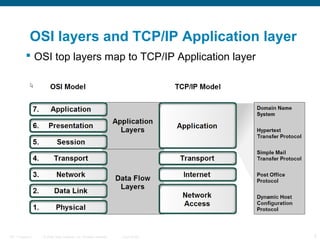
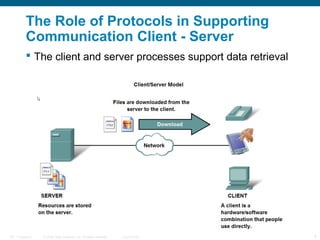
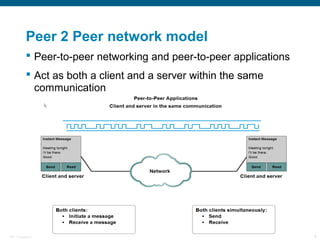
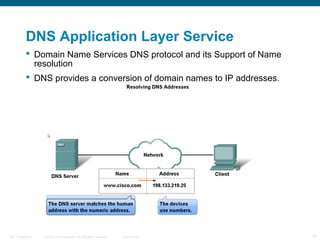
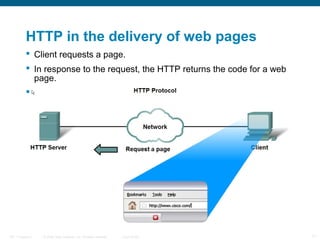
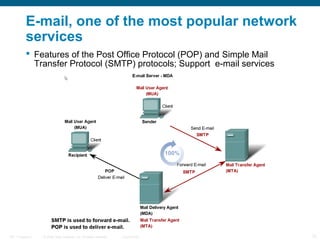
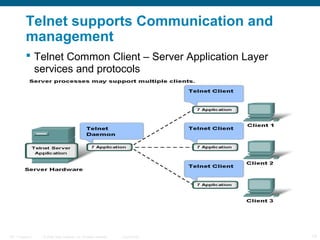
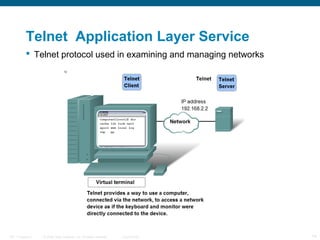
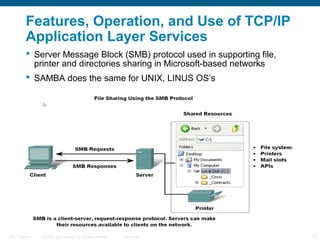
The document discusses the application layer in the OSI model and TCP/IP protocols. It describes how the application layer generates data and provides an interface between users and networks via applications. Common application layer protocols like HTTP, DNS, SMTP, and Telnet are examined along with their roles in file transfer, email services, network management, and supporting client-server and peer-to-peer communication models. The document also reviews presentation and session layers in OSI and various application layer protocols used in networking labs.