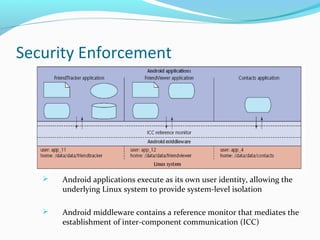
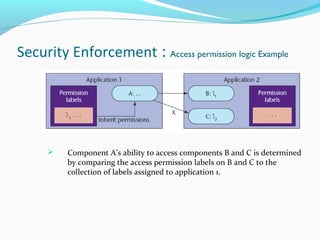
The document discusses Android OS architecture, focusing on security enforcement through a permission label assignment model that restricts application access. It highlights best practices for defining access permissions, including setting exported attributes, specifying intent broadcast permissions, and using separate read/write permissions. Lessons from the document emphasize the importance of a clear security policy and the role of mandatory access control in Android applications.