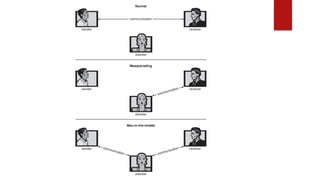
This document discusses operating system security. It begins by defining security as ensuring confidentiality and integrity of the OS. It then discusses common security problems like systems being targets for thieves. Security can be threatened by threats and attacks, which are intentional violations like malware or accidental issues like denial of service attacks. The goals of security systems are integrity, secrecy and availability. Attacks use methods like masquerading, replay attacks, and man-in-the-middle attacks. Security is protected at the physical, human, operating system and network levels. Measures include access control, encryption, authorization and detecting intrusions.