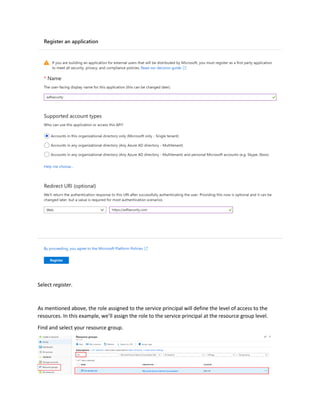
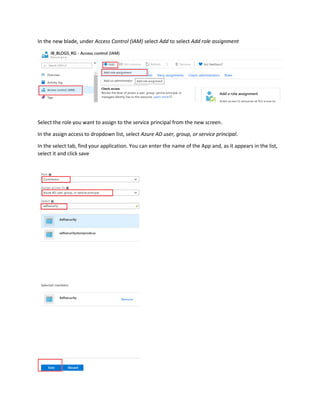
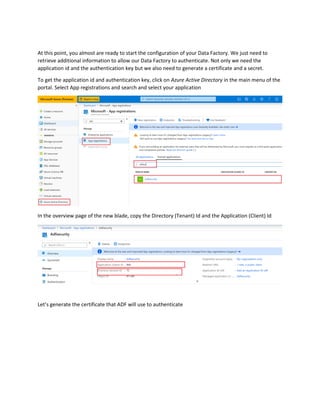
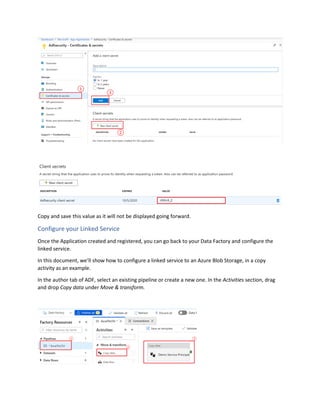
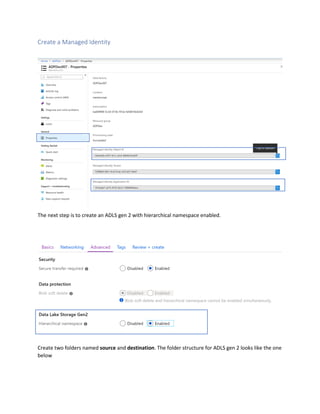
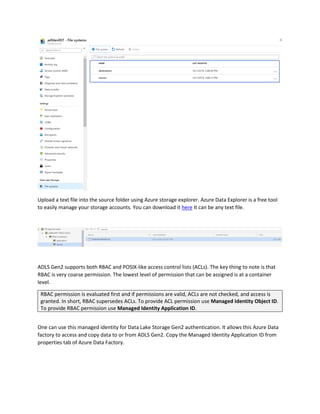
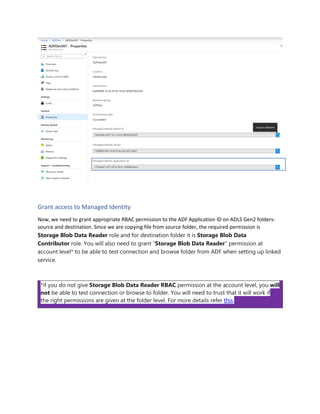
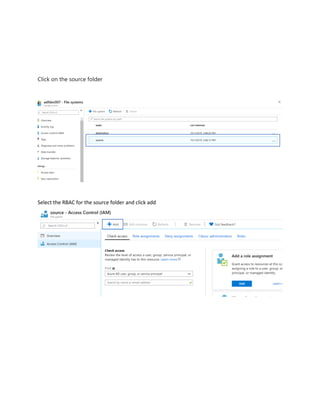
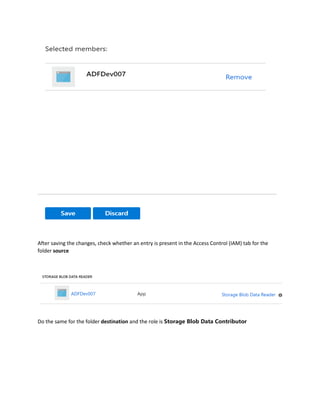
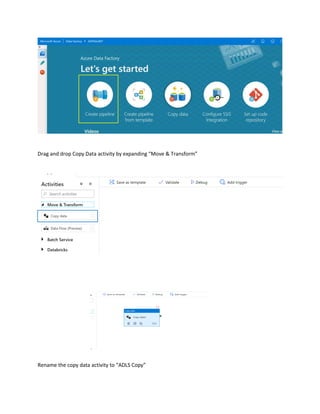
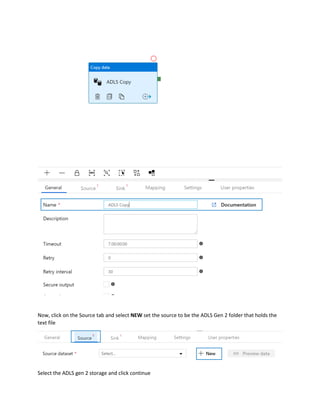
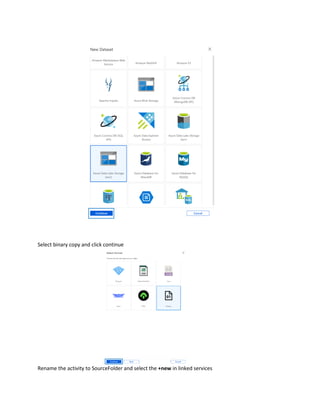
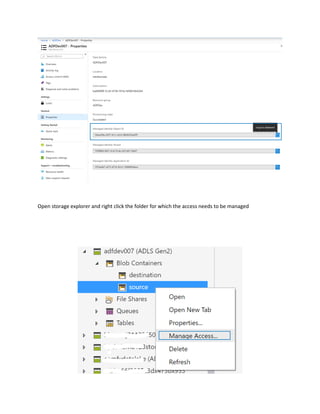
This document is a comprehensive guide to security options for Azure Data Factory (ADF), focusing on authentication methods such as Service Principal and Managed Identity. It outlines the steps to create and configure these identities for secure access to data sources, emphasizing the importance of proper permissions to facilitate data pipeline operations. The guide also compares the functionalities of Service Principal and Managed Identity, recommending Managed Identity as the preferable option for environments where managed services are prioritized.