Embed presentation

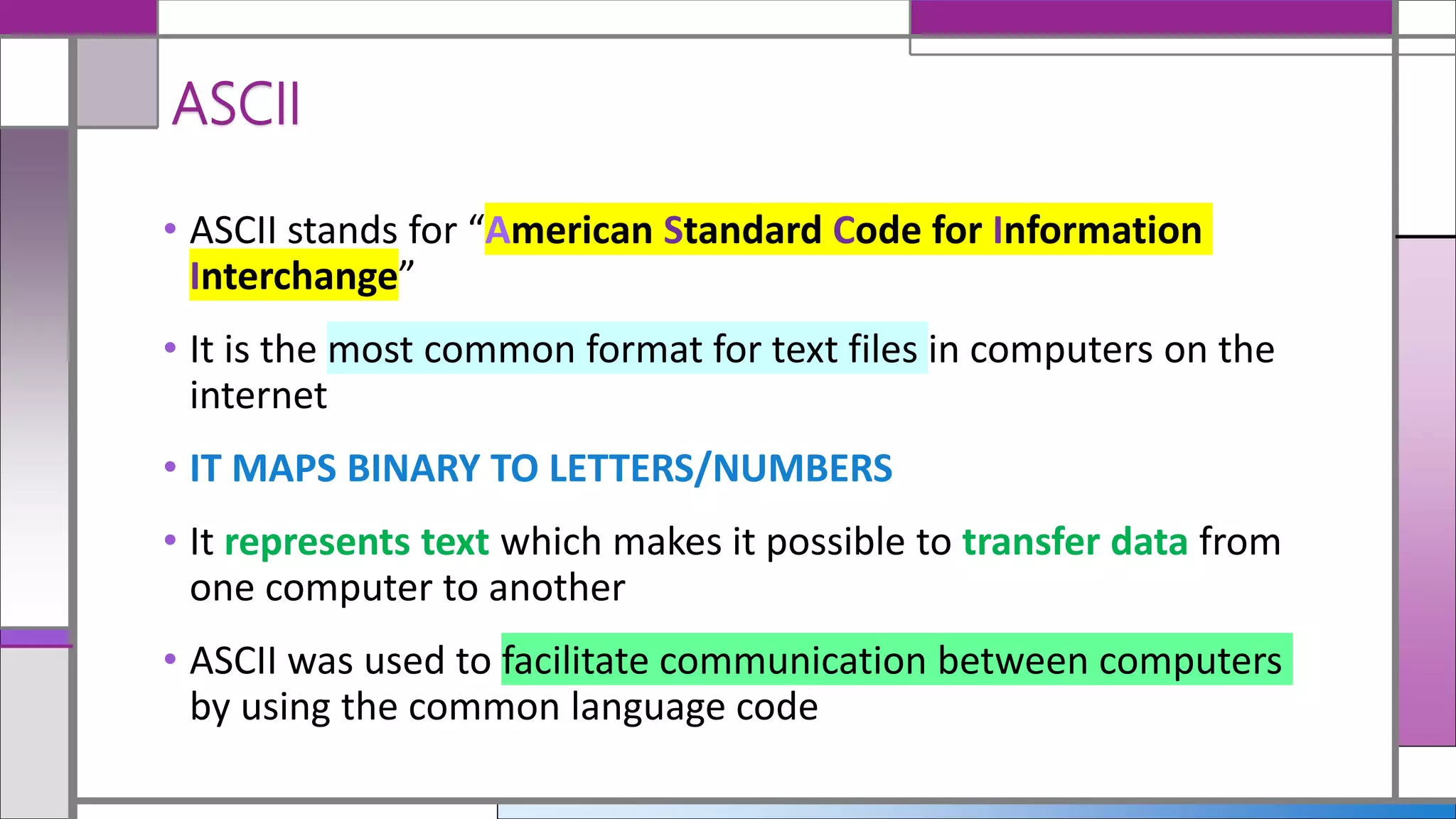
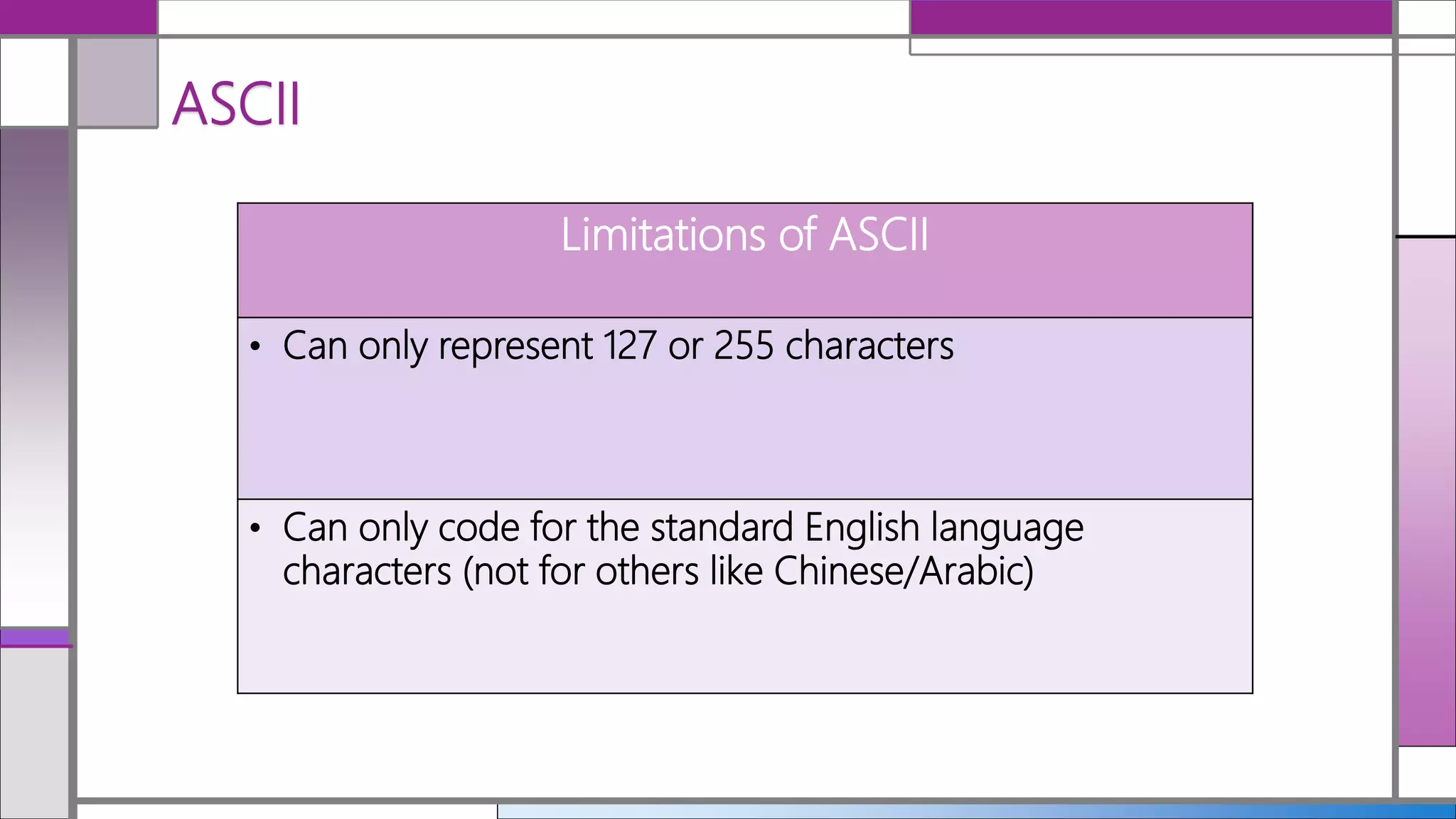




The document discusses ASCII and Unicode, highlighting ASCII as a common format for text files that represents a limited set of English characters. Unicode is introduced as a multilingual character coding system that supports a broader range of characters from various languages and facilitates global communication. It details the different UTF formats, indicating their bit sizes and character set expansions.






