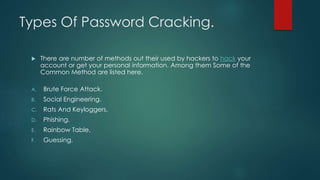
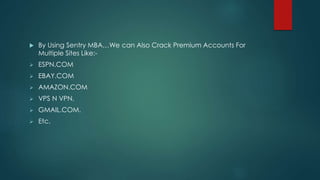
The document discusses password cracking and brute force tools, outlining various methods and tools used to gain unauthorized access to systems or recover forgotten passwords. It details common cracking techniques such as brute force attacks, social engineering, and phishing, along with specific tools like Brutus, RainbowCrack, and Cain & Abel. Emphasis is placed on the importance of complex passwords to counteract these attacks and the various methods employed by hackers to acquire sensitive information.