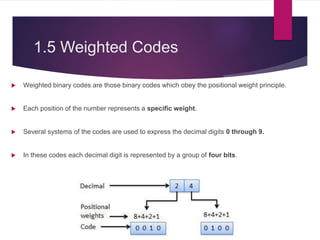
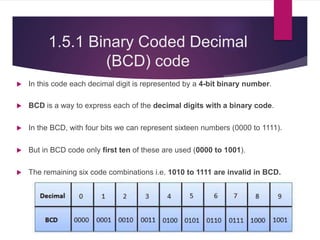
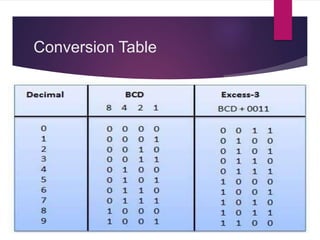
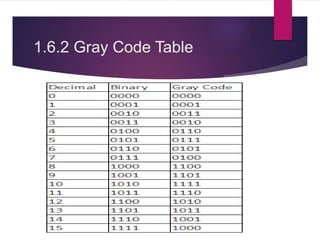
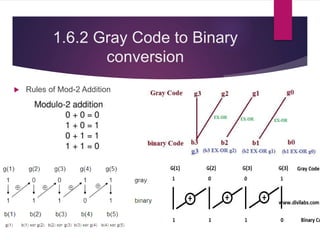
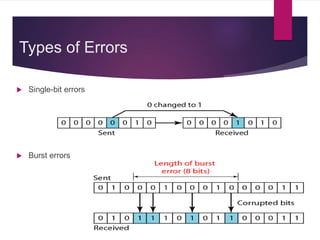
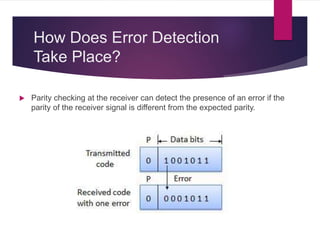
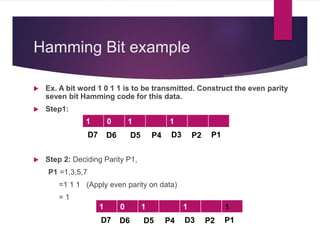
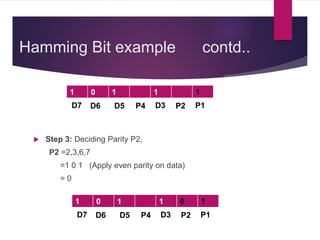
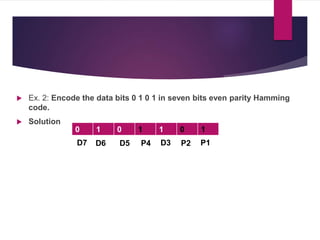
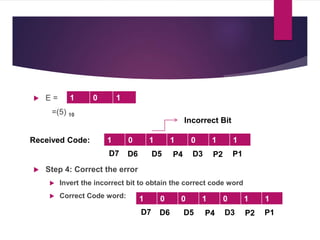
The document discusses various types of binary codes, including weighted and non-weighted codes, binary coded decimal, excess-3 code, gray code, and alphanumeric codes like ASCII and EBCDIC. It also addresses error detection and correction methods, such as parity bits and Hamming code, which are critical for maintaining accuracy in digital communications. Additionally, it highlights the advantages and disadvantages of different coding methods in relation to efficiency and implementation in digital systems.