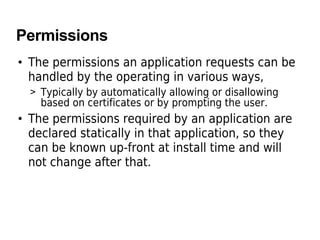
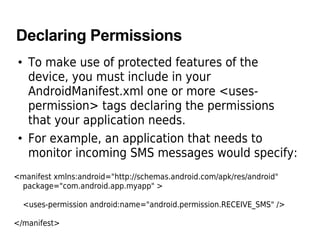
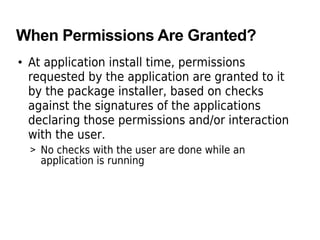
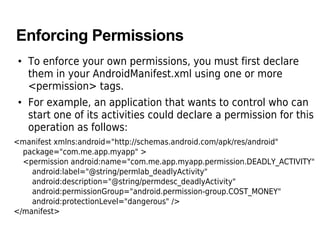
The document discusses Android security principles, permissions, and application signing. It describes how Android enforces security at the process level using Linux features and provides additional security through a permission mechanism. No application has default permission to perform operations that could harm other apps, the OS, or user. An app must explicitly declare any permissions it needs for additional capabilities. Permissions are declared in the app's manifest and granted at install time based on the app's certificate. The permissions an app requests cannot change after installation.