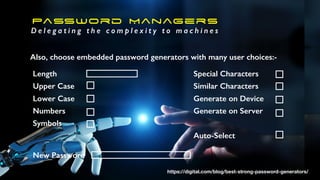
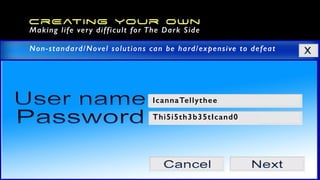
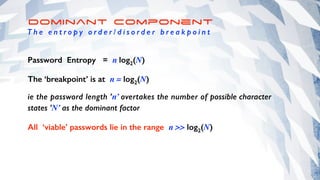
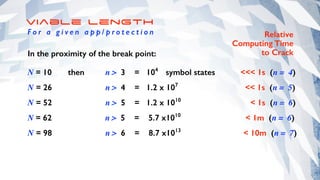
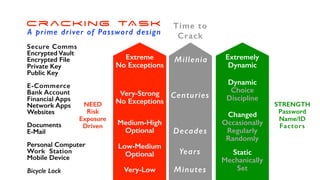
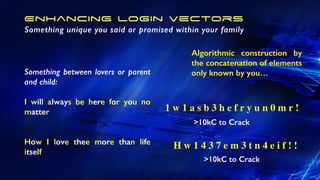
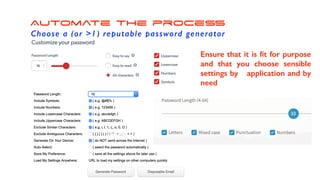
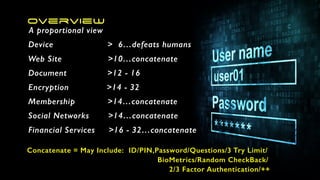
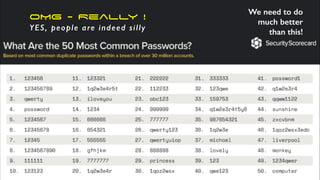
The document offers extensive advice on password security, emphasizing the need for strong passwords of at least 12 characters that include a mix of letters, numbers, and symbols, while avoiding common pitfalls such as using obvious substitutions or shared passwords. It critiques the current security practices and emphasizes the importance of diverse methods, including using password managers to manage complexity and enhance security defenses against various threats like social engineering. Additionally, it discusses password entropy and cracking vulnerabilities, illustrating the necessity for heightened protection measures in our increasingly digital landscape.




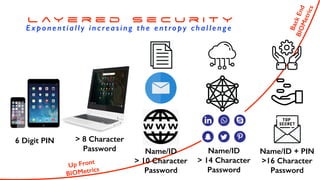
![12 Characters, Minimum: There’s no minimum or standardised password
length; but in general go for >12 to 14 characters
Mix Numbers: Letters, Symbols, Upper & Lower-Case: Many different types
makes passwords harder to crack
Dictionary Words/Combination: To be avoided as much as possible - any
isolated word is bad, and word combinations are also high risk
Avoid Obvious Substitutions: Eg, replacing an ‘o’ with ‘0’ is obvious - a 3 for e
or E, 2 for z or Z only slightly better - and DO use “, ; -} ] ) et al
Number Strings: at the end, beginning or in the middle are also ‘obvious’
Industry Advice
For a strong password you ‘at least’ need..](https://image.slidesharecdn.com/howtodesignapassword-191228164025/85/How-to-Design-Passwords-8-320.jpg)
![12 Characters, Minimum: There’s no minimum or standardised password
length; but in general go for >12 to 14 characters
Mix Numbers: Letters, Symbols, Upper & Lower-Case: Many different types
makes passwords harder to crack
Dictionary Words/Combination: To be avoided as much as possible - any
isolated word is bad, and word combinations are also high risk
Avoid Obvious Substitutions: Eg, replacing an ‘o’ with ‘0’ is obvious - a 3 for e
or E, 2 for z or Z only slightly better - and DO use “, ; -} ] ) et al
Number Strings: at the end, beginning or in the middle are also ‘obvious’
Industry Advice
For a strong password you ‘at least’ need..
Machines are fast
intelligent exhaustive
with extensive libraries
One size does not fit all
people and machines
present different risks
people are slow and
get exhausted and
use different methods](https://image.slidesharecdn.com/howtodesignapassword-191228164025/85/How-to-Design-Passwords-9-320.jpg)