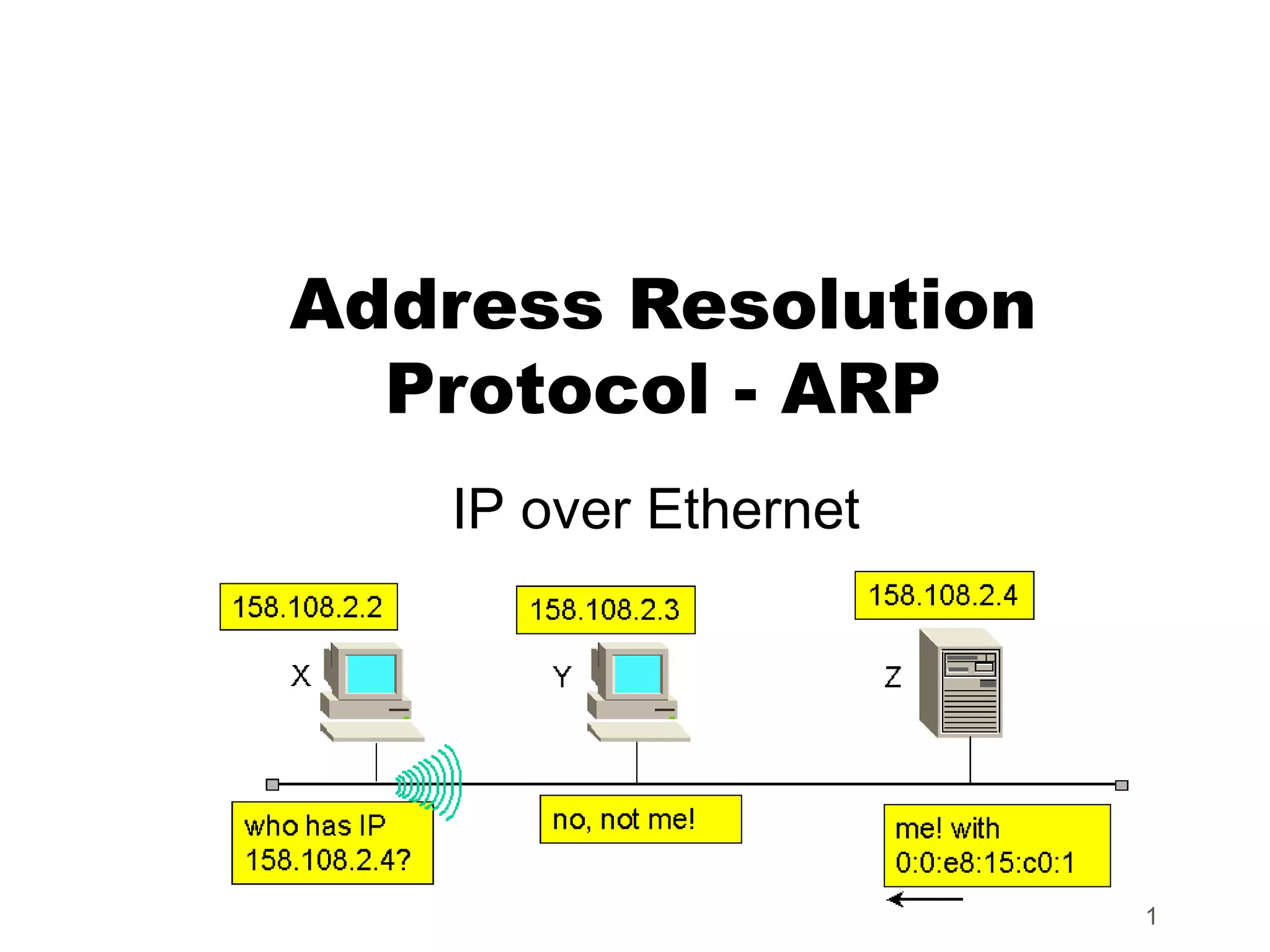
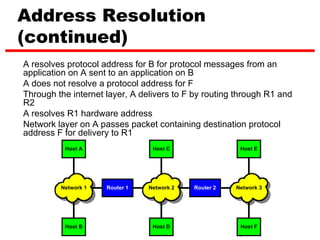
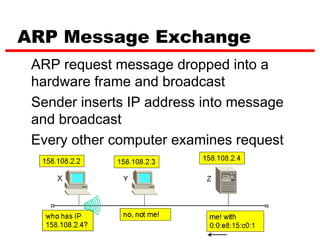
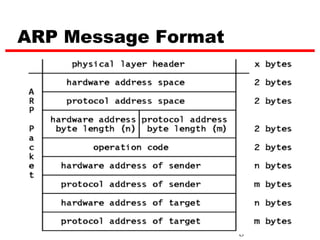
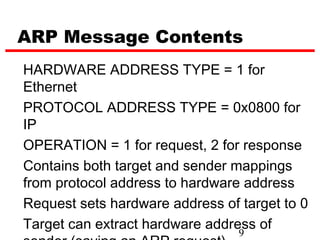
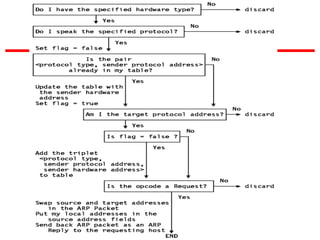
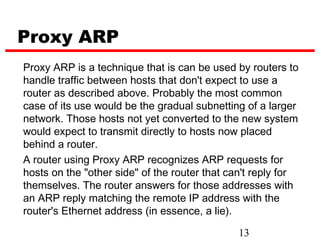
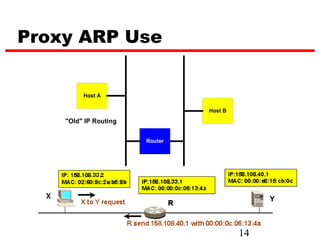
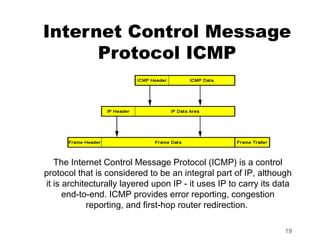
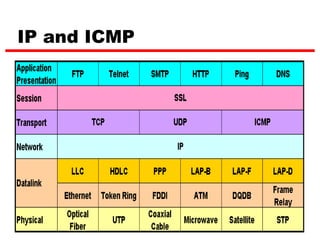
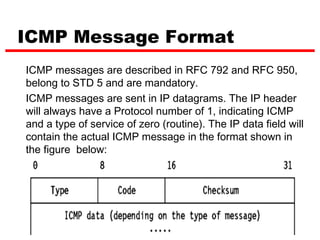
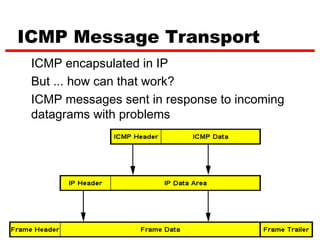
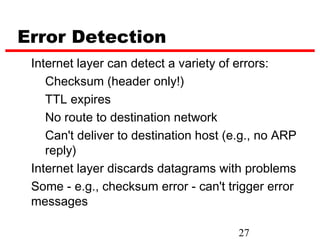
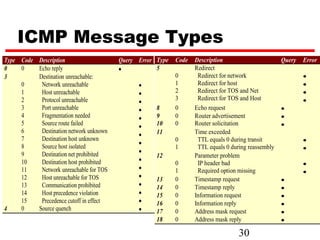
ICMP provides error reporting and feedback messages for IP. It uses IP datagrams to transport control messages between hosts and routers. ICMP messages include echo requests/replies used by ping, time exceeded and destination unreachable errors, redirects, and path MTU discovery fragments needed messages. ARP resolves IP addresses to hardware addresses locally through broadcast requests and unicast replies to populate caches. Proxy ARP allows routers to answer for hosts on remote networks to allow communication before subnet migration.