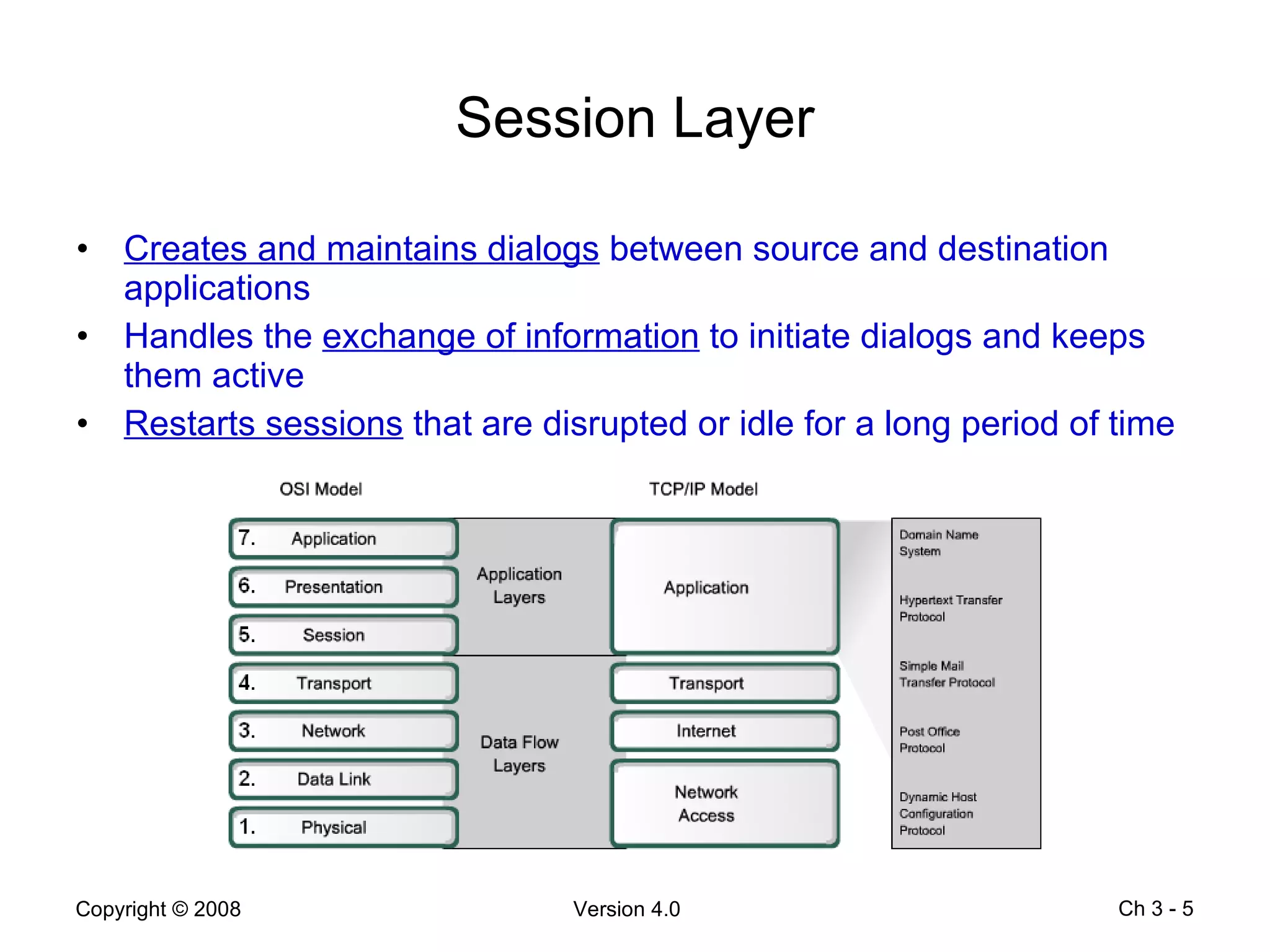
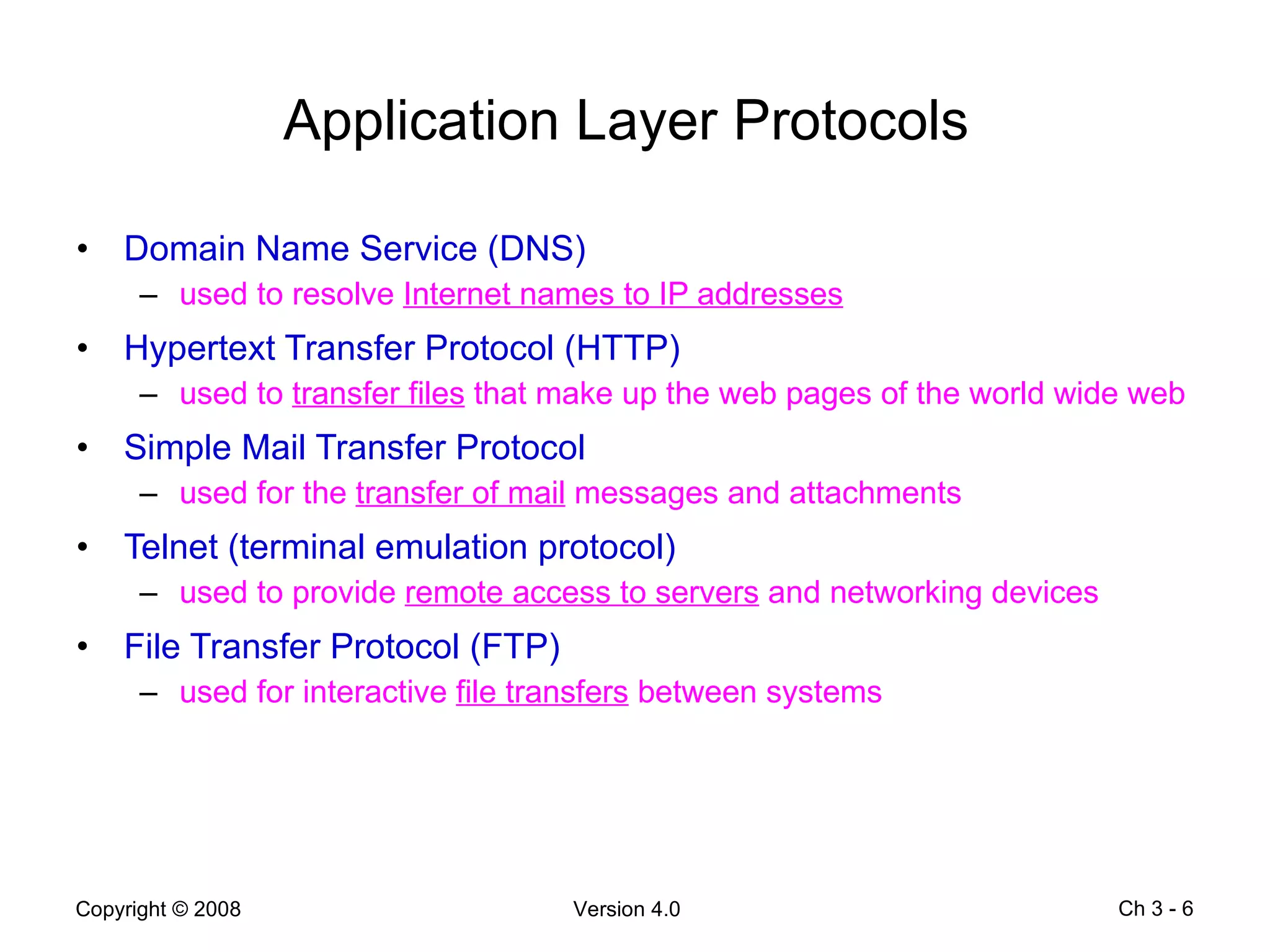
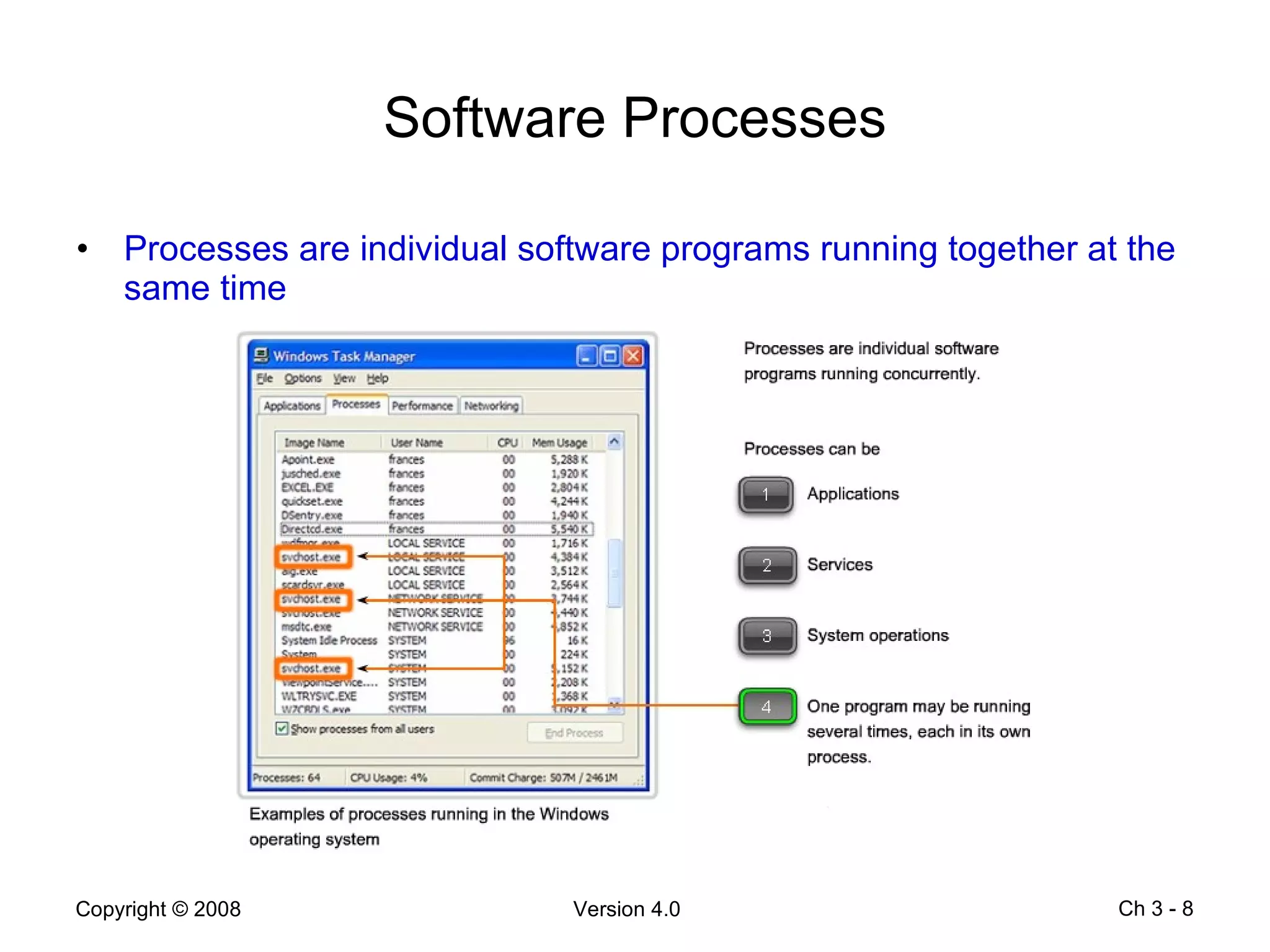
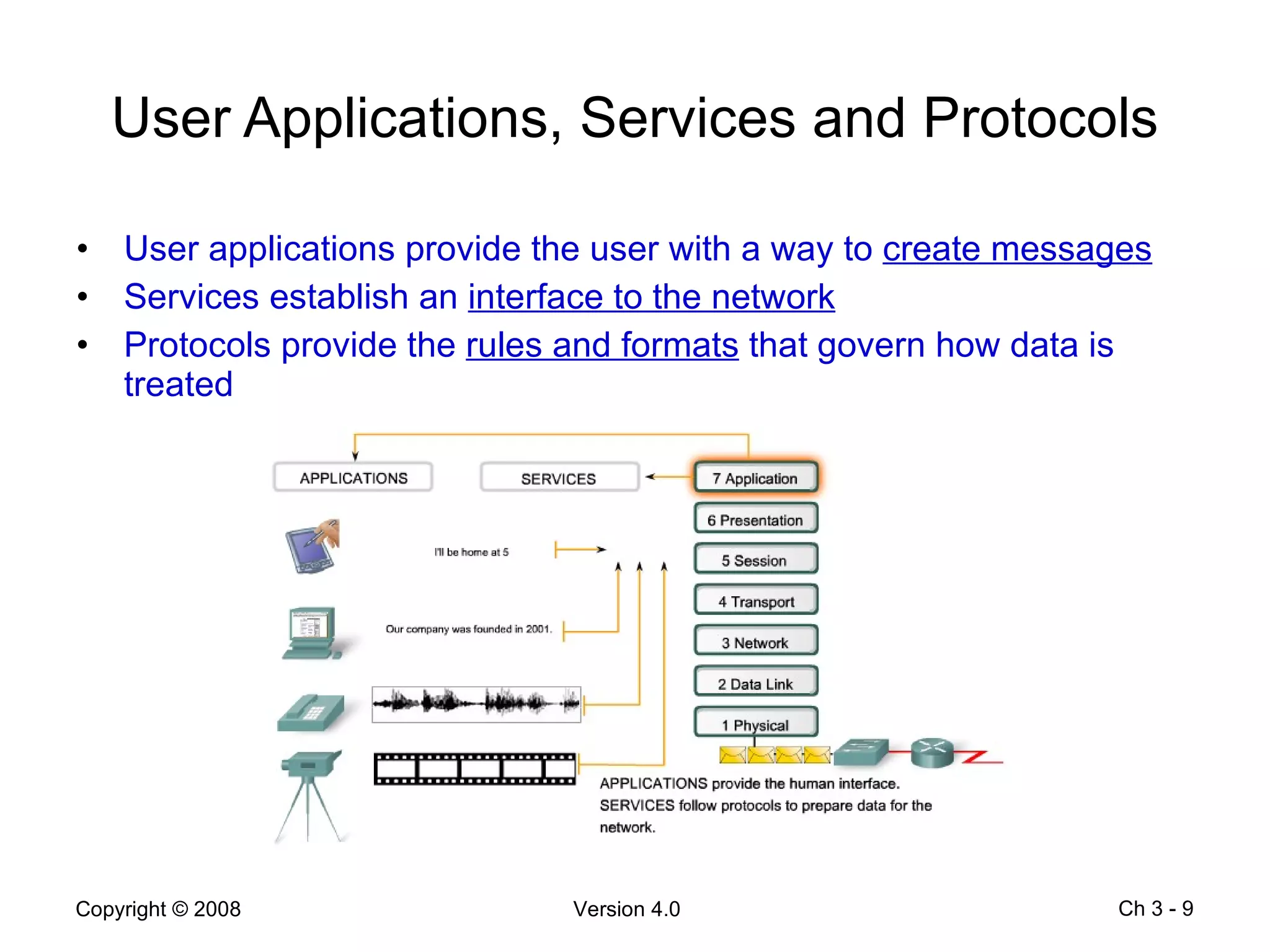
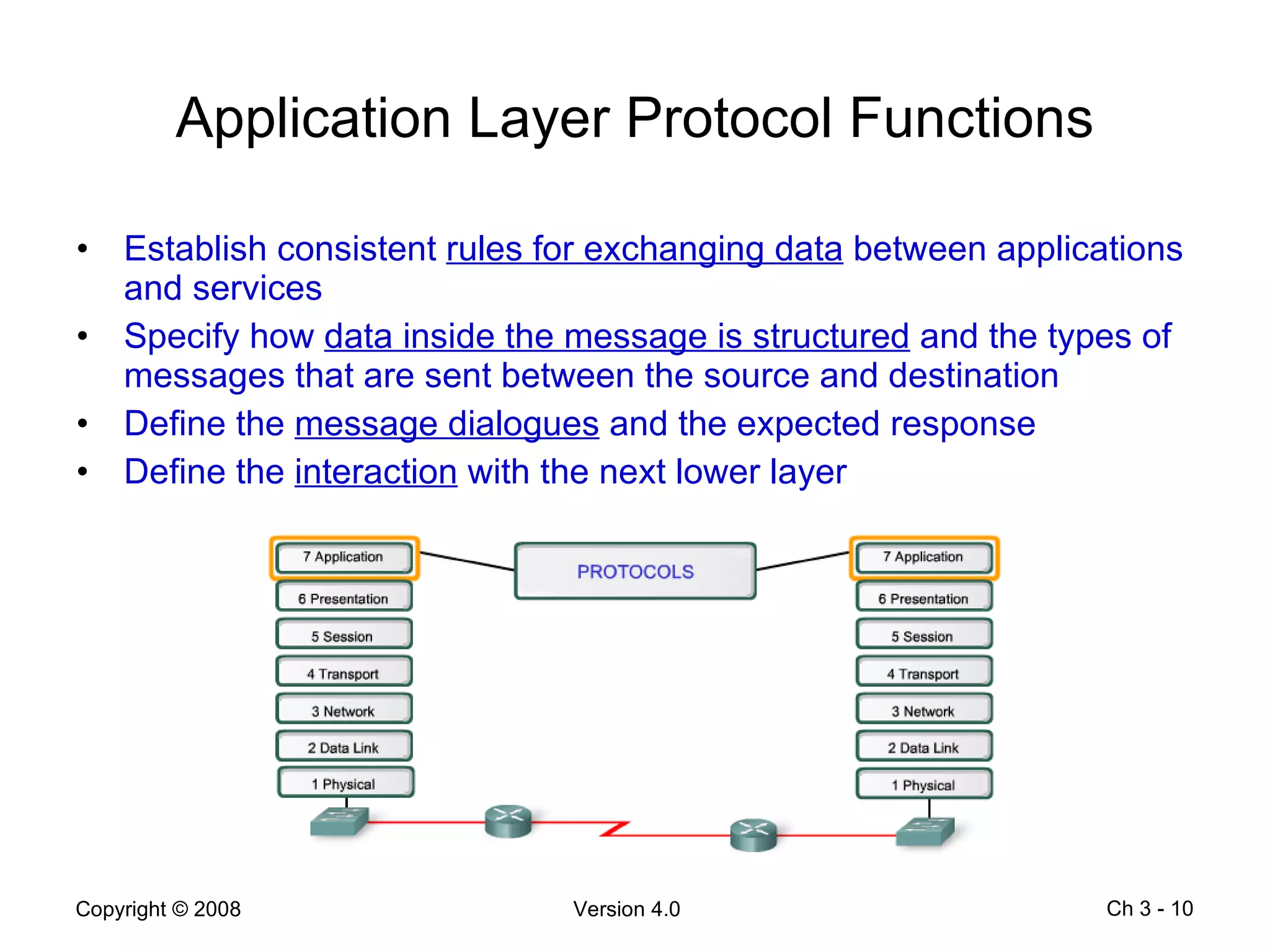
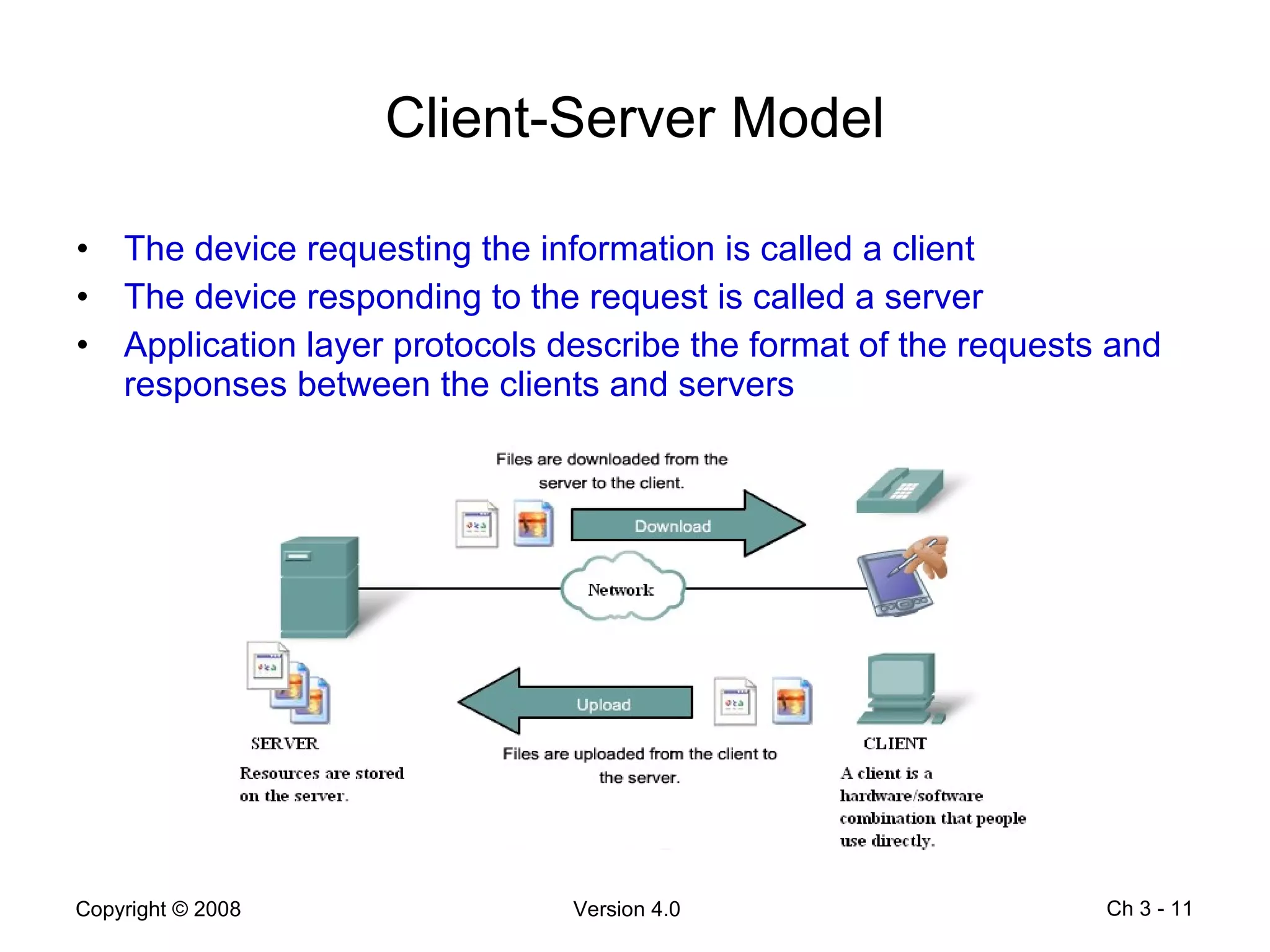
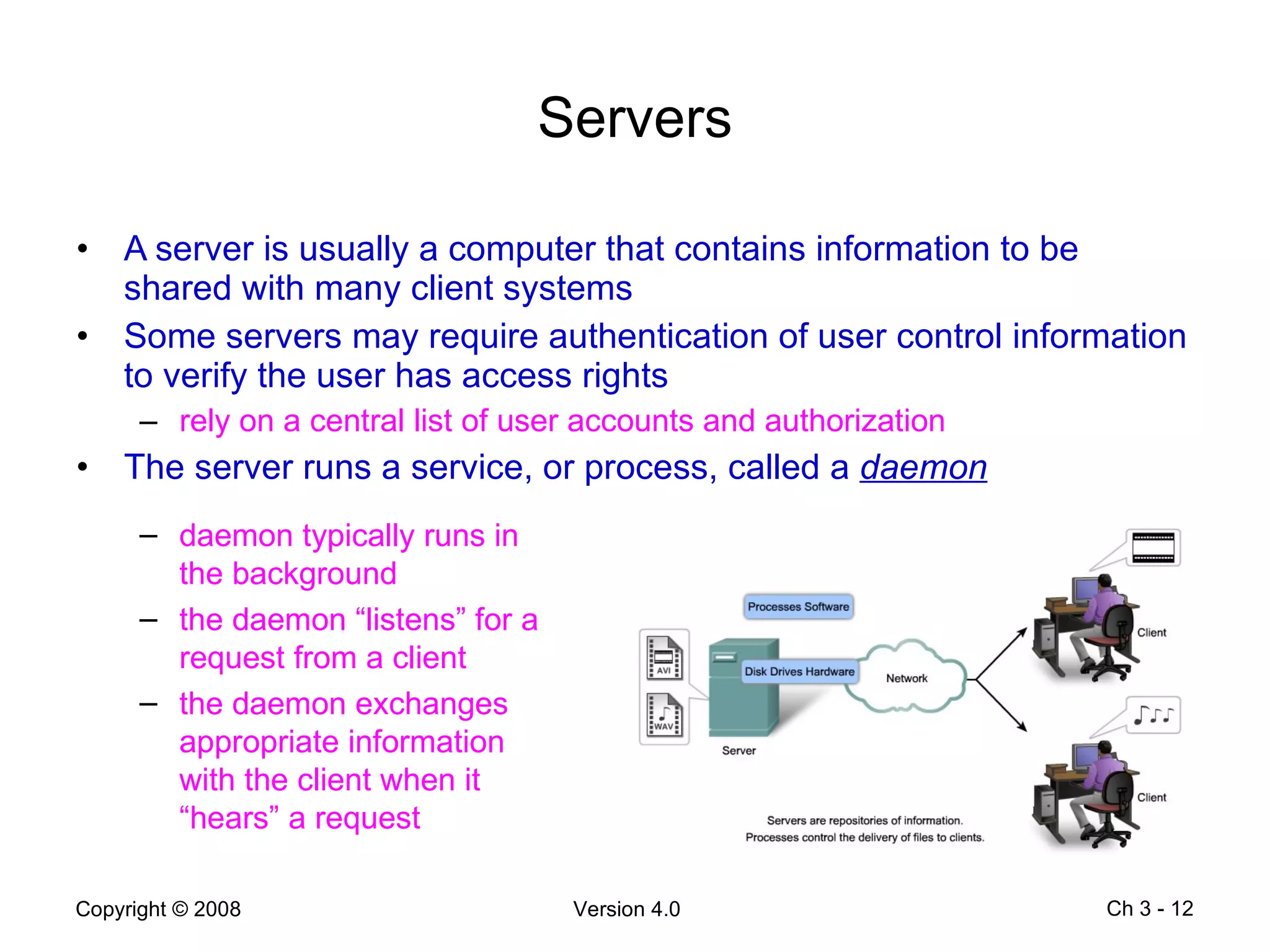
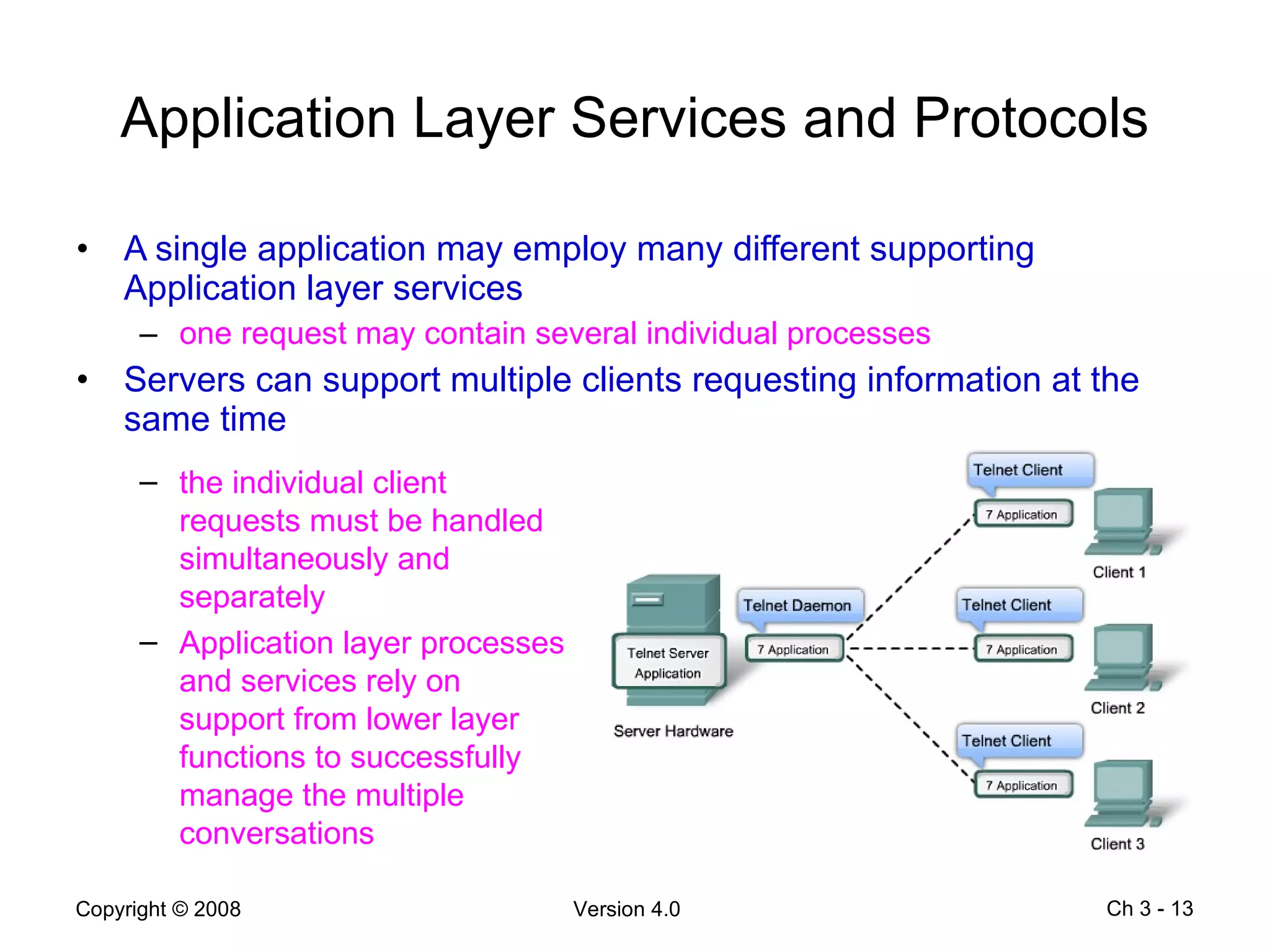
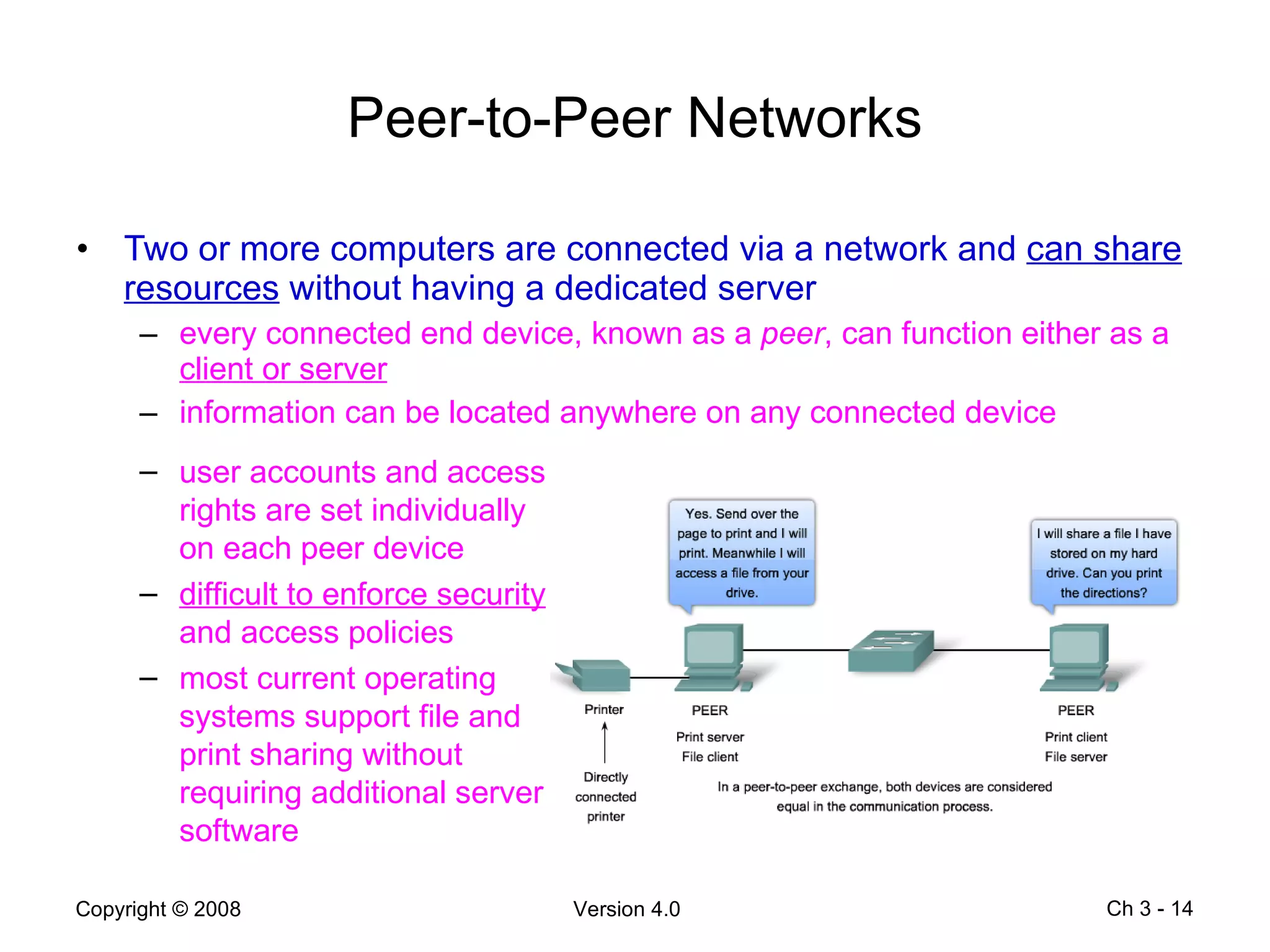
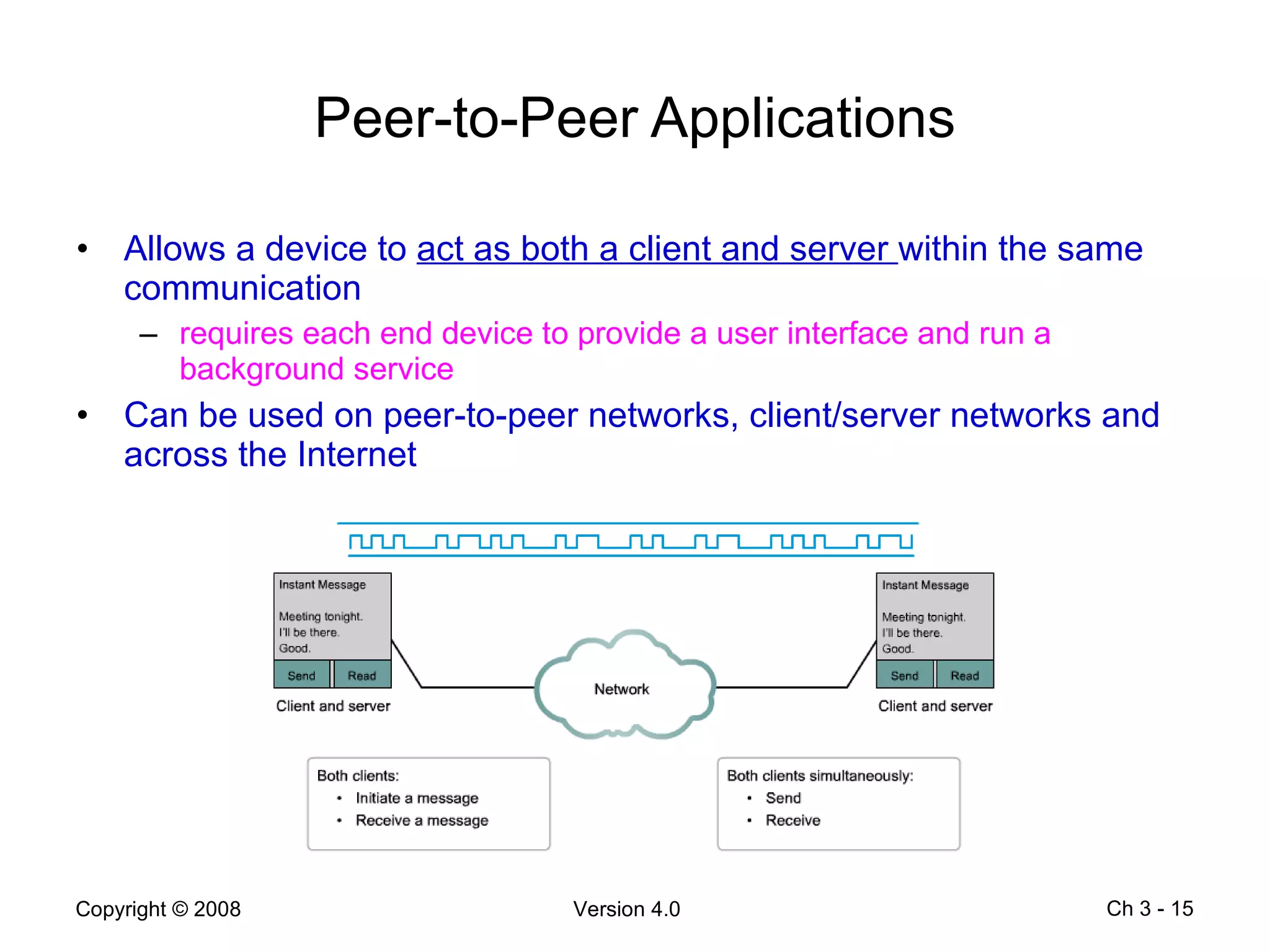
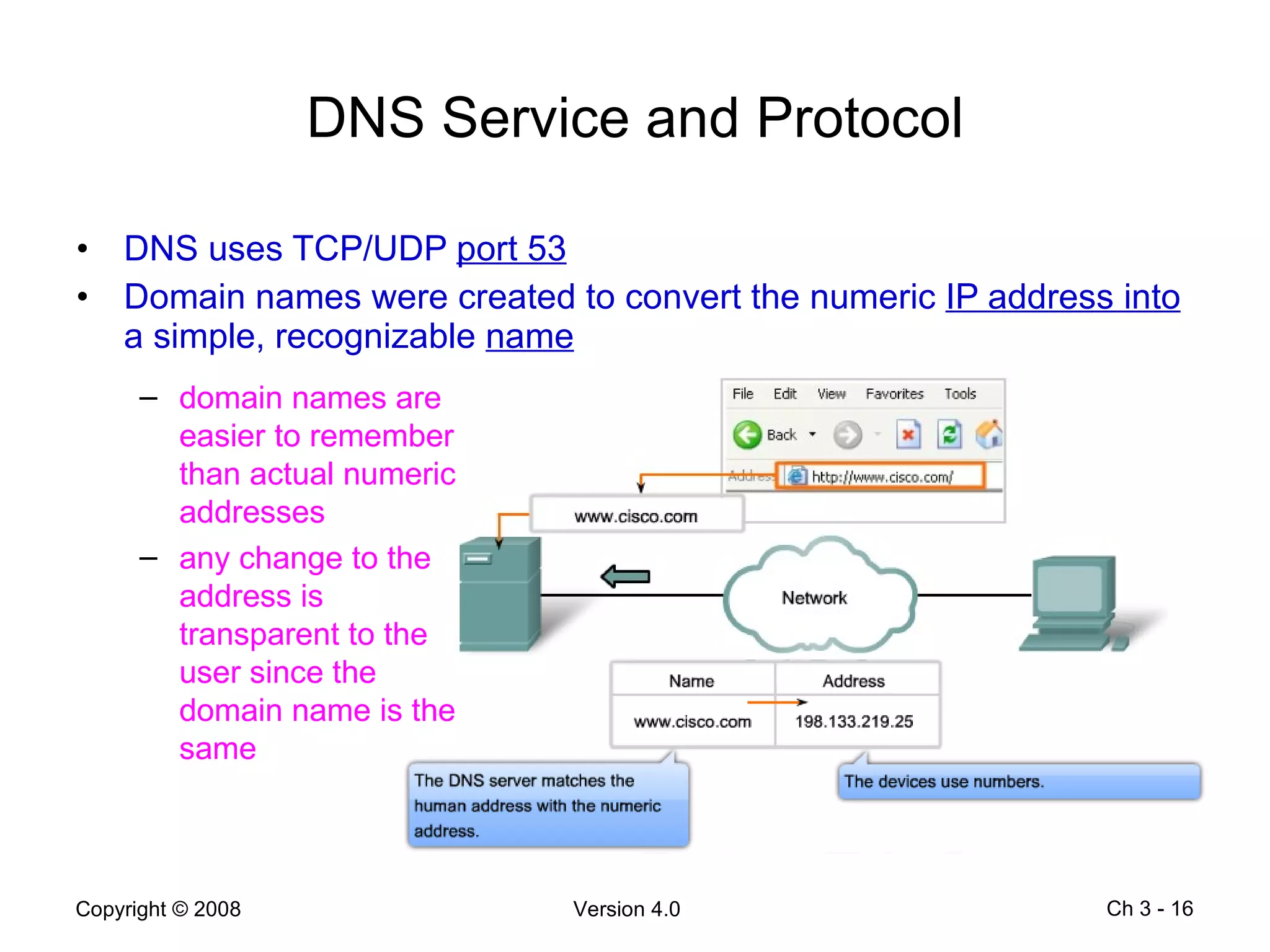
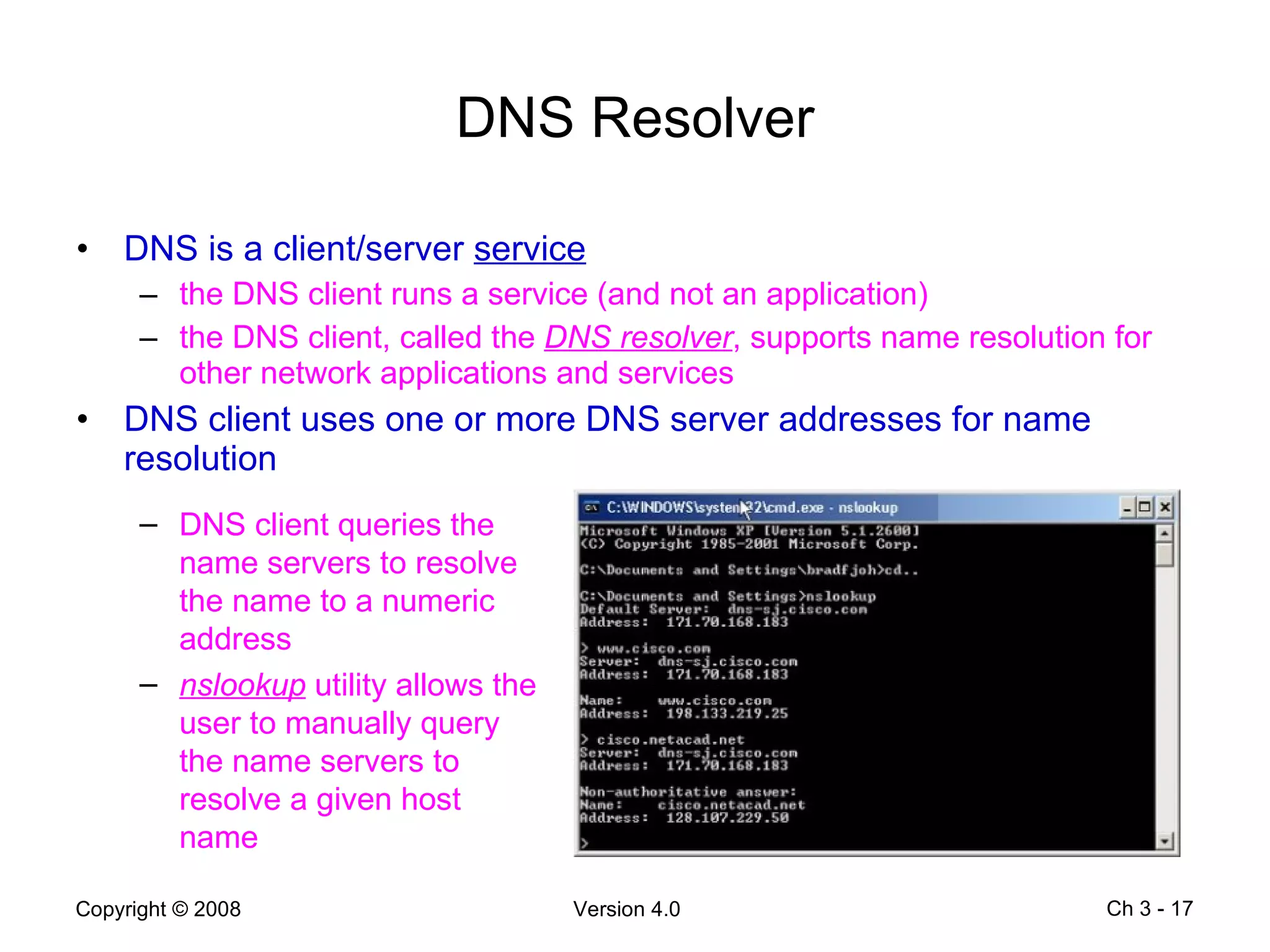
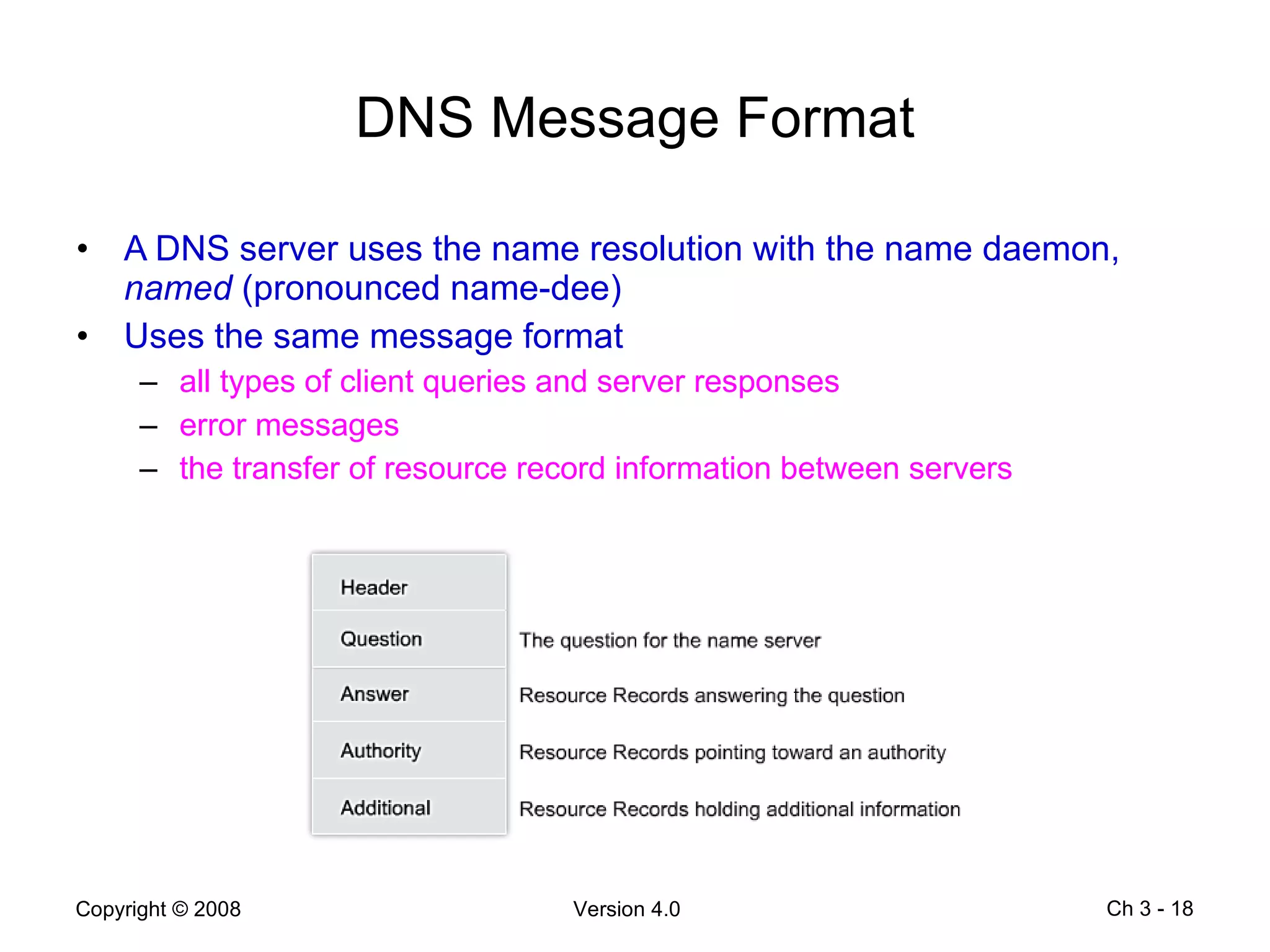
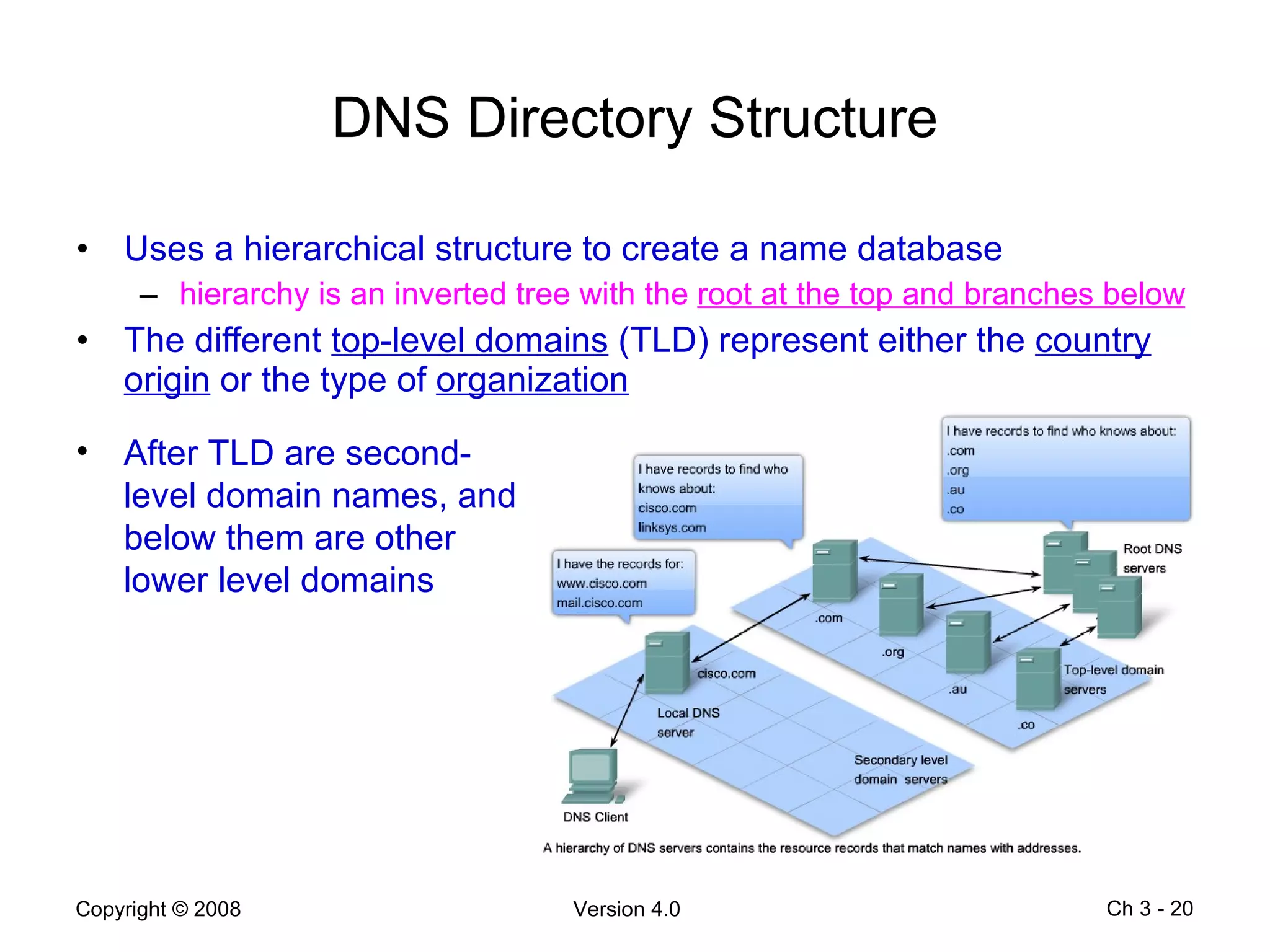
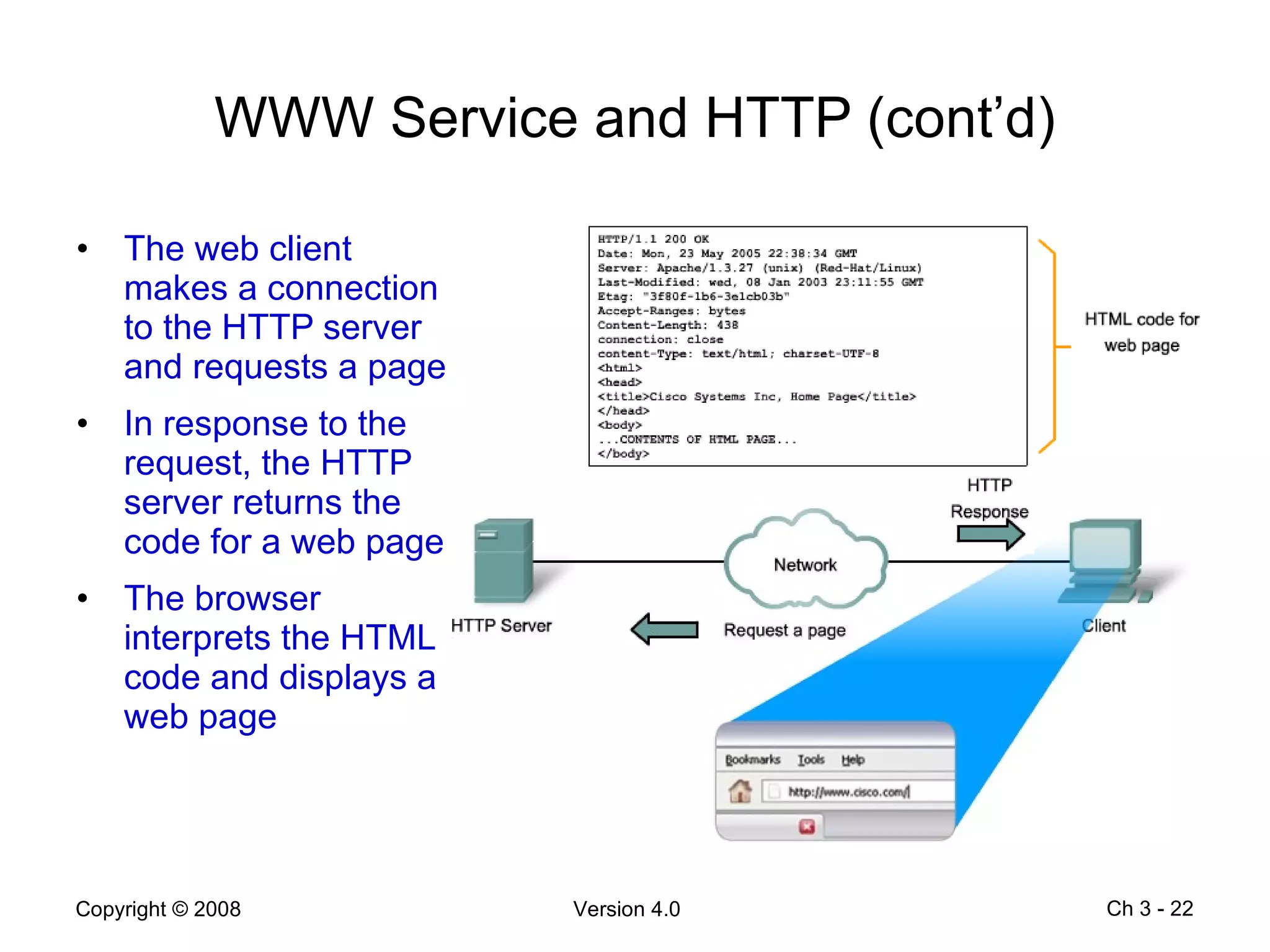
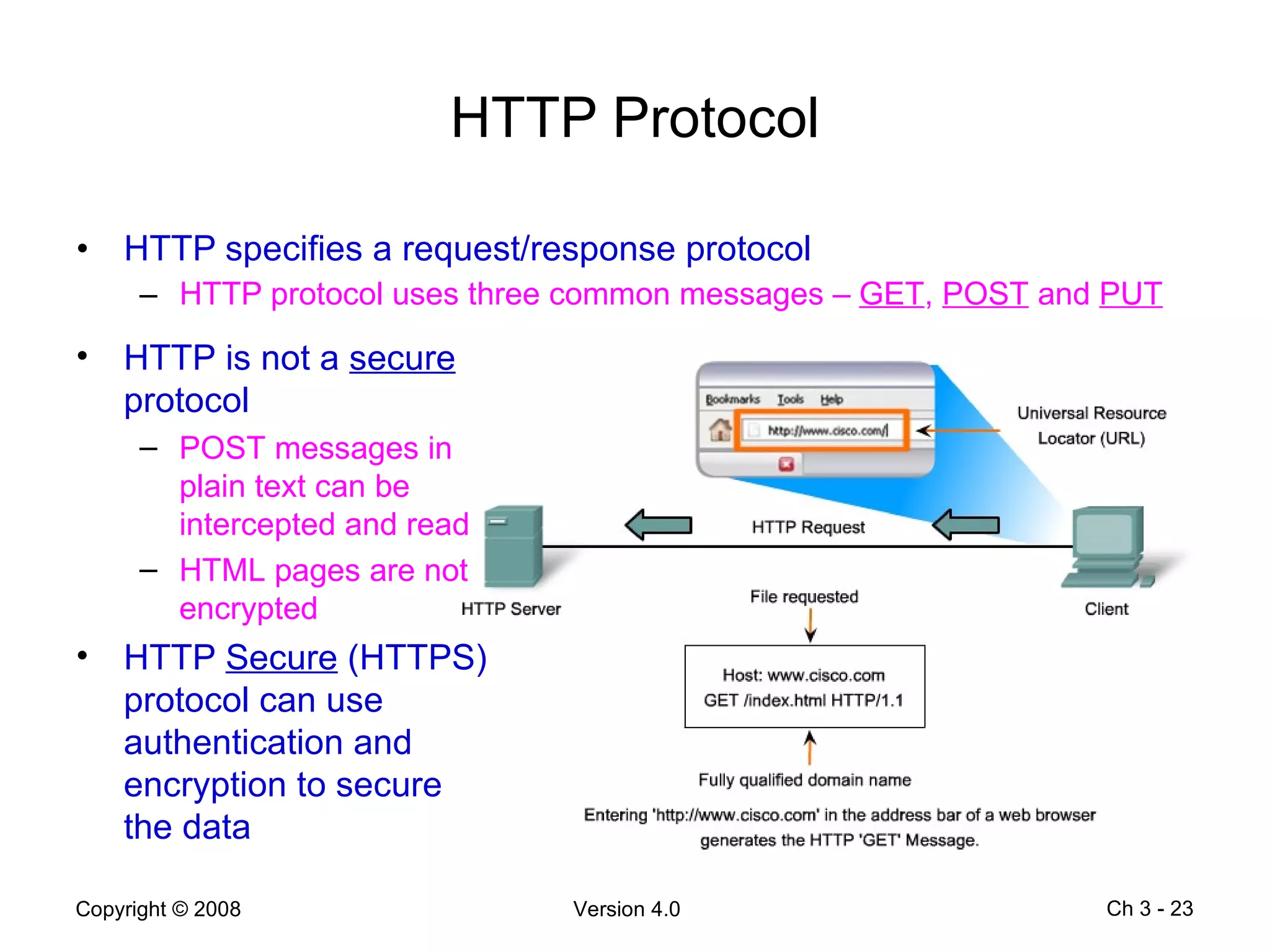
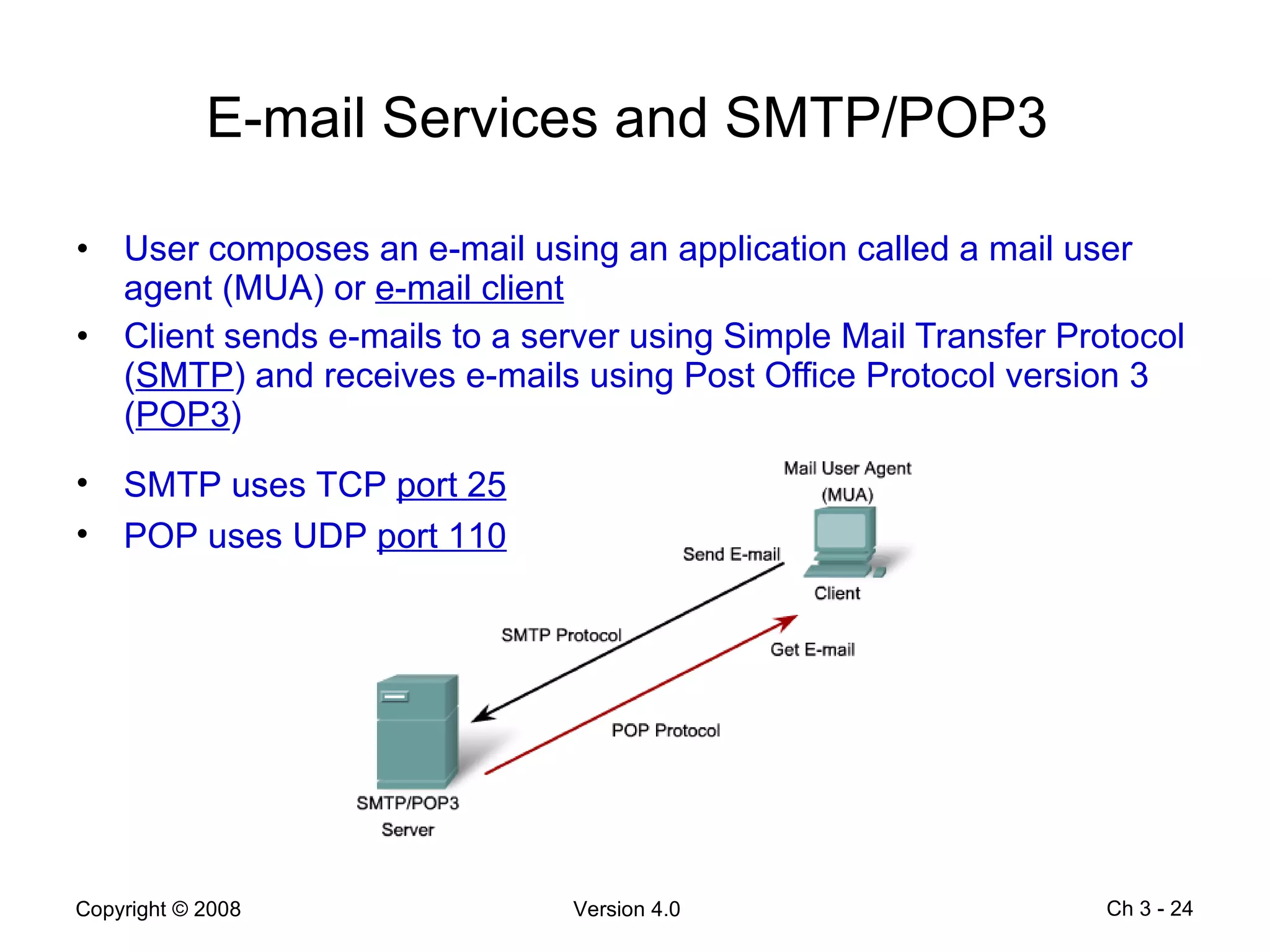
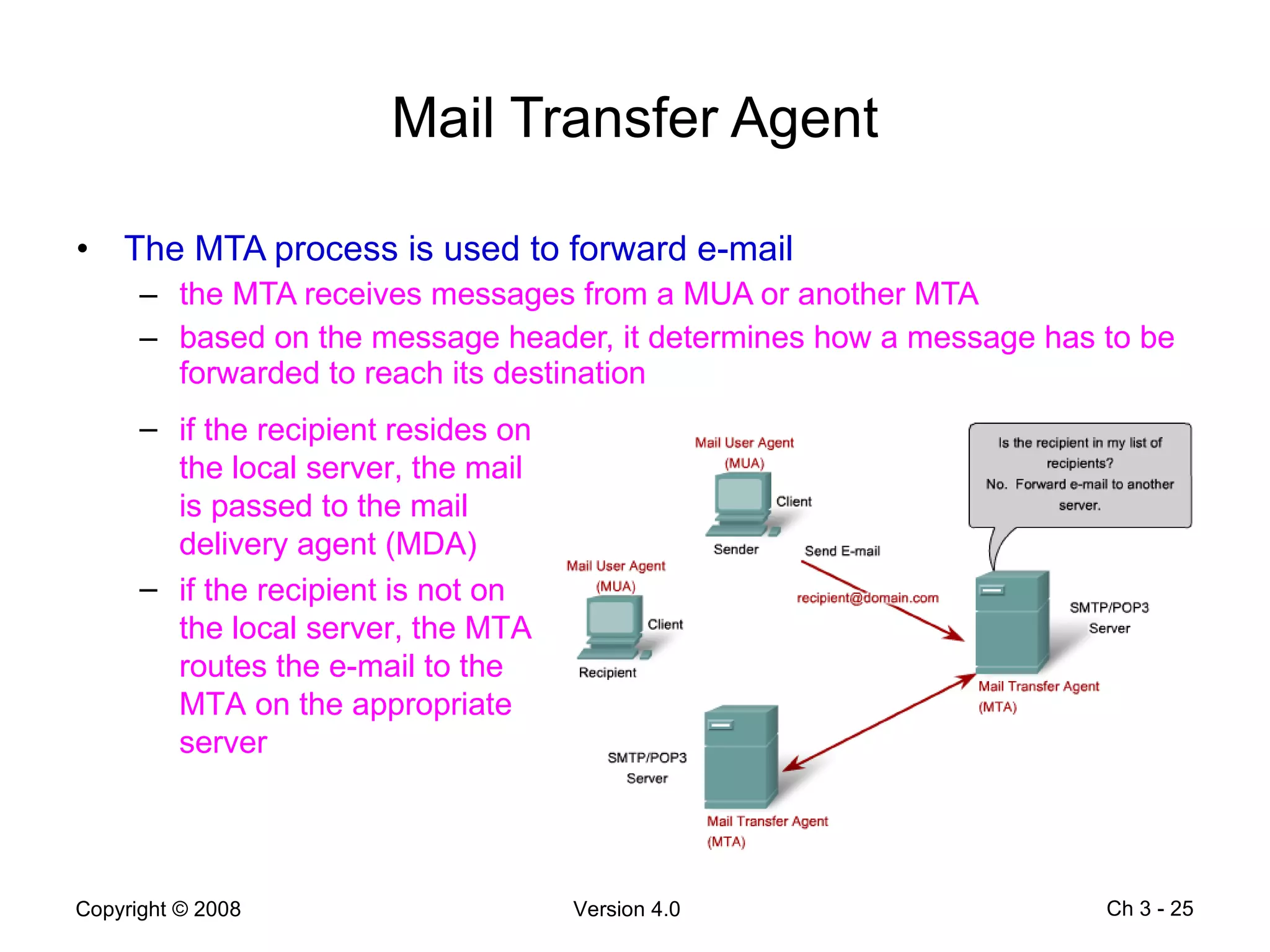
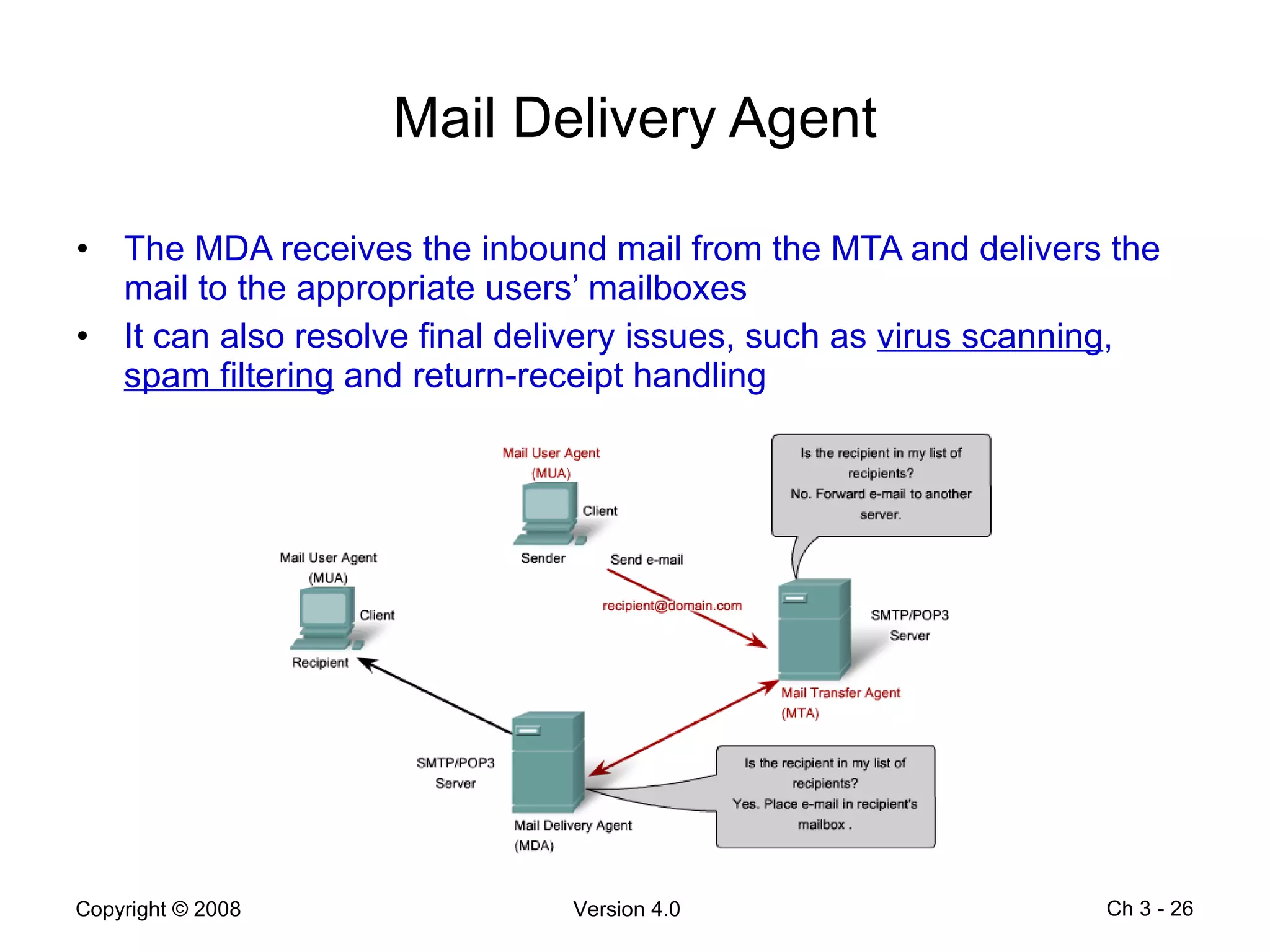
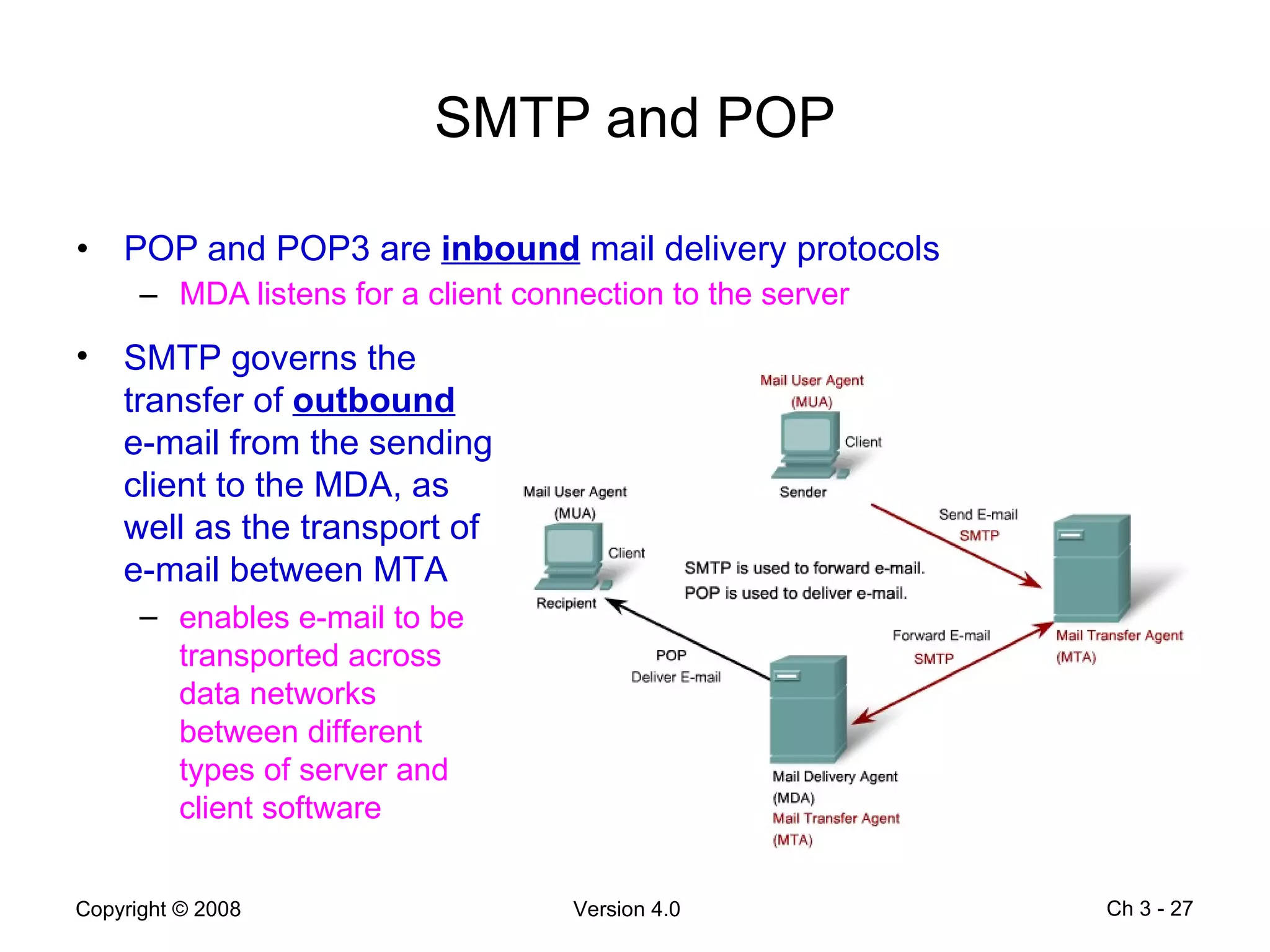
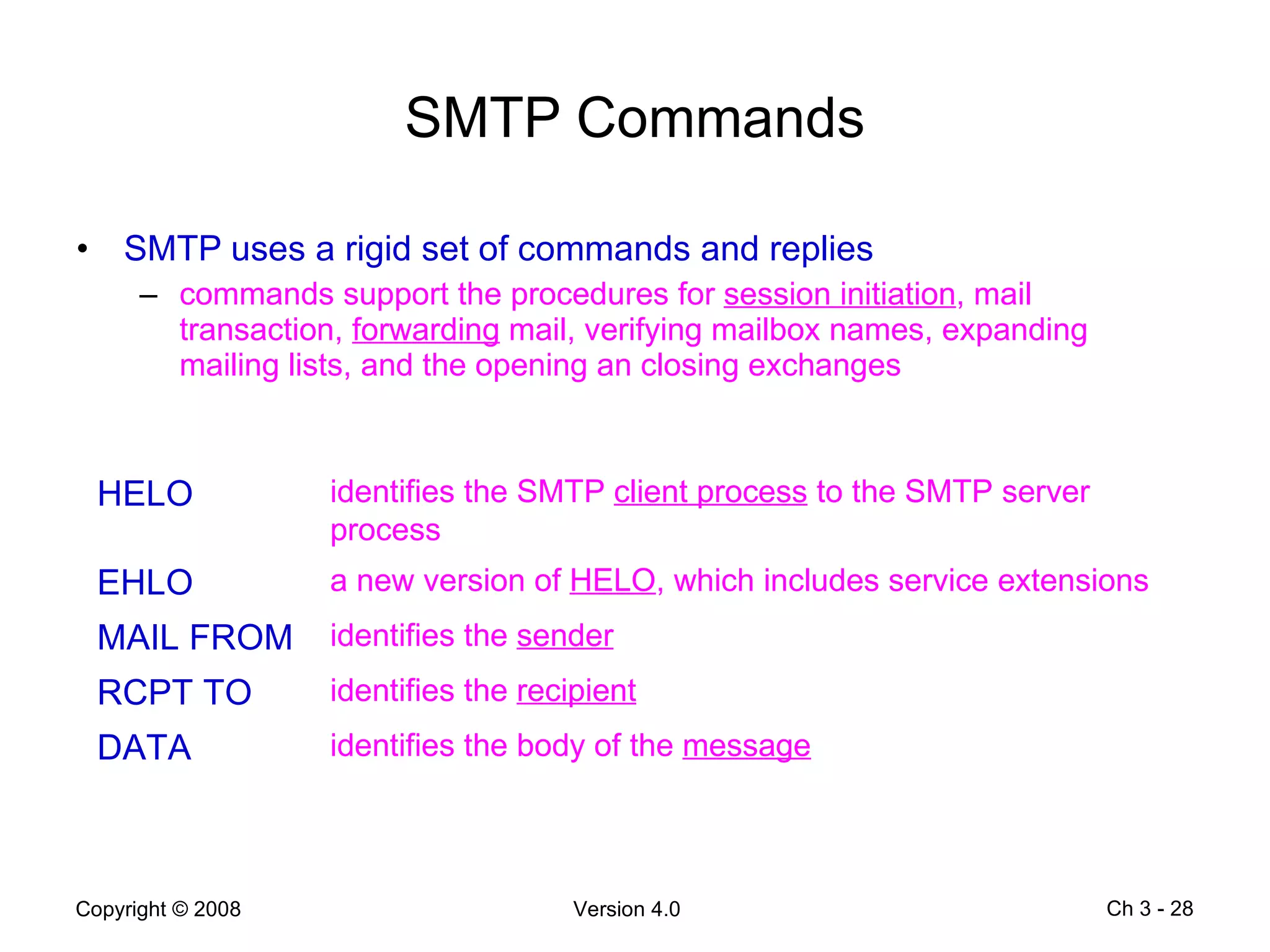
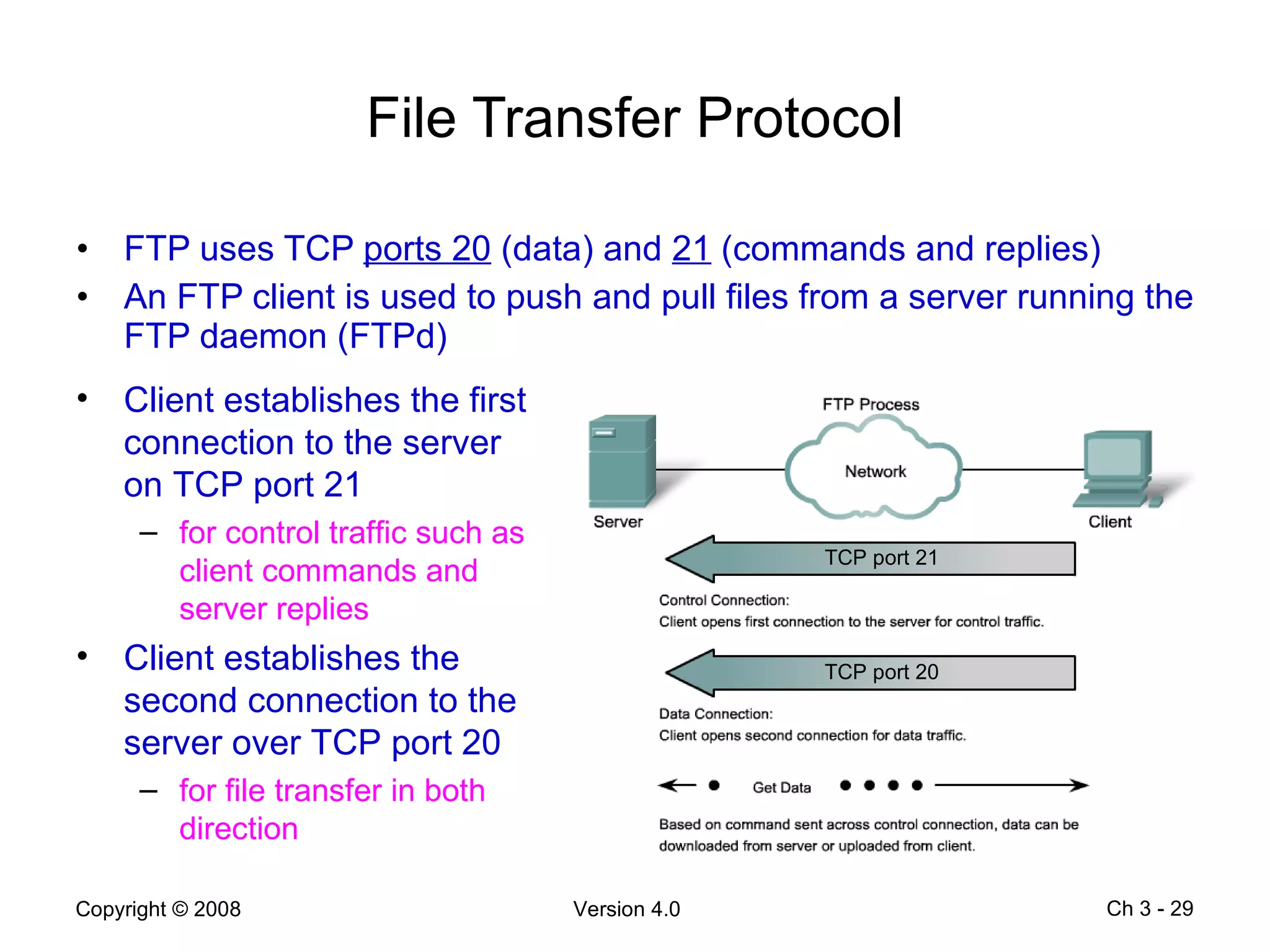
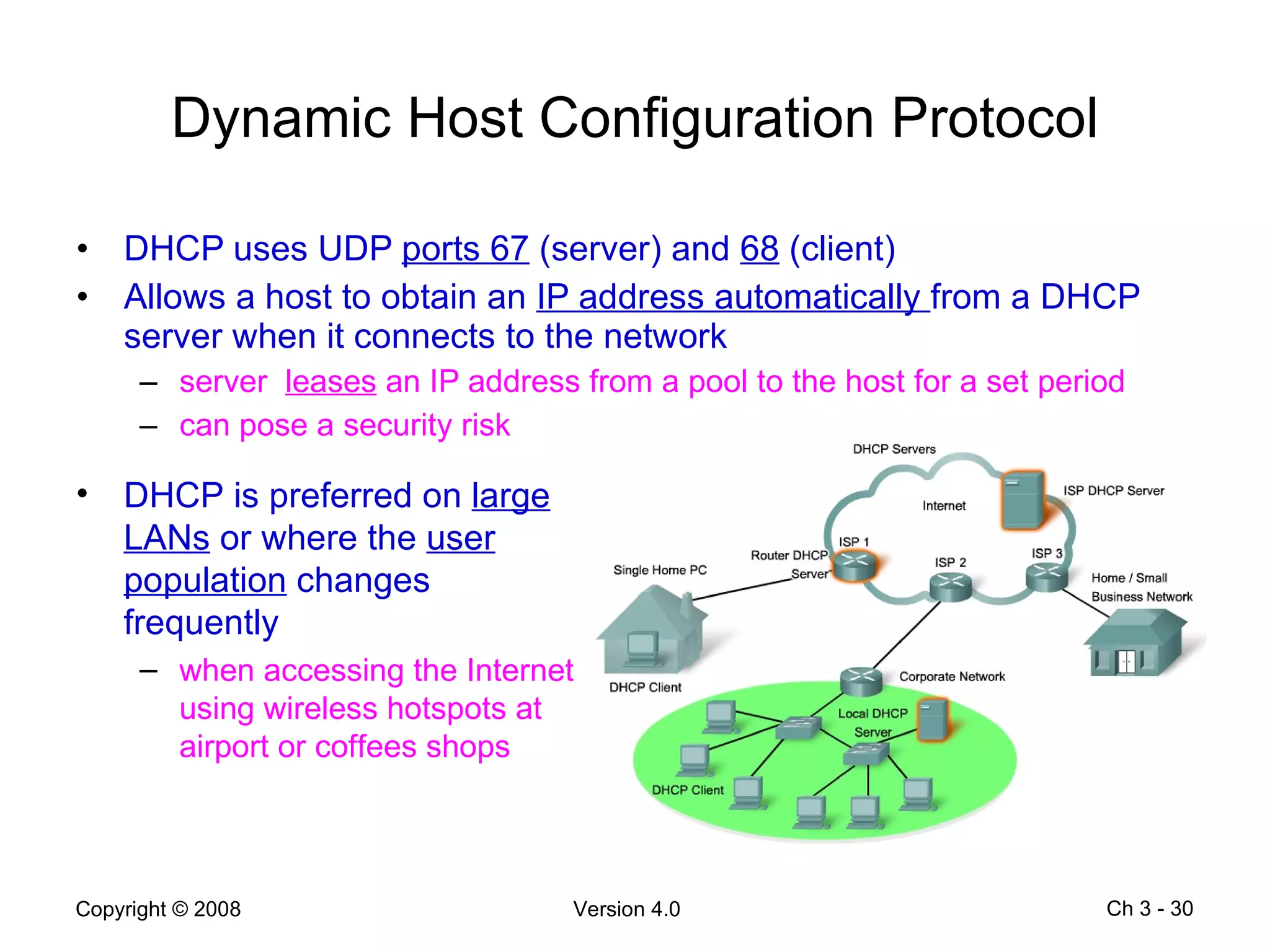
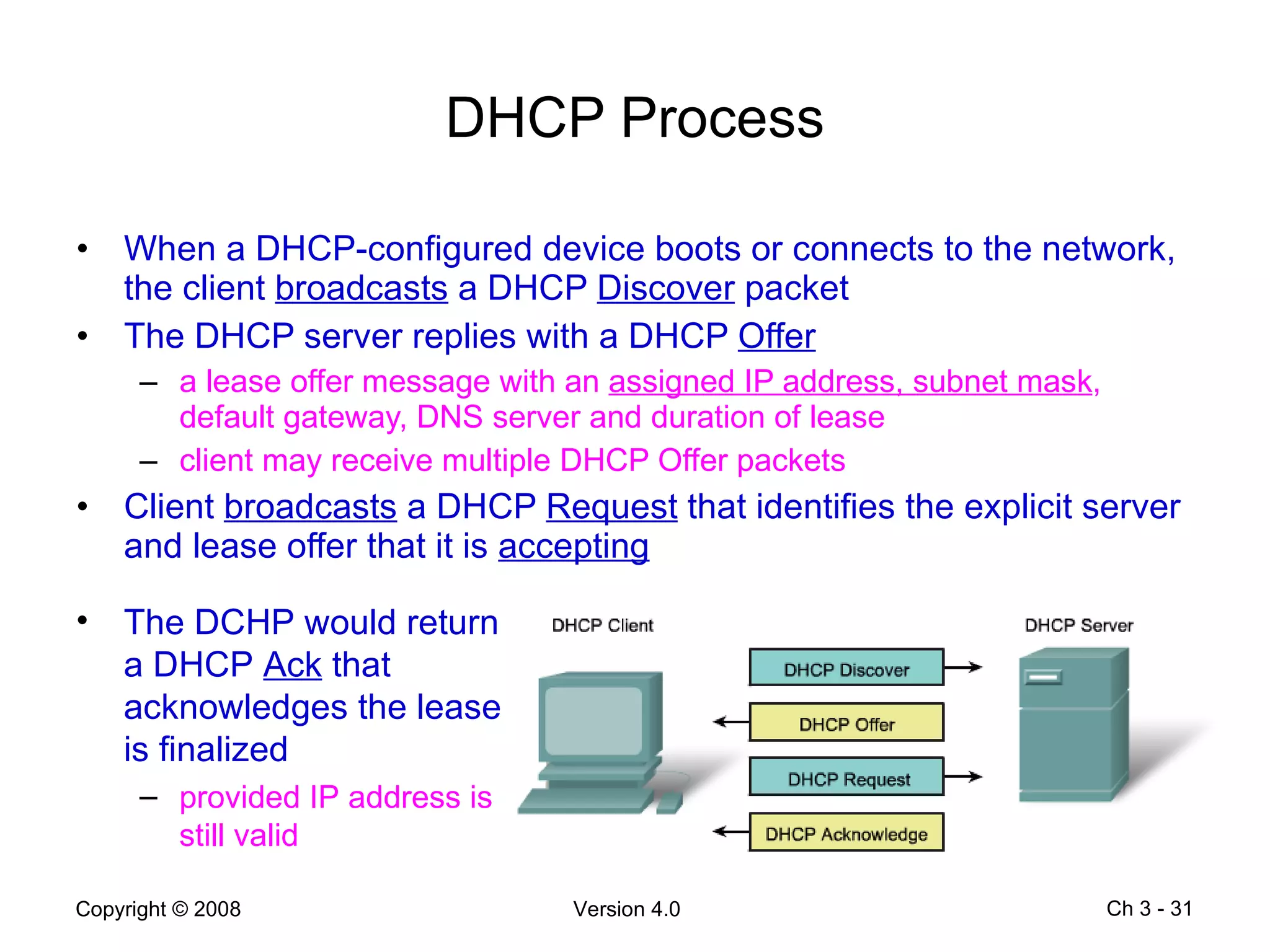
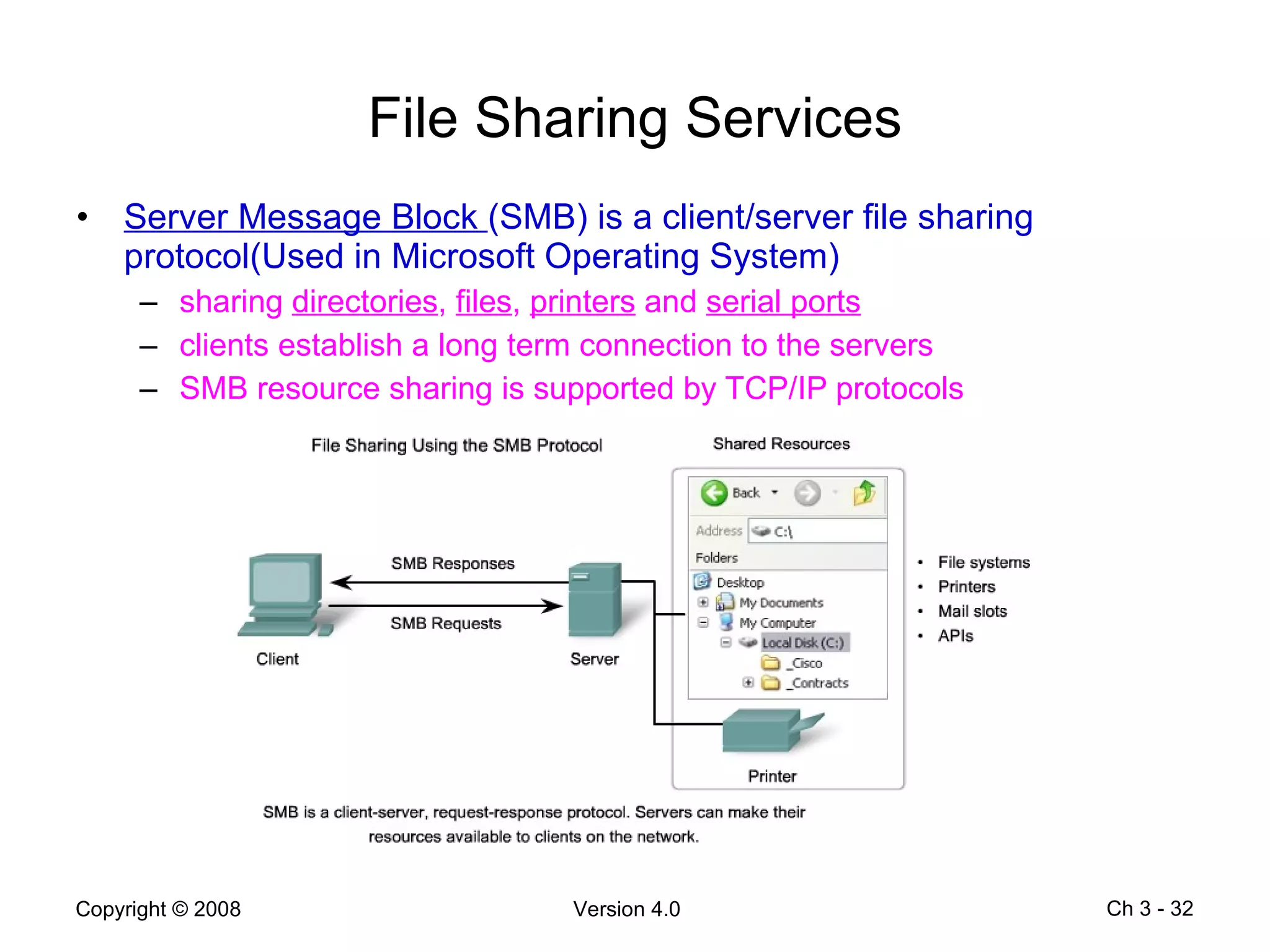
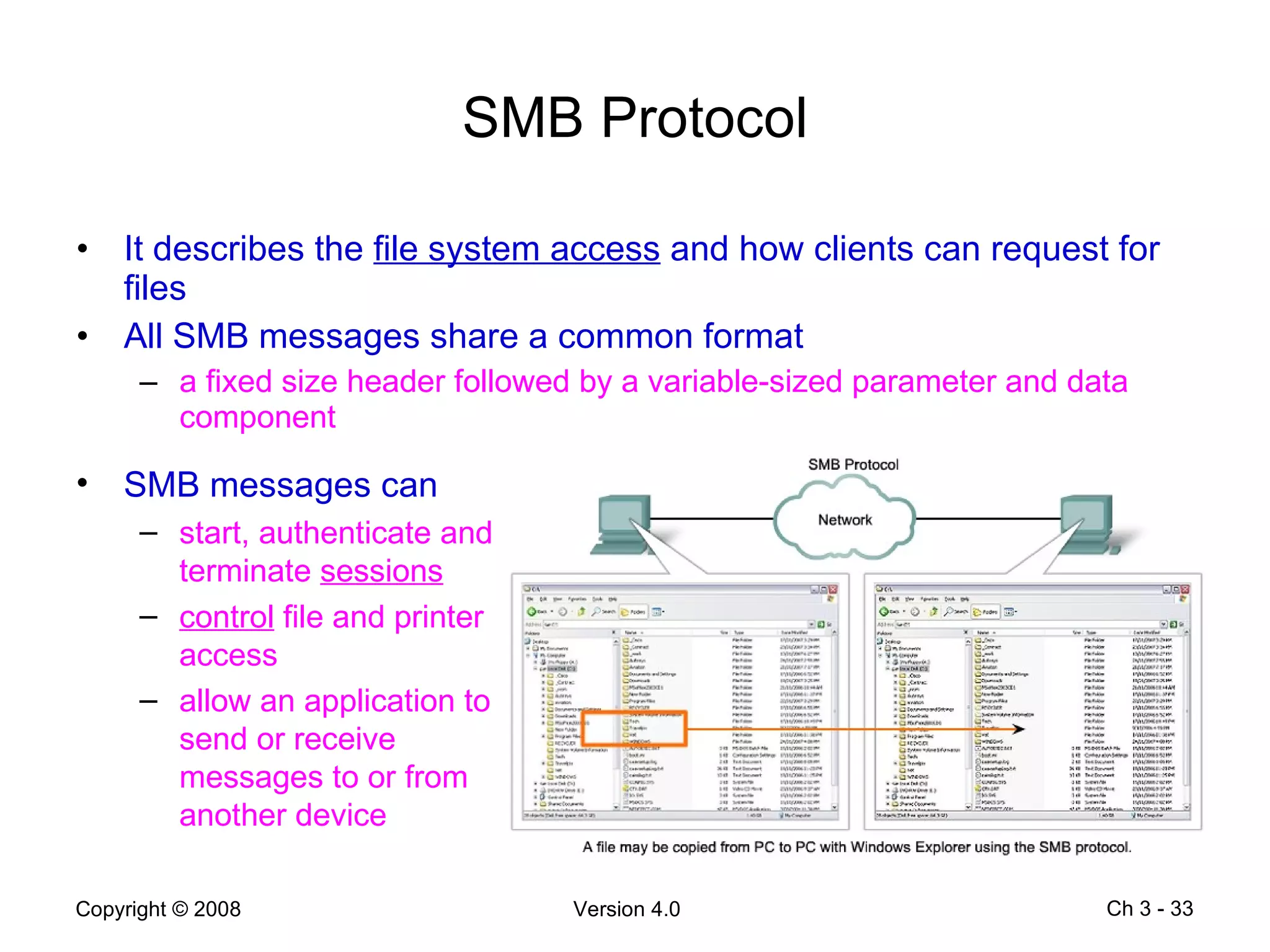
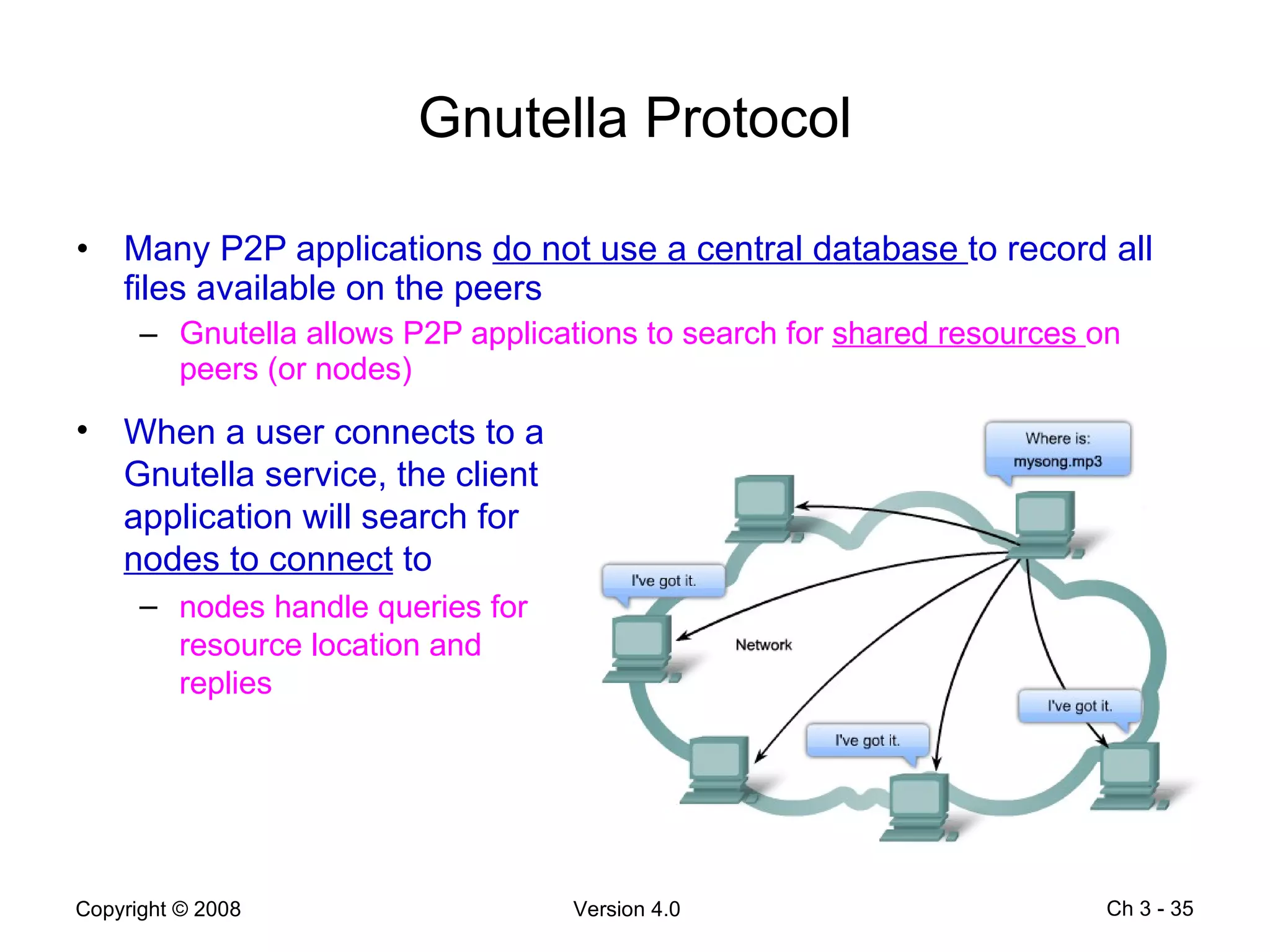
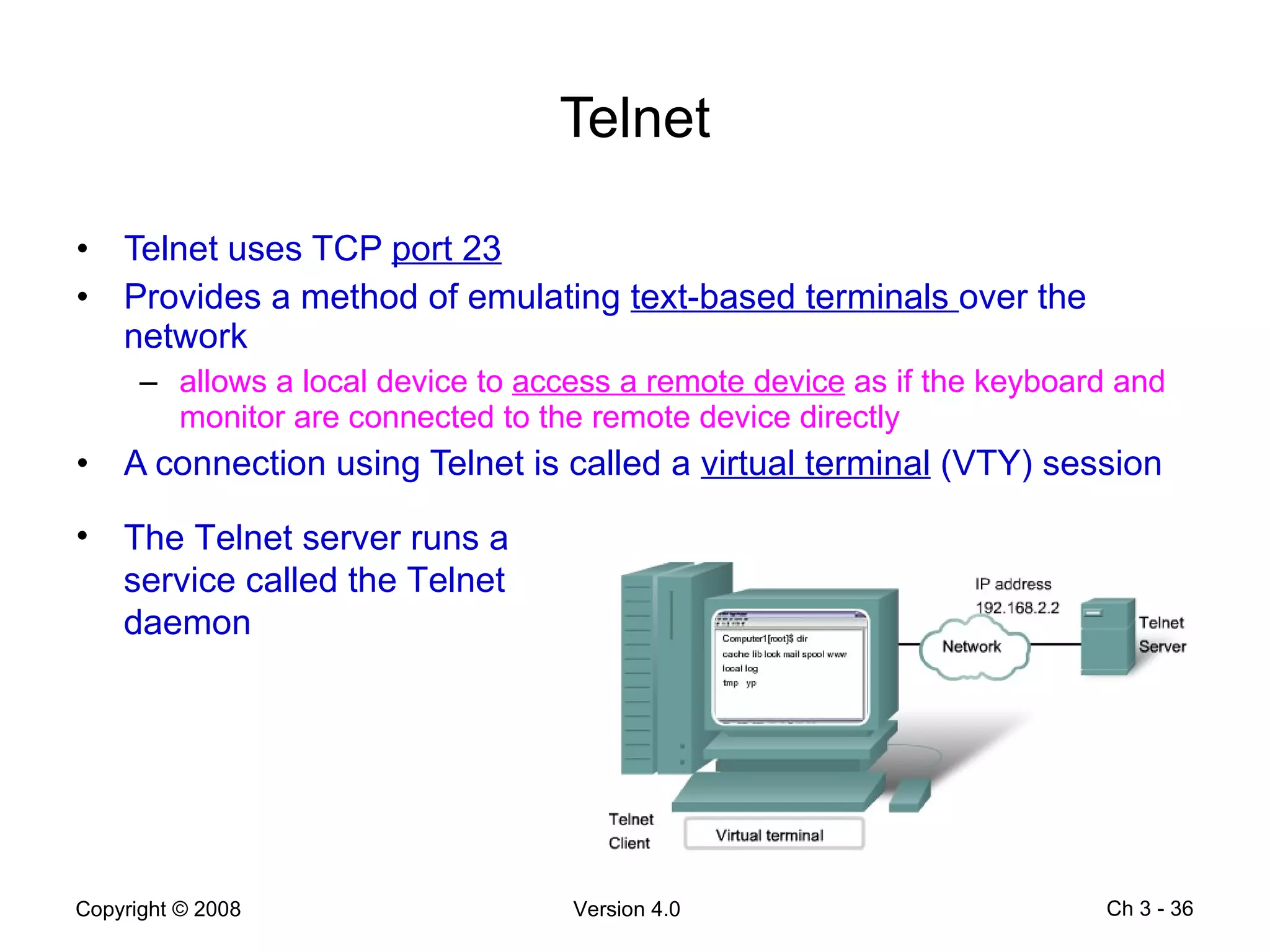
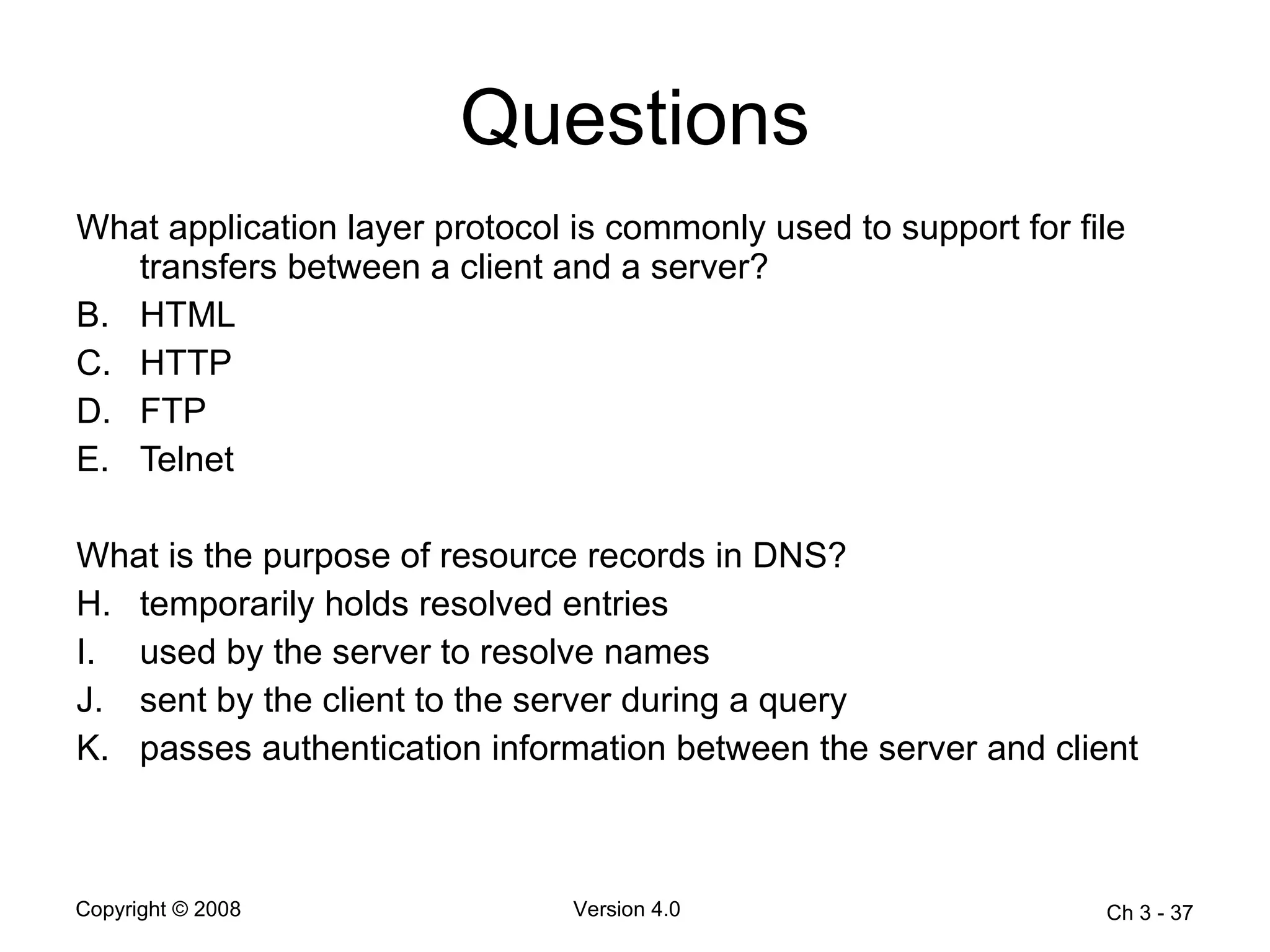
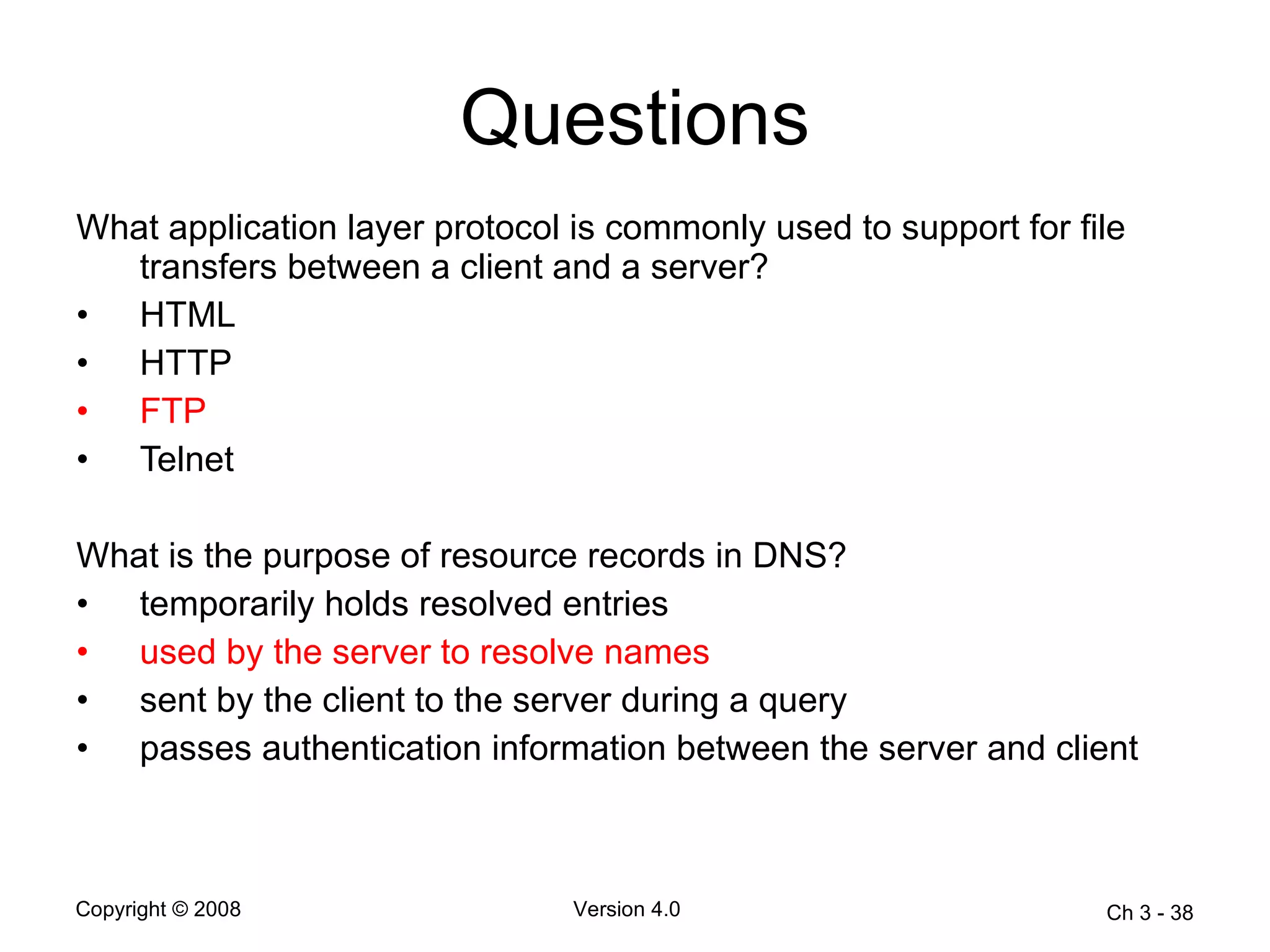
The document describes application layer protocols and services including:
- Application layer protocols provide end-user applications with network services and include HTTP, DNS, DHCP, SMTP/POP, and Telnet.
- Peer-to-peer applications allow devices to act as both clients and servers to share resources without a dedicated server.
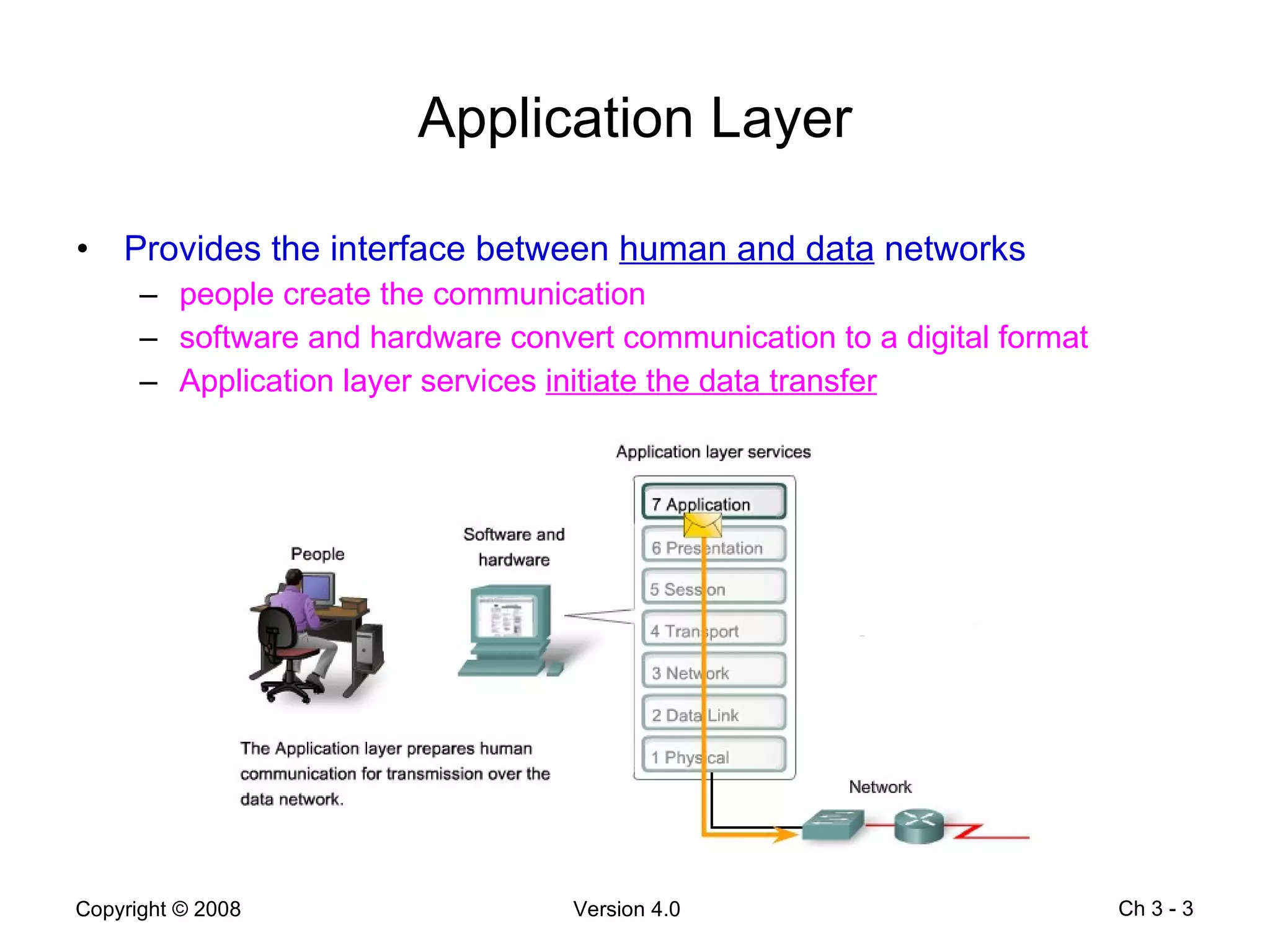
- Common application layer functions are establishing communication rules, structuring message formats, and defining interactions with lower layers.