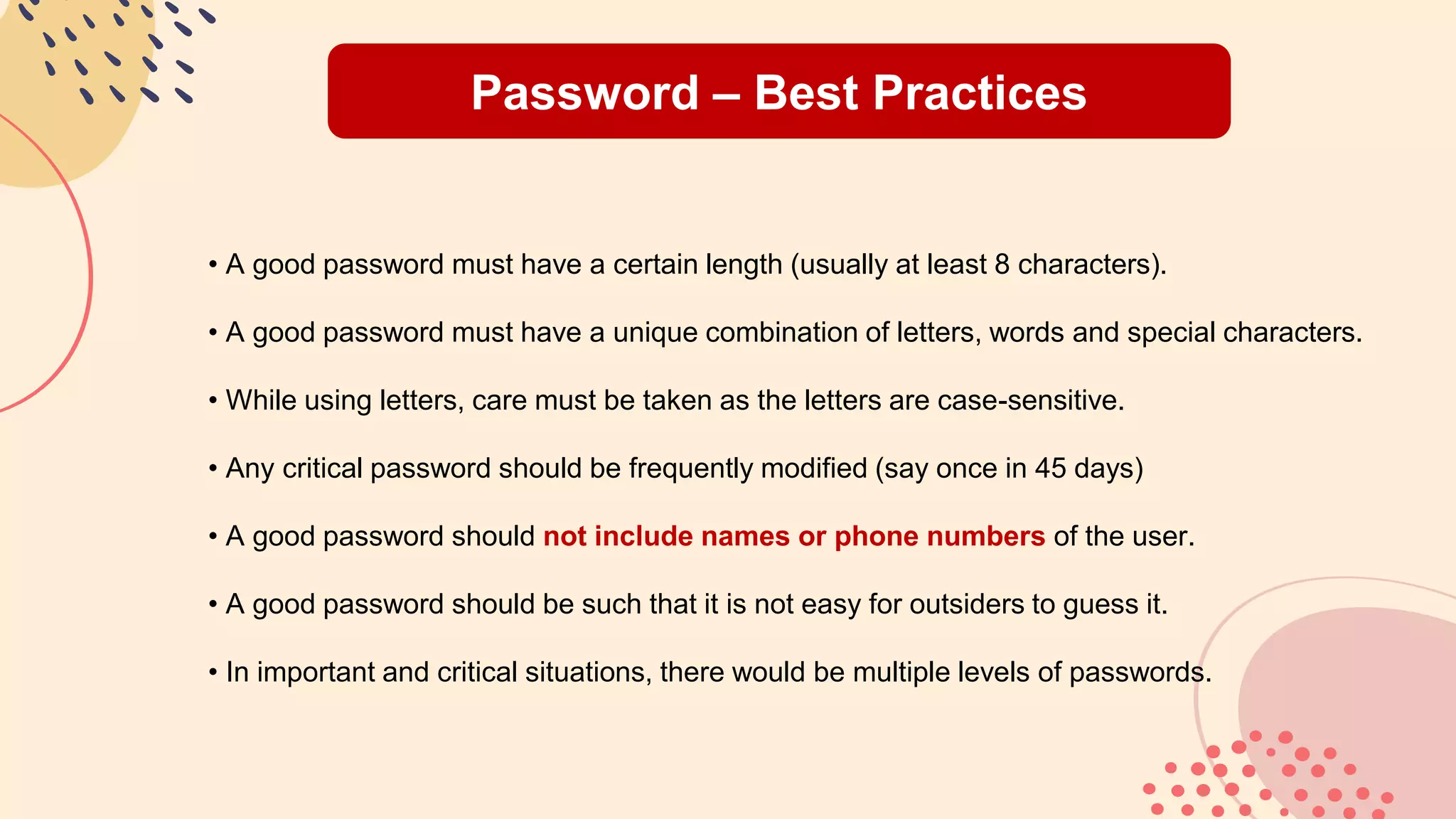
This document provides an overview of password best practices and security. It discusses the history of passwords, definitions of key terms like passwords and passcodes, techniques like two-factor authentication, best practices for password creation and management, common mistakes, what to do if a password is compromised, alternatives to passwords for authentication, and tips for proper password usage in different contexts. The document emphasizes using long, unique passwords that are changed periodically and avoiding weak passwords that are easy for hackers to guess.