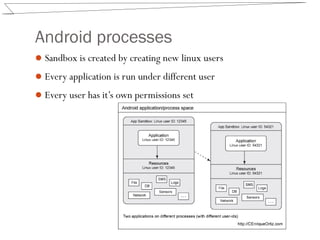
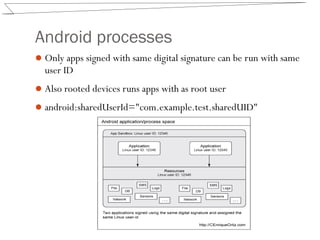
Android uses a permission model and sandboxing to isolate apps and their data. Each app runs as a separate Linux user and has its own permissions and filesystem area. SharedPreferences and SQLite databases are also isolated by app in private storage areas. Developers must specify any permissions needed in the app manifest and use the principle of least privilege to only request necessary permissions.

![Unix processes
F S UID PID PPID C PRI NIADDR SZ WCHAN TTY TIME CMD
4 S 0 1 0 0 68 0 - 373 select ? 0:02 init [2]](https://image.slidesharecdn.com/android1-131003031129-phpapp02/85/Android-1-3-320.jpg)