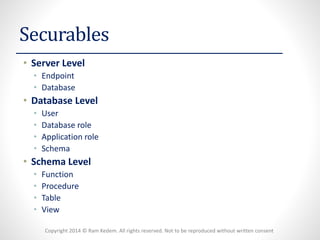
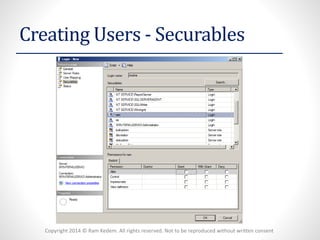
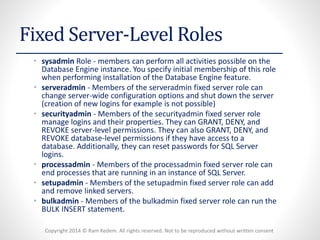
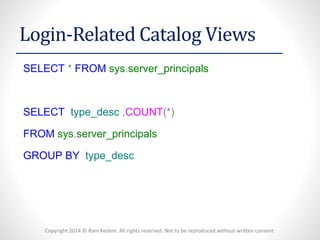
The document discusses security logins and server roles in SQL Server. It describes the different types of principals (Windows, Server, Database), securables (server, database, schema), and logins (Windows authenticated, SQL authenticated). It also covers creating and managing users, server roles, database roles, and application roles. Server roles include fixed and user-defined roles. Logins must be mapped to database users and can be altered or removed.