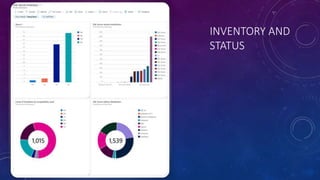
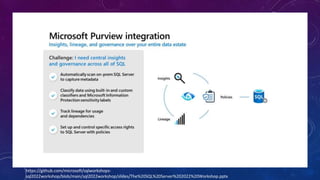
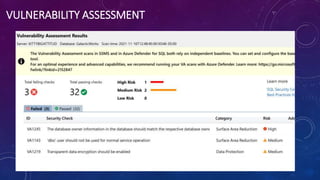
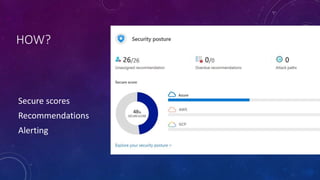
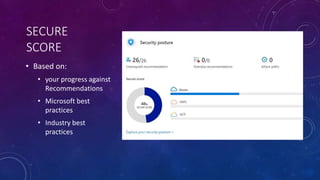
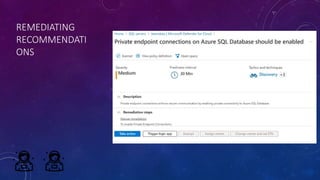
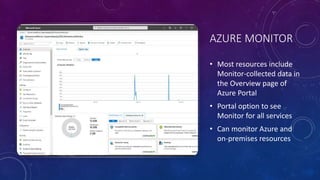
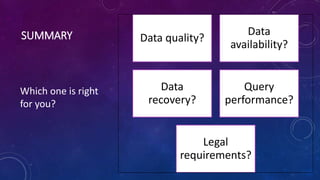
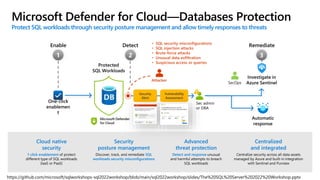
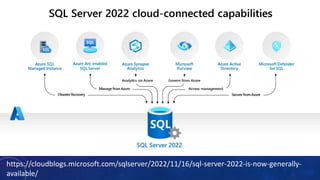
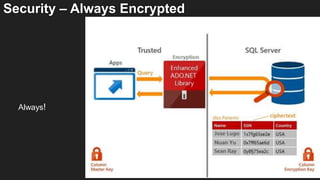
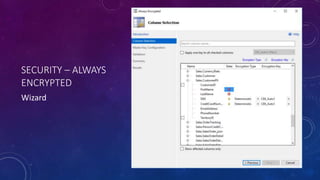
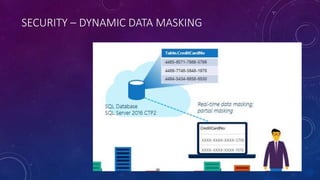
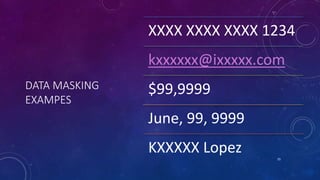
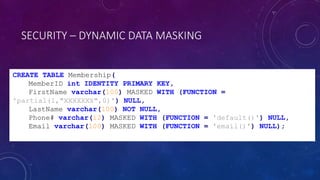
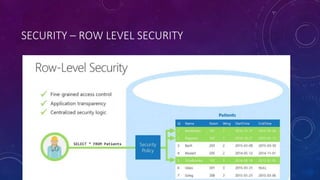
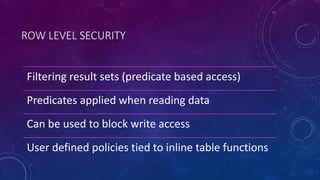
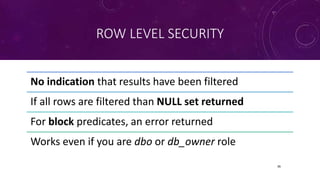
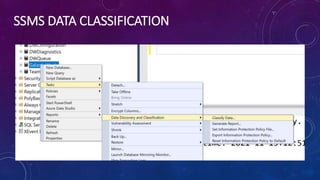
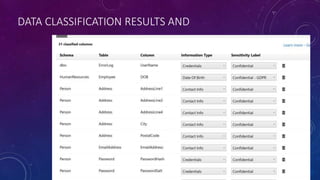
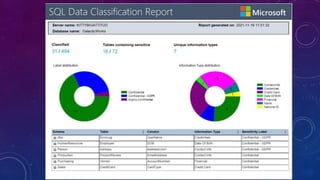
Karen Lopez, a database designer with over 20 years of experience, discusses important security and privacy features in SQL Server and Azure, emphasizing the significance of data governance, metadata tracking, and security measures like always encrypted and dynamic data masking. She outlines the importance of every design decision being based on cost, benefit, and risk while highlighting features such as row-level security and ledger tables. The document also reviews Microsoft's Azure Defender for effective database security management, showcasing tools for vulnerability assessments and compliance with legal requirements.














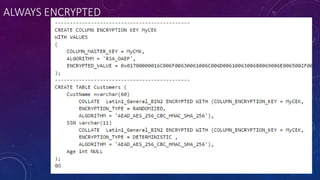











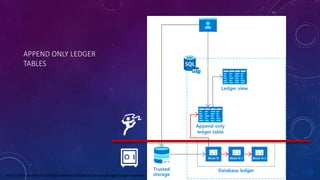
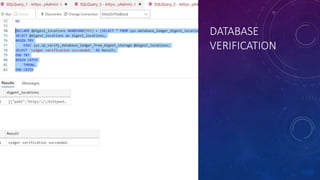
![AZURE SQL DB LEDGER TABLE – APPEND ONLY
CREATE SCHEMA [AccessControl]
CREATE TABLE [AccessControl].[KeyCardEvents]
(
[EmployeeID] INT NOT NULL,
[AccessOperationDescription] NVARCHAR (MAX) NOT NULL,
[Timestamp] Datetime2 NOT NULL
)
WITH (LEDGER = ON (APPEND_ONLY = ON) );](https://image.slidesharecdn.com/karensfavfeaturessqlserver2023-231017150224-4e48b2c3/85/A-Designer-s-Favourite-Security-and-Privacy-Features-in-SQL-Server-and-Azure-SQL-DB-43-320.jpg)
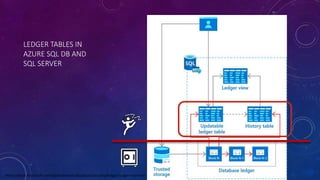
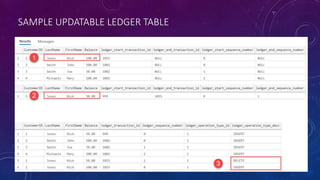
![AZURE SQL DB LEDGER TABLE – UPDATABLE
CREATE TABLE [Account].[Balance]
(
[CustomerID] INT NOT NULL PRIMARY KEY CLUSTERED,
[LastName] VARCHAR (50) NOT NULL,
[FirstName] VARCHAR (50) NOT NULL,
[Balance] DECIMAL (10,2) NOT NULL
)
WITH
(SYSTEM_VERSIONING = ON, LEDGER = ON);](https://image.slidesharecdn.com/karensfavfeaturessqlserver2023-231017150224-4e48b2c3/85/A-Designer-s-Favourite-Security-and-Privacy-Features-in-SQL-Server-and-Azure-SQL-DB-45-320.jpg)