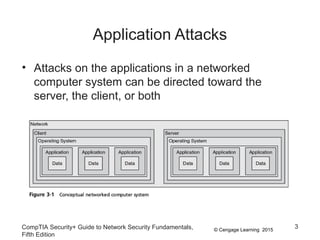
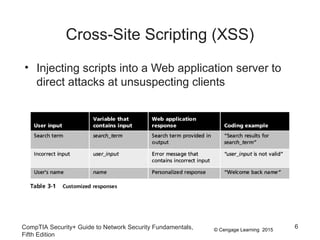
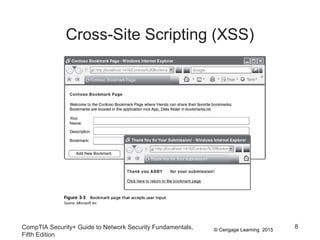
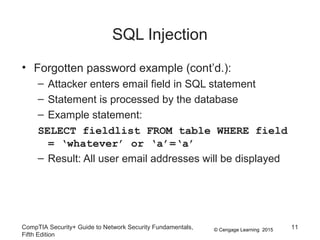
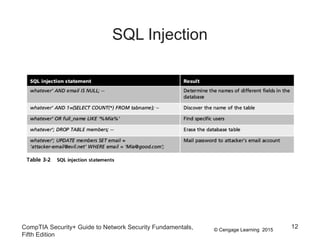
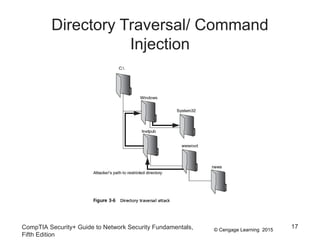
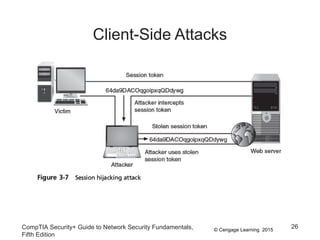
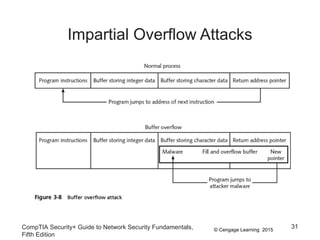
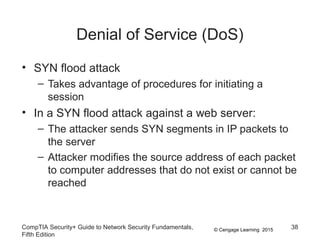
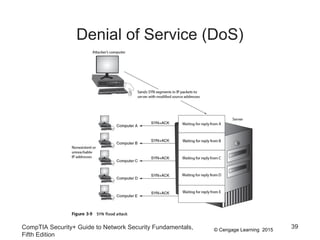
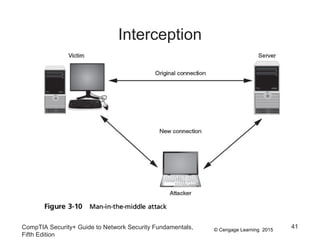
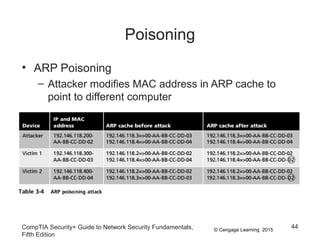
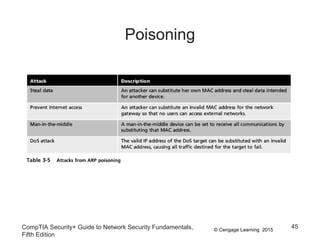
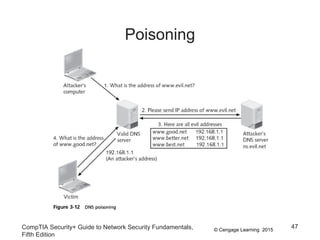
This document discusses different types of application and networking attacks. It covers server-side web application attacks like cross-site scripting, SQL injection, and command injection that target vulnerabilities in web applications. It also covers client-side attacks like drive-by downloads, cookie manipulation, session hijacking, and malicious browser add-ons that compromise client computers. The document provides details on how each type of attack works and potential vulnerabilities they exploit.