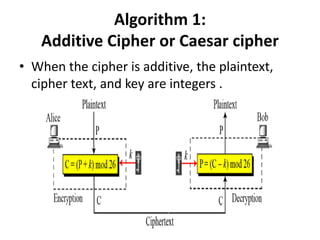
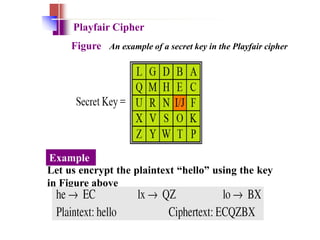
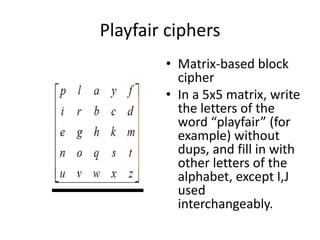
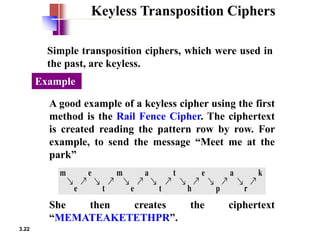
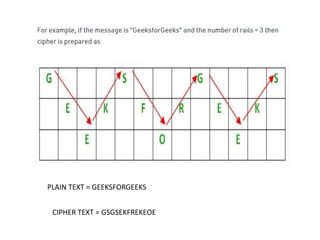
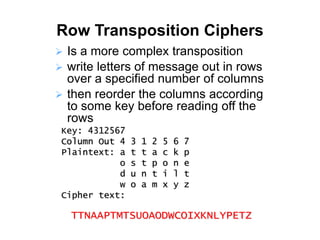
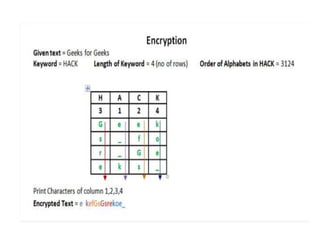
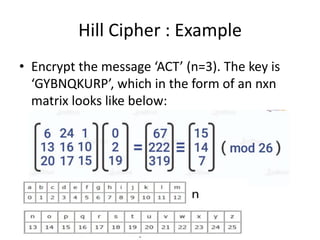
Classical encryption techniques include substitution ciphers like the Caesar cipher where letters are replaced, and transposition ciphers like the Rail Fence cipher where the order of letters is changed. The Playfair cipher is a substitution cipher that encrypts digrams (pairs of letters) based on a 5x5 key matrix. The Hill cipher is a polygraphic substitution cipher that encrypts blocks of letters using matrix multiplication modulo 26.