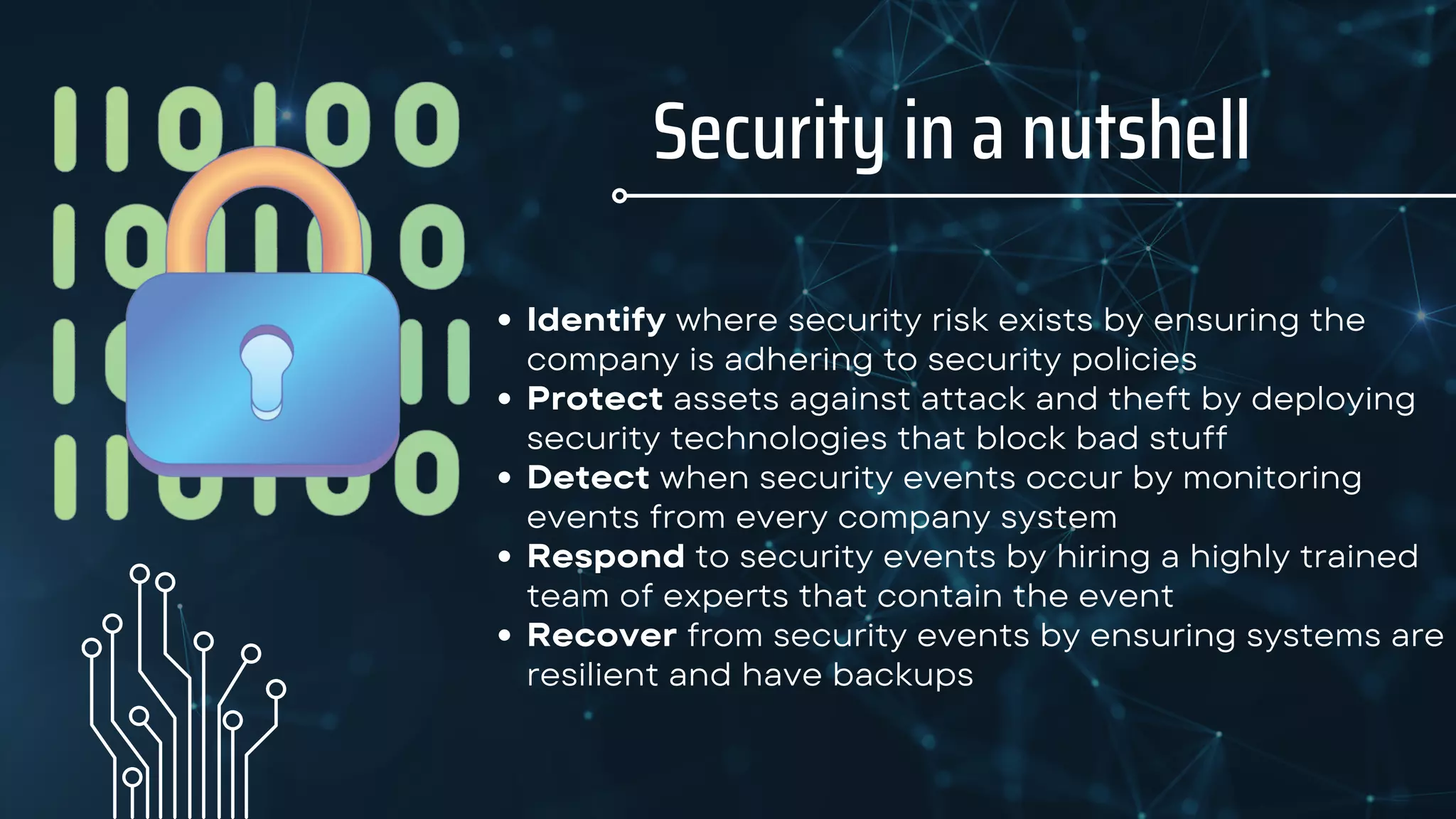
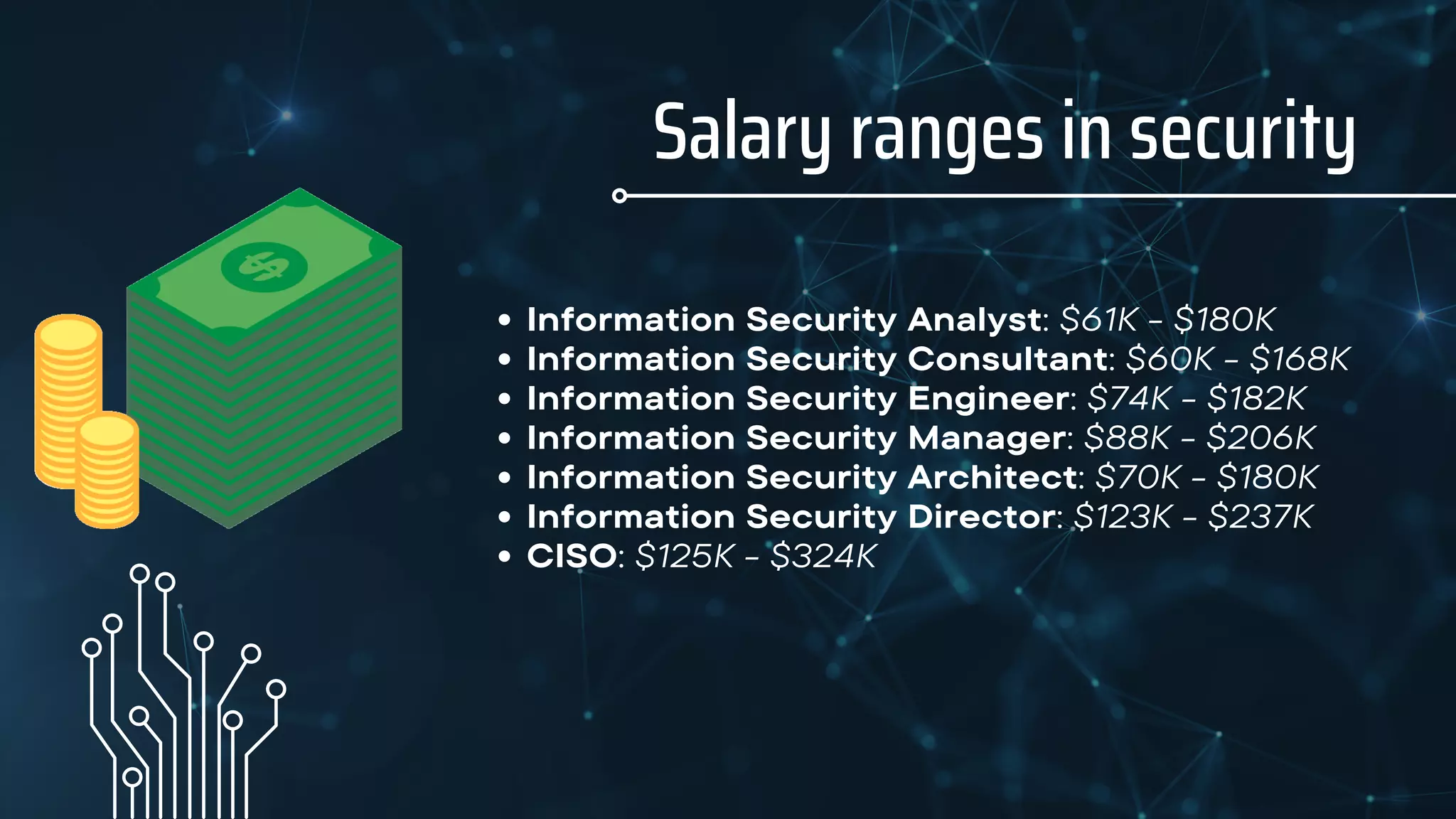
Dan Glass is a cybersecurity expert with over 25 years of professional experience, including roles as a CISO at American Airlines and advisor to various organizations. The document outlines the responsibilities and qualifications of a CISO, emphasizing the importance of security in organizations and the increasing demand for skilled professionals in this field. It also highlights job roles in security, salary ranges, and the educational pathways for entering the industry.