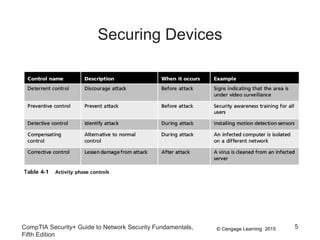
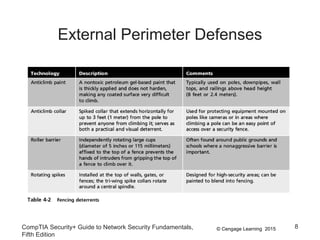
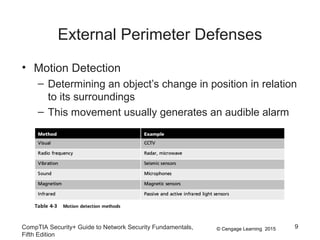
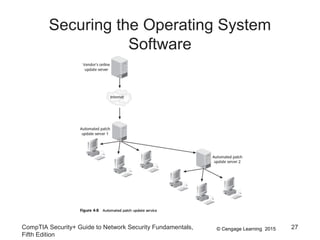
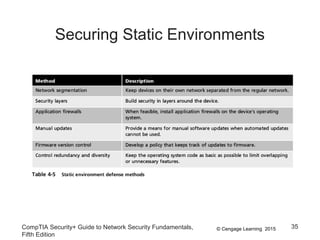
The document discusses securing hosts, applications, and data. It describes securing the host by protecting physical devices, securing the operating system software, and using antimalware software. Securing the operating system involves developing security policies, baselining the OS configuration, configuring security settings, deploying security settings using tools like group policy, and implementing patch management. Antimalware software like antivirus, antispam, and firewall programs provide additional security for the host.