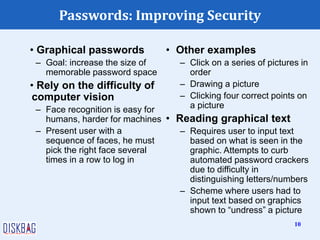
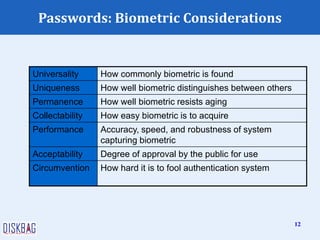
The document provides an overview of password authentication and security, emphasizing the importance and vulnerabilities of passwords as a primary defense mechanism. It discusses different authentication methods, types of password cracking, and strategies for improving password security, such as using biometric authentication and implementing strong password policies. Additionally, it lists common mistakes users make regarding password management and offers recommendations to enhance overall security.