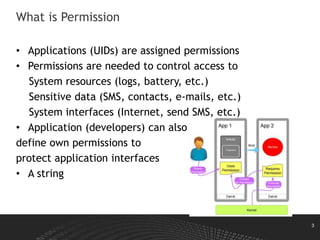
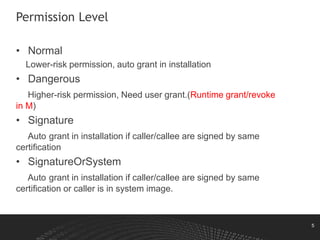
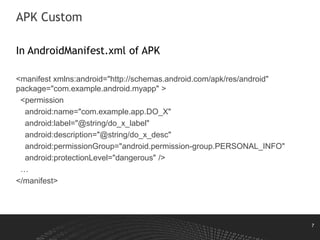
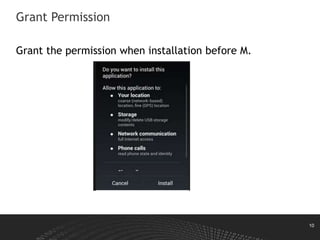
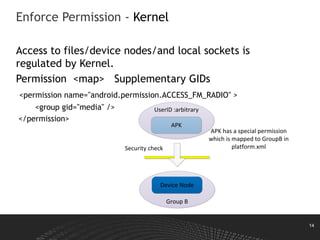
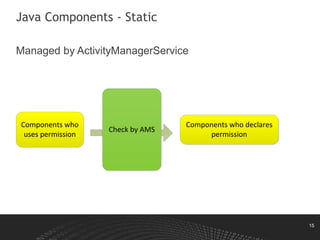
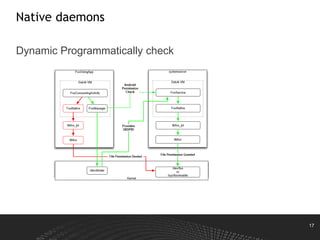
This document discusses Android permissions, including what permissions are, different permission levels (normal, dangerous, signature, signatureOrSystem), how to define and request permissions in the manifest file, how permissions are granted at install time and in runtime in Android M and later, and how permission enforcement works at the kernel, Java component, and native daemon levels. It also covers defining custom permissions in an APK manifest, permission conflicts, and revoking permissions in runtime.










![20
Runtime Permission - Caller
• Always Check for Permissions
• Handle Lack of Permissions Gracefully
if (checkSelfPermission(Manifest.permission.READ_CONTACTS)
!= PackageManager.PERMISSION_GRANTED) {
if (shouldShowRequestPermissionRationale(
Manifest.permission.READ_CONTACTS)) {
}
requestPermissions(new
String[]{Manifest.permission.READ_CONTACTS},
MY_PERMISSIONS_REQUEST_READ_CONTACTS);
return;
}](https://image.slidesharecdn.com/androidsecuirty-permission-upload-160705140348/85/Android-secuirty-permission-upload-20-320.jpg)