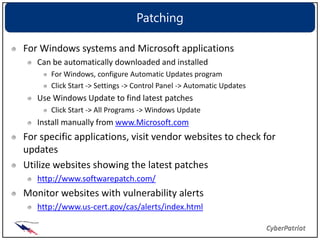
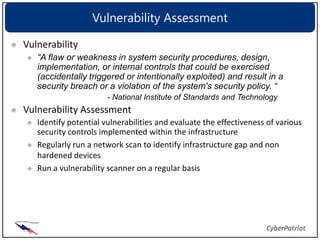
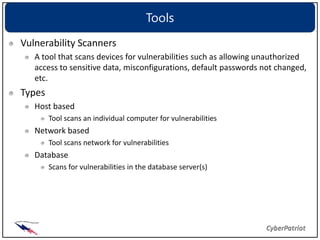
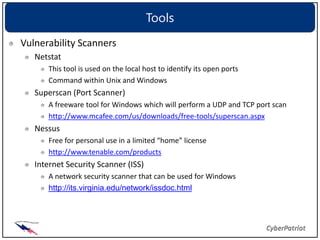
Patching and updating software is important to mitigate vulnerabilities. Regularly applying patches from vendors keeps systems secure by fixing known issues exploited by viruses, worms, and hackers. It is also important to monitor websites for the latest vulnerability information and use scanning tools to identify vulnerabilities on networks and hosts. Once found, vulnerabilities should be remediated by applying patches, changing configurations, or removing unauthorized access. Regular assessments help measure security controls and identify gaps.