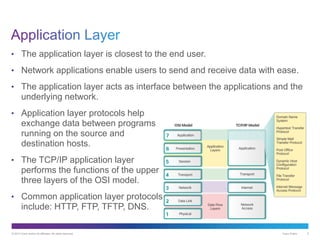
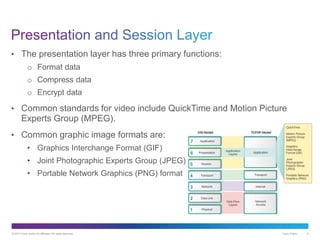
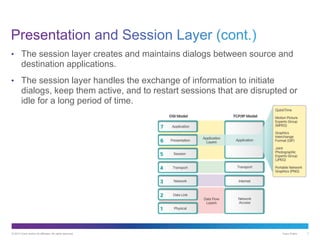
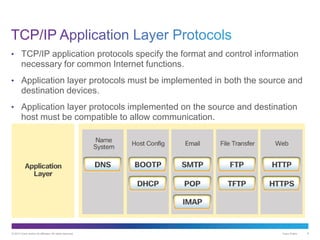
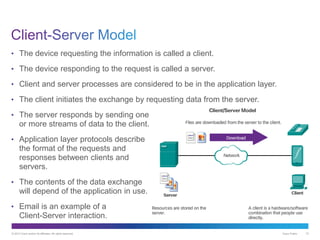
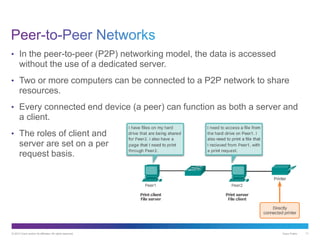
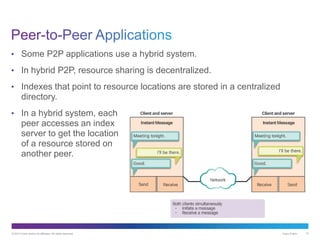
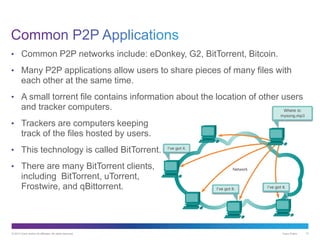
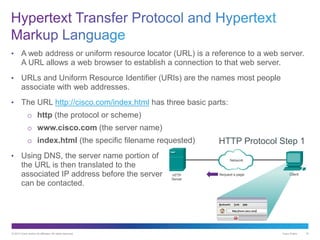
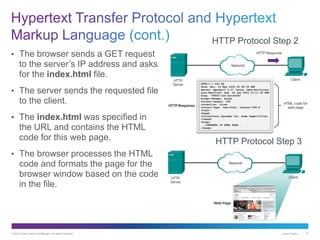
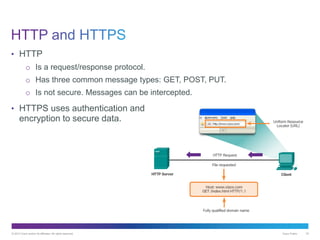
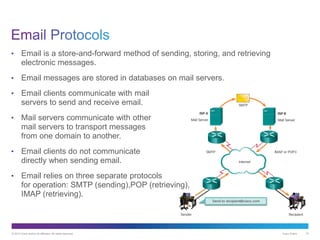
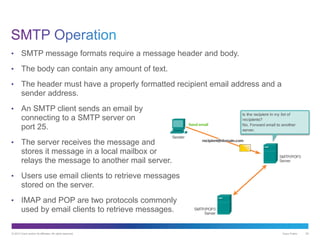
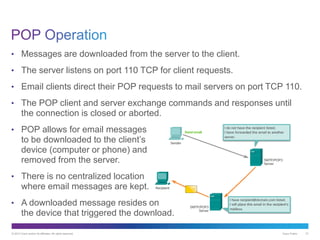
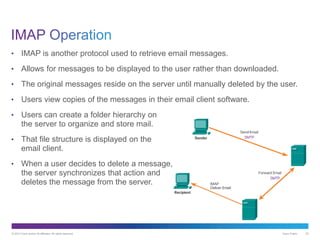
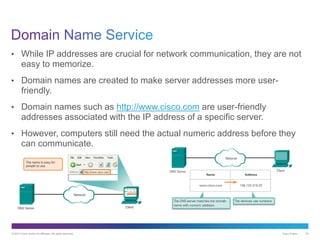
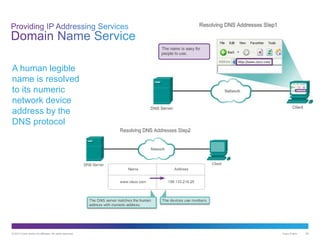
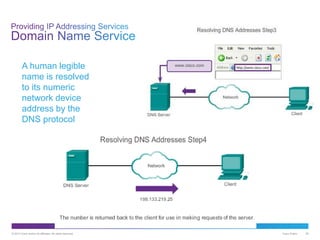
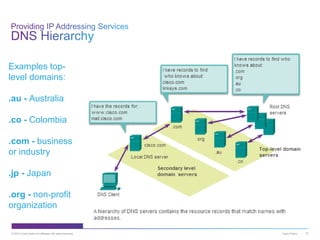
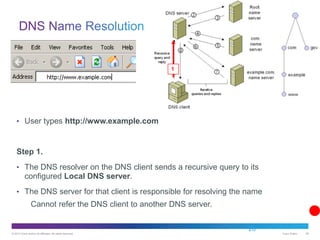
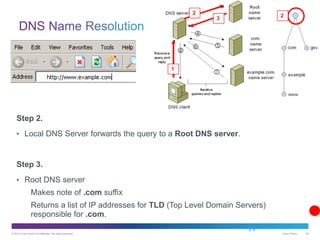
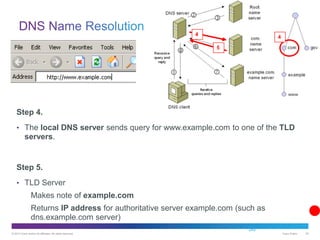
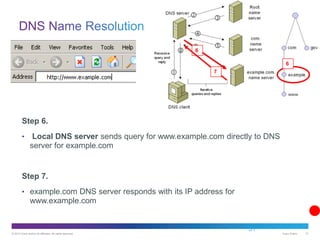
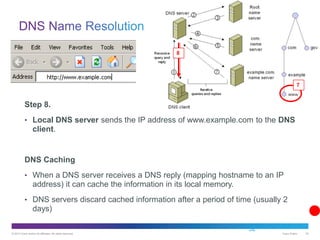
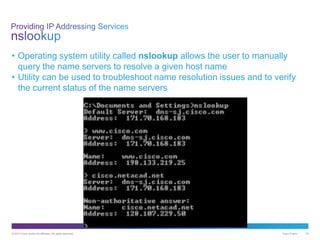
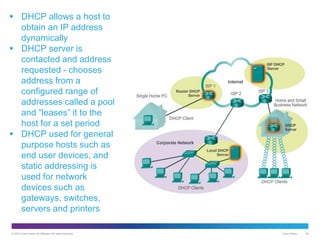
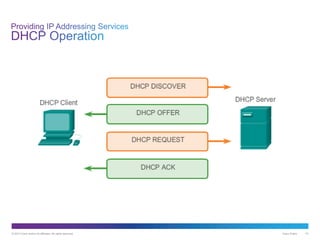
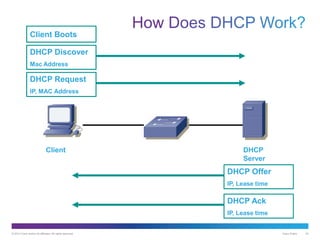
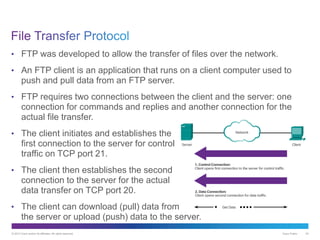
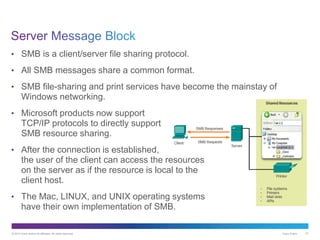
The document discusses application layer protocols and services. It explains that the application layer acts as an interface between network applications and the underlying network, and that common application layer protocols like HTTP, FTP, and DNS help exchange data between programs running on source and destination hosts. It also discusses client-server and peer-to-peer networking models and provides examples of protocols like HTTP, SMTP, POP, IMAP, and DNS.