This document provides an introduction to various protocols related to electronic commerce and the internet. It discusses IP addressing and how IP addresses are assigned to devices. It then explains protocols like ARP, RARP, BOOTP, DHCP, and ICMP that are used to map IP addresses to hardware addresses, assign IP addresses, and handle network errors and messages.




![PREPARED BY ARUN PRATAP SINGH 4
4
An Internet Protocol address (IP address) is a numerical label assigned to each device (e.g.,
computer, printer) participating in a computer network that uses the Internet Protocol for
communication.[1]
An IP address serves two principal functions: host or network
interface identification and location addressing. Its role has been characterized as follows:
"A name indicates what we seek. An address indicates where it is. A route indicates how to get there."](https://image.slidesharecdn.com/webtechnologyandcommerceunit-1byarunpratapsingh-140728225010-phpapp02/85/Web-technology-and-commerce-unit-1-5-320.jpg)
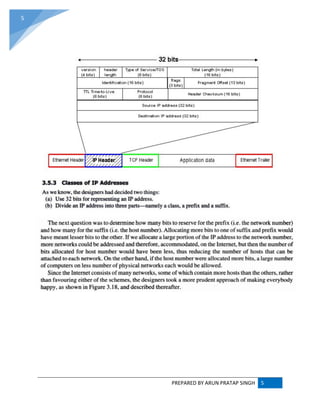
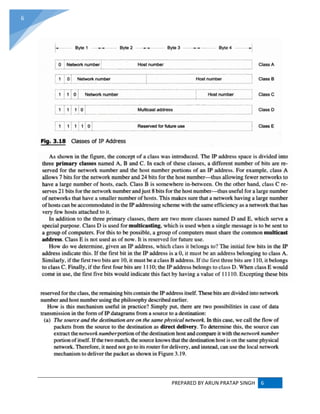
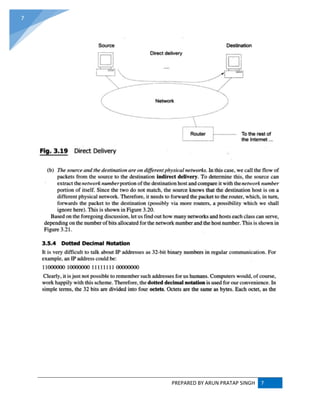
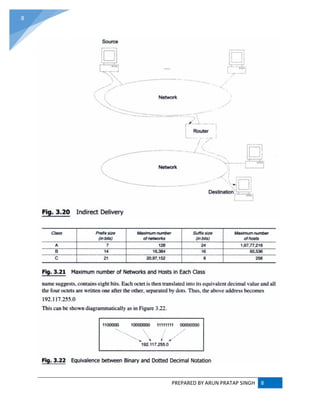
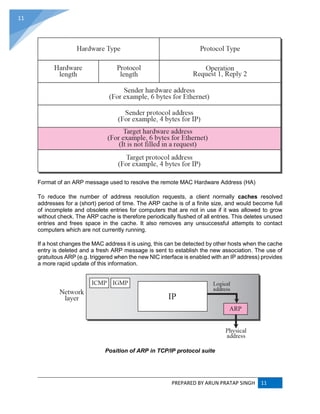
![PREPARED BY ARUN PRATAP SINGH 9
9
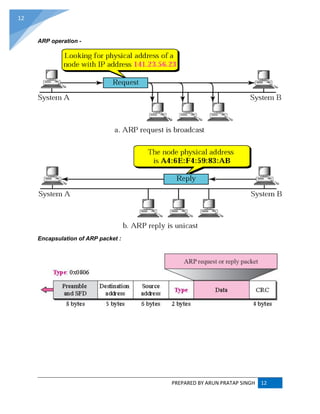
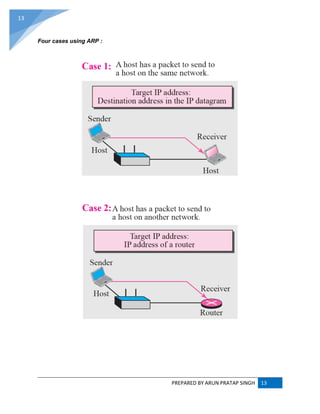
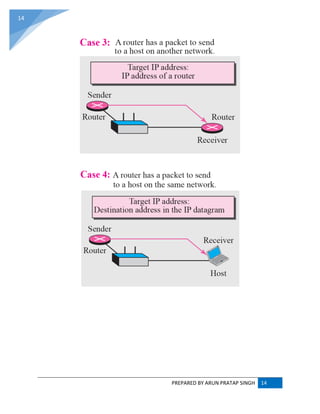
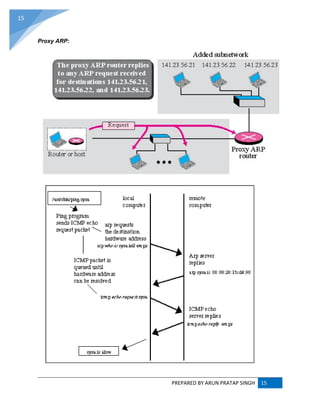
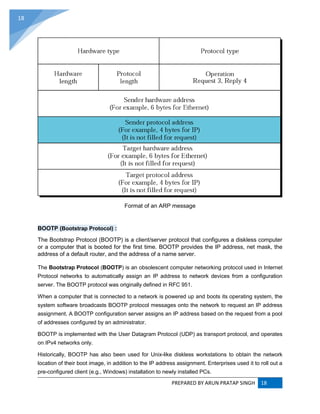
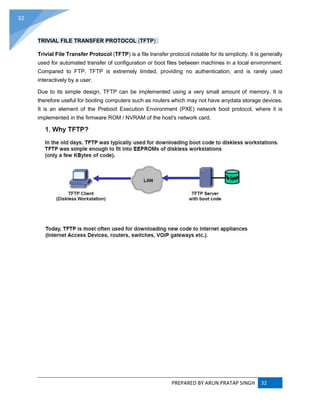
ADDRESS RESOLUTION PROTOCOL (ARP) :
ARP converts an Internet Protocol (IP) address to its corresponding physical network address.
ARP is a low-level network protocol, operating at Layer 2 of the OSI model.
The address resolution protocol (ARP) is a protocol used by the Internet Protocol (IP) [RFC826],
specifically IPv4, to map IP network addresses to the hardware addresses used by a data link
protocol. The protocol operates below the network layer as a part of the interface between the
OSI network and OSI link layer. It is used when IPv4 is used over Ethernet.](https://image.slidesharecdn.com/webtechnologyandcommerceunit-1byarunpratapsingh-140728225010-phpapp02/85/Web-technology-and-commerce-unit-1-10-320.jpg)

![PREPARED BY ARUN PRATAP SINGH 16
16
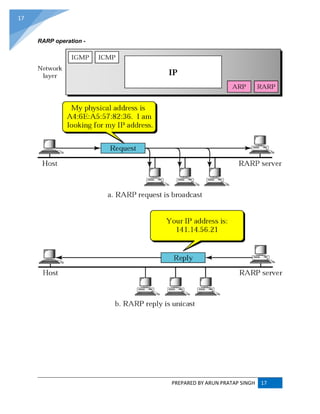
RARP (REVERSE ADDRESS RESOLUTION PROTOCOL) :
RARP (Reverse Address Resolution Protocol) is a protocol by which a physical machine in a local
area network can request to learn its IP address from a gateway server's Address Resolution
Protocol (ARP) table or cache. A network administrator creates a table in a local area network's
gateway router that maps the physical machine (or Media Access Control -MAC address)
addresses to corresponding Internet Protocol addresses. When a new machine is set up, its
RARP client program requests from the RARP server on the router to be sent its IP address.
Assuming that an entry has been set up in the router table, the RARP server will return the IP
address to the machine which can store it for future use.
RARP is available for Ethernet, Fiber Distributed-Data Interface, and token ring LANs.
The Reverse Address Resolution Protocol (RARP) is an obsolete computer networking protocol
used by a client computer to request its Internet Protocol (IPv4) address from a computer network,
when all it has available is its Link Layer or hardware address, such as a MAC address. The client
broadcasts the request, and does not need prior knowledge of the network topology or the identities
of servers capable of fulfilling its request.
RARP is described in Internet Engineering Task Force (IETF) publication RFC 903.[1] It has been
rendered obsolete by the Bootstrap Protocol (BOOTP) and the modern Dynamic Host Configuration
Protocol (DHCP), which both support a much greater feature set than RARP.
RARP requires one or more server hosts to maintain a database of mappings of Link Layer addresses
to their respective protocol addresses. Media Access Control (MAC) addresses needed to be
individually configured on the servers by an administrator. RARP was limited to serving only IP
addresses.
Reverse ARP differs from the Inverse Address Resolution Protocol (InARP) described in RFC 2390,
which is designed to obtain the IP address associated with a local Frame Relay data link connection
identifier. InARP is not used in Ethernet.
Position of ARP and RARP in TCP/IP protocol suite](https://image.slidesharecdn.com/webtechnologyandcommerceunit-1byarunpratapsingh-140728225010-phpapp02/85/Web-technology-and-commerce-unit-1-17-320.jpg)
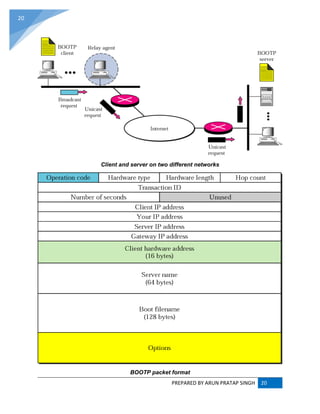
![PREPARED BY ARUN PRATAP SINGH 21
21
Use of UDP ports
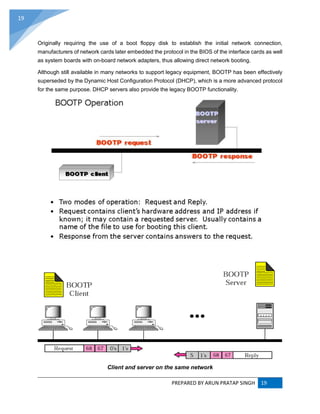
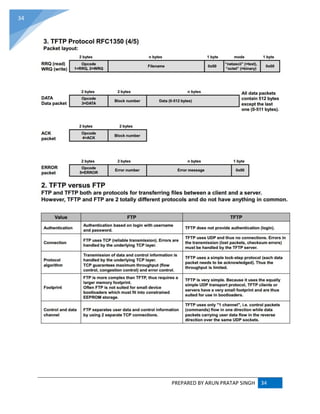
DHCP (Dynamic Host Configuration Protocol) :
The Dynamic Host Configuration Protocol (DHCP) is a standardized networking protocol used
on Internet Protocol (IP) networks for dynamically distributing network configuration parameters,
such as IP addresses for interfaces and services. With DHCP, computers request IP addresses
and networking parameters automatically from a DHCP server, reducing the need for a network
administrator or a user to configure these settings manually.
The Dynamic Host Configuration Protocol is used by computers for requesting Internet Protocol
parameters, such as an IP address from a network server. The protocol operates based on
the client-server model. DHCP is very common in all modern networks[1]
ranging in size from home
networks to large campus networks and regional Internet service provider networks. Most
residential network routers receive a globally unique IP address within the provider network.
Within a local network, DHCP assigns a local IP address to devices connected to the local
network.](https://image.slidesharecdn.com/webtechnologyandcommerceunit-1byarunpratapsingh-140728225010-phpapp02/85/Web-technology-and-commerce-unit-1-22-320.jpg)
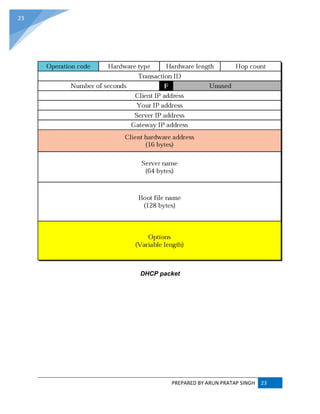
![PREPARED BY ARUN PRATAP SINGH 22
22
When a computer or other networked device connects to a network, its DHCP client software in
the operating system sends a broadcast query requesting necessary information. Any DHCP
server on the network may service the request. The DHCP server manages a pool of IP addresses
and information about client configuration parameters such as default gateway, domain name,
the name servers, and time servers. On receiving a request, the server may respond with specific
information for each client, as previously configured by an administrator, or with a specific address
and any other information valid for the entire network, and the time period for which the allocation
(lease) is valid. A host typically queries for this information immediately after booting, and
periodically thereafter before the expiration of the information. When an assignment is refreshed
by the client computer, it initially requests the same parameter values, but may be assigned a
new address from the server, based on the assignment policies set by administrators.
On large networks that consist of multiple links, a single DHCP server may service the entire
network when aided by DHCP relay agents located on the interconnecting routers. Such agents
relay messages between DHCP clients and DHCP servers located on different subnets.
Depending on implementation, the DHCP server may have three methods of allocating IP-
addresses:
dynamic allocation: A network administrator reserves a range of IP addresses for DHCP, and
each client computer on the LAN is configured to request an IP address from the
DHCP server during network initialization. The request-and-grant process uses a lease
concept with a controllable time period, allowing the DHCP server to reclaim (and then
reallocate) IP addresses that are not renewed.
automatic allocation: The DHCP server permanently assigns an IP address to a requesting
client from the range defined by the administrator. This is like dynamic allocation, but the
DHCP server keeps a table of past IP address assignments, so that it can preferentially assign
to a client the same IP address that the client previously had.
static allocation: The DHCP server allocates an IP address based on a preconfigured mapping
to each client's MAC address. This feature is variously called static DHCP assignment by DD-
WRT, fixed-address by the dhcpd documentation, address reservation by Netgear, DHCP
reservation or static DHCP by Cisco and Linksys, and IP address reservation or MAC/IP
address binding by various other router manufacturers.
DHCP is used for Internet Protocol version 4 (IPv4), as well as IPv6. While both versions serve
the same purpose, the details of the protocol for IPv4 and IPv6 are sufficiently different that they
may be considered separate protocols.[2]
For IPv6 operation, devices may alternatively
use stateless address autoconfiguration. IPv4 hosts may also use link-local addressing to achieve
operation restricted to the local network link.](https://image.slidesharecdn.com/webtechnologyandcommerceunit-1byarunpratapsingh-140728225010-phpapp02/85/Web-technology-and-commerce-unit-1-23-320.jpg)
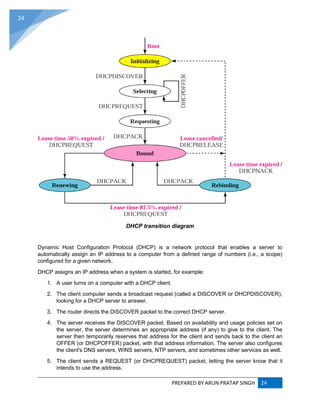
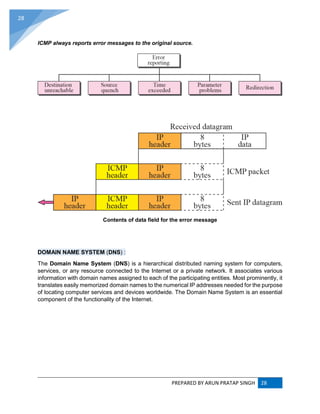
![PREPARED BY ARUN PRATAP SINGH 25
25
6. The server sends an ACK (or DHCPACK) packet, confirming that the client has a been given
a lease on the address for a server-specified period of time.
When a computer uses a static IP address, it means that the computer is manually configured to use
a specific IP address. One problem with static assignment, which can result from user error or
inattention to detail, occurs when two computers are configured with the same IP address. This creates
a conflict that results in loss of service. Using DHCP to dynamically assign IP addresses minimizes
these conflicts.
Diagram of a typical DHCP session
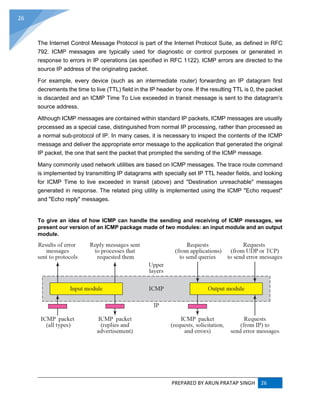
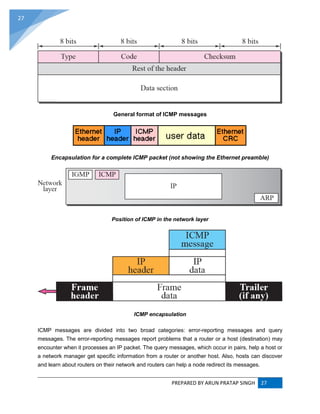
INTERNET CONTROL MESSAGE PROTOCOL (ICMP) :
The Internet Control Message Protocol (ICMP) is one of the main protocols of the Internet Protocol
Suite. It is used by network devices, like routers, to send error messages indicating, for example, that
a requested service is not available or that a host or router could not be reached. ICMP can also be
used to relay query messages.[1]
It is assigned protocol number 1.[2]
ICMP[3]
differs from transport
protocols such as TCP and UDP in that it is not typically used to exchange data between systems, nor
is it regularly employed by end-user network applications (with the exception of some diagnostic tools
like ping and trace route).
ICMP for Internet Protocol version 4 (IPv4) is also known as ICMPv4. IPv6 has a similar
protocol, ICMPv6.](https://image.slidesharecdn.com/webtechnologyandcommerceunit-1byarunpratapsingh-140728225010-phpapp02/85/Web-technology-and-commerce-unit-1-26-320.jpg)



![PREPARED BY ARUN PRATAP SINGH 36
36
When Telnet was initially developed in 1969, most users of networked computers were in the
computer departments of academic institutions, or at large private and government research
facilities. In this environment, security was not nearly as much a concern as it became after the
bandwidth explosion of the 1990s. The rise in the number of people with access to the Internet,
and by extension the number of people attempting to hack other people's servers, made
encrypted alternatives necessary.
Experts in computer security, such as SANS Institute, recommend that the use of Telnet for
remote logins should be discontinued under all normal circumstances, for the following reasons:
Telnet, by default, does not encrypt any data sent over the connection (including passwords),
and so it is often practical to eavesdrop on the communications and use the password later
for malicious purposes; anybody who has access to a router, switch, hub or gateway located
on the network between the two hosts where Telnet is being used can intercept the packets
passing by and obtain login, password and whatever else is typed with a packet analyzer.
Most implementations of Telnet have no authentication that would ensure communication is
carried out between the two desired hosts and not intercepted in the middle.
Several vulnerabilities have been discovered over the years in commonly used
Telnet daemons.
These security-related shortcomings have seen the usage of the Telnet protocol drop rapidly[citation
needed]
, especially on the public Internet, in favor of the Secure Shell (SSH) protocol, first released](https://image.slidesharecdn.com/webtechnologyandcommerceunit-1byarunpratapsingh-140728225010-phpapp02/85/Web-technology-and-commerce-unit-1-37-320.jpg)
