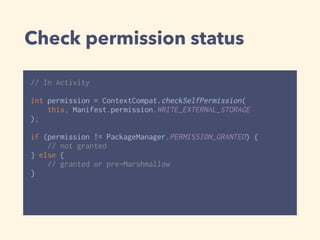
The document discusses Android's new permission model introduced in Android 6.0 (Marshmallow). It notes that normal permissions are automatically granted, while dangerous permissions need to be requested at runtime. It provides code samples to check permission status, request permissions, and handle the permission grant result. Developers are directed to the Android developer guide for more information on managing runtime permissions.


















![Request permission
if (
ActivityCompat.shouldShowRequestPermissionRationale(
this,
Manifest.permission.WRITE_EXTERNAL_STORAGE
)
) {
// should show rationale
} else {
// needs request permission
ActivityCompat.requestPermissions(
this,
new String[]{Manifest.permission.WRITE_EXTERNAL_STORAGE},
PERMISSION_REQUEST_CODE
);
}](https://image.slidesharecdn.com/android-permissionkanmoba-151028105650-lva1-app6891/85/Android-new-permission-model-25-320.jpg)
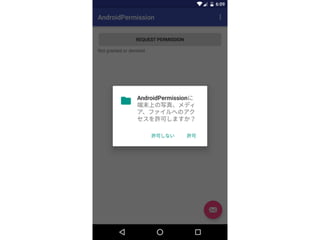

![Check permission granted
// In Activity
@Override
public void onRequestPermissionsResult(int requestCode, @NonNull String[]
permissions, @NonNull int[] grantResults) {
super.onRequestPermissionsResult(requestCode, permissions, grantResults);
if (requestCode == PERMISSION_REQUEST_CODE) {
int grantResult = grantResults[0];
String statusString = toStatusString(grantResult);
statusTextView.setText(statusString);
if (
grantResults.length > 0 &&
grantResult == PackageManager.PERMISSION_GRANTED
) {
// granted
} else {
// not granted
}
}
}](https://image.slidesharecdn.com/android-permissionkanmoba-151028105650-lva1-app6891/85/Android-new-permission-model-28-320.jpg)
