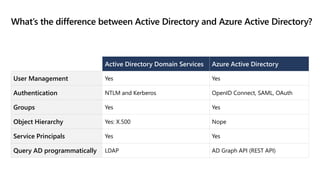
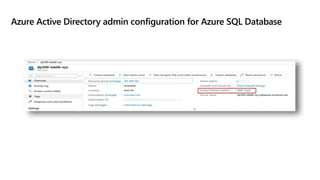
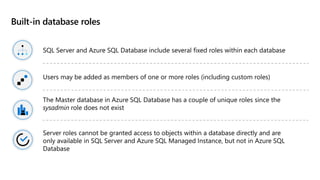
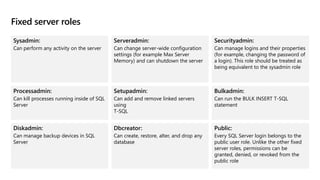
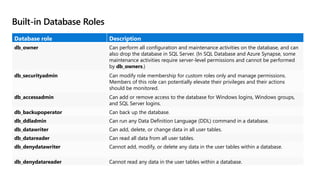
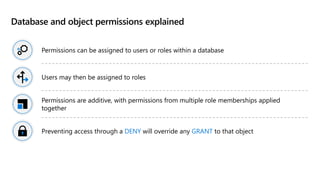
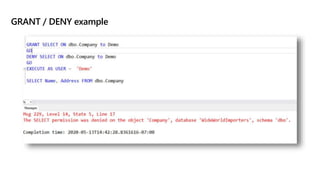
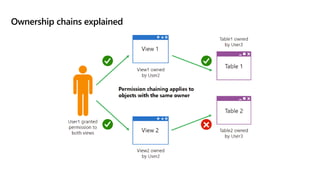
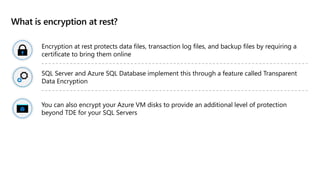
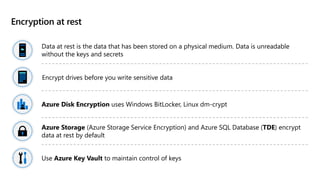
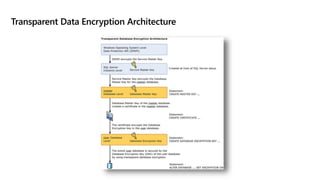
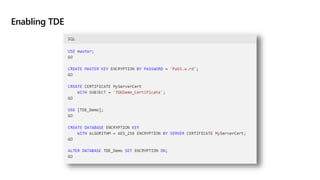
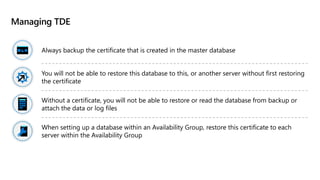
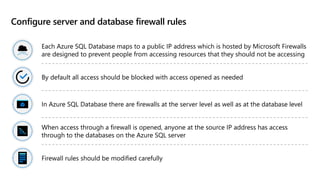
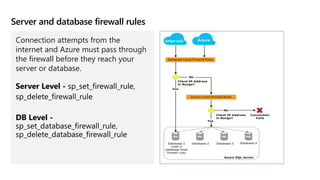
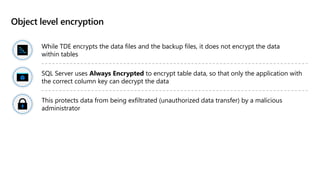
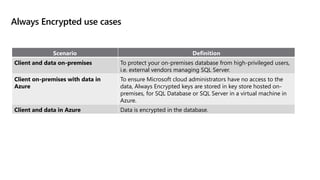
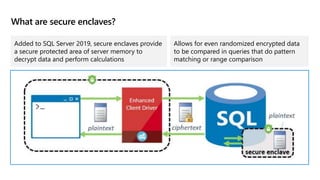
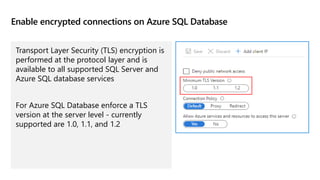
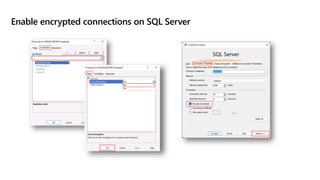
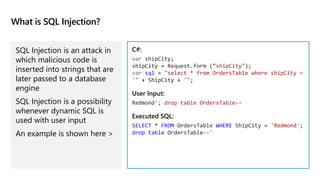
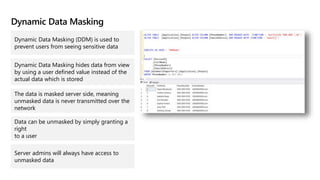
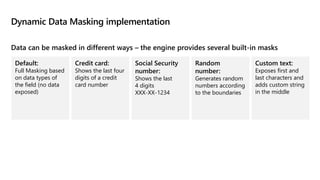
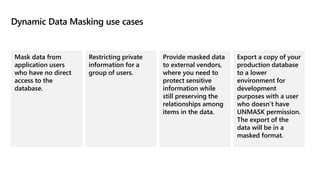
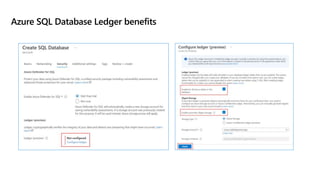
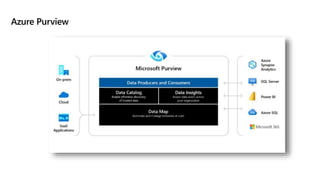
This document provides an overview of implementing a secure environment for an Azure SQL database. It discusses authentication options like Azure Active Directory authentication and SQL authentication. It also covers encrypting data at rest using Transparent Data Encryption (TDE) and encrypting data in transit. Additionally, it describes configuring firewall rules and private endpoints for network security. The document demonstrates configuring an Active Directory admin, permission chaining, and Always Encrypted for encrypting column values. It also discusses using Azure Key Vault for securely storing encryption keys.